
5 Lessons Learned from Ransomware Attacks in 2022
By SOCRadar Research
In 2022, SOCRadar researchers detected over 1700 alleged ransomware victims. The total number was approximately 29% higher than in 2021. According to another research conducted by Verizon in 2022, data breach incidents due to ransomware attacks increased by 13%.
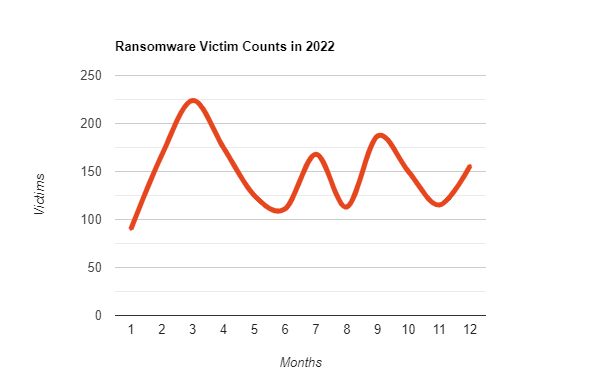
Ransomware attacks have shown a greater growth rate in the past years. Although this rapid growth slowed in 2022, the total number is still increasing. However, even with the decrease in growth rate, ransomware attacks in 2022 targeted the places where they could hurt organizations the most.
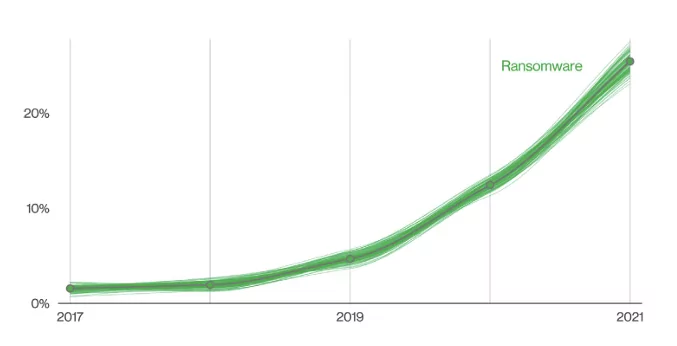
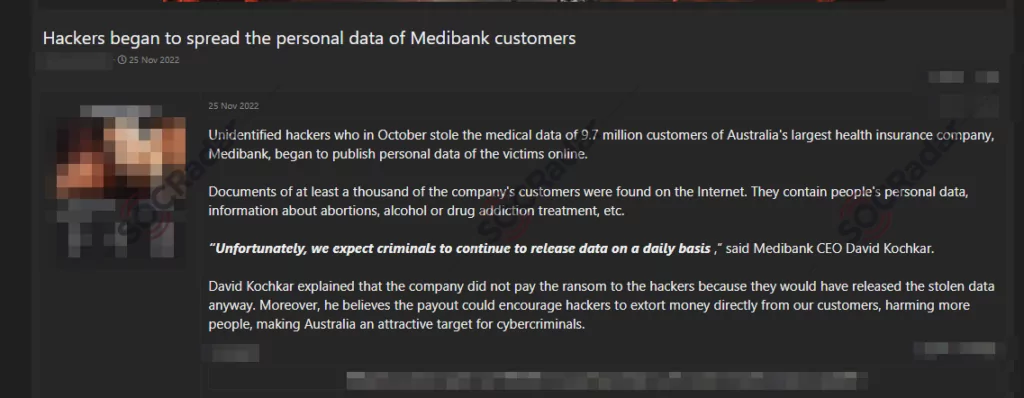
The size and sensitivity levels of the leaked data have increased significantly this year. One of the biggest ransomware attacks of this year was the REvil’s attack on Medibank. In October 2022, the Australian health insurance company Medibank was impacted by ransomware and refused to pay the ransom. This incident, in which the personal data of 9.7 million people and the health information of half a million people were leaked, showed that ransomware attacks pose a greater danger in every respect.
Download SOCRadar’s 2022 End-of-Year Report to gain insights into major ransomware attacks.
Another topic on the rise was the increase in the initial access market by more than %50 from 2021 to 2022. Initial access offered by brokers is usually offered for ransomware groups. Again, the fact that the ransomware groups that emerged in 2022 reached large attack volumes in a short time may also be due to the initial access market’s growth.
The State of Ransomware in 2022
Ransomware attacks continue to increase as we enter 2023. Cybersecurity experts predict this trend to continue over the next year. Since Conti ceased its activities, there has yet to be a clear leader among ransomware groups. However, LockBit was the group that brought this infamous race ahead in 2022. Again in 2022, we witnessed the emergence of new ransomware groups such as Black Basta and Royal Ransomware. When we examine these emerging groups, it can be easily said that they are seasoned threat actors, but their relationship with Conti continues only as an allegation.
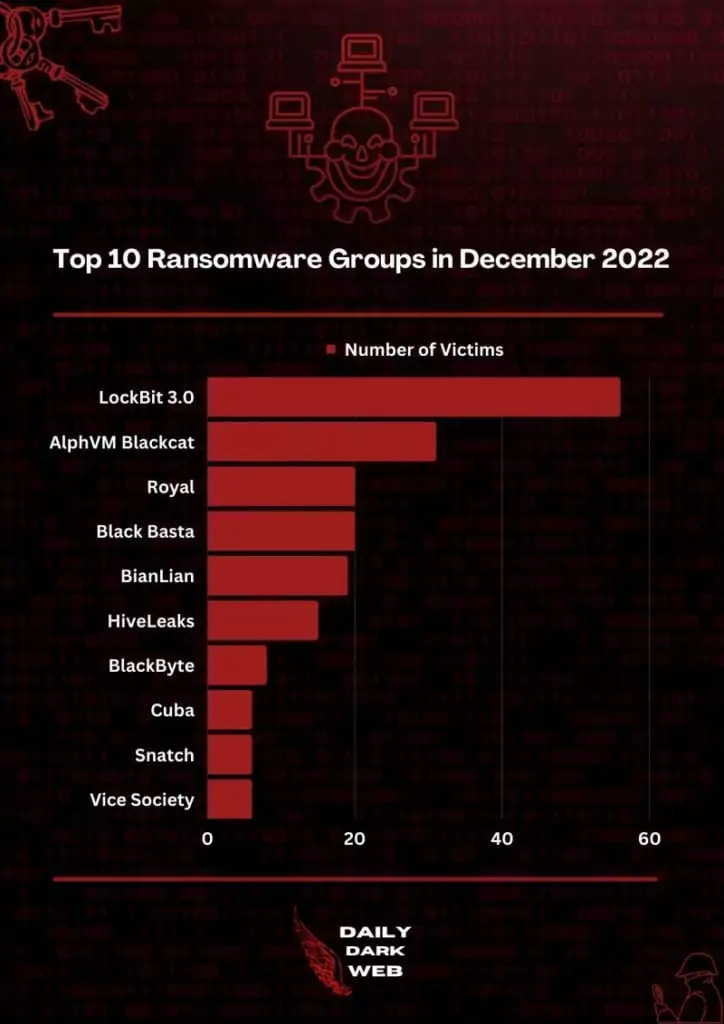
Lesson 1: Although many researchers thought ransomware attacks would decrease when Conti ceased operations, it did not turn out that way. In 2022, when many ransomware groups surfaced, their TTP showed unique features as well as similarities.
One of the unique tactics of Royal Ransomware uses Callback Phishing, one of the recently emerged phishing techniques.
Ransomware is Getting Political
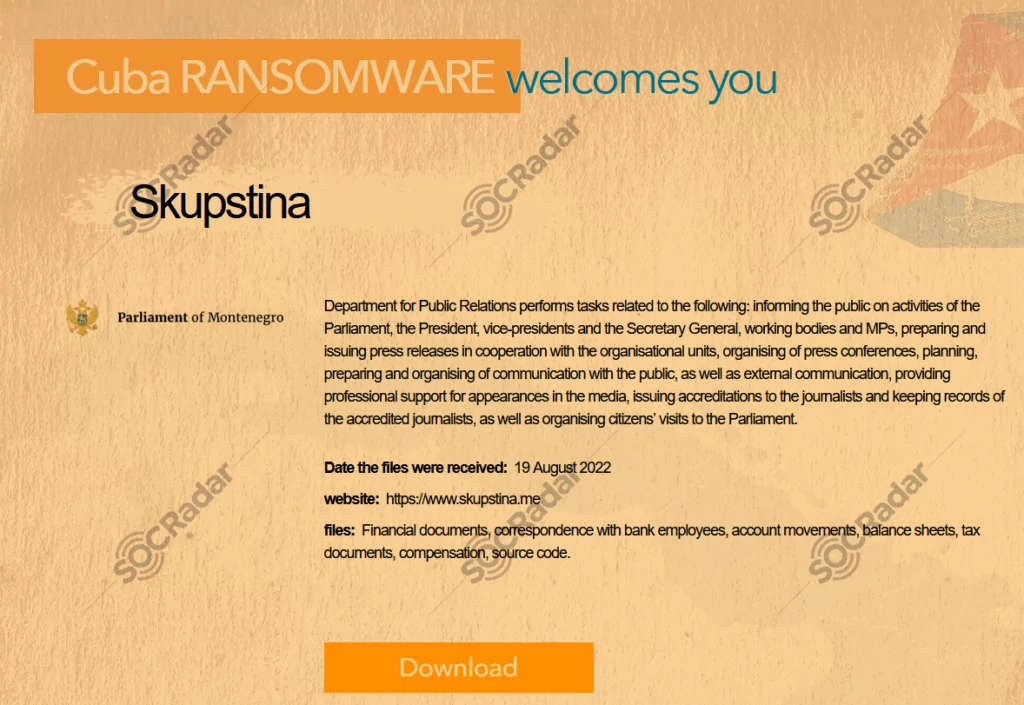
In 2022, we saw ransomware groups pursuing more political goals. Such attacks by Iranian state-affiliated hackers on the Albanian government’s systems, or the Montenegro Parliament’s breach by the Cuba Ransomware group, and Conti’s attack on Costa Rican Government have been political rather than financial. It is also observed that the Russian threat actors are also participating in the cyber war against Ukraine, and this phenomenon can be expected to keep increasing with the continuation of the war in 2023.
Lesson 2: It is clear that ransomware groups are not always only motivated by financial gains. We saw that in 2022, non-profit and governmental organizations could also suffer tremendous damage from such groups. For this reason, these kinds of organizations should also take precautions against these threats.
Ransomware Variants are Increasing
Forti Guard Lab has observed a 100% increase in ransomware variants, with over 10,000 in the first half of 2022 alone. The most common variants in 2022 were in descending order were;
- LockBit 3.0
- Black Basta
- Hive
- ALPHV, aka BlackCat.
Considering that the new strains are not only limited to the threat groups they belong to but some of them are presented as RaaS (ransomware as a service), the existing threat grows even more. Moreover, researchers even encountered ransomware tools distributed on GitHub in 2022.
Lesson 3: The emergence of new and updated variants will complicate signature-based detection. As a solution to this situation, SOC Analysts should be able to follow up-to-date IoCs, and organizations should support their cybersecurity technologies with cyber threat intelligence to adopt a more proactive defensive approach.
Target Industries are Changing
Although it can be interpreted as a case like the politicization of ransomware, there are varied reasons for the change in the targeted industries. Throughout 2022, the manufacturing industry was the most targeted vector, followed by information. The purpose of targeting businesses that provide this critical infrastructure is that downtime is very costly, and they are more likely to pay a ransom.
Healthcare, a crucial industry, has become the victim of these attacks more frequently in 2022. Although the reason for this is that downtime cannot be tolerated in these industries, the data’s sensitivity was also important. The education industry has also risen to the point of organizations targeted for reasons similar to healthcare.
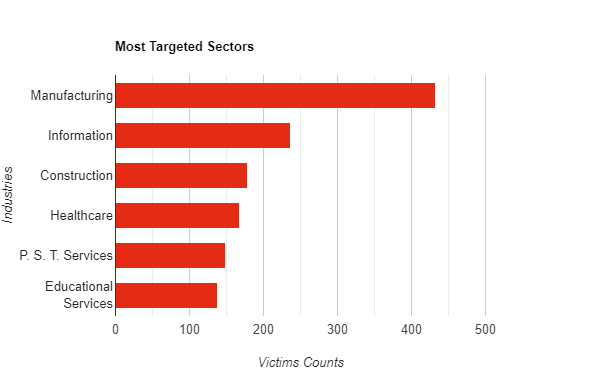
Lesson 4: Although industries where uptime and data sensitivity is critical make relatively less money, they may seem more prone to paying the ransom because they have less tolerance for such attacks. One of the most common security vulnerabilities in industries such as healthcare and education is that the systems are outdated. It may be necessary to regularly update and replace the devices that reached the end of life.
Digital assets also should be tracked by using Extended Attack Surface Management products. In this way, organizations gain views on all known and unknown assets.
All Sizes of Organizations are Under the Threat of Ransomware
Another highlight this year was that ransomware groups attacked medium and small-sized companies more frequently. This situation can be interpreted as the absence of a ransomware group equivalent to Conti. Still, the main point within the working logic of ransomware groups is to achieve maximum profit with minimum effort. Relatively small organizations with loose security measures are ideal targets for threat actors.
Lesson 5: Small and medium-sized enterprises spend less money on cybersecurity measures. As a result, it can cause them to spend much more money in the event of a ransomware attack. It is essential for every organization to meet certain standards in cybersecurity and to detect where attacks may come from to take precautions.
Attacks May Increase in 2023
Ransomware attacks are not always on a steady increase, but they have been on an upward trend since they emerged.
Like the Australian government’s action after Medibank’s breach, many law enforcement agencies are creating solutions such as monetary rewards for any information about threat actors. Such measures can be a blow to these attacks, but there are still essential indications that it may increase.
Topics such as inflation, energy crisis, and food insecurity continue to be on the world agenda because of major geopolitical events such as the Russia-Ukraine war. The economy could therefore play an important role in increasing such attacks. In addition, the increasing attack surface and the way the threat actors work in the ‘as a service’ style are other topics that may cause an increase in 2023.



































