
Diplomatic Crisis: Cyber Attack from Iran to Albania
On September 7, Edi Rama –the Prime Minister of Albania– released a video message on the website of the Government of Albania. According to the video message, Prime Minister Rama requested all diplomatic, technical, and administrative staff working in the Iranian embassy to leave the country within 24 hours due to Albania’s cut diplomatic relations with Iran.
The White House released an assessment that condemned Iran for attacking a NATO ally, Albania, on July 15. Also, the US stated that it stands by its NATO ally. According to Aljazeera’s news article, Iran strongly condemned the decision and rejected Albania’s reasons for the move as “baseless claims.”
In addition to the US and Edi Rama’s explanation, the Iranian government sponsored the actors according to Microsoft Security Threat Intelligence Center (MSTIC) and Microsoft Detection and Response Team’s (DART) investigation.
After these assessments, on September 10, Albania blamed Iran for a second cyber-attack that temporarily forced the Albanian officials to take offline its system for tracking the data entering and leaving Albania, Total Information Management System (TIMS). The attack led to increased border queues and forced some points, such as the Port of Durrës, to manually process the registrations of entries and exits.
Ignition of the Initial Attack
The threat actor’s first attack, sponsored by Iran, occurred on July 15, 2022. This attack may be because Albania was denounced by Iran, allowing the People’s Mojahedin Organization of Iran (Mujahedeen-e-Khalq group) -known by various names such as MEK or PMOI- to take refuge in the country.
Details of the attack on Mid-July
NetBlocks, an organization that monitors cybersecurity and internet governance, posted a tweet about this incident and confirmed the attack had shut down the network for a short time.
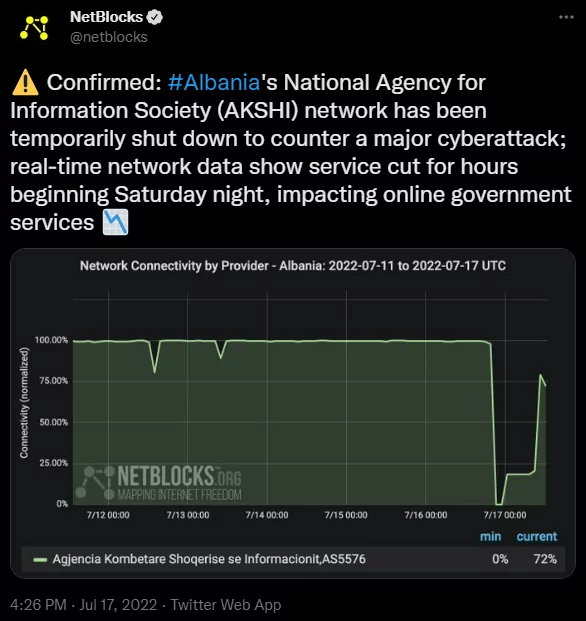
Microsoft observed that multiple actors in distinct phases participated in this attack and tagged them with “DEV-####” statements that it used for unknown actors. These actors are labeled as:
- DEV-0842, the unknown threat actor who has deployed the ransomware and wiper malware,
- DEV-0861, the unknown threat actor who gained initial access and exfiltrated data.
- DEV-0166 was the unknown threat actor who exfiltrated data and was labeled as “IntrudingDivisor” later. Microsoft claims that the actors involved in gaining initial access and playing a role in the exfiltration of the data in this attack are linked to EUROPIUM -also known as OilRig or APT34- which has been linked to Iran’s Ministry of Intelligence and Security (MOIS) before.
- DEV-0133, the unknown threat actor who has probed victim infrastructure.
The shreds of evidence gathered from MSTIC’s forensic analysis show the actor is Iran-affiliated because of the tools used in this attack by other known Iranian attackers. An Iranian APT group affiliated with EUROPIUM -known as ITG13 in that case, according to IBM X-Force Incident Response and Intelligence Services (IRIS)- used that “ZeroCleare” named wiper code in an attack on a Middle East energy company in mid-2019.
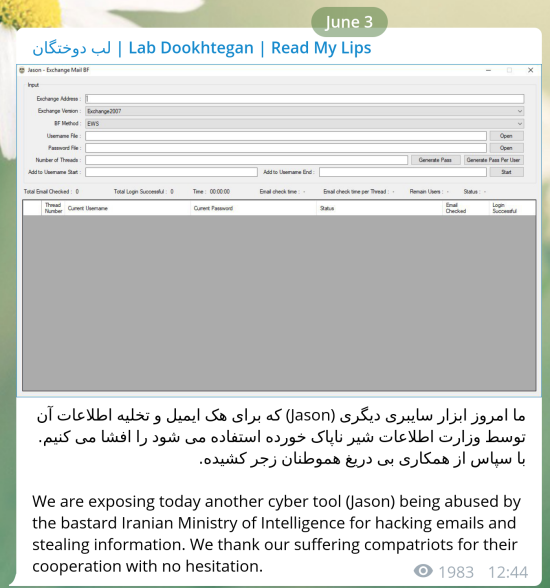
For the intrusion and exfiltration phase, DEV-0861 gained access on May 2021 by exploiting the CVE-2019-0604 vulnerability on an unpatched SharePoint Server. Then fortified its access by using misconfigured administrator account by July 2021. MSTIC’s analysis of Exchange logs shows that data exfiltration was made between October 2021 and January 2022. In addition to that exfiltration, the other actor, DEV-0166, was observed by MSTIC that using Jason.exe tool -a GUI tool to perform brute-forcing Microsoft Exchange accounts developed by APT34 group that leaked by Lab Dookhtegan in 2019- to access compromised mailboxes.
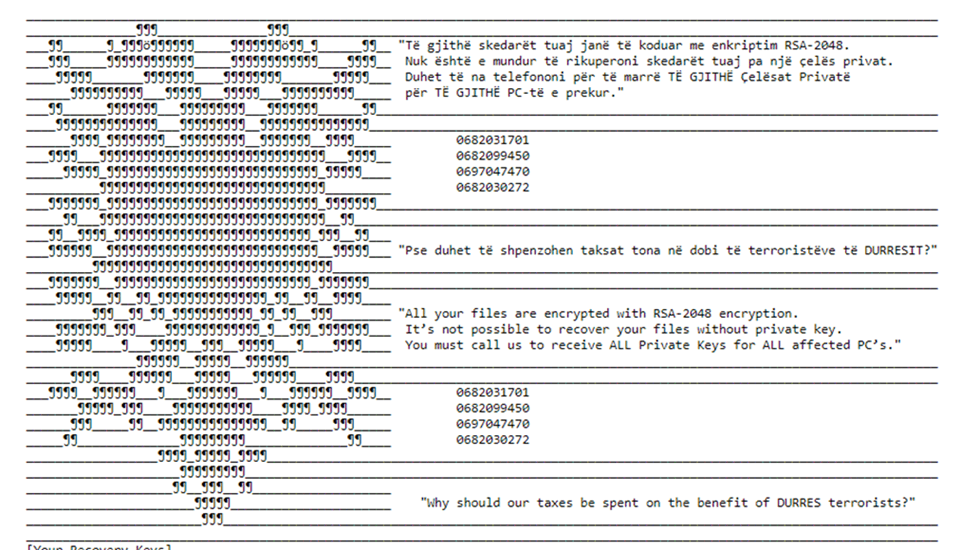
The final phase of the attack is ransomware and wiping. Strings are encrypted with the RC4 algorithm with a predetermined key, and it generates a key pair using a random function with a predetermined key, which is stored in a ransom note. Then, it drops a ransom note in Albanian, as seen below.
What Happened on the Dark Web About This Incident?
Besides the first destructive cyberattack, the MSTIC and DART assess that a separate Iranian state-sponsored actor leaked sensitive information that had been exfiltrated a few months before. Connected to the leak from the first attack, on August 5, a new email content leak was detected in a hacker forum monitored by SOCRadar about the Prime Minister of Albania.
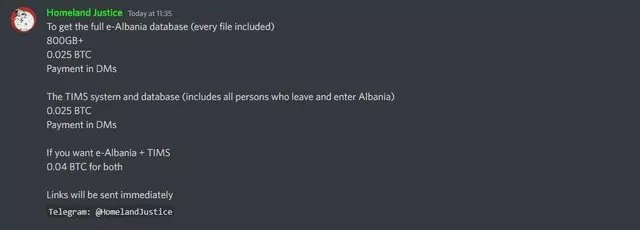
According to SOT News, the e-Albania and TIMS data have been sold on the dark web by the Homeland Justice group, which made statements on Twitter about this incident.
Notable Characteristics of the Incident
It was a unique case of a country cutting diplomatic relations over a cyber-attack. It may lead other countries to do this kind of reaction in case such an incident occurs. There have been instances of such diplomatic implications in the past. But they were not as tough as this reaction.
In-depth analysis of attack using various techniques, including forensic analysis, analyzing events that are possible to link with the incident from acquired data, then correlating with its background led us to the threat source. It shows why Cyber Threat Intelligence (CTI) is critical in such incidents. Threat intelligence can enlighten the unknown. This must be kept in mind that CTI makes it possible to unmask criminals.
As we can understand from this incident, CTI may play a considerable role even in diplomatic issues that can cause significant problems between countries.
Iran-related APT Groups Continue Targeting Organizations
The Joint Cybersecurity Advisory released a paper about Iranian government-sponsored cyber-attacks. The report highlights that the continuing cyber activities from the Advanced persistent threat (APT) actors are related to the Iranian Government’s Islamic Revolutionary Guard Corps (IRGC). Also, according to the report, The IRGC-affiliated actors’ target is a broad range of entities, including the critical infrastructure of the U.S., Australian, Canadian, and United Kingdom organizations.

On September 14, Chris Wray -the director of the FBI- released a video message and announced the three Iranian nationals for compromising the networks of companies, organizations, and institutions giving critical services to the world. According to Wray’s statement, these three Iranian nationals are charged because of engaging in a pattern of hacking, cyber theft, and extortion for personal gain. Following Wray’s announcement, the FBI added three Iranian nationals -Mansour Ahmadi, Ahmad Khatibi Aghda, and Amir Hossein Nickaein Ravari- to its wanted list.
Also, Reward for Justice (RFJ), the U.S. Department of State’s national security rewards program, tweeted about these three Iranian cyber actors and announced they are giving up to 10 million U.S dollars to those who share information about them.



































