
Deep Web Profile: REvil
REvil is a ransomware hacking group, as its name suggests -REvil = “ransomware” + “evil”-. This ransomware group is thought to be centered in Russia. It is also named “Sodinokibi.”
Who is REvil?
Their work style mainly includes stealing the data from the victim’s computer and threatening to publish the stolen data on Happy Blog unless the ransom is paid after their attack. This is a one-of-a-kind method of delivering more pressure on victims.
One of the high-profile attacks by REvil took place in April 2021. On that date, REvil attacked the system of Apple’s supplier and took the critical blueprints for Apple’s upcoming products. REvil demanded a $50 million ransom not to release these sensitive data. It demonstrates that REvil is mainly motivated financially.
Find out how you can detect ransomware attacks with SOCRadar!
Shut Down
After the Kaseya attack by REvil, law enforcement and the White House were putting growing pressure on the group. The organization was finally confronted by Russia’s Federal Security Service (FSB) after many inquiries from the United States.
Police and the FSB raided 25 residences, arrested 14 persons, and seized 426 million roubles, $600,000, 500,000 euros, computer equipment, and 20 luxury cars. It is not surprising that REvil ransomware attacks were listed first in the reports, revealing that 79% of global cybersecurity incidents were ransomware attacks.
REvil vanished soon after the operation, and its Tor servers and infrastructure were also shut down. However, no word yet on whether any of the group’s true leaders have taken, and the organization is shut down. Although Russia has been under a great deal of strain in recent years, it is thought that the organization is still active. It’s unclear whether the notorious gang has been deactivated.
Back Online
According to mounting evidence, REvil ransomware organization appears to be back online again. Several security researchers were drawn to a new wave of ransomware assault reports and the group’s leak site reactivation last week. The dark website, which has been redirected from the original URL, includes several recent alleged victim organizations and offers the same proven (but enhanced) software.
Oil India Attack: A network compromise and data leak at Oil India, a natural resources firm operating on the subcontinent, was the most visible new REvil ransomware attack. Last week, the TOR leak site disclosed the attack, which REvil operators use to announce their victims and ridicule people who refuse to pay ransom demands. Oil India not only revealed that it had been hacked and received a $7.5 million ransom demand, but it also enlisted the help of local cops and foreign cyber security experts to investigate the situation.
Rumors: While the attack sparked rumors that REvil was resuming activities, it remained unclear whether the organization had been wrongly identified or if it was a copycat strike.
Several ransomware samples on open-source malware repositories have been recognized as REvil (Sodinokibi). The researchers have also reported seeing some of its infection’s signature malware samples.
REvil as a name may be returning, but its controlling group remains a secret. Because no person has been named, it is unknown whether the operation is managed by the same people who oversaw the prior process or whether a new group has taken over.
The Last Incidents of REvil
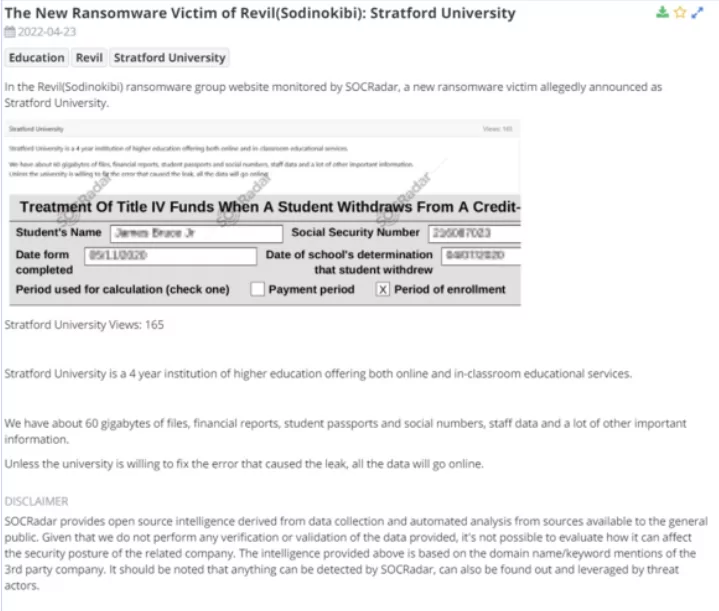
1. New Ransomware Victim of REvil (Sodinokibi): Stratford University
SOCRadar detected a new victim allegedly announced as Stratford University on the REvil (Sodinokibi) ransomware group website. Stratford University is a four-year institution of higher education that enables online and in-classroom educational services to students. The Ransomware group stated that they have about 60 gigabytes of files, financial reports, student passports, social numbers, staff data, and other important information. Unless the university does not repair the error that caused the leak, all the leaked data of Stratford University can be accessed online.
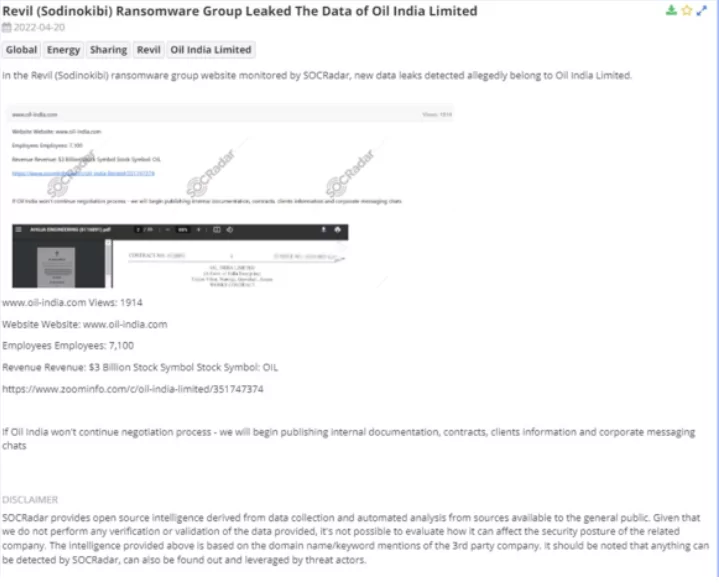
2. REvil (Sodinokibi) Ransomware Group Leaked The Data of Oil India Limited
SOCRadar detected new data leaks that allegedly belong to Oil İndia Limited in the threat actor’s website. Information about the Oil India Limited Company website, the number of its employees, and their income exist on the ransomware group website. Moreover, the ransomware group stated that they would start publishing internal documentation, contracts, client information, and corporate messaging chats if Oil India will not proceed in the negotiation process.
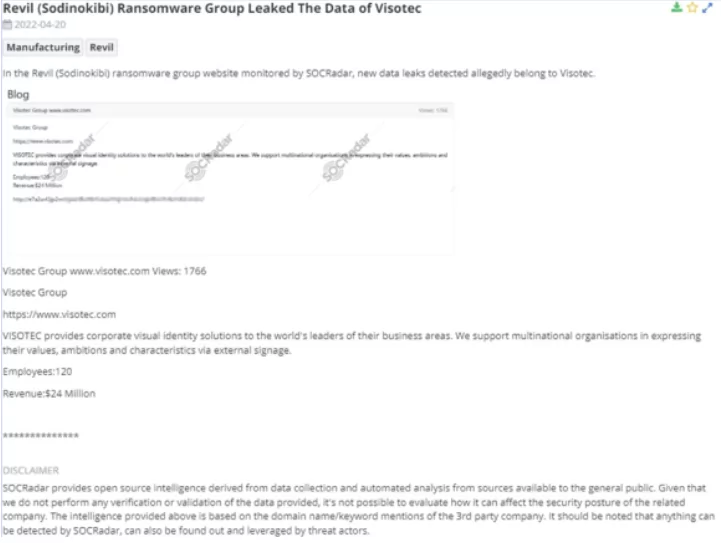
3. REvil (Sodinokibi) Ransomware Group Leaked The Data of Visotec
SOCRadar noticed a new data leak belonging to Visotec in the REvil (Sodinokibi) ransomware group website. There is the website address of the Visotec and data about its employees and income on the ransomware group website. REvil ransomware group state that Visotec provides corporate visual identity solutions to the world’s leaders in their business areas. Also, it is revealed that they support multinational organizations in expressing their values, ambitions, and features through external signage.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































