New Rorschach Ransomware: The Fastest Encryptor
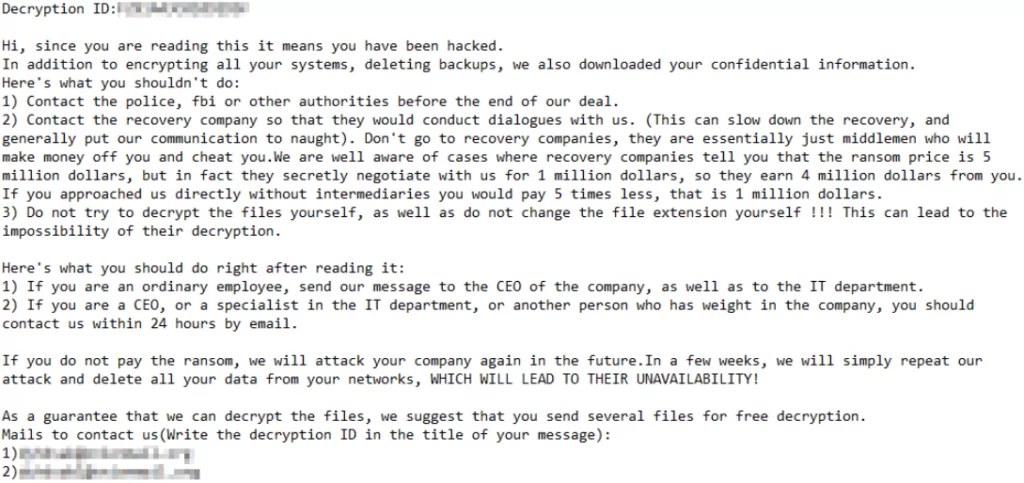
Researchers have discovered a new ransomware strain called Rorschach. This sophisticated and fast form of malware was used to target a company based in the United States.
Rorschach is also among the fastest ransomware ever seen in terms of encryption speed due to its different implementation techniques.
The ransomware is easily customizable. Some other ransomware families also provide this feature; ransomware operators can use optional arguments to modify the ransomware’s behavior to suit their needs. It also has some unique features that are uncommon in ransomware, like the use of direct syscalls.
What sets Rorschach further apart from most other ransomware threats is that it does not have any alternative names. The ransomware looks unique as it cannot be easily associated with known ransomware strains.
How Is Rorschach Similar to Other Ransomware?
Researchers named the new ransomware Rorschach to reference how each person examined it differently. Although it cannot be directly affiliated, the Rorschach ransomware shares some similarities with other ransomware’s behavior:
- The ransomware can automatically copy itself after its execution on a domain controller (DC), so it is partly autonomous. It can also delete event logs after a successful compromise. LockBit 2.0 was previously linked to similar functionality.
- Rorschach’s ransomware note has a similar format to Yanluowang‘s, though other variants used a note resembling DarkSide ransom notes.
- The ransomware uses a hybrid cryptography scheme, which is similar to the source code of Babuk Ransomware. It encrypts the files partially by combining the curve25519 and eSTREAM cipher hc-128 algorithms, significantly increasing encryption speed. According to the researchers, Rorschach’s encryption routine demonstrates a highly effective implementation of thread scheduling via I/O completion ports.
How Did the Attack Happen?
To deploy the Rorschach ransomware, the attacker utilized version 7.3.0.16740 of the Cortex XDR Dump Service Tool (cy[.]exe). They used this tool to sideload the Rorschach loader and injector (winutils[.]dll). This allowed the attacker to launch the ransomware payload called “config[.]ini” into a Notepad process.
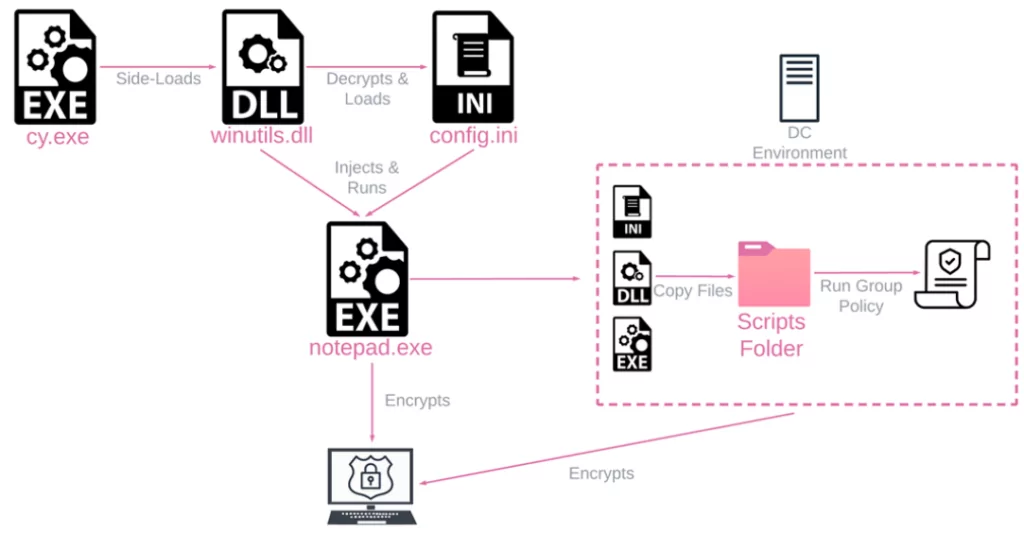
The loader file includes UPX-style anti-analysis protection. On the other hand, the main payload is safeguarded against reverse engineering and detection. This is achieved by virtualizing parts of the code using the VMProtect software.
Once the Rorschach ransomware is executed on a Windows Domain Controller, it automatically generates a Group Policy and replicates itself to the %Public% folder of other devices within the domain.
The ransomware also creates another group policy to terminate specific processes by scheduling a task to run taskkill[.]exe.
Lastly, Rorschach creates a final group policy that registers a scheduled task to run the ransomware’s main executable with the relevant arguments immediately upon user logon.
Once it successfully infiltrates a system, Rorschach removes event logs from the Application, Security, System, and Windows PowerShell.
The ransomware also stops various services, deletes system backups, and disables the Windows firewall to evade detection by running processes in SUSPEND mode, which results in falsified arguments.
Although Rorschach has a hardcoded configuration, it also allows using command-line arguments to enhance its capabilities. However, researchers stated that these options are concealed and cannot be accessed without reverse engineering.
Also, it is worth noting that Rorschach will only begin encrypting data if the target device is set to a language that is not part of the Commonwealth of Independent States (CIS).
Rorschach Ransomware IOCs
The indicators of compromise include the files used in the execution of the Rorschach ransomware:
Cy[.]exe (PA Cortex Dump Service Tool)
Hash:2237ec542cdcd3eb656e86e43b461cd1
Winutils.dll (Loader and injector into notepad[.]exe)
Hash: 4a03423c77fe2c8d979caca58a64ad6c
Config.ini (Encrypted ransomware payload)
Hash: 6bd96d06cd7c4b084fe9346e55a81cf9
For the list of interfered processes, hardcoded configuration, and group policies, see here.
Find Threats and IOCs on SOCRadar
SOCRadar monitors the activity of threat actors and malware to provide you with the critical information you need to safeguard your organization against them. The Threat Actor/Malware tab contains the most recent information on threat activities and indicators of compromise.
SOCRadar also offers a Threat Feed/IOC service to update you on emerging trends through easily customizable collections.