
What are SMB Ports?
The SMB (Server Message Block) protocol provides for “client-server communication,” allowing programs and services on networked computers to communicate. File, print, and device sharing are just a few of the network functions enabled by SMB.
History of SMB
During the mid-1990s, Microsoft incorporated SMB in their LAN Manager product, which IBM initially built. SMB 1.0 was renamed CIFS (Common Internet File System), and Microsoft published some draft standards to the Internet Engineering Task Force (IETF), though those have expired.
SMB/early CIFS’s implementation had several flaws that limited its applicability to managing small files for end-users. The protocol was “chatty,” which resulted in poor performance over long distances or when there was a lag between client and server.
Around this time, the Samba project was born to reverse-engineer the SMB/CIFS protocol and developed an SMB server that would allow MS-DOS clients to access files on Unix machines.
What are Versions of SMB Ports?
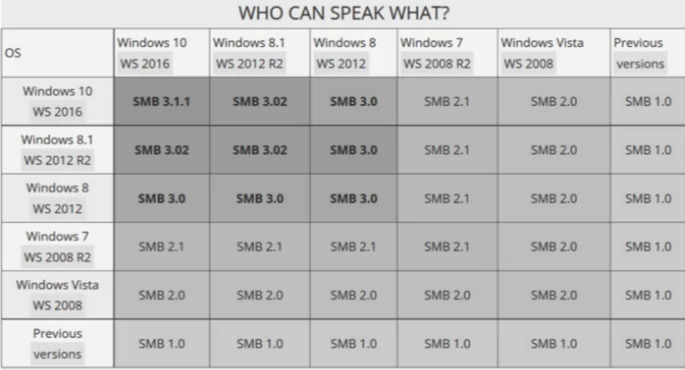
SMB 2.0
Microsoft released SMB2 with Windows Vista in 2006. SMB2.0 had many improvements over SMB 1.0, particularly reducing the “chattiness” of the protocol by reducing the number of commands and subcommands from hundreds to nineteen. The term CIFS become redundant, as it only applied to SMB version 1.0
SMB2
SMB2 supported many other improvements like TCP window scaling and WAN acceleration, opportunistic locking, and a feature known as “pipelining” to enable multiple requests to be queued simultaneously.
Performance improvements involved allowing larger block sizes, thus improving large file transfers. Microsoft introduced “durable file handles,” which allowed the connection to an SMB server to survive brief network failure frequently seen in wireless networks by enabling clients to reconnect to servers transparently.
SMB 2.1
SMB 2.1 was released alongside Windows 7 and Windows Server 2008 and included minor upgrades.
SMB 3.0
With Windows 8 and Windows Server 2012, SMB 3.0 (also known as SMB 2.2) was released. SMB3 included significant protocol modifications such as the SMB Direct Protocol (SMB over RDMA) and SMB Multichannel (many connections per SMB session), which improved SMB2 performance, particularly in virtualized data centers.
How Does SMB Work?
The SMB protocol establishes communication between clients and servers by sending and receiving request-response messages. A user accessing data on their hard drive would set up a file-sharing system. It would make dealing with networked systems worldwide a lot easier.
Other operating systems, such as Unix, Linux, and OS/2, use Samba to connect and provide file-sharing services within a network by speaking the same language as SMB.
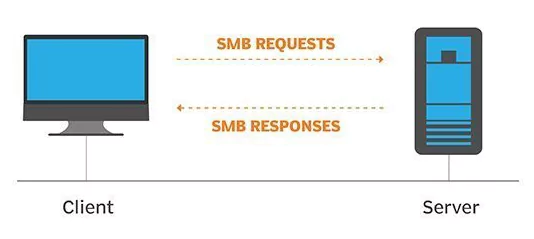
What Ports are Used by SMB Protocol?
To provide file and print sharing services within a network, SMB uses numerous ports. The following are all known SMB v2/v3 ports:
- TCP 445 — SMB over TCP without the need for NetBIOS
- UDP 137 — SMB over UDP (Name Services)
- UDP 138 — SMB over UDP (Datagram)
- TCP 139 — SMB over TCP (Session service)
What are SMB Ports 139 and 445?
Port 139
Port 139 is used by the NetBIOS session service. Before Windows 2000, most operating systems used TCP 139, with SMB running on top of NetBIOS. NetBIOS, which stands for Network Basic Input/Output System, is a service on the OSI model’s session layer that allows applications to communicate within a local network (LAN). This situation might be anyone on the internet, but it is not a recommended alternative because of security concerns.
Port 445
Simply put, Windows uses port 445 for file sharing across the network. From Windows 2000 forward, Microsoft changed SMB to use port 445. Microsoft directory services, often known as Microsoft-DS, use port 445.
TCP and UDP protocols both use port 445 for numerous Microsoft services. Microsoft Active Directory and Domain Services use this port for file replication, user and computer authentication, group policy, and trusts. SMB, CIFS, SMB2, DFSN, LSARPC, NbtSS, NetLogonR, SamR, and SrvSvc protocols and services are most likely to be found on these ports.
Is SMB Secure?
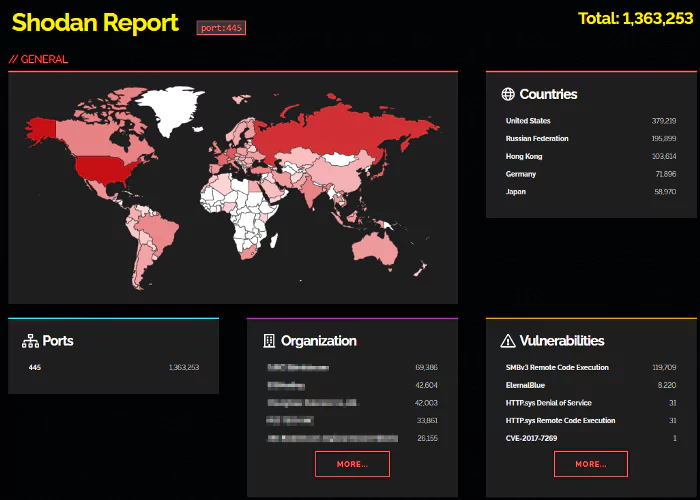
While different versions of SMB provide differing levels of security and protection, SMBv1 was discovered to have a vulnerability that hackers may exploit to execute their code without the user’s knowledge. When a gadget becomes infected, it attacks any other devices linked to it. In 2017, the National Security Agency (NSA) uncovered the flaw.
EternalBlue was the name of the exploit, which was taken from the NSA and posted online by the Shadow Brokers hacker group. Microsoft did issue a patch to address the vulnerability, but the WannaCry ransomware attack hit the world just a month later.
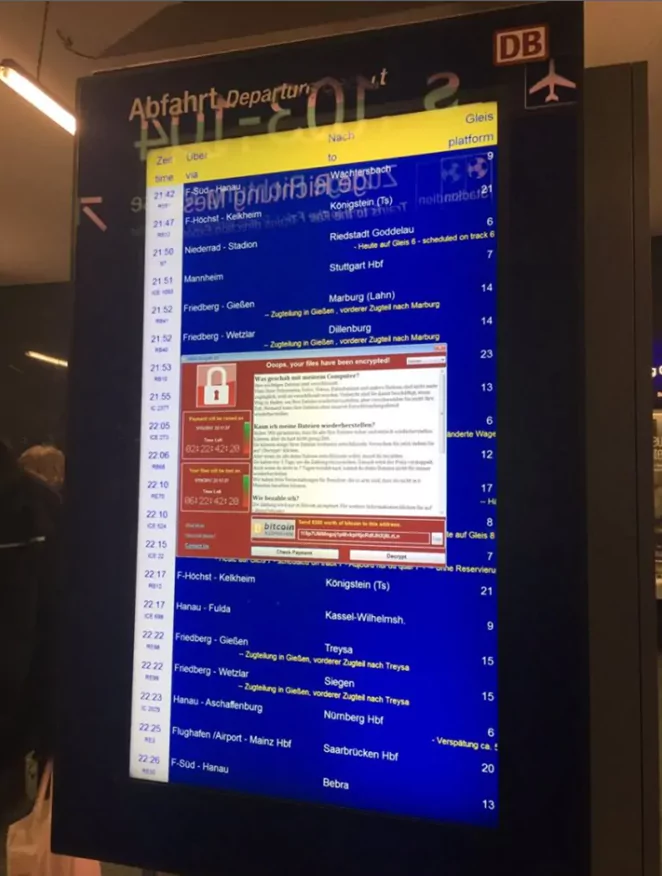
How to Prevent SMB Vulnerabilities?
Patching your system is the best defense against an SMB attack. Attackers will be unable to access a patched machine, but many Windows computers have yet to be patched. The March 2017 update from Microsoft can assist in patching the Server Message Block vulnerabilities, and applying this fix is one of the most incredible ways to safeguard a system.
The update fixes are already built-in if your Windows system is Windows 10 or later, which is why most SMB assaults target Windows 7 and earlier. Furthermore, the WannaCry patch can prevent EternalBlue exploits and other similar flaws. These fixes are among the most effective SMB server security solutions available.
It’s better to have layers of security when protecting yourself from cyberattacks, as it is with other things. Apart from the Wannacry and ransomware patches, you can further safeguard your systems by restricting SMB access from the internet, blocking SMB in off-site computers when in public areas, and removing SMB if it’s not needed. These easy measures can help protect your system from SMB exploits. Finally, vulnerability scanning and Managed Detection and Response services can help your system avoid and identify SMB attacks and other cyberattacks.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































