
Dark Web Threat Profile: Cuba Ransomware Group
Cuba is a C++ based ransomware, and Cuba Ransomware group uses it as the final step payload for double extortion attacks. Operators utilize Cuba in combination with a data leak site that publishes information extracted from compromised systems.
What is Cuba Ransomware?
After affecting several individual machines, the Cuba Ransomware group was first sighted in late 2019. It should also be considered that while there are pictures of famous names from Cuba and the group’s name is Cuba, they are allegedly associated with Russia because Profero, a cyber security firm, observed the Russian language on the data leak site and during negotiations.
Throughout 2020 and 2021, Cuba Ransomware was reported on numerous systems, though none significant. Cuba, living up to its reputation in February 2021 and November 2021, was marked as a potential prominent threat actor after the increasing number of reports including incidents linked to the ransomware gang.

Cuba Gang Attacked The Automatic Funds Transfer Services (AFTS)
On February 4, Cuba ransomware hit the Automatic Funds Transfer Services (AFTS). The AFTS is a payment processing that runs out of Seattle. They operate with many municipal, local, and state government entities in Washington and throughout the United States. The AFTS rejected paying the ransom on their data. Then the Cuba ransomware group quickly transferred it back to their servers to trade on the Dark Web.
The most considerable victim was the California Department of Motor Vehicles. The details of up to 38 million people have been disclosed, which may be sold online for identity theft and different purposes. Besides the California Department of Motor Vehicles, there were numerous victims, but the breach is less disruptive than it could have been for most cities using affected AFTS. Because while the data disclosed from the breach comprises names, addresses, phone numbers, credit card information, and various personally identifiable information (PII), the breach did not disclose social security numbers in the encrypted files.

Victim Profile of The Cuba Ransomware Group
Cuba ransomware has affected organizations from Europe, North and South America. Their most notable attack was against the ATFS, a widely used billing and payment processor for local and state governments. However, in a flash notice released on 2 December 2021, the FBI has indicated that Cuba ransomware actors compromised at least 49 entities in five critical infrastructure sectors last month. Affected industries include the financial, government, healthcare, manufacturing, and information technology sectors.
The Genesis of a Cuba Ransomware Attack and Hancitor Downloaders Dropping Cobalt Strike Beacons
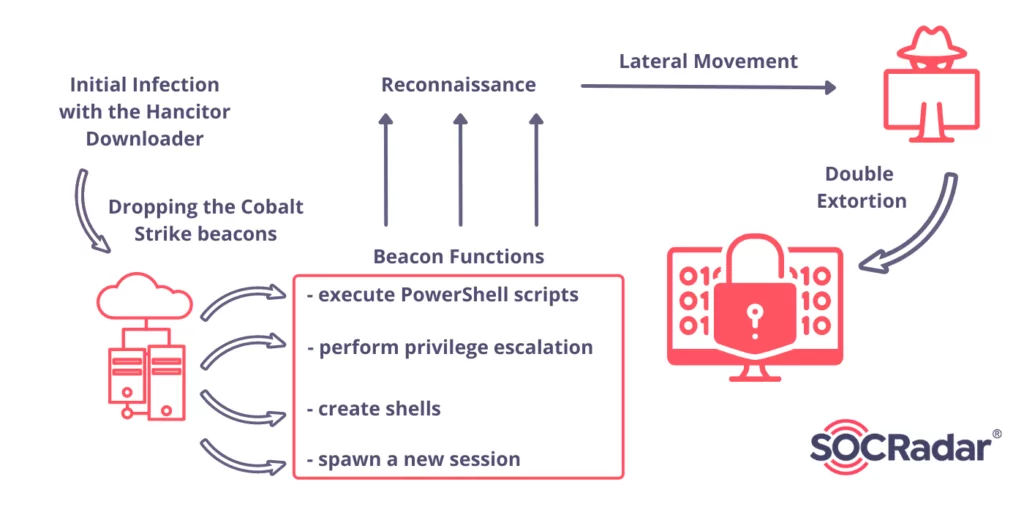
In the security alert, the FBI described how the Cuba ransomware gang realize the delivery and its activities. Similar to the partnership of Ryuk and Conti with TrickBot or Egregor and ProLock with QBot, so as to gain access to compromised networks, Cuba Ransomware has partnered with Hancitor downloader. Many cybersecurity firms have discovered recent Hancitor campaigns dropping Cobalt Strike beacons on compromised computers.
Cobalt Strike is a legitimate penetration testing tool set that uses deployed beacons on infected devices. This deployment enables to remotely execute PowerShell scripts, perform privilege escalation, create shells or spawn a new session to create a listener on the victim system.
Ransomware gangs commonly use cracked versions of Cobalt Strike as part of their attacks to gain a foothold and spread laterally throughout a network. After the Cobalt Strike beacons are deployed, the threat actors use this remote access to gather network credentials, domain information and spread throughout the network. The beacons are also able to scan the compromised network, and Cuba leveraged some custom instruments for reconnaissance of the networks. The first tool is Netping, a superficial scanner gathering information from active hosts in the network and saving it into a file, and the other tool, Protoping, an instrument that collects information about open network shares.
The threat actors operate Remote Desktop for lateral movement. However, if Cobalt Strike beacons are disabled, they use different backdoor arsenals such as Ficker stealer or SystemBC, becoming more favored among multiple ransomware groups. While the attackers move through the network, they gather unencrypted data and transmit it to the ransomware servers for a double-extortion strategy.
The IOCs (Yara Rules, Network and Host Indicators, MITRO ATT&CK Techniques) for this ransomware group’s attacks can be found on the SOCRadarThreatFusion Portal.
Protecting and Defending Against Cuba Ransomware
According to the SOCRadar Analyst Team, so as to evade ransomware attacks and minimize risks:
- The company data should be backed up periodically.
- Administrator credentials should be installed on extra software.
- Two-factor authentication must be implemented where possible.
- Keep all operating systems and software up to date. Timely patching is one of the most efficient and cost-effective steps security teams can take to minimize its exposure to cybersecurity threats.
- Given the sustained progress of significant game hunter ransomware attacks, organizations need to diminish the attack surface of hosts exposed to the internet, such as servers or network devices.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































