Increased Healthcare Security Breaches in 2022
Data from the US government shows that there has been a significant increase in healthcare security breaches.
At least 125 data breaches of healthcare organizations have been reported since the beginning of April, according to a list compiled by the US Department of Health and Human Services (HHS).
The US Health Department Warns of Venus Ransomware
The United States Department of Health and Human Services (HHS) issued a warning that healthcare organizations across the nation are being targeted by Venus ransomware.
A report from The Health Sector Cybersecurity Coordination Center (HC3) states that there has been at least one incident of Venus ransomware being used to attack the networks of US healthcare organizations, and there are no data leak sites linked to the Venus ransomware affiliates.
“The operators of Venus ransomware are not believed to operate as a ransomware-as-a-service (RaaS) model, and no associated data leak site (DLS) exists at this time.”
Active Ransomware Threats in Healthcare
Venus Ransomware has been active worldwide since it was first recognized in August 2022. It is known to spread through hacking into Windows devices’ exposed remote desktop services.
The same method has been employed by the Quantum ransomware group of Quantum Locker operations, which also targets healthcare organizations.
In June, Quantum began their Jormungandr campaign, their version of BazarCall; this technique involves emailing victims for phishing. After convincing the victim to participate in a remote access session, they collect information from the system they can use to infect it. Quantum affiliates have impersonated numerous brands with this technique, including CrowdStrike and Oracle.
Professional Finance Company Inc (PFC) disclosed in a data breach notification that a Quantum ransomware attack from late February resulted in a data breach that affected 657 healthcare organizations.
Quantum attacked New Jersey Healthcare’s network in July and demanded a ransom of $500,000 in exchange for the information they stole. The group also attacked Interim Healthcare around the same time and a biopharmaceutical company and clinic in June.
Another thing to note is that according to the HHS Cybersecurity Program, listed below are the RaaS groups that targeted the healthcare industry the most:
- ALPHV (BlackCat)
- Conti
- Hive
- LockBit
- SunCrypt
Download SOCRadar’s Healthcare Threat Landscape Report to get full insights and analysis on ransomware threats.
The Most Expensive Industry: Healthcare
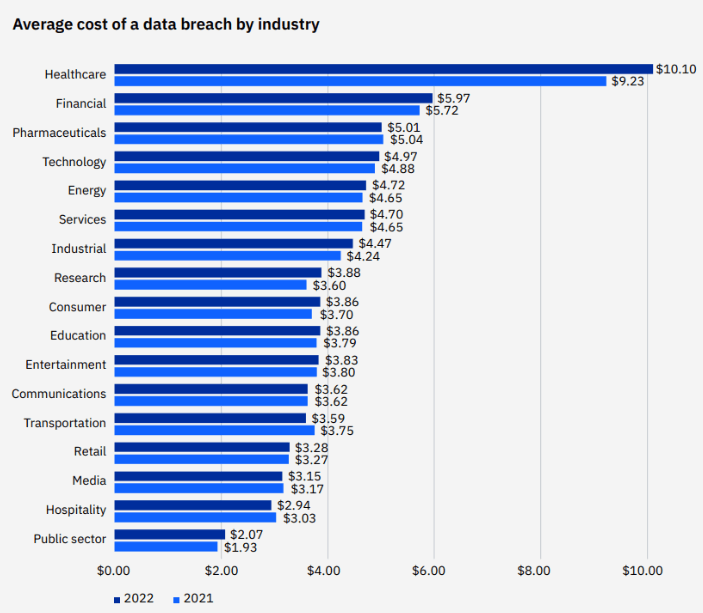
According to the IBM Cost of a Data Breach Report in 2022, healthcare breach costs have risen by 41.6% since the 2020 report, making it the most expensive sector for the past 12 years.
The average total cost of a healthcare breach increased from $9.23 million in the report from 2021 to $10.10 million in 2022, an increase of $0.87 million or 9.4%.
The US government sees healthcare as critical infrastructure, making it one of the more highly regulated industries.
Researches show that healthcare organizations need to spend more money to strengthen their defenses against cyberattacks.
Some industries allocate between 10% and 15% of their IT budgets to cybersecurity. According to the HIMSS survey, healthcare organizations typically spend at most 6% of their IT budgets on cybersecurity.
Medibank Data Theft as a Recent Case
Last month, an Australia-based private insurance provider named Medibank received a ransom demand from unidentified hackers but declined to pay. The threat actor has published customer data believed to have been taken from Medibank’s systems on a dark web forum.
Personal information like names, addresses, dates of birth, phone numbers, email addresses, Medicare numbers for ahm customers (without expiration dates), and occasionally passport numbers for our international students (also without expiration dates) are included in this data.
According to AFP Commissioner Reece Kershaw’s statement:
“The AFP will consult with Russian law enforcement regarding the suspects because it thinks those behind this cybercrime are in Russia.“
Additional Healthcare Incidents
Federal authorities in the United States have issued warnings about additional ransomware attacks this year aimed at healthcare organizations nationwide.
- Previous alerts have included cautions about threat actors using the ransomware payloads Maui and Zeppelin to attack Healthcare and Public Health (HPH) organizations.
- FBI, CISA, and HHS warned last month about how the HPH sector is being targeted by ongoing ransomware attacks by a cybercrime organization known as Daixin Team.
- Yuma Regional Medical Center in Arizona recently revealed that it had been the target of a ransomware attack that exposed the data of 700,000 people.
- A Quincy-based business claimed in a statement that personal medical information, including names, Social Security numbers, addresses, insurance details, details of medical procedures, and more, was accessed. According to the Office for Civil Rights at the US Department of Health and Human Services, two million people are reportedly impacted by the hacking incident.
- In a breach notification to the Maine Attorney General, Partnership HealthPlan of California (PHC) acknowledged that attackers had possibly stolen the protected health information of 854,913 current and former health plan members. Allegedly 400 GB of files were stolen by the Hive ransomware gang. Threat actors momentarily uploaded a sample to their data leak site.
- Keystone Health is informing 235,237 patients in Pennsylvania about an incident that was reported on its website. An investigation revealed that an unauthorized person accessed files on their system. Some of those files included names, Social Security numbers, and clinical data related to patients.
Risk of Third-Party Vendors
Third-party incidents caused a significant part of healthcare data breaches in 2022.
Supply chain partners and third-party vendors have privileged access to important systems and data; healthcare organizations usually need to manage these privileges properly they grant to third parties. As a result, third-party providers frequently become targets for threat actors looking for an entry point into healthcare networks, and they increase the risk of a security breach.
According to SecureLink’s “The State of Cybersecurity and Third-Party Remote Access Risk” report, 55% of healthcare organizations had a third-party incident in 2022. 65% of those healthcare organizations state that their IT systems do not prioritize third-party risks.
Listed below are some third-party healthcare data breach incidents in 2022:
- Connexin Software, a medical records vendor and practice management software, confirmed a network hack that affected 119 providers and over 2.2 million patients. The attackers stole data such as names, contact information, social security numbers, guarantor names, guardian names, birthdates, health insurance information, medical record numbers and history, and billing data.
- Shields Health Care Group, a third-party vendor, was hacked. During the attack, attackers compromised the data of 2 million patients associated with 60 providers. The vendor had to rebuild all impacted systems after the attack. Attackers stole various data, including social security numbers, medical record numbers, medical history, patient IDs, insurance details, and billing information.
- A third-party vendor connected to Broward Health was hacked, allowing access to Broward Health’s network as well. 1.35 million patients’ and employees’ data was stolen. Social security numbers, financial account information, medical records and history, and driver’s licenses were among the information stolen.
Avoid Third-Party Threats With SOCRadar
Knowing when there is a risk to their information is advantageous to users. SOCRadar’s Supply Chain Intelligence can alert you about recent incidents and incidents that have specifically affected a related vendor to provide insight for upcoming supply chain attacks.