
Manufacturing Industry Pays the Highest Average Ransom at $2.04M
The past five years have witnessed the evolution of threat actors in ransomware. These developments, both operationally and technically, have significantly increased the damage done by ransomware groups.
Ransomware gangs are no longer content with simply encrypting files and demanding ransom from the victim. They also use triple or even quadruple extortion tactics, such as publicly sharing the victim’s data or threatening to crash their system with a DDoS attack.
The comprehensive Global Ransomware Report by the SOCRadar research team offers new perspectives to security leaders by conducting an in-depth analysis of the economic effects and disruptive aspects of this powerful weapon, which threat actors use most frequently.
You can click the button below to download the report.
Phishing is Still the Top Attack Vector for Ransomware Campaigns
In the past, we often saw the names of big companies in ransomware news. A radical change has occurred in this situation in recent years. According to Verizon 2022 DBIR, all sizes of businesses suffer from ransomware.
Most of them, whether giant enterprises or much smaller organizations, need a tighter understanding of cybersecurity. This becomes even clearer when you look at the attack vectors of ransomware. Attackers mostly upload file-encrypting malware to their victims using email phishing, remote desktop protocol, and security vulnerabilities.

Email phishing attacks are a frequently used method not only for ransomware but also for credential-stealing malware and remote access trojans. Therefore, it is necessary to be extra careful against such social engineering schemes and to spread awareness.
The tendency of threat actors to exploit remote desktop protocol (RDP) is a result of remote working practice, which has skyrocketed with the pandemic. Research shows that with the widespread use of this practice, RDP usage has increased by 41%.
Security vulnerabilities, another common attack vector, are due to the lack of vulnerability management. We know that unpatched security vulnerabilities are exploited in major known ransomware attacks. For example, Conti exploited more than 30 vulnerabilities in its attacks in 2021.
Nearly 70% of Organizations Pay the Ransom
Over the years, the average ransom demanded by threat actors has increased. This number, which was $170,000 in 2020, has reached $812,000 in 2021. You can imagine how much revenue the ransomware gangs have brought in total for a few hundred thousand dollars, which may seem insignificant for some large companies.
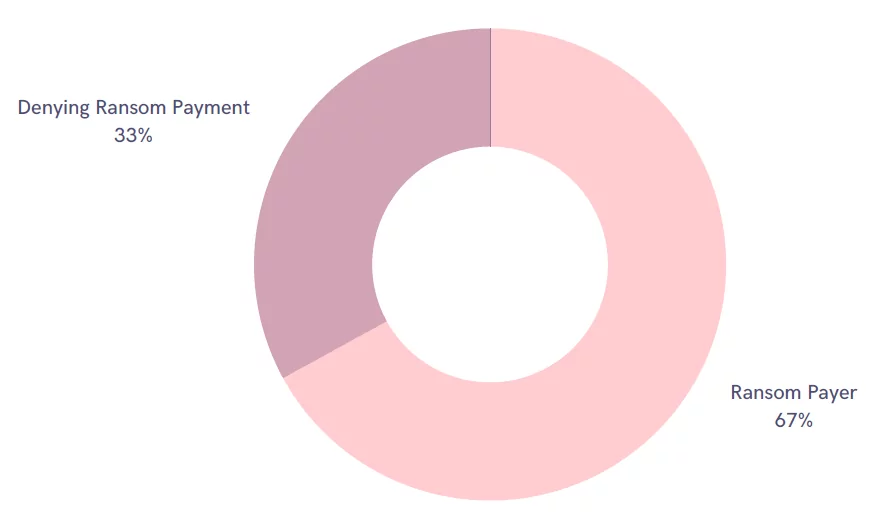
Attackers have used the “double extortion” technique, threatening to expose victims’ critical data after encrypting it. Many organizations are trying to control the situation by paying a ransom. The ransomware gangs have seized much data that could put organizations’ internal correspondence, employee information, agreements, and intellectual property rights at risk, causing panic. According to SOCRadar’s research, 68% of victims in 2021 and 67% in 2022 tend to pay the ransom immediately. About 30% of those who refuse to pay the ransom to face new threats, such as DDoS attacks.
Get a more detailed analysis of the issue by downloading our Global Ransomware Report.
Most Targeted Country is the US
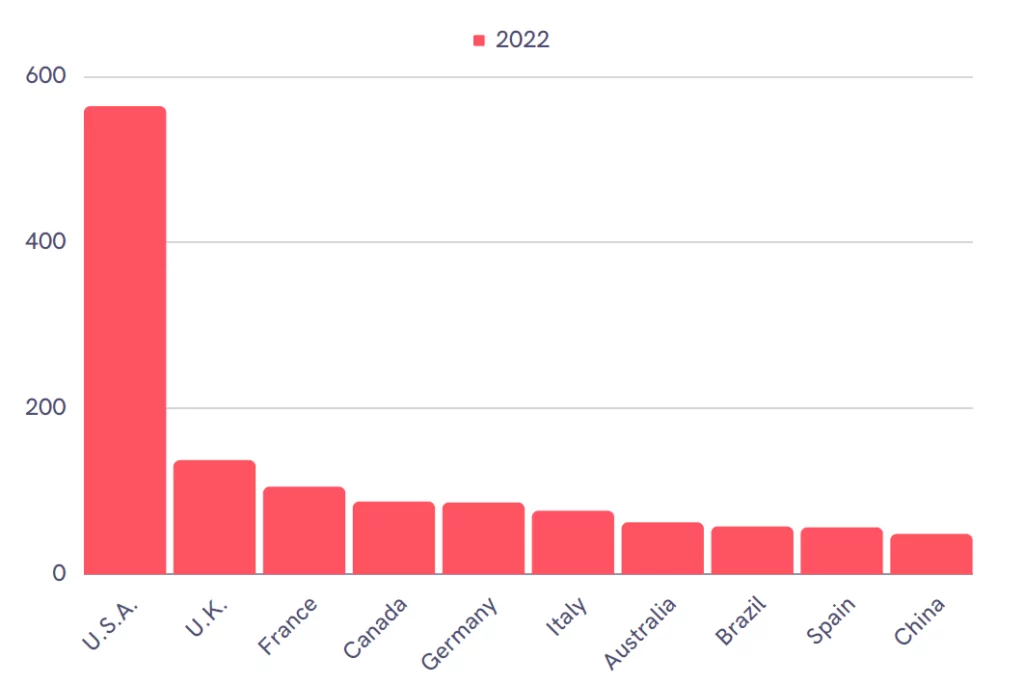
SOCRadar found that the 1987 ransomware attack, carried out in 2021, targeted 102 different countries. In addition to countries with high GDPs, there are also developing countries like Bangladesh and Haiti.
The most targeted countries stand out as the Americas and continental Europe.
The United States is the most targeted country in attacks carried out until June 2022. While countries such as Australia, Germany, Canada, and Italy continue to be targeted, Switzerland-based companies that are not on the list in 2021 are in 2022.
LockBit Dominates the Ransomware Landscape
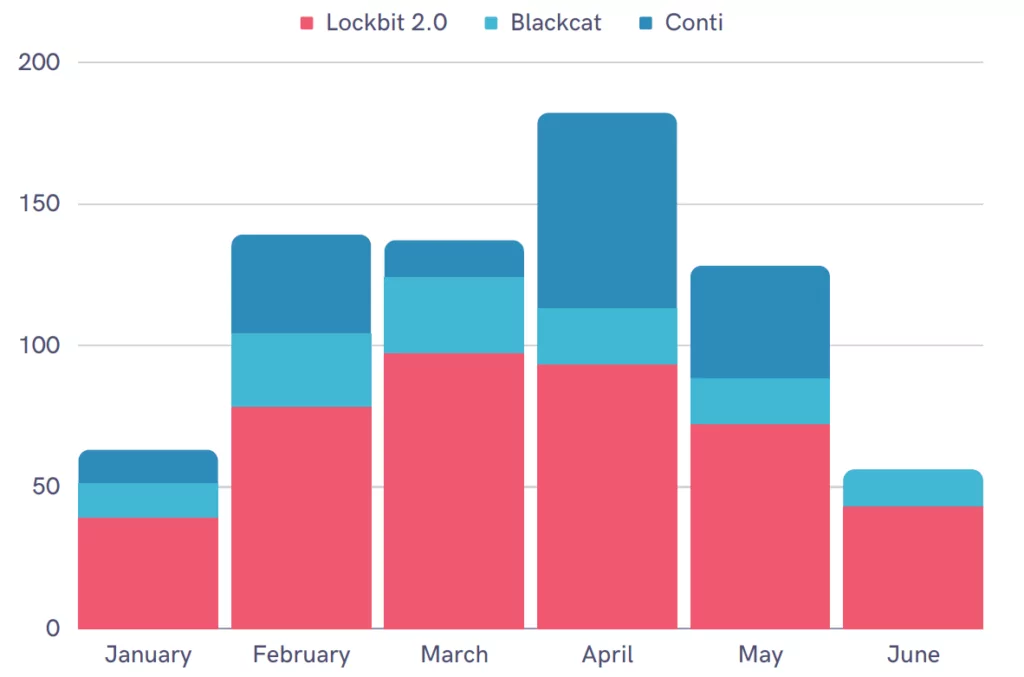
2019 and 2020 were the golden years of the REvil ransomware gang. The Russian-based group was behind most ransomware attacks. The FBI even announced that it would offer a $10 million reward to those who provide information about people in key positions in the group.
In early 2022, officials conducted a series of investigations and arrests against REvil. Thus, the group seemed to have left its place to the Conti gang, which was first detected in 2020.
When the Conti group openly sided with Russia in the Russia-Ukraine war, the ransomware landscape started to change again. After leaks revealing everything from the gang’s internal memos to its organizational structure, Conti also announced that it was dissolving itself as of May 2022.
LockBit has been operating as a ransomware-as-a-service operator for about three and a half years and announced its new version this year, continuing its attacks.
Download the report to read a more detailed analysis of other ransomware gangs and attacks.



































