Mutation Effect of Babuk Code Leakage: New Ransomware Variants
Ransomware continues to be a significant concern for individuals and organizations alike. One particular ransomware group, Babuk, made headlines in 2021 due to the leakage of its source code. This event has led to the emergence of new ransomware variants, demonstrating the mutation effect that occurs when malicious code falls into the wrong hands.
Babuk is a ransomware group that first appeared in early 2021. Initially, the group gained notoriety for targeting corporate networks and extorting victims by encrypting their files. However, in April 2021, Babuk’s source code was leaked, allowing other cyber criminals to modify and repurpose it for their malicious activities.
Emergence of New Ransomware Variants
The leakage of Babuk’s source code has triggered a phenomenon known as the “mutation effect.” This term refers to the ability of cybercriminals to adapt and modify existing malware code to create new strains of ransomware. Various cybercriminal groups have capitalized on the opportunity to develop their variants based on Babuk’s leaked code, resulting in a proliferation of new ransomware strains.
The mutation effect has enabled the customization of ransomware variants, allowing threat actors to tailor their attacks to specific targets or sectors. By modifying the leaked Babuk code, cybercriminals introduced new features, evasion techniques, or encryption algorithms to enhance the potency and stealth of their ransomware strains. This customization has made it more challenging for security researchers and organizations to detect and defend against these evolving threats.
RA Group and its Custom Take on Babuk
One notable active group that has emerged in the wake of the Babuk code leakage is the RA Group. Leveraging the exposed source code, the RA Group has developed its custom variant of the Babuk ransomware. This customization allows the RA Group to differentiate its operations and tailor its attacks to specific targets or sectors.
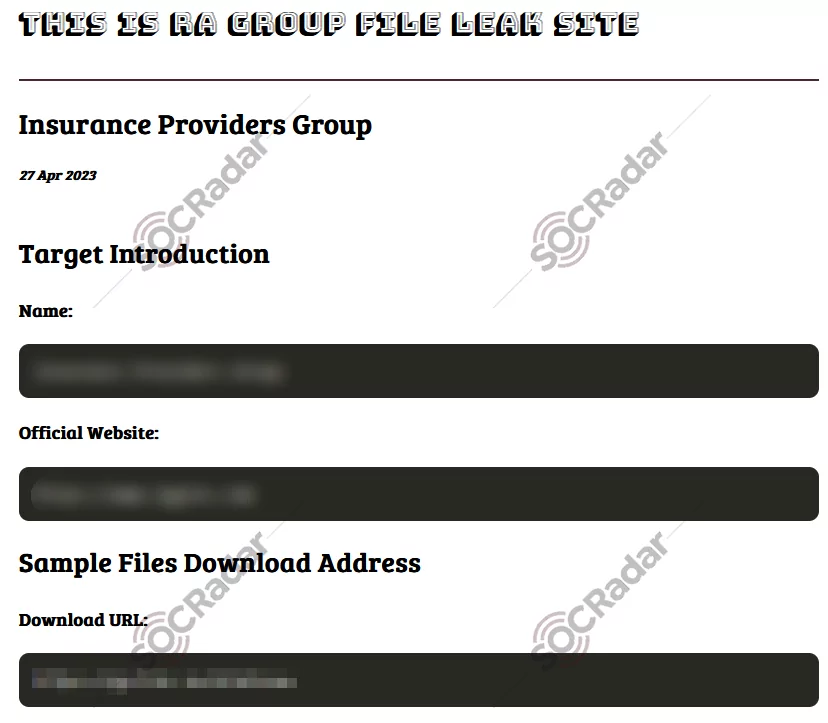
With their custom take on Babuk, the RA Group introduces unique characteristics and modifications to the ransomware. These alterations could include changes to the encryption algorithms, evasion techniques, or even the overall attack methodology. Such customization enhances the potency and stealth of the RA Group’s ransomware strain, making it more difficult for security researchers and organizations to detect and defend against, and the RA Group’s custom variant of Babuk serves as a prime example of how threat actors can exploit leaked code to create their own specialized ransomware strains. It demonstrates their ability to adapt and evolve, constantly refining their techniques to maximize the impact and profitability of their attacks.
In addition to the RA Group, several other active cybercriminal groups have seized the opportunity presented by the leaked Babuk source code in the last one and a half years, leading to a surge in new and customized ransomware variants. The recently surfaced reports reveal that nine new ransomware strains have emerged due to code leakage, each developed by different groups with innovative approaches. These groups, leveraging the exposed source code, have utilized the foundational Babuk code as a starting point to craft their distinct ransomware strains and have introduced unique characteristics and alterations to the original Babuk ransomware by modifying key code elements.
Ransomware strains that originated from Babuk:
- Cylance
- Rorschach
- RTM Locker
- LOCK4
- DATAF
- Mario
- Play
- XVGV
The customization efforts undertaken by these groups go beyond simple cosmetic changes. They delve into critical aspects such as encryption algorithms, evasion techniques, and attack methodologies. These modifications enhance the potency and stealth of the customized ransomware strains, posing significant challenges for security researchers and organizations seeking to detect and defend against these evolving threats.
Buhti: Another New Ransomware Operator
Buhti, a relatively new ransomware operator, has adopted a distinctive strategy by utilizing rebranded versions of leaked LockBit and Babuk ransomware payloads. Instead of creating their ransomware from scratch, Buhti leverages modified variants of these established ransomware families to target both Windows and Linux systems.
While Buhti relies on existing ransomware strains, they have integrated a custom-developed tool into their arsenal. This information stealer tool is specifically designed to locate and retrieve specific file types, augmenting the group’s data exfiltration capabilities.
Initially, Buhti gained prominence for its focus on targeting Linux computers when it emerged in February 2023. However, recent findings from security researchers indicate that Buhti has expanded its operations to include attempts to compromise Windows systems within compromised networks, suggesting a more comprehensive range of targeted platforms.
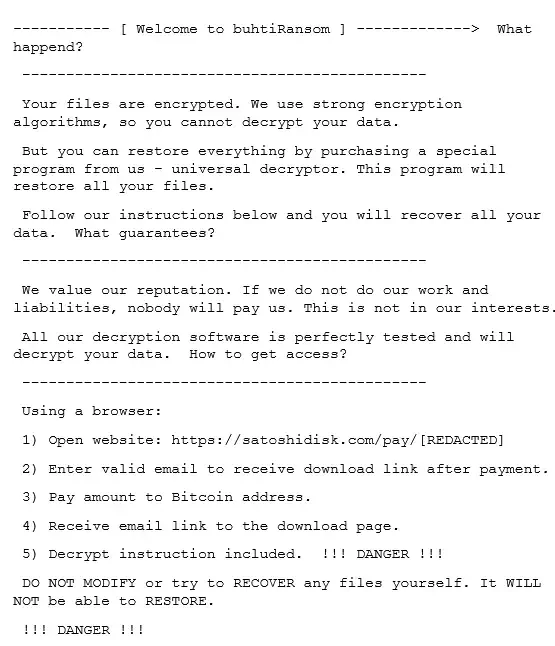
One notable characteristic of the Buhti group is their agility in exploiting recently disclosed vulnerabilities. In a recent attack, they took advantage of a recently patched vulnerability in PaperCut, demonstrating their ability to quickly adapt and capitalize on new security weaknesses. In short, using rebranded ransomware variants, their custom information-stealing tool and agility in exploiting vulnerabilities signifies Buhti’s unique operational approach.
The Implications for Security and Defense
As we discussed, the leakage of Babuk’s source code has created a ripple effect, leading to the emergence of new and more sophisticated ransomware variants. This mutation effect highlights the adaptability and creativity of cybercriminals who can take advantage of leaked code to develop customized malware strains. As the threat landscape evolves, organizations must remain resilient and implement robust security strategies to counter the growing menace of ransomware attacks.
The mutation effect resulting from the Babuk code leakage emphasizes the need for constant vigilance and proactive security measures. Organizations must stay updated on the latest threat intelligence, employ robust cybersecurity solutions, and adopt best practices to mitigate the risk of falling victim to these evolving ransomware strains. Collaboration between security vendors, researchers, and law enforcement agencies becomes even more critical to address the emerging challenges of mutated ransomware variants.
Ransomware operators like Babuk commonly employ phishing campaigns as a primary method to gain initial access for launching their attacks. To counteract this, organizations can leverage SOCRadar’s Digital Risk Protection solution, which acts proactively to block potential phishing campaigns that impersonate the organization’s domains, thereby safeguarding their brand integrity.
While maintaining offline backups is a crucial step in preventing ransomware attacks, it’s important to note that some ransomware groups, including RA, adopt a double extortion strategy. This involves stealing the victim’s data before encrypting it, rendering offline backups inadequate for circumventing ransom payments. To address this challenge, organizations need to be vigilant about potential vulnerabilities within their environment. SOCRadar’s Attack Surface Management provides a solution by offering visibility into external-facing digital assets, empowering security teams to identify and track vulnerabilities effectively. This proactive approach helps organizations limit the attack surface that ransomware operators may exploit, bolstering their defense against evolving threats.