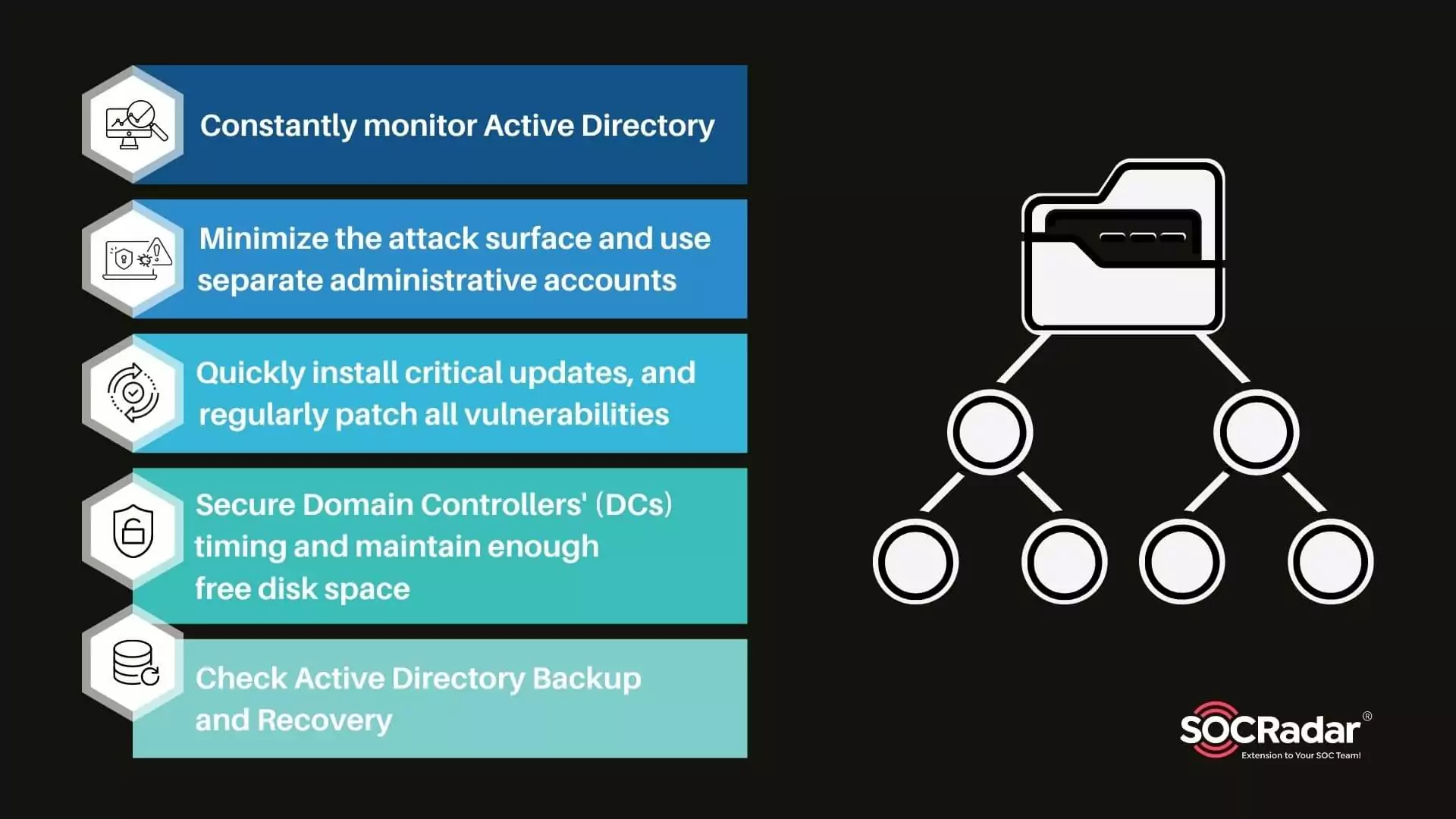
Security for Active Directory in 5 Steps
Microsoft Windows directory service Active Directory (AD) enables IT administrators to manage permissions and restrict access to network resources.
With this identity and access management solution, you can specify who has access to what parts of your network. Active Directory is used by businesses to manage their networks effectively.
Data is stored in Active Directory as objects, which can be users, groups, applications, or devices. These objects are categorized based on their name and attributes.
Once configured, Active Directory has a backup and recovery feature that enables you to restore data when required.
Standard users can access any Active Directory object authorized for the Domain Users group. Additionally, the Domain Admins group’s members are a powerful group in the network and have access to many privileged functions.
If an attacker gains access to Active Directory as a privileged user or manages to increase their privilege, they have complete control over the organization. Once they have access to all user identities, an attacker can remain undetected for days, months, or even years in some cases.
The organization could suffer a sizable loss of revenue if the attacker managed to collapse the Active Directory completely. IT admins can secure Active Directory environments within a company by following these steps:
1. Constantly monitor Active Directory
You should monitor Active Directory changes regularly to help ensure that no unauthorized changes that might harm the organization are missed. You can use alerts and reports to monitor Active Directory continuously.
The sooner you identify and correct such changes, the lower the risk of a breach. Manage account lockouts and send password expiration and other useful notifications to achieve that.
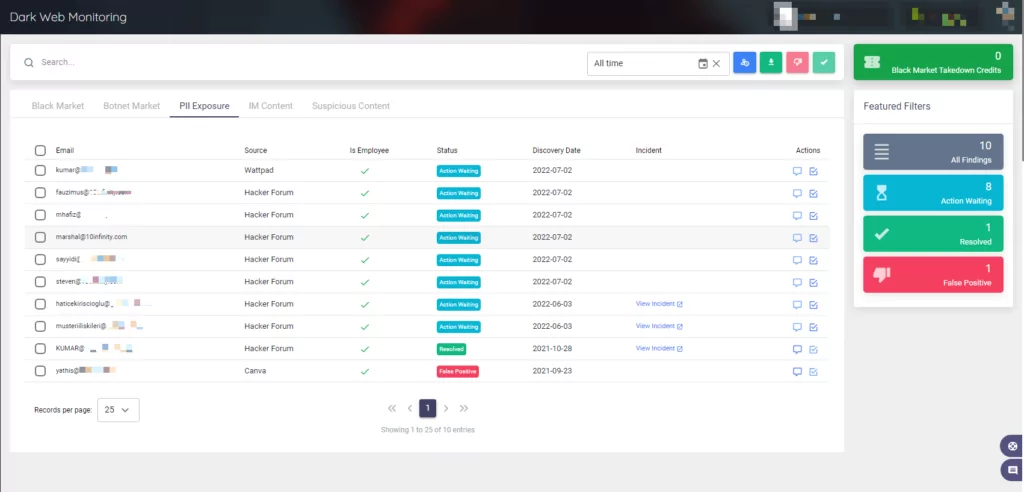
SOCRadar will immediately notify you if information about your employees, VIPs, and customers is exposed in hacker forums and combo lists.
You can use the customer, employee, and VIP filtering options in the Leak API we provide to feed your various Active Directory structures.
On the SOCRadar Platform, you can access this information in the Dark Web Monitoring section under Digital Risk Protection.
These are some of the things you should be looking over and monitoring each week:
- Every action carried out by privileged accounts
- Modifications to privileged groups like Enterprise Admins, Schema Admins, and Domain Admins
- An increase in unsuccessful password attempts and locked-out accounts
- Removal or disablement of antivirus software
How can Active Directory events be monitored?
The ideal approach involves gathering all the logs on a centralized server and using log analysis software to produce reports.
There are several ways to collect, analyze, and centrally store all your Active Directory security event logs. You can also use them to start an automated action to stop or fix a security incident.
You can quickly identify suspicious activity in your Active Directory environment with the help of a good log analyzer.
The most popular log analyzers are listed below:
- ManageEngine ADAudit Plus
- Windows Event Forwarding
- Elk Stack
- Lepid
- Splunk
For more information, you can visit Microsoft’s Monitoring Active Directory for Signs of Compromise support page. For a complete list of event IDs to monitor, see Microsoft’s Events to Monitor information page as well.
2. Minimize the attack surface and use separate administrative accounts
Reduce the attack surface of Active Directory by using the least access privilege model, protecting administrative hosts, Domain Controllers (DCs), privileged accounts, and other resources. According to the principle of least privilege (POLP), each user, service, and application should only be given the permissions necessary to carry out their tasks.
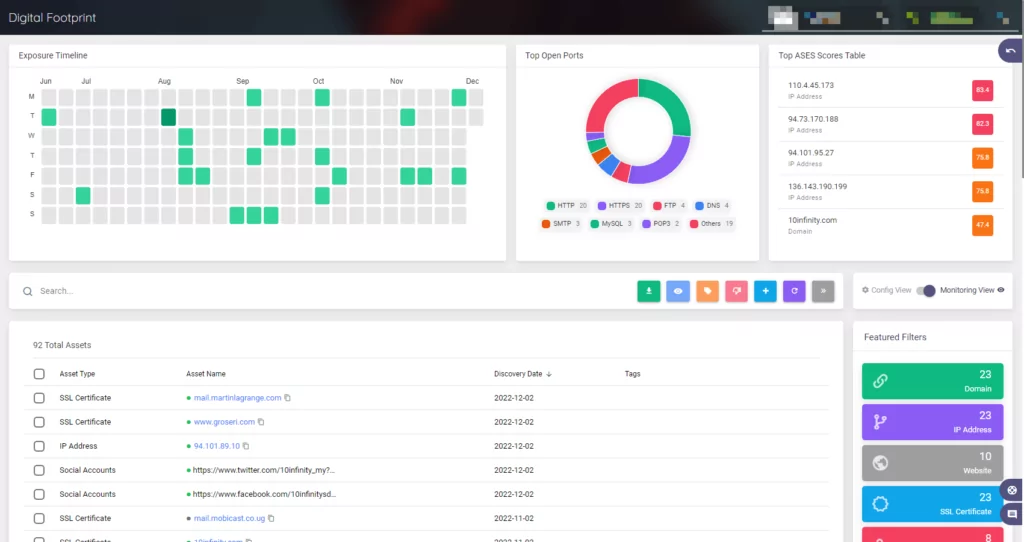
Customers can automatically gain more visibility and context about the seriousness of unidentified external-facing digital assets with the help of our external attack surface management solution, AttackMapper.
You can easily manage the security of your domain with the help of Group Policy. You can implement these policies in phases, linking them first to specific OUs and then, if necessary, to the entire domain.
Create an Active Directory solution using multiple Group Policy Objects to give users restricted access without making them Domain Admins.
The next step is ensuring all privileged users use separate administrative accounts. To recognize these accounts easily, they should have different naming systems.
To apply specific GP (Group Policy) settings to them, they should also be organized into categories and kept in separate OUs (Organizational Units).
The risk is much higher if an administrator unintentionally gets malware on their computer because viruses with administrative rights can run programs or scripts.
As a result, administrators should carry out privileged AD tasks using a separate administrative account and a nonprivileged account (such as a user account) for general use.
3. Quickly install critical updates and regularly patch all vulnerabilities
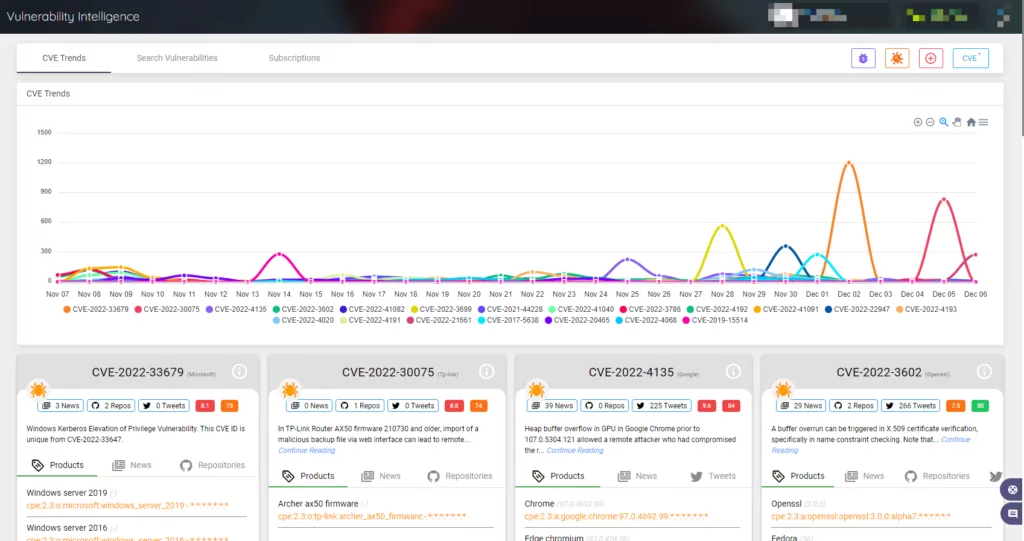
One of the key responsibilities of the IT department is finding and fixing vulnerabilities. You must closely monitor any security updates that are released. At least once a month, scan all systems to find any potential vulnerabilities.
Threat actors are closely watching vulnerability trends as well as your technology and services that are accessible to the general public to find the easiest way in.
Receive notifications with SOCRadar whenever there is a new critical vulnerability or exploit for the pre-defined product components and technologies connected to your digital footprint to avoid them disrupting your business.
Automatic Updates allow immediate security update installation, while Microsoft Software Update Services (SUS) allows for testing and selective update installation.
Set fixing the vulnerabilities discovered by vulnerability scans as a top priority, starting with the ones that have been identified as being in use.
The outdated software that is no longer supported should be located and updated. Additionally, automatic updates for third-party software and operating systems are advised.
4. Secure Domain Controllers’ (DCs) timing and maintain enough free disk space
Keep roles and software installations on domain controllers to a minimum. Enterprises rely heavily on DCs, so adding more software increases their security risk.
The DC role and other roles like DHCP, DNS, print servers, and file servers can all be run on Windows Server Core, which is a great option. Due to its smaller footprint, Server Core requires fewer security updates and doesn’t have a graphical user interface. However, some third-party software incompatible with the server core can cause difficulties.
Denial of service attacks can fill up the available disk space with needless files, eventually bringing down the DC. You can prevent this by regularly checking the available disk space and deleting the extra files.
Domain controllers automatically use the primary domain controller (PDC) in the root domain to run with accurate time. Work on protecting the PDC’s time source to make sure that all DCs are properly synchronized.
5. Check Active Directory backup and recovery
You should always back up the AD configuration and directory. Practice disaster recovery procedures to enable quick recovery if AD integrity is compromised.
Depending on your current backup solution and how you’ll back up, your DCs may vary. You can back up your Active Directory DCs using the free and effective Windows Server Backup feature. For more information, check Microsoft’s documentation on Windows Server Backup installation.
Don’t just backup one DC; backup all of them. As a result, there is a lower chance that a breach, especially a ransomware attack, will lose your Active Directory database.
Finally, run disaster recovery tests regularly by restoring your Active Directory to ensure that your backups are reliable.
References:
- https://petri.com/active-directory-security-5-steps-to-secure-ad/#5_Harden_domain_controllers_according_to_Microsoft_best_practices
- https://activedirectorypro.com/active-directory-security-best-practices/#monitor-dhcp-logs
- https://www.lepide.com/blog/how-to-ensure-your-active-directory-is-secure/
- https://www.itprotoday.com/active-directory/5-steps-secured-active-directory
- https://www.beyondtrust.com/blog/entry/active-directory-security-explained-7-best-practices
- https://www.manageengine.com/products/ad-manager/what-is-active-directory-and-how-does-it-work.html
- https://www.lepide.com/blog/what-is-active-directory-and-how-does-it-work/



































