ALPHV Seized, Unseized, Decrypted; Pandora’s Box May Be Reopened
Emerging as a significant player in the ransomware landscape, ALPHV (BlackCat) has established itself through sophisticated ransomware attacks. Utilizing advanced techniques and targeting a wide range of industries, including critical infrastructure, this group has demonstrated a capacity for causing widespread disruption. Recently, they have been filling the headlines with unusual operational approaches.
They are now experiencing the consequences of being extraordinary. ALPHV’s operations, marked by a Ransomware-as-a-Service model, have seen them involved in significant global attacks, making them a focus of international law enforcement agencies.
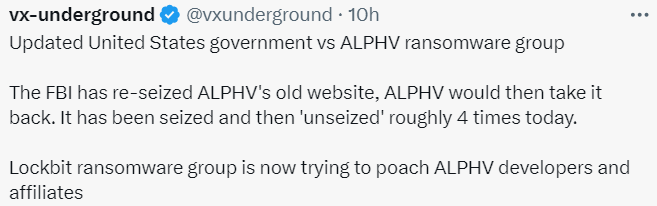
In our latest update on ALPHV, we covered the complex sequence of events surrounding its possible takedown. Recently, law enforcement indeed seized a domain of ALPHV, but the group resiliently unseized its domain for a time. Amidst these fluctuations, authorities released a decryption tool, while ALPHV threatened to escalate attacks on critical sectors. Concurrently, other ransomware groups are chasing ALPHV affiliates amidst growing concerns in both cybersecurity and cybercriminal communities. This intricate scenario presents a multifaceted view of the ongoing cyber struggle. For a detailed exploration, let’s delve into the whole story.
Timeline of Recent Events Regarding ALPHV
Takedown Claims
On December 7, ALPHV’s leak site went offline, sparking rumors of a law enforcement operation against their websites. Although ALPHV’s admin suggested that the sites would resume operation soon, they remained inaccessible. RedSense Intel confirmed this downtime was due to law enforcement action. There were indications that the FBI might be involved, similar to previous disruptions targeting ransomware groups.
Initial FBI Seizure
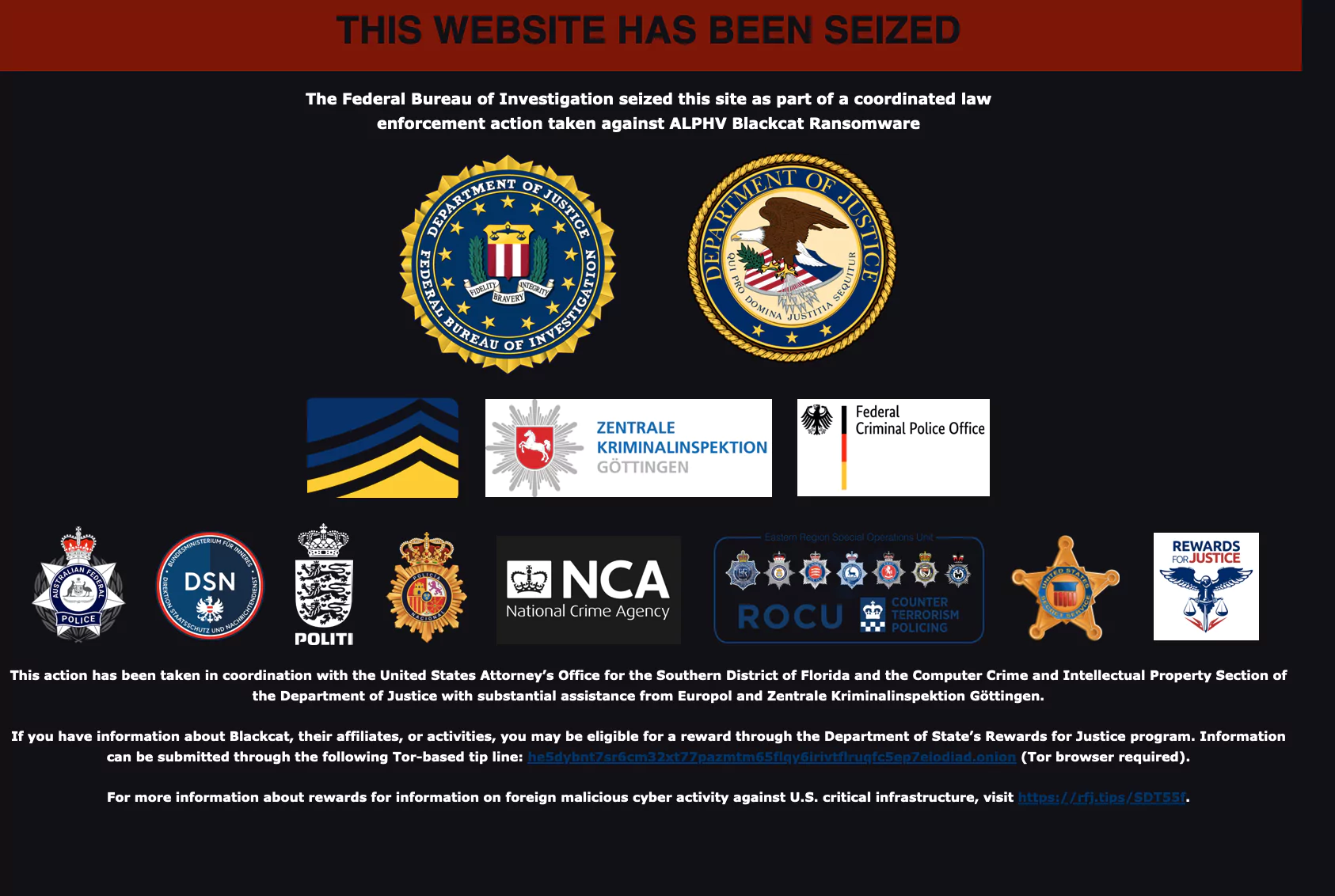
On 19 December, the first visible move against ALPHV/BlackCat came from the FBI, in a coordinated effort with international law enforcement, seized the group’s website and shared the known seizure poster on the leak site. This action marked a critical step in disrupting the operations of one of the most prolific ransomware groups.
ALPHV’s Countermove
On the same day, in a surprising turn, ALPHV regained control of their site temporarily. This bold move was displayed when their dark web site reappeared with a defiant message, challenging the authority of law enforcement despite stating that this is the old domain and it doesn’t matter.

FBI and ALPHV’s Mutual Retaliation
The seizure and re-seizure of the website occurred multiple times, illustrating a mutual retaliation. Each seizure by the FBI was met with a resilient response from ALPHV, who managed to “unseize” their site several times.
Again, before the end of December 19, the FBI shared its official statement document and said that it shared decryptors with the relevant victims. Meanwhile, ALPHV responded aggressively, removing restrictions on ransomware deployment and encouraging affiliates to launch unrestricted attacks; groups working with the RaaS model could set certain sets of rules for their affiliates and impose various prohibitions, such as targeting certain sectors or government institutions.
This move, akin to opening Pandora’s box, contrasted with the FBI’s efforts to contain the box, symbolizing different approaches to the same narrative.
LockBit’s Opportunistic Involvement
Amidst this chaos, the LockBit ransomware group saw an opportunity. They attempted to recruit ALPHV’s developers and affiliates, demonstrating the dynamic and opportunistic nature of cybercriminal networks.
Although they had made similar calls before, this time, they made this announcement at a much more practical time. However, another question that comes to mind is that the call to ALPHV’s affiliates they recently renewed seems that LockBit may have foreseen that ALPHV would get into trouble.
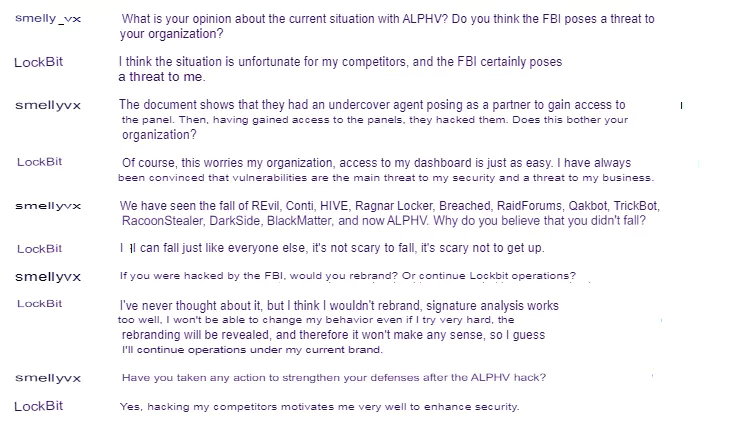
In LockBit’s interview with vx-underground about the current event, they also stated that they see danger for themselves as well.
These events unfolded rapidly, highlighting the complexity and challenges in the ongoing battle against cybercrime. The resilience and tactics of ALPHV, coupled with the determined efforts of law enforcement agencies, paint a vivid picture of the high-stakes environment that defines modern cybersecurity.
Insights and Analysis
Law Enforcement Strategies
In the FBI’s operation against ALPHV/BlackCat, a confidential source within the group granted the FBI access to their internal systems. This access allowed the FBI to retrieve critical decryption keys, leading to the development of a decryptor tool that helped numerous victims. Additionally, the FBI gained control of the group’s online infrastructure, significantly disrupting their operations.
The concerted effort of the FBI, alongside international agencies, demonstrates an evolving strategy in combating ransomware. The use of confidential sources and deep infiltration into the ransomware group’s network indicates a sophisticated approach to cybercrime investigation.
Do not forget to review the official documents for detailed information about the operation.
Impacts on the Threat Landscape
ALPHV’s attacks have been far-reaching, targeting over 1,000 entities globally, including those within critical U.S. infrastructure. The disruption and extortion caused by these attacks underline the serious consequences of ransomware on both a corporate and societal level.
In addition, as much as the group itself, its affiliates were groups that were at least as dangerous as BlackCat and posed a major cyber threat on their own. In the coming days, they may focus on other ransomware alternatives and we may watch LockBit’s popularity increase.
Cybersecurity Implications
While law enforcement agencies have shown remarkable adaptability and coordination, the resilience of groups like ALPHV presents a formidable challenge. These events highlight the need for continuous evolution in cybersecurity strategies and cooperation. The fluctuating control over ALPHV’s website symbolizes not just a single victory or setback but the ongoing, dynamic struggle in the digital realm between law enforcement and cybercriminals.
In this context, it is essential to approach the ransomware threat, which stands out even among all cyber threats, with proactive solutions. The Ransomware Check feature within SOCRadar Attack Surface Management addresses exactly this problem. It helps you identify your vulnerable points before attacks occur and prevent intrusions.