International Authorities Strike Blow Against LockBit Ransomware: Operation Cronos
[Update] October 1, 2024: “New Arrests and Infrastructure Seizures”
[Update] June 6, 2024: “FBI Offers +7,000 LockBit Decryption Keys to Ransomware Victims”
[Update] March 7, 2024: “The Man Behind the LockBit Ransomware Has Been Identified”
[Update] March 6, 2024: “LockBit’s Seized Leak Site Resurfaces”
[Update] March 3, 2024: “LockBit’s Many Bluffs”
[Update] February 26, 2024: “A Week After: LockBit Strikes Back”, “Speculations”
[Update] February 23, 2024: “Who is LockBitSupp?”, “Attempt for LockBit 4.0”, “Alleged LockBit Activity”
[Update] February 22, 2024: “Rewards for Reporting”
[Update] February 21, 2024: “A Day After: A Major Leak on the Horizon”
[Update] February 20, 2024: “Update: National Crime Agency of UK Reveals Details”
In a coordinated effort spanning 11 countries, law enforcement agencies have dealt a significant blow to the infamous LockBit ransomware operation through a joint initiative dubbed “Operation Cronos.”
Just recently, the LockBit group’s stronghold on their data leak website was wrested away by the United Kingdom’s National Crime Agency, in collaboration with the FBI and an international law enforcement task force.

Seizure announcement on LockBit’s leak site
A banner prominently displayed on the now-seized LockBit site bears the message: “This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos’.
Operation Cronos
While access to LockBit’s leak site has been effectively cut off, displaying either a seizure banner or a connection error, some of the gang’s other dark web platforms remain operational.
Almost all LockBit’s leak site Onion links appear to be unreachable. However, currently, not all of them exhibit a seizure notice.
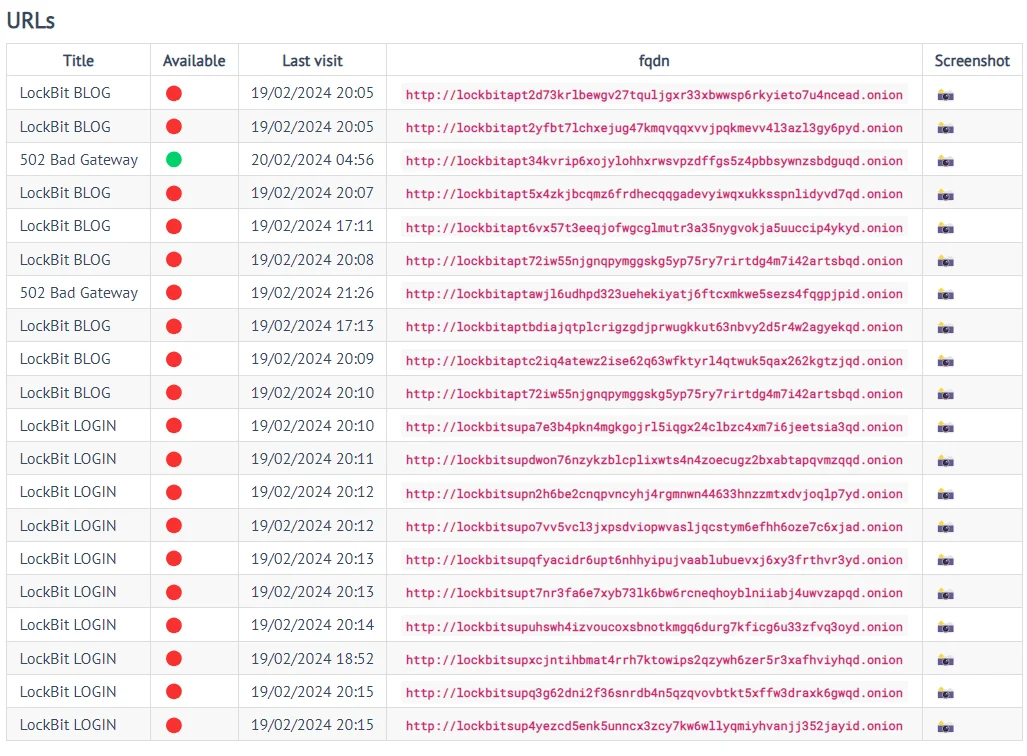
LockBit’s URLs by ransomware.live
Furthermore, the affiliate panel of LockBit has also been taken down by law enforcement, with a message indicating the seizure of LockBit’s source code, chats, and victim data.
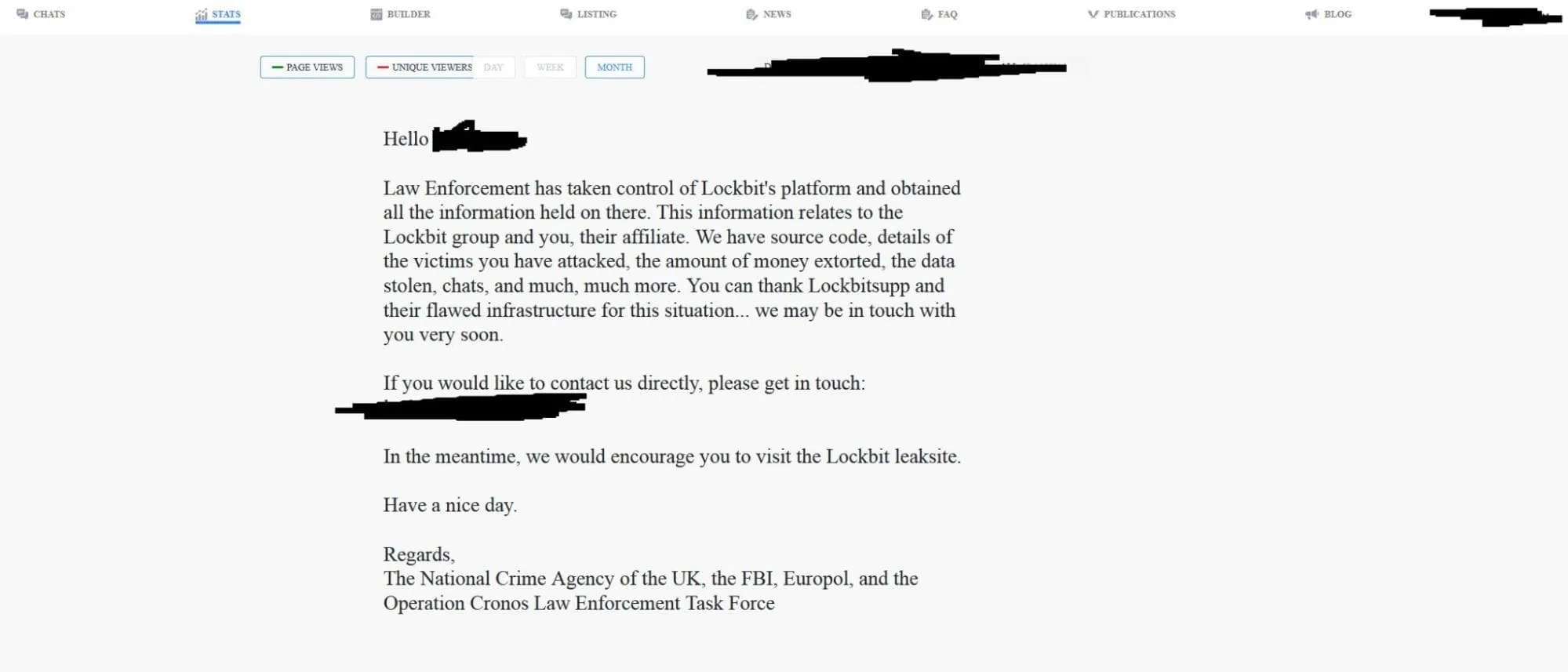
When a Lockbit affiliate tries to log into the LockBit panel, this is what they see. (vx-underground)
The message addressed to LockBit’s affiliates approximately reads: We have obtained all the information held on there, including details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much more.
In a revealing status update on the Tox messaging service, LockBitSupp, the operator behind the LockBit operation stated that the breach of their servers by the FBI via a PHP exploit.
As vx-underground shared in a tweet, the message from LockBitSupp reads:
“ФБР уебали сервера через PHP, резервные сервера без PHP не тронуты”
Translated as: “The FBI f**** up servers using PHP, backup servers without PHP are not touched”
They also claim that the law enforcement agencies compromised them via exploiting a known vulnerability.
CVE-2023-3824 – Phar Directory Entries, Insufficient Length Check Leading to RCE
Allegedly, CVE-2023-3824 is used to take control of LockBit’s leak sites. The vulnerability occurs during the loading of a Phar (PHP Archive) file. Phar files are used in PHP for packaging entire applications or libraries into a single file for distribution. However, a flaw in specific PHP versions occurs while processing the directory entries within a Phar file.
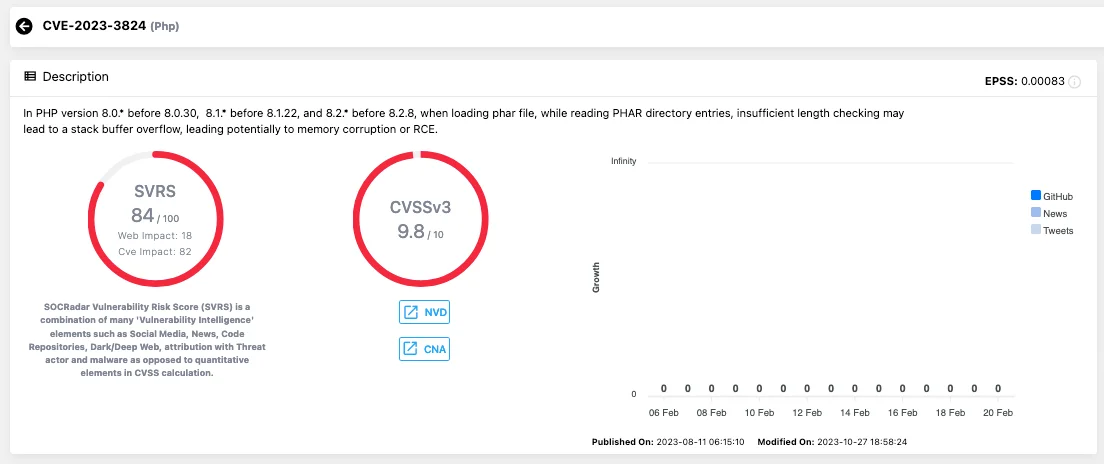
Vulnerability card of CVE-2023-3824, SOCRadar Vulnerability Intelligence
Insufficient length checking during this process can trigger a stack buffer overflow. A stack buffer overflow occurs when a program writes more data to a buffer, or memory space, than it can hold, leading to the corruption of adjacent memory locations. In the context of this vulnerability, the stack buffer overflow has the potential to cause memory corruption or allow for Remote Code Execution (RCE).
Remote Code Execution is a severe security risk where an attacker (FBI in this scenario) could exploit the vulnerability to execute arbitrary code on the affected system remotely. This could lead to various forms of malicious activity, such as installing malware, stealing sensitive data, or taking control of the affected system.
Another Blow to LockBit
Recently, LockBitSupp also found themselves banned from the XSS forum due to a breach of trust. Accusations arose suggesting that LockBit, having gained network access for encryption from another threat actor and collecting a ransom, failed to honor the agreed commission.
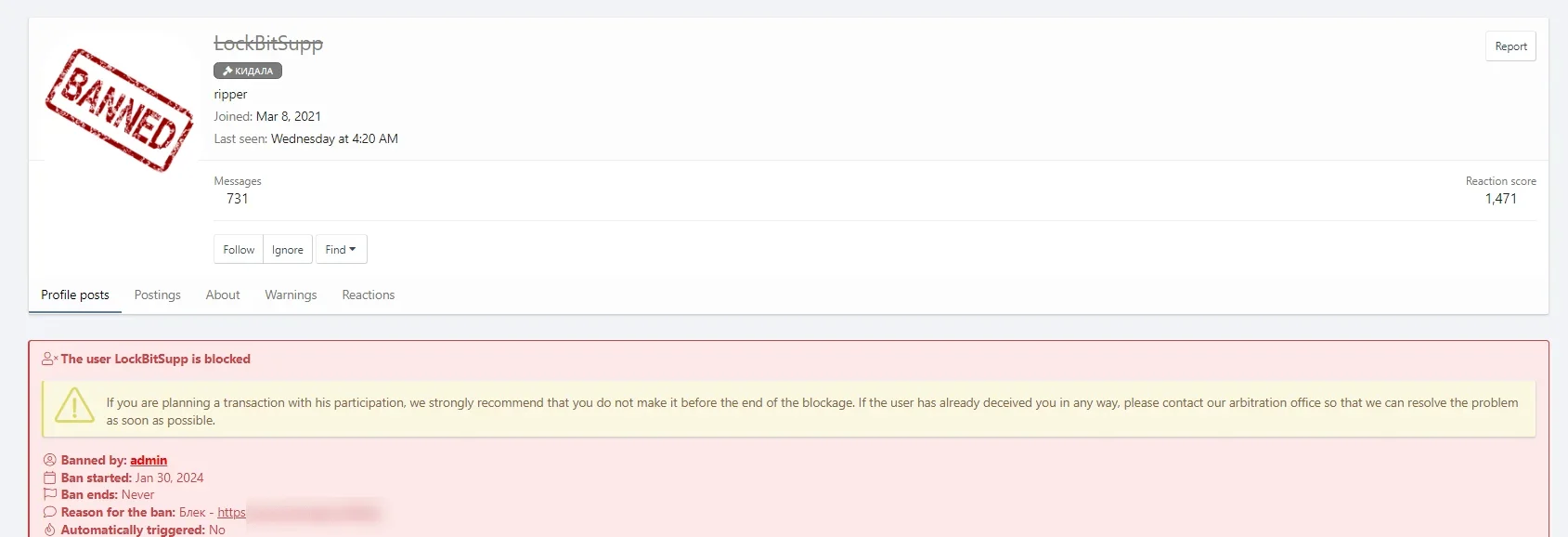
LockBit’s now banned account
Instead, they provided compensation solely for the network access. Subsequently, following the ban on the XSS forum, LockBit’s profile was also barred from Exploit. In other words, LockBit, which started to be ostracized within its own circles, now suffered another major blow. However, a question arises, did the escalation of this event also have an impact on the seizure of LockBit leak sites?
Conclusion
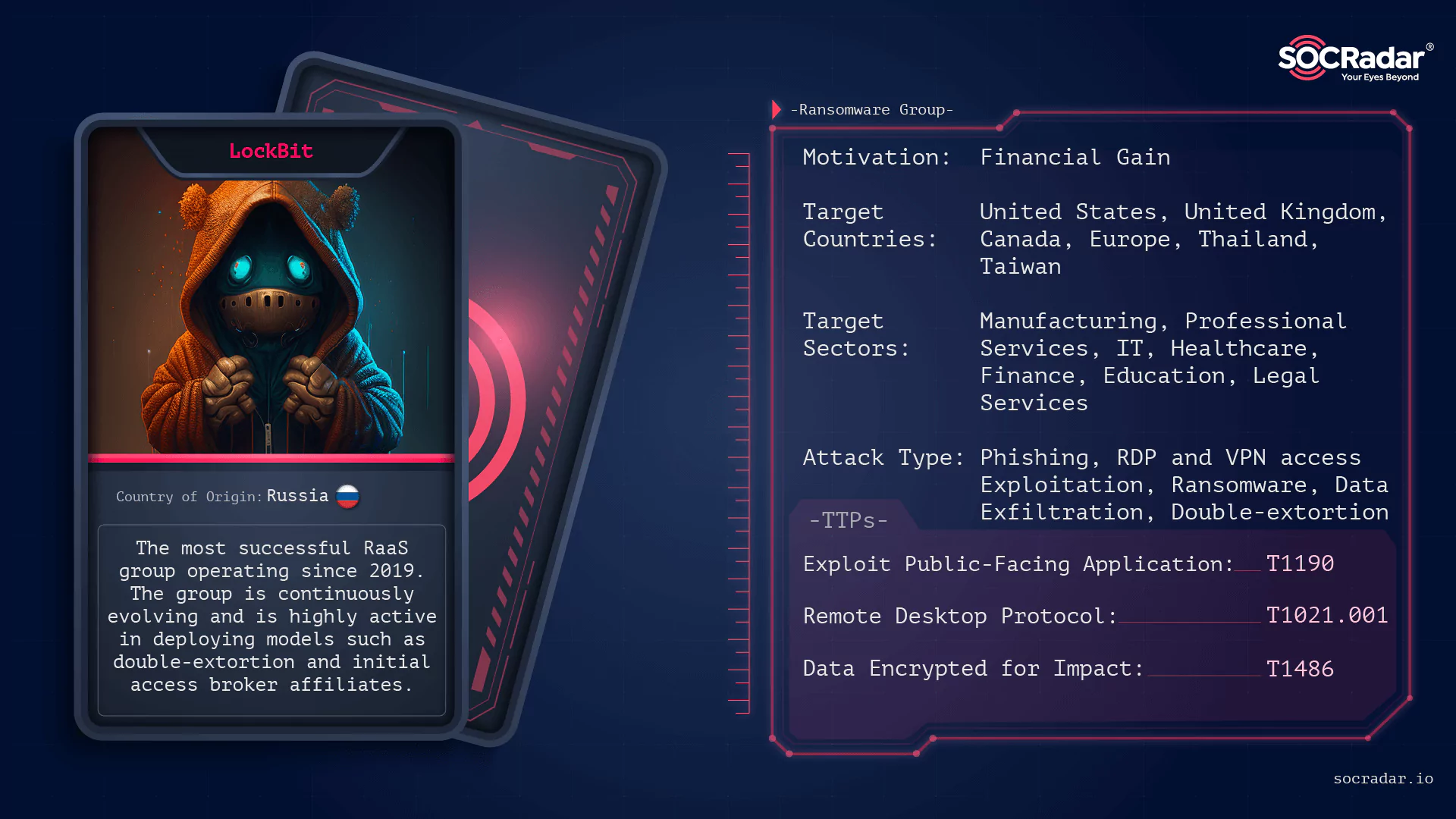
LockBit’s emergence as a Ransomware-as-a-Service (RaaS) group in 2019 signaled the onset of a campaign aimed at various prominent organizations globally. Throughout the past few years, LockBit has maintained its position as the preeminent and most prolific ransomware group, boasting the highest tally of victims.
Therefore, the takedown of LockBit signifies a significant victory in the ongoing battle against cybercrime, showcasing the effectiveness of international cooperation in combating such threats.
Update: National Crime Agency of UK Reveals Details
After a countdown in X, the NCA disclosed information about the international campaign aimed at disrupting LockBit.
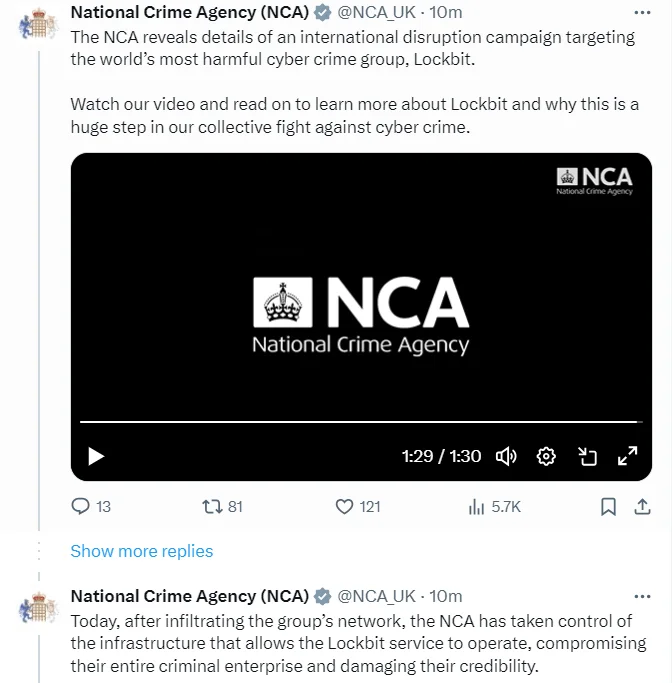
National Crime Agency’s statements (X)
Their statement as follows:
“LockBit offered ransomware-as-a service, supplying global hacker with tools and infrastructure required to carry out ransomware attacks. LockBit attacks have targeted over 2,000 global victims, causing billions of pounds-worth of damage. The NCA, FBI and a number of international partners have been covertly investigating this group for some time. Today, after infiltrating the group’s network, the NCA has taken control of the infrastructure that allows the LockBit service to operate, compromising their entire criminal enterprise. We have obtained a vast amount of intelligence from their systems and will continue to target LockBit and their associates. This activity forms part of an ongoing, concerted campaign by the international Operation Cronos taskforce to target and disrupt Lockbit ransomware. LockBit will likely attempt to regroup and rebuild their criminal enterprise. But we know, who they are, and we will be watching.”
Furthermore, the international coalition, employing tactics akin to cybercriminals’ tactics, defaced the LockBit leak site and filled its leak site’s main page with their statements, decryption tools, and threat feeds.

Current main page now belongs to security forces
In one segment law enforcement agencies also announced the arrest of 2 LockBit ransomware group members in Poland and Ukraine.
Some of the other segments are as follows:
After a brilliant operation, security forces demonstrate their penchant for humor, showcasing a lighter side amidst their serious duties.
LockBit even got banned from their own infrastructure
In addition to seizing numerous infrastructures, security forces are further undercutting LockBit’s operations by disseminating decryptor and recovery tools directly within the heart of their adversaries’ territory. This strategic move suggests that LockBit is poised to remain significantly incapacitated for the foreseeable future, signaling its eventual demise.
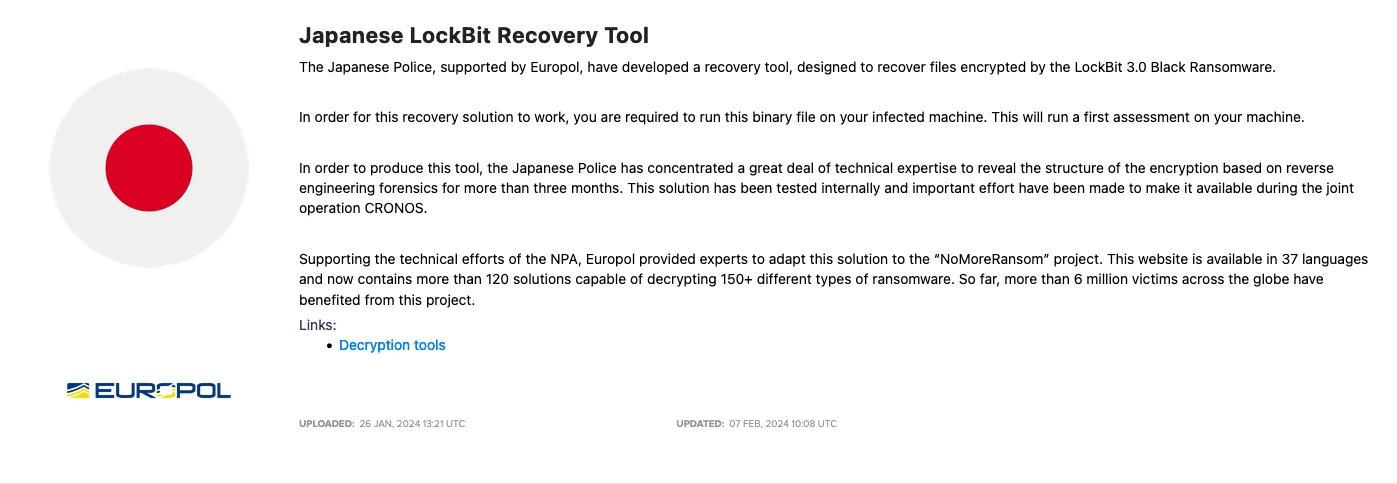
Recovery Tool by Japanese Police and Europol
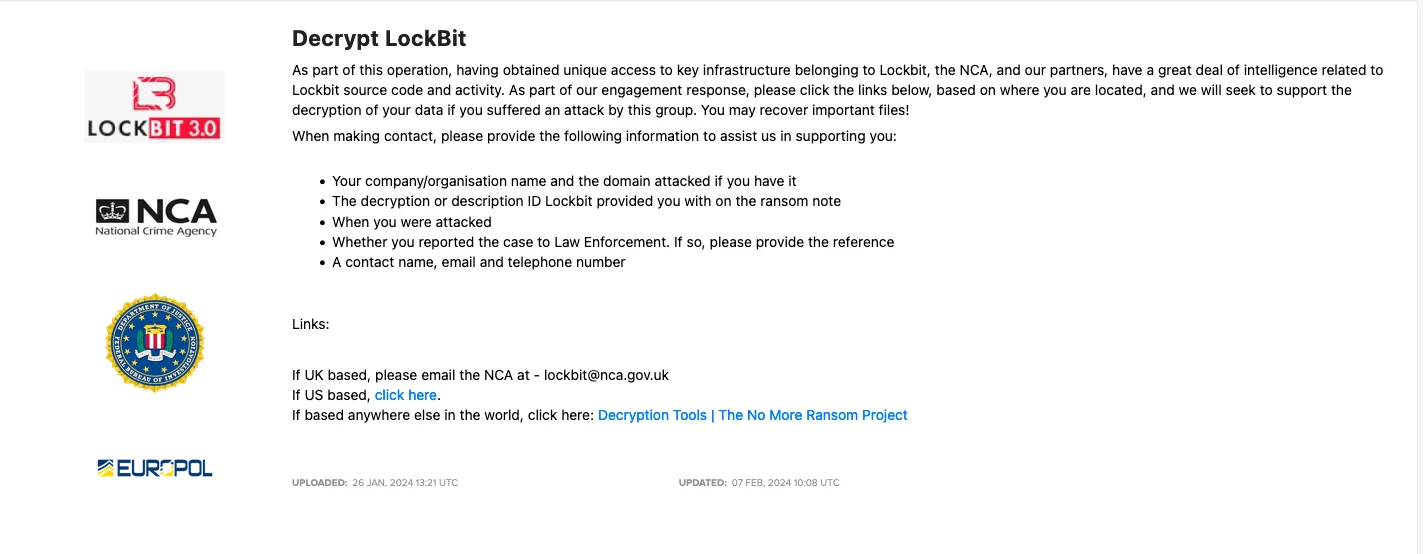
LockBit Decryptors from The No More Ransom Project
Check out the official source for the full statement.
Europol also made a statement on the subject and shared an infographic summarizing the issue.

Europol’s infographic about the Operation Cronos
A Day After: A Major Leak on the Horizon
What happened yesterday?
International authorities have intensified their crackdown on the LockBit ransomware operation. With the arrests of two LockBit operators in Poland and Ukraine, the subsequent release of a decryption tool, and the seizure of over 200 cryptocurrency wallets, the law enforcement agencies dealt a heavy blow to the group’s infrastructure yesterday.
What do we know today?
Newly released information from the US, UK, and Europol details that LockBit operates with 187 affiliates, highlighting the group’s extensive network. While security forces are working to identify these threat actors, an announcement about the LockBit admin will also be published this week.
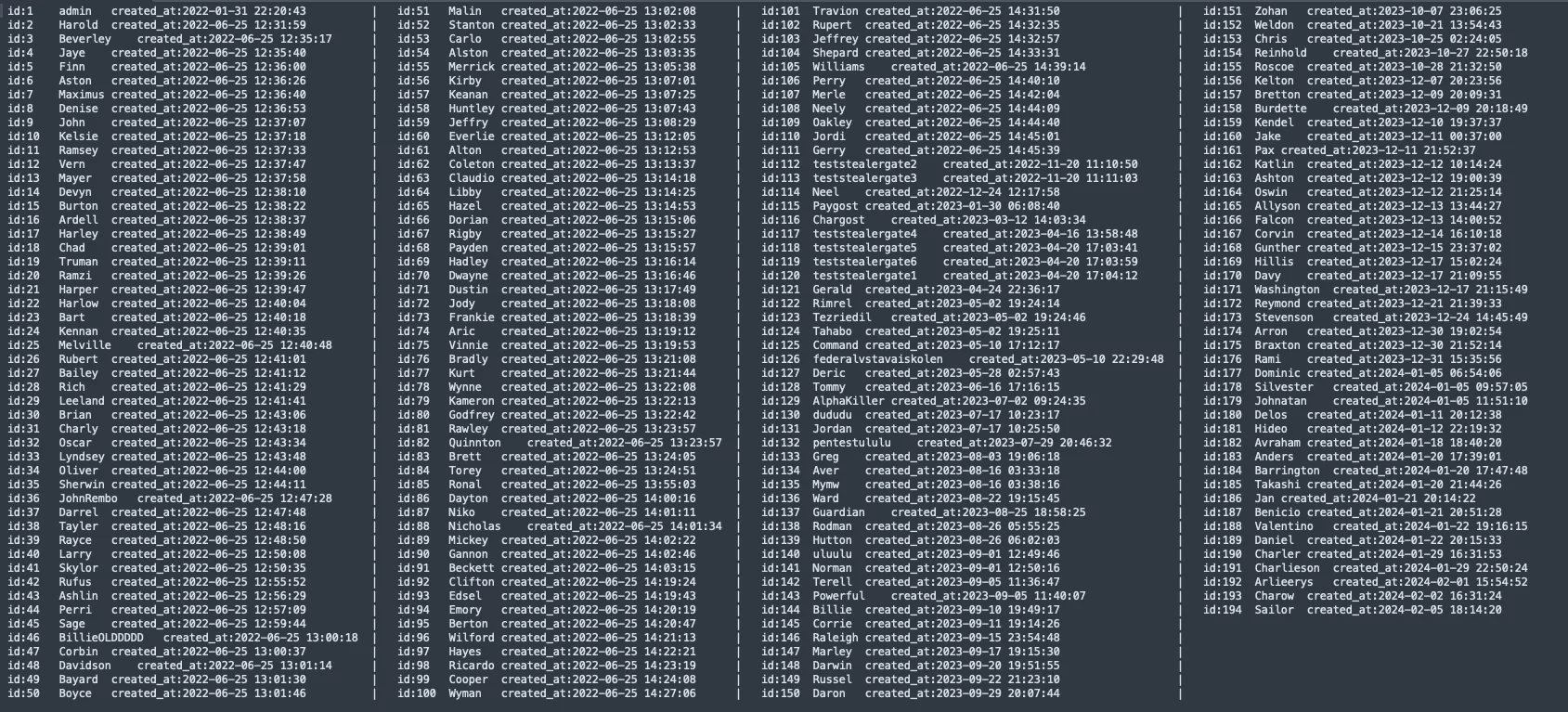
LockBit affiliate accounts have nearly 190 threat actor names, there are also admin and test accounts, total account number is 193.
Is LockBit going to execute a counterstrike?
Despite these setbacks, some claims suggest that LockBit administrators may launch an alternative server and cause a significant data breach. So, it seems that further breaches are possible to come if LockBit has some resources left. It’s also important to note that among the data LockBit has, there is data of companies that have already paid the ransom. However, security forces also state that the stolen data is safe.
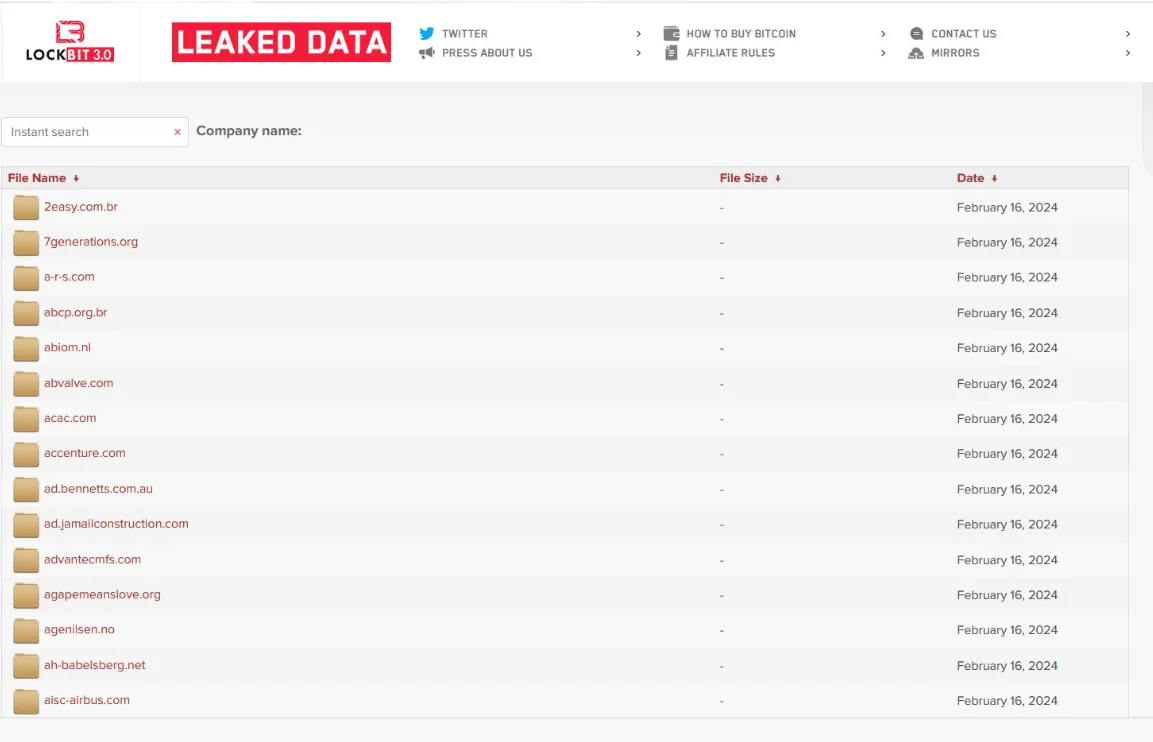
The latest leaked companies by LockBit before the operation
How to stay informed?
SOCRadar XTI provides comprehensive monitoring across all internet surfaces, including dark web. Utilize the SOCRadar platform to stay updated on possible data breaches. Users pertinent to LockBit’s data exposures receive alerts, and you can delve deeper into specific threats through the Threat Hunting feature.
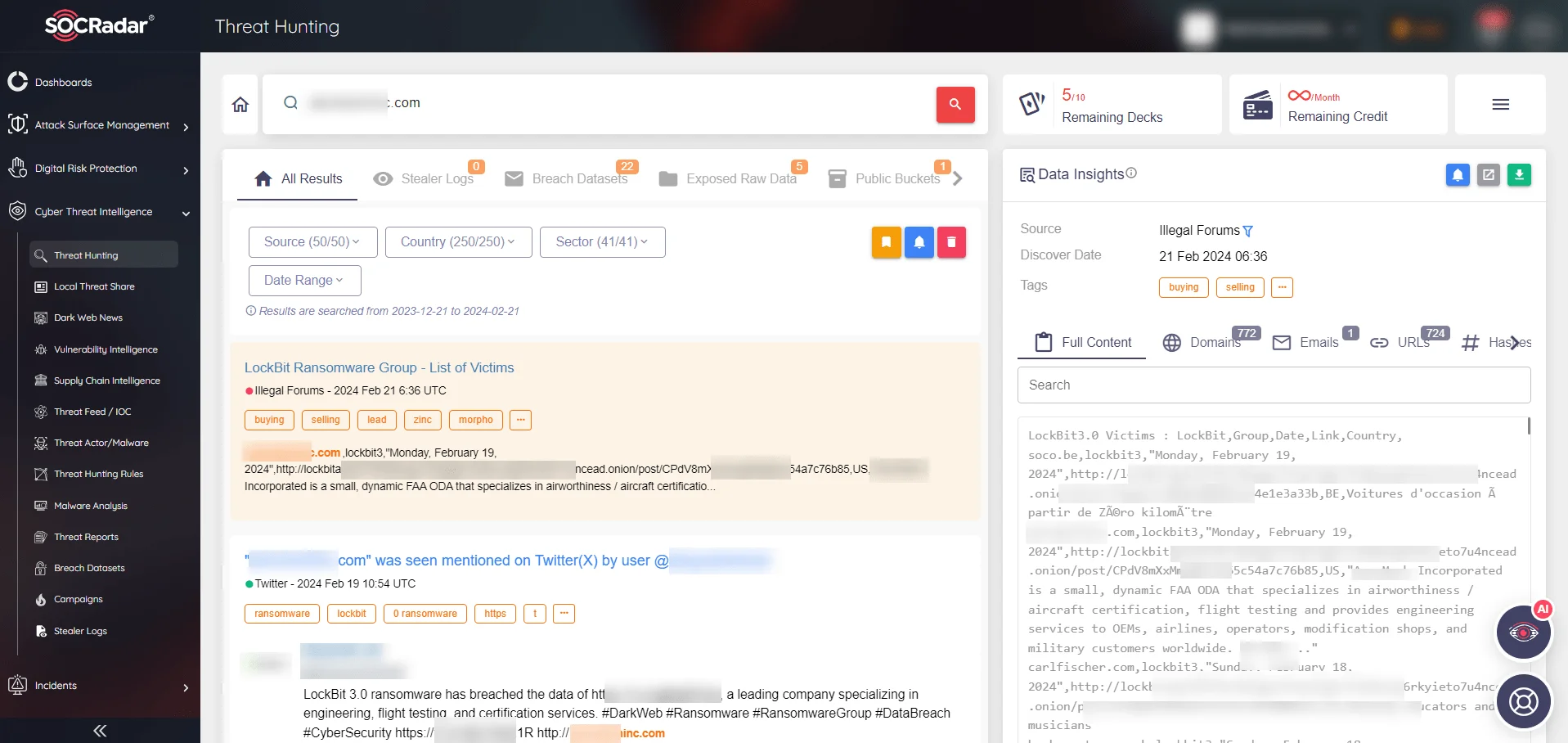
SOCRadar Platform, Threat Hunting feature
Rewards for Reporting
As of 22 February, the U.S. Department of State is providing a reward of up to $10 million to anyone who can provide information that helps identify or locate individuals holding key leadership roles within the Transnational Organized Crime group associated with the LockBit ransomware variant. Additionally, a reward of up to $5 million is available for information leading to the arrest or conviction, in any country, of individuals involved in or attempting to participate in LockBit ransomware activities.
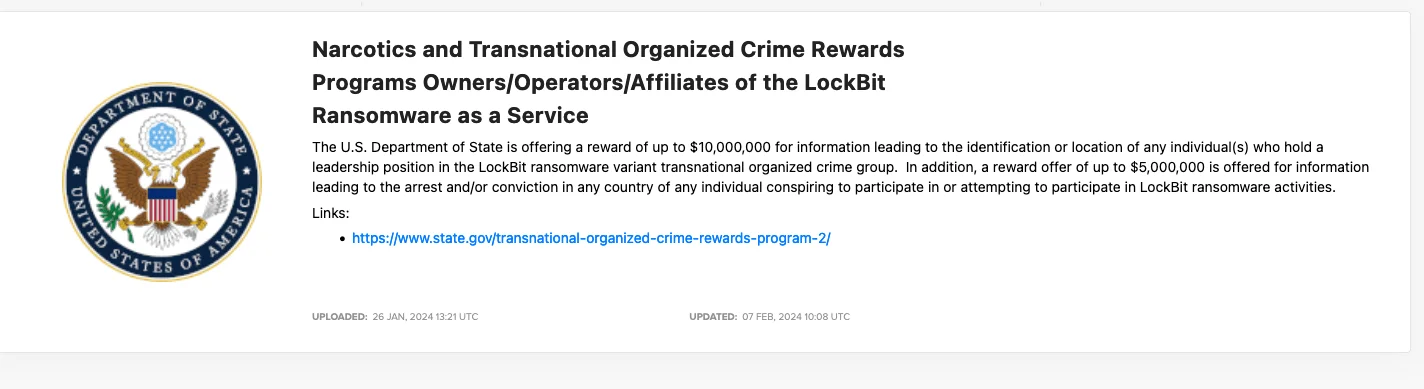
The U.S. Department of State, Bounty Program
They did not forget to share the bounty program on LockBit’s leak site.
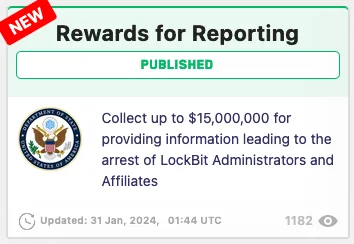
A new segment in the defaced leak site
Who is LockBitSupp?
Following the operation, a countdown appeared on LockBit’s taken-down website. The countdown for the section labeled “Who is LockbitSupp” has recently concluded, revealing the mocking response from law enforcement once more. Although it doesn’t fully address the question, this response indicates that the identity of the LockBit administrator is indeed known.
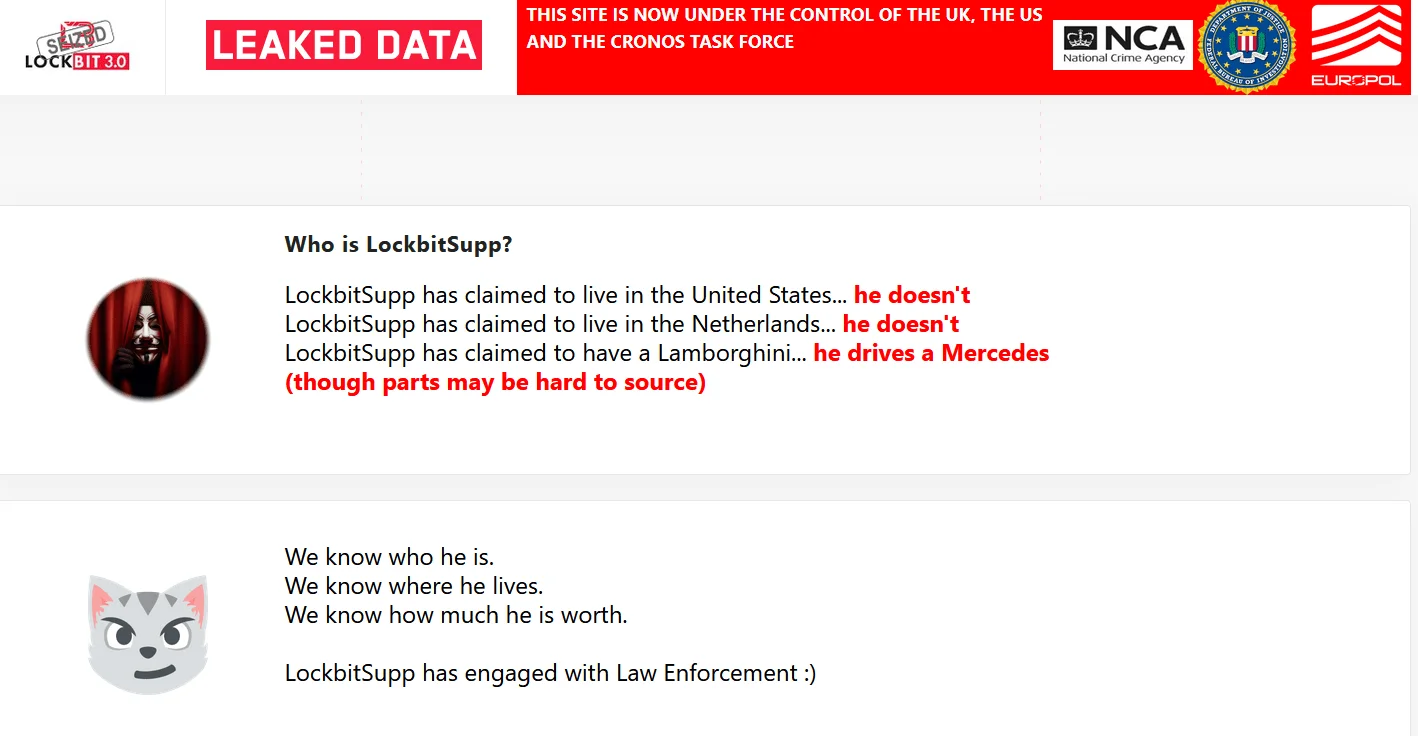
Who is LockbitSupp section on the data leak site
An Attempt for LockBit 4.0
Another detail justifying the timing of the operation was revealed by Trend Micro.
Researchers have obtained a sample indicating a significant advancement in LockBit’s development: an in-progress version of a platform-agnostic malware, distinct from its predecessors. This sample, identified as LockBit-NG-Dev, is appended with a suffix “locked_for_LockBit” to encrypted files, suggesting it’s an upcoming version still subject to changes.
LockBit-NG-Dev, currently in its developmental phase, is written in .NET and compiled using CoreRT, enhancing its platform compatibility. Although it has fewer features compared to previous versions like v2 (Red) and v3 (Black), ongoing development is expected to augment its capabilities. Notable changes include the removal of self-propagating capabilities and the ability to print ransom notes via user printers.
Additionally, LockBit-NG-Dev incorporates a validity period for execution, likely aimed at controlling affiliate use and evading automated analysis by security systems. While retaining some features from v3 (Black), such as configuration settings and file renaming capabilities, LockBit-NG-Dev represents a significant shift in LockBit’s evolution towards version 4.0.
Alleged LockBit Activity
On February 22, 2024, Sophos researchers reported ongoing LockBit activity despite recent law enforcement actions against the group. Multiple LockBit ransomware attacks were observed within the preceding 24 hours, believed to be facilitated by a leaked malware builder tool.
Although signature-based detection systems successfully identified these malicious payloads, variations were noted in the ransom notes. One ransom note labeled the ransomware as “buhtiRansom,” while the other lacked a specific identifier.
However, these findings suggest a mutation effect rather than direct LockBit activity. However, given their association with the ConnectWise ScreenConnect attacks, the seriousness of the situation remains evident.
A Week After: LockBit Strikes Back
A week after, LockBit reemerged, disclosing details about the breach and outlining measures to enhance their infrastructure’s resilience against hacking attempts. As well 6 new victims were announced on 24 and 25 February.
LockBit resumed its ransomware operations this weekend. The gang retained its brand name and relocated its data leak site to a new address, featuring a countdown for publishing stolen information from 6 victims.
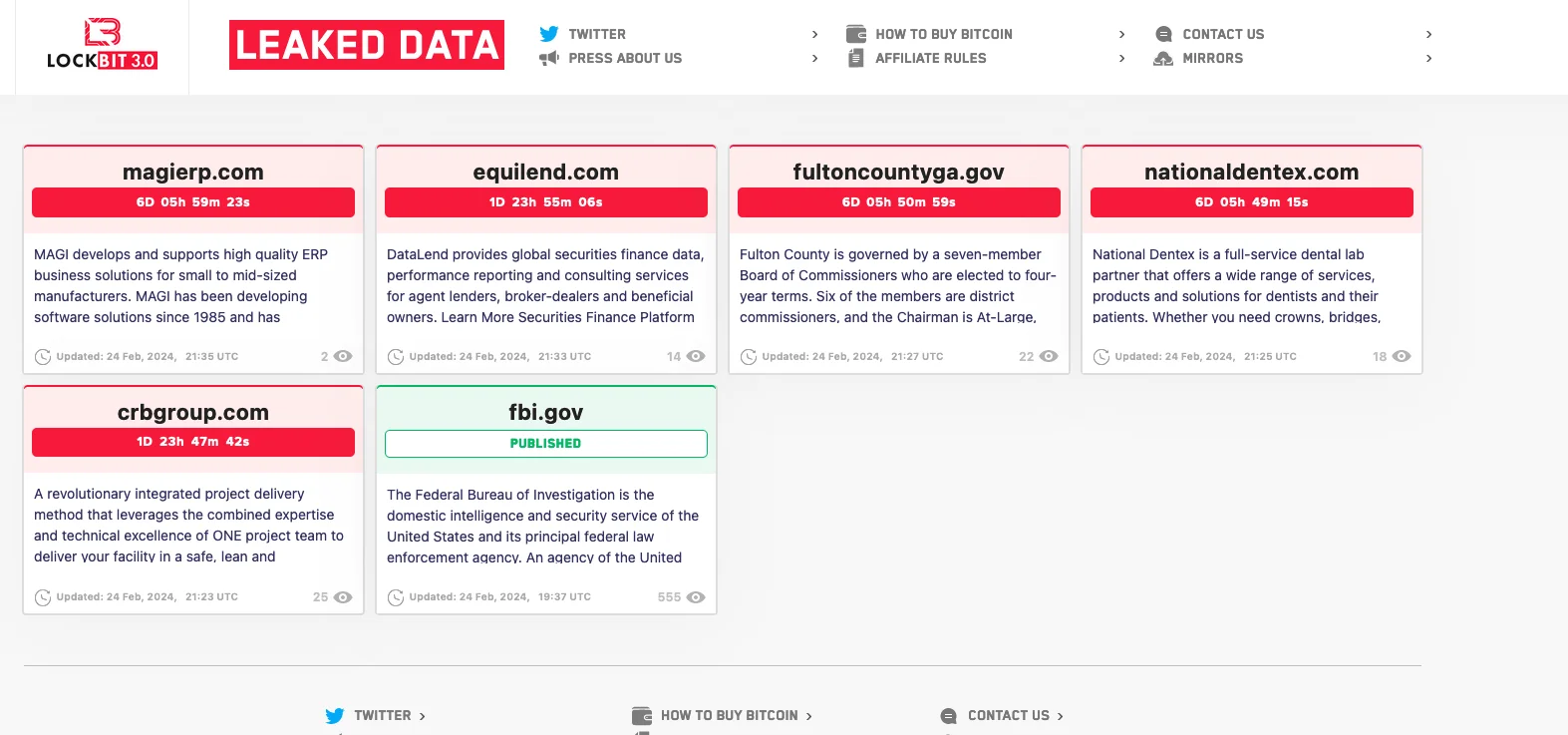
LockBit’s new data leak site
They also made a hefty statement about the operation. As we reported before, during Operation Cronos, authorities seized over 1,000 decryption keys. LockBit recently asserted that these keys were acquired from “unprotected decryptors,” comprising nearly 20,000 decryptors on the server out of the total 40,000 generated during the operation’s lifespan. “Unprotected decryptors” are defined as builds of the malware lacking the “maximum decryption protection” feature, typically utilized by low-level affiliates demanding smaller ransoms.
Countdown for the statement below about Operation Cronos
Furthermore, to gain trust once again, LockBit intends to bolster its infrastructure security by manually releasing decryptors, conducting trial file decryptions, and hosting the affiliate panel across multiple servers. Partners will access different copies based on their trust level. According to LockBit, these measures, along with panel separation and enhanced decentralization, will significantly diminish the risk of hacking.
The full statement as follows:
Speculations
LockBit speculated that other Ransomware-as-a-Service (RaaS) groups, like their competitors, might have had similar compromises to their systems, but haven’t found out yet. They also speculate the FBI’s strong response might be because of a recent attack by one of their partners, which allegedly had sensitive info about Donald Trump. Lastly, they suggest their partners to target government organizations more to show their vulnerabilities, similar to ALPHV’s move after the operation that targeted their infrastructure.
Following the operation against Hive, it became evident that the group’s operations were disrupted. However, the emergence of Hunters International shortly after appeared to be a rebranding of Hive. In the case of ALPHV, although significant damage was inflicted on the ransomware group, its activities have been somewhat curtailed but continue nonetheless. The situation mirrors what is now unfolding with LockBit. Despite the efficacy of the operations conducted against these criminal entities, they persist in their activities unless completely eradicated.
As these groups lift constraints on their affiliates, they also incentivize them to target more critical sectors, thereby escalating the risk of exposing sensitive data. Recent events, such as the I-SOON leaks involving government-related organizations, underscore the potential magnitude of such breaches. Moreover, it seems that ransomware groups are not operating in isolation
In light of Julian Assange’s extradition appeal, a new group, WikiLeaksV2, has emerged to express support for him and the original WikiLeaks mission. Bearing a resemblance to its predecessor, WikiLeaksV2 features sections dedicated to healthcare, facilitates donations, and accepts data submissions. The group claims access to significant data and offers contact information for law enforcement and legal entities. Notably, WikiLeaksV2 has disclosed data from healthcare and corporate entities, potentially obtained from ransomware groups.
Despite maintaining a limited presence on social media platforms, WikiLeaksV2 appears focused on advocating for Assange’s cause, albeit primarily through republishing data already leaked by ransomware groups. The group’s future actions as Assange’s case unfolds remain uncertain, raising the possibility of ransomware groups seeking revenge through this avenue.
LockBit’s Many Bluffs
In an unexpected turn of events following the fervor sparked by FBI emails brimming with outlandish conspiracy theories regarding a hack on a US government website, LockBit’s proclamation of triumph has been definitively debunked. Fulton County officials refute any suggestion of ransom payment, directly contradicting LockBit’s assertions.
LockBit’s claim of success hinged on the alleged deletion of data, a claim swiftly dismissed by Fulton County officials who maintain no ransom was ever paid. It appears LockBit sought to salvage its reputation following a downturn in fortunes.
LockBit also listed nearly 30 victims, including Boeing again. However many purported victims showcased on LockBit’s website have vanished, casting doubt on the authenticity of their accounts. Furthermore, the recent new victims of LockBit have been old incidents, and only 6 of them are new, exposing their attempt to feign a resurgence.
Once a formidable presence, LockBit now finds itself in dire straits. Each desperate maneuver they undertake only exacerbates their predicament. Despite their efforts to project success, affiliates’ trust in LockBit continues to erode.
LockBit’s Seized Leak Site Resurfaces
The LockBit ransomware group’s seized leak site, which was previously shut down, is now back online, surprising everyone in cybersecurity. People are eager to find out who LockBitSupp is, as the countdown to reveal their identity gets closer to zero.
The lock on LockBit’s leak site, which was put there during Operation Cronos, has been removed mysteriously. Many speculate about what this could mean, especially with LockBitSupp’s identity about to be revealed.
The current seized leak site
Maybe, LockBitSupp won’t be anonymous much longer, as a timer is counting down to when their identity will be disclosed. Everyone in cybersecurity is excited and curious about what will happen when the clock reaches 2024-05-07 14:00:00 UTC, expecting big news.
The Man Behind the LockBit Ransomware Has Been Identified
The countdown clock hit zero, now we know who LockbitSupp is. The FBI, UK National Crime Agency, and Europol have announced extensive indictments and sanctions against the administrator of the LockBit ransomware operation, disclosing the identity of the Russian threat actor for the first time.

Who is LockbitSupp again?
The individual allegedly responsible for developing and operating the most prolific ransomware variant known as “LockBit” and “LockBitSupp” has been identified as Dimitry Yuryevich Khoroshev, also known as “putinkrab.” He is 31 years old and from Voronezh, Russia. The U.S. State Department is offering a reward of up to $10 million for information leading to his capture, and the U.S. Department of Treasury has designated him for sanctions. Khoroshev faces a 26-count indictment from a grand jury in the District of New Jersey.

Reward of up to 10,000,000$ for Dimitry Yuryevich Khoroshev
“The Russian national who serves as both the administrator and developer of LockBit is now facing asset freezes and travel bans, as declared by the UK Foreign, Commonwealth and Development Office, in addition to the actions taken by the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) and the Australian Department of Foreign Affairs and Trade,” as stated in a Europol announcement.
These sanctions are poised to significantly disrupt the operation, as paying a ransom might violate these sanctions and result in hefty government fines for companies involved. Moreover, all affiliates have been revealed, including their surnames this time. Has another criminal network been rooted out? We shall see.
For further details please refer to the press release of the US Department of Justice.
FBI Offers +7,000 LockBit Decryption Keys to Ransomware Victims
The FBI has successfully acquired over 7,000 decryption keys from the notorious LockBit ransomware group and is now calling on affected entities to step forward to reclaim their data.
This announcement was made by FBI Cyber Division Assistant Director Bryan Vorndran during his keynote address at the 2024 Boston Conference on Cyber Security, in which he emphasized the importance of victims reaching out to retrieve their keys, which could significantly aid in their recovery process, avoiding the hefty ransoms typically demanded by LockBit.

Tweet by FBI Boston (X)
Having faced extensive law enforcement actions to neutralize its operations, LockBit continues to adapt, migrating to new servers and maintaining its dark web presence. The ransomware group has responded to these crackdowns by intensifying its attacks and leaking vast quantities of stolen data, and remains one of the most active ransomware operations.
The release of these decryption keys offers a lifeline to organizations previously victimized by LockBit. The FBI urges any entities that suspect they have been impacted by LockBit ransomware to contact them via the Internet Crime Complaint Center, ic3.gov, to recover their data without succumbing to ransom demands.
New Arrests and Infrastructure Seizures
As of Monday, the United States Federal Bureau of Investigation (FBI) and the United Kingdom National Crime Agency (NCA) have made further strides against the LockBit ransomware group, marking significant progress in Operation Cronos. New arrests of LockBit affiliates have been reported, accompanied by additional infrastructure takedowns. This continued offensive follows the initial blows dealt in previous stages of the operation, where law enforcement crippled key components of LockBit’s network.
LockBit’s seized website (vx-underground)
Despite LockBit’s notorious resilience, the coordinated international pressure signals a sustained commitment to dismantling the group’s operations. These recent actions highlight the effectiveness of global cooperation in cybersecurity enforcement.