
5 Lessons Learned from Healthcare Industry Cyberattacks in 2022
Like other critical infrastructures, the healthcare industry is frequently targeted by cyberattacks. The attacks in the healthcare vertical have begun to increase in recent years due to security vulnerabilities triggered by changes in procedures during the covid 19 pandemic and increased digitalization. According to the IBM Security X-Force Threat Intelligence Index 2022 report, healthcare was the sixth most attacked industry in 2021.
Cyberattacks are especially harmful in the healthcare industry due to the nature of healthcare. Attacks can directly endanger patients’ health and safety, in addition to system and information security. Beyond financial and reputational loss, cyberattacks can cause life-threatening effects.
Download SOCRadar’s Healthcare Threat Landscape Report to get full insights and analysis.
Primary Targets in the Healthcare Industry
The primary targets in the healthcare industry can be categorized as follows;
- Hospitals
- Medical Devices
- Health Insurance
- Biotechnology Industries
- Pharma& Chemicals
- Other end users
Healthcare organizations are prime targets for cyberattacks as they hold large amounts of patient data. Recently, the focus of cybercriminals has shifted from large hospitals to smaller healthcare providers, such as small or rural hospitals or private clinics.
The most apparent reason for targeting smaller healthcare providers is the perception that they are less likely to invest in cybersecurity programs and have a weaker cyber defense. However, the media and law enforcement interests are likely to be less.
Medical devices are one of the healthcare industry’s weak points against cyber criminals. Healthcare digitalization is rising, and providers employ more connected medical devices daily. The devices can vary from wearable IoMT (Internet of Medical Things) devices such as patient tracking wristbands, pacemakers, and insulin pumps to medical devices such as ventilators, portable X-ray machines, and vital signs monitors. The devices interact through a network, providing physicians with critical patient information. Updates are required to keep them operational and secure like any other digital device. Cybercriminals can abuse unpatched and insecure medical devices as entry points.
The FBI issued a white notification (20220912-001) on September 12, 2022, mentioning the increasing number of vulnerabilities posed by unpatched medical devices that run on outdated software and devices that lack adequate security features. This warning pointed out that cyber threat actors exploiting medical device vulnerabilities adversely impact healthcare facilities’ operational functions, patient safety, data confidentiality, and data integrity.
Cybersecurity and infrastructure security agency (CISA) released several ‘ICS MEDICAL ADVISORIES’ about vulnerabilities on medical devices:
- Hillrom Medical Device Management (ICSMA-22-167-01), June 16, 2022
- Baxter Sigma Spectrum Infusion Pump (Update A) (ICSMA-22-251-01), September 29, 2022
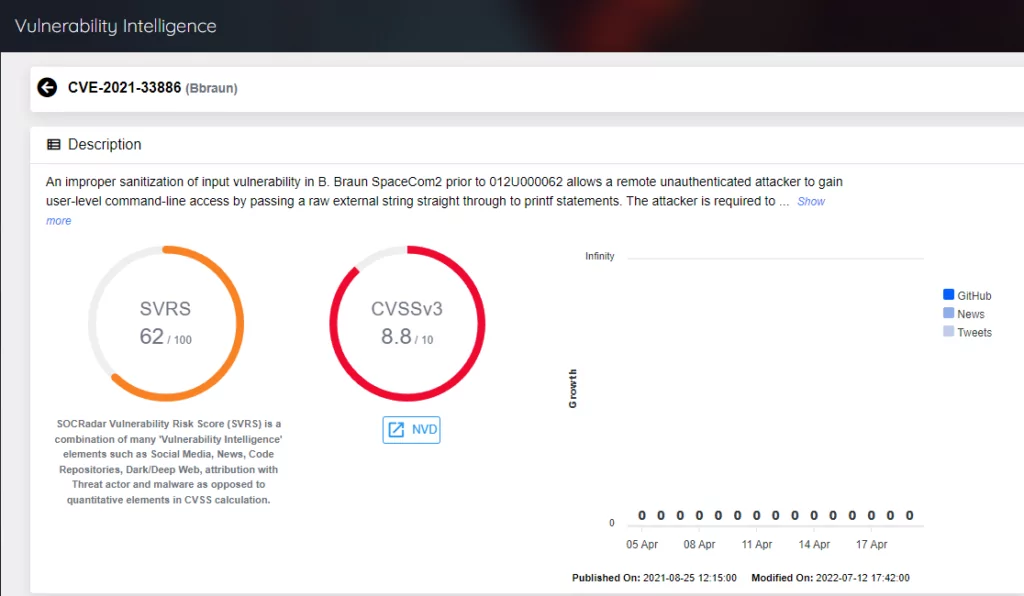
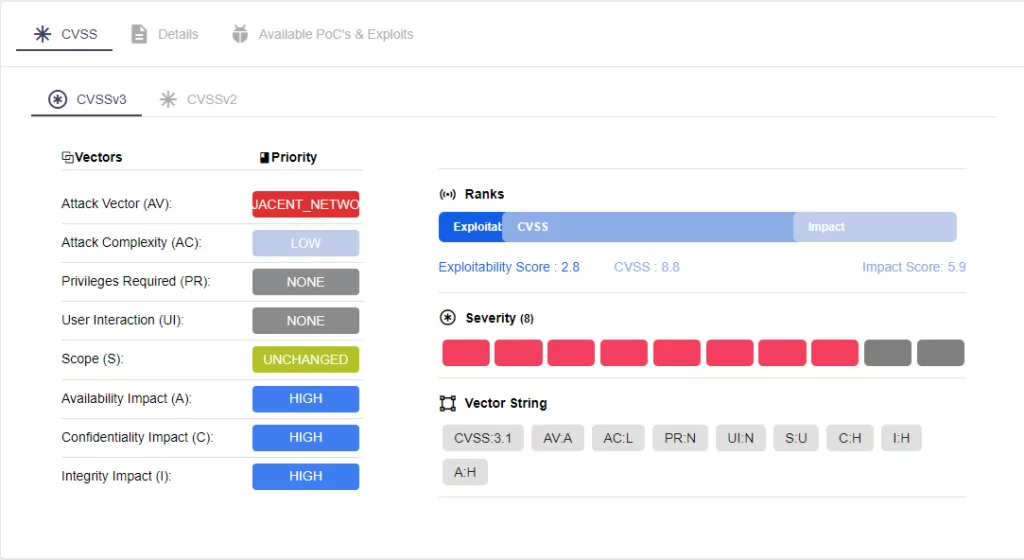
- B. Braun Infusomat Space Large Volume Pump (Update A) (ICSMA-21-294-01), October 20, 2022
- B. Braun Battery Pack SP with Wi-Fi (ICSMA-23-103-01), April 13, 2023
The Rise of the Cyberattacks in the Healthcare Industry
The main reasons for the rising cyberattacks in the healthcare industry are as follows;
– The expansion of cloud-based solutions
– Increase in usage of connected devices
– Personal Health Information (PHI) is more valuable on the black market than credit cards or Personal Identifiable Information (PII)
– Choosing the ransom payment as a first option for the healthcare providers because of the continuity of the systems is vital
– Inadequate security controls in medical devices
– Security measures that are put in the background due to insufficient awareness of cyber security and the workload of healthcare professionals. Cyber security is not the priority for most employees and C-suite executives.
– Usage of outdated technologies
– Complex and extensive supply chain of the healthcare systems
Common Cyber Attack Vectors in the Healthcare Industry
Ransomware is one of the most popular types of healthcare threats. Threat actors realize the importance of minimizing operational disruptions in healthcare and consider healthcare providers closer to paying the ransom. In this context, double extortion tactics, threatening to expose sensitive data in addition to encrypting, can be used. Additionally, the healthcare industry’s low tolerance for disruptions to critical systems can lead to triple extortion, in which DDoS (Distributed Denial of Service) attacks are combined with ransom demands.
Healthcare is one of the critical industries most vulnerable to data breaches. Many systems, such as Hospital Information Systems (HIS), are used by healthcare providers to store sensitive data. Personal Health Information (PHI) is valuable on the black market due to its non-changeability. Personal health history (symptoms, illnesses, surgeries, etc.) cannot be changed, unlike other personal information (credit card information, credentials, etc. As a result, threat actors have a greater motivation to target medical databases.
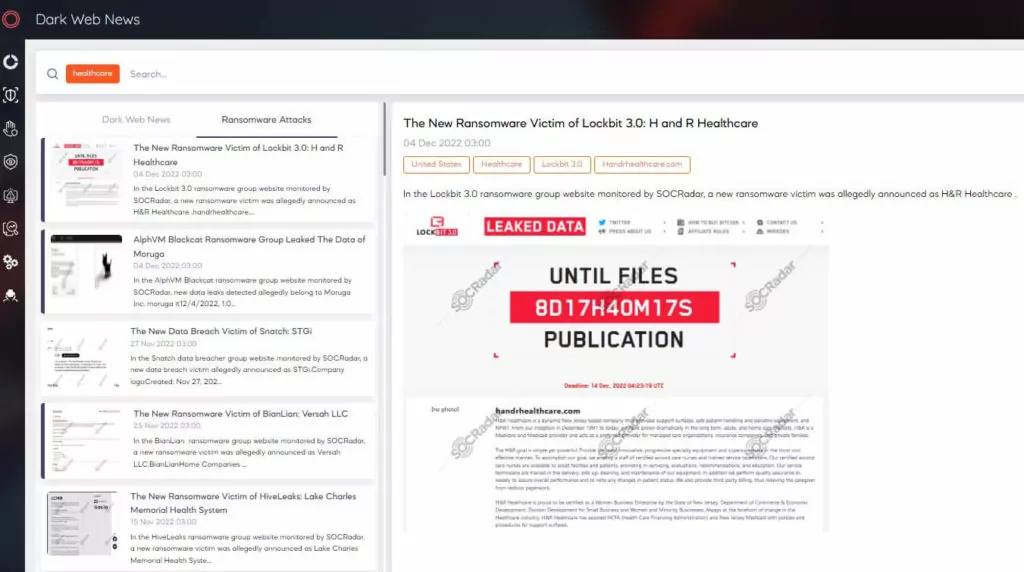
Considering the SOCRadar XTI platform database, almost 464 dark web posts related to the healthcare industry have been reported in the last 12 months (April 1, 2022- March 31, 2023), and the number of posts increased by 35% compared to the previous term (April 1, 2021- 31 March 2022). The most active threat actors were ‘Kelvinsecurity‘, ‘LeakBase‘ , and ‘Osiris.’ SOCRadar research team analysis revealed that underground posts in the healthcare industry are mostly focused on the United States, Indonesia, and Russian Federation.
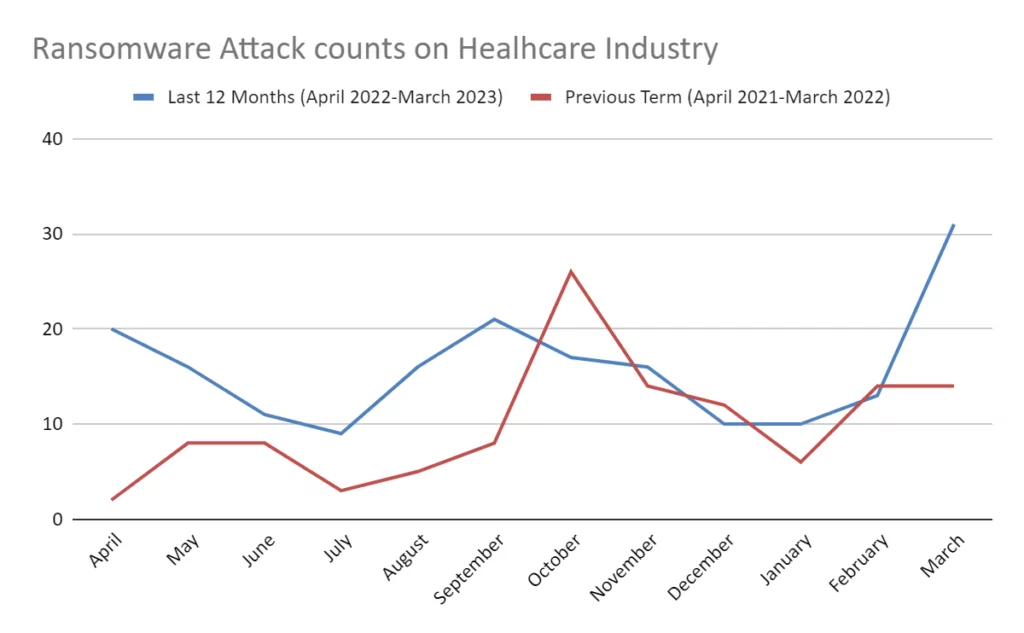
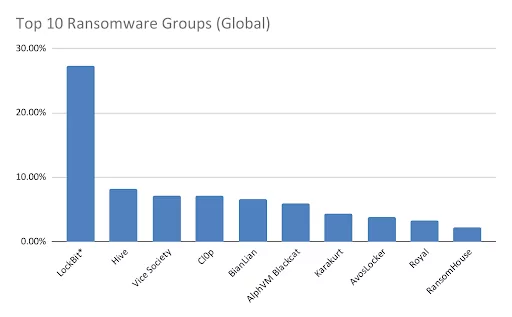
According to the SocRadar XTI platform database, 190 ransomware attacks against the healthcare industry have been reported in the last 12 months, and the number of ransomware attacks has increased by 58.3% compared to the previous term. The most active ransomware group was LockBit, Hive and Vice society ransomware. The distribution of ransomware attacks in the healthcare industry detected by SOCRadar is as follows.
The increase in ransomware attacks on the healthcare vertical has also led official institutions to react. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) released a joint cybersecurity advisory about the Daixin Team Ransomware Group (AA22-294A) and the Hive Ransomware (AA22-321A) Group. The advisories dated October 21, 2022 and November 17, 2022 both stated that the groups are targeting the healthcare and public health industries.
FBI and CISA released a joint cyber security advisories about ;
– Zeppelin Ransomware group ( AA22-223A) on August 11, 2022,
– CUBA Ransomware group (AA22-335A) on January 05, 2023, and
– Royal Ransomware group (AA23-061A) on March 02, 2023
The adversaries noticed that some of the critical infrastructure industries along with healthcare and public health were targeted by mentioned ransomware groups.
In addition, being aware of ransomware attacks on the Health and Public Health (HPH) industry, the U.S. Department of Health and Human Services/Health Sector Cybersecurity Coordination Center (HC3) released the following analysis notes about ransomware groups that are considered a threat to the HPH sector.
-Lorenz ransomware (report number 202211211700) on November 21, 2022
-Royal ransomware (report number: 202212071400), on December 7, 2022
-LockBit 3.0 Ransomware (report number 202212121700 ) and Blackcat (report number 202212121500) on December 12, 2022
-Clop Ransomware (report number: 202301041300 ) on January 04, 2023.
The HPH industry has been recognized as being a highly targeted industry for mentioned ransomware groups by the listed reports.
State-Sponsor Threats on Healthcare Industry
Health institutions are often on the radar of nation-state threat actors due to the potentiality of espionage, theft, and disruptive attacks. According to the SOCRadar XTI database, 68 APT groups were detected that targeted the healthcare industry in the last 12 months.
On July 6, the FBI, CISA, and the Department of the Treasury (Treasury) released a joint cybersecurity advisory mentioning that North Korean state-sponsored cyber actors use Maui ransomware to target the healthcare and public health industry.
According to the advisory, the FBI has observed in HPH organizations various incidents that Maui ransomware was used to encrypt services responsible for healthcare services, including electronic health records, diagnostic services, imaging services, and intranet services. In some cases, the incidents disrupted services for extended periods. And the FBI revealed that North Korean state-sponsored cyber actors used Maui ransomware in these incidents.
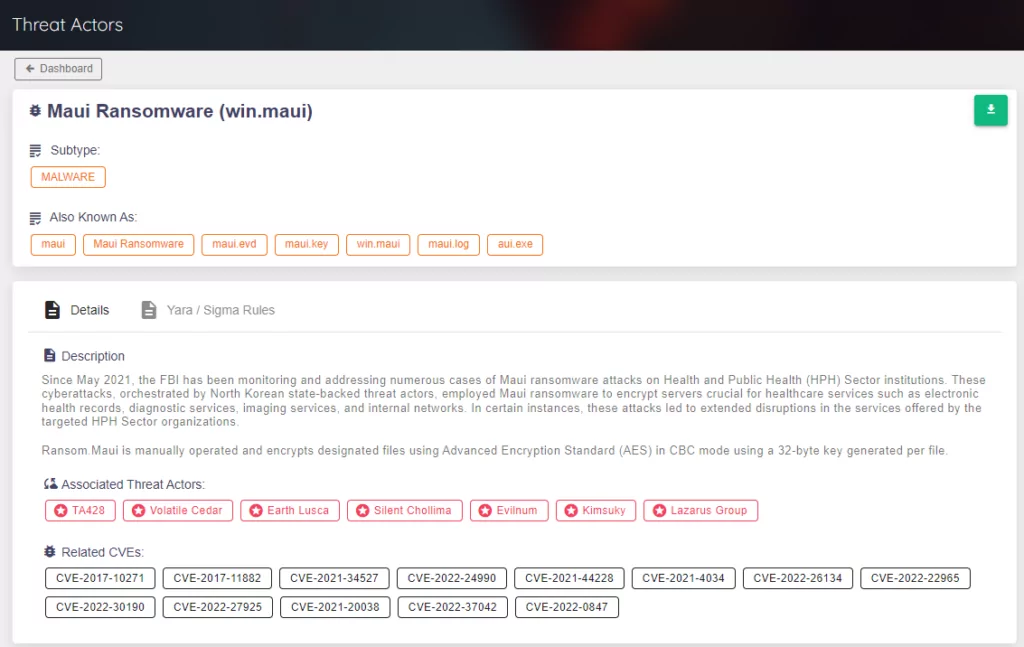
As the well-known North Korean state-sponsored threat actor, the Lazarus group also targets healthcare organizations. In 2020, the group attacked pharmaceutical companies and research facilities working on COVID-19 vaccines. Lazarus group members attempted to steal crucial information about the vaccine development process by posing as medical professionals and contacting pharmaceutical business personnel with messages that contained malicious attachments.
The Lazarus group used ‘healthcare’ also as a weapon in their attacks. The group organized phishing attacks with COVID-19 themed e-mails that were customized with personal information obtained during an initial reconnaissance operation in the “ThreatNeedle” campaign that was carried out against security researchers and the defense industry.
Lessons Learned from Cyberattacks in the Healthcare Industry
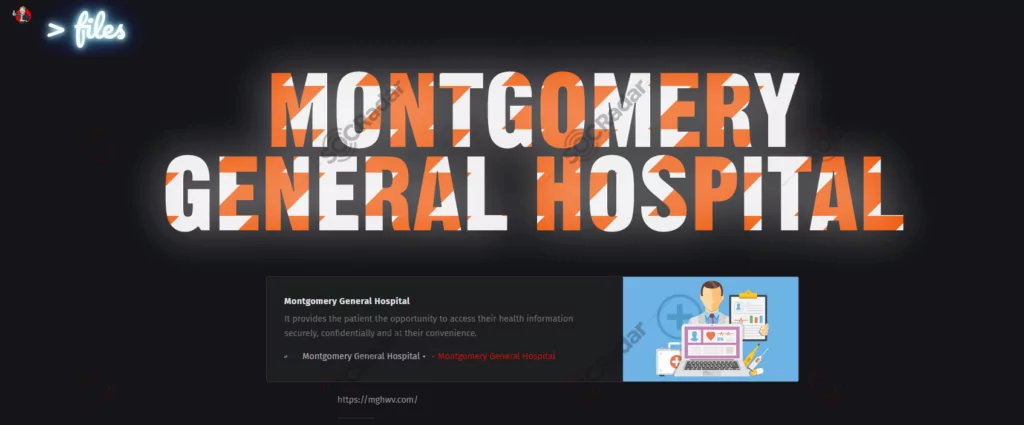
Lesson 1: Montgomery General Hospital, a 25 bed critical access facility, located in West Virginia was victim of Donut Ransomware group in early March 2023. Montgomery General Hospital engaged a third-party security firm to assist with the investigation of the incident. After the MGH refused to pay the ransom some of the stolen files have been publicly released on the ransomware group’s data leak site.
Small hospitals and clinics are targeted since they are considered more accessible targets for attackers. Most minor medical institutions need more human resources and resources to implement the latest cybersecurity precautions. To fill this gap, institutions should consider external support from security companies.
Lesson 2: Connected medical devices are one of the healthcare industry’s most severe security weak points. According to Cynerio and Ponemon Institute’s ‘The Insecurity of Connected Devices in Healthcare 2022‘ survey, 56% of respondents have encountered at least one cyberattack involving connected devices in the recent 24 months.
Connected medical devices will be more secure when they are listed in the digital asset inventory and their network activity is monitored and encrypted. It is also crucial to use network segmentation to prevent these devices from accessing critical databases. Also, it is essential to follow the security updates of the devices regularly.
Herein, SOCRadar Attack Surface Management (ASM) solution ‘AttackMapper’ can help organizations gain additional visibility and monitoring of all digital assets in an automated manner.
Lesson 3: To pay close attention to phishing attacks, which are the first point(s) of compromise for many attacks. People are vulnerable to attacks such as phishing and social engineering. The risk factor should be reduced by training that increases the cybersecurity awareness of healthcare professionals.
SOCRadar Digital Risk Protection (DRP) solution ‘RiskPrime’ builds on industry-leading instant phishing domain identification, internet-wide scanning, and compromised credential detection technologies.
Lesson 4: Ransomware attacks are one of the most common cyberattacks in the healthcare industry. Identifying the security vulnerabilities commonly used against the healthcare industry for ransomware attacks and taking proper precautions is crucial. To save data, apply the 3-2-1 backup strategy the Cybersecurity and Infrastructure Security Agency (CISA) advised.
Lesson 5: Encryption is one of the effective ways to prevent a threat actor from accessing sensitive data in healthcare systems. Encryption must be utilized during data storage and transmission to mitigate data breaches.
In addition to any organization’s cybersecurity threats, healthcare providers must handle industry-specific challenges. They must protect networks, databases, and endpoints from internal and external cyber threats. They are also responsible for the availability of medical services, the proper operation of medical systems and equipment, and the security and integrity of patients’ and employees’ private financial and medical information.
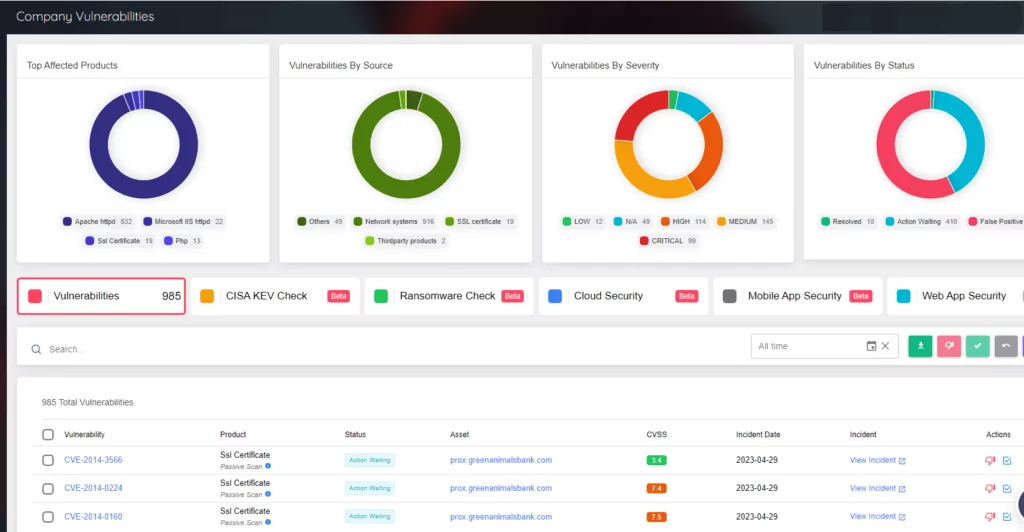
It is essential to increase security visibility to provide a solid cyber security posture. With Attack Surface Management, you can identify and monitor all digital assets 24/7 and detect security vulnerabilities proactively.
Using Cyber Threat Intelligence (CTI) solutions is also critical to identify, mitigate, and remediate security risks effectively. In particular, CTI tools that provide intelligence from the dark web can offer an early warning of PHI data leaks for predictive measures.



































