
10 Free Security Testing Tools to Test Your Website
Security testing for an application is a crucial element in the lifecycle of software testing. It restricts unwanted intrusions at multiple application layers, including servers, the front-end application layer, middleware modules, and network security.
This testing verifies that only the system or users with correct authentication are permitted to access the application. In contrast, those who fail the authentication are prohibited from utilizing the program.
Top 10 Security Testing Tools
1- ZED Attack Proxy (ZAP)
It is an open-source tool mainly created to assist security experts in discovering web application security flaws. It is designed to operate on Windows, Unix/Linux, and Macintosh operating systems. It may be used as a web page scanner/filter.
Key Features:
- Intercepting Proxy
- Passive Scanning
- Automated Scanner
- REST-based API
2- Burp Suite
It is a tool used for checking the security of online applications. There are both professional and community editions. With more than 100 preset vulnerability criteria, the Burp suite protects the application’s security by applying these conditions to identify flaws.
3- NetSparker
NetSparker is an all-inclusive solution for online security requirements. Available as a hosted and self-hosted solution, this platform may be simply integrated into any test or development environment. NetSparker’s Proof-Based-Scanning solution employs automation to identify vulnerabilities and check false positives, eliminating the need to spend unnecessarily large amounts of person-hours.
4- Vega
It is a Java-based, open-source vulnerability screening and testing application. Vega is GUI-enabled and is compatible with OS X, Linux, and Windows. An internet crawler-powered automated scanner that facilitates rapid testing.
The proxy that intercepts client-server communication supports tactical inspection by scrutinizing and monitoring client-server communication. Vega can detect vulnerabilities in online applications, such as blind SQL injection, shell injection, reflected and stored cross-site scripting, etc. Its discovery modules are written in JavaScript, and APIs may be used to construct new attack modules on demand.
5- SQLMap
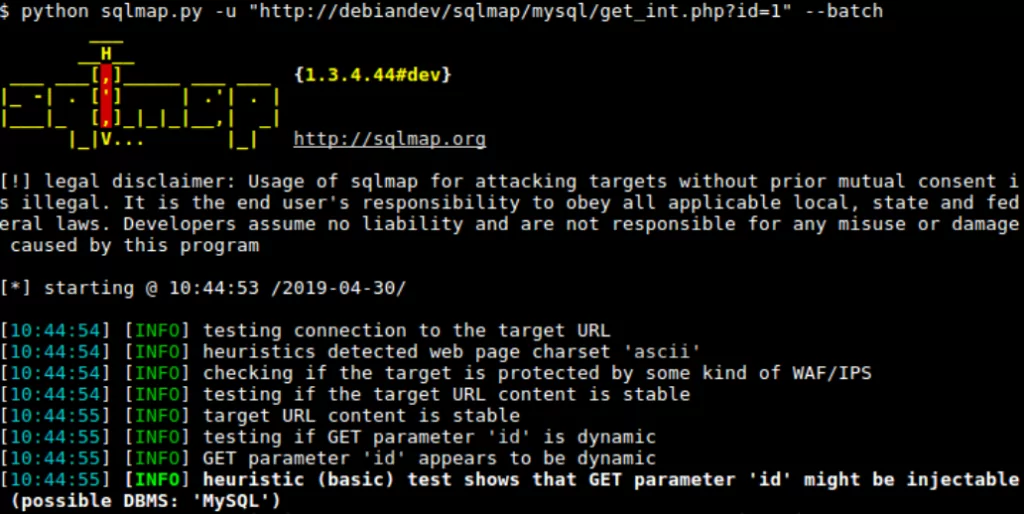
SQLMap is a popular web-based security testing application that automates the identification of SQL injection vulnerabilities in a website’s database. The test engine is equipped with a variety of capabilities that make penetration and SQL injection testing of a web application simple. SQLMap supports many databases, such as MySQL, Oracle, PostgreSQL, Microsoft SQL, etc. In addition, the testing tool supports six distinct SQL injection techniques.
6- Acunetix
With its vulnerability scanner, Acunetix automates the security testing of online applications. In the form of AcuSensor and DeepScan, the Acunetix Vulnerability Scanner highlights novel black-box scanning and SPA crawling techniques.
DeepScan’s multithreaded crawler can conduct an uninterrupted search of WordPress installations for over one thousand vulnerabilities. A Login Sequence Recorder enables the tool to scan password-protected sections. At the same time, an integrated vulnerability management system facilitates the generation of several technical and compliance reports.
7- BeEF (Browser Exploitation Framework)
BeEf, which stands for Browser Exploitation Framework, identifies application vulnerabilities by exploiting browser vulnerabilities. It employs client-side attack vectors to validate the security of an application. It may broadcast browser instructions such as redirection, URL modification, and dialogue box creation. BeEf expands its scan radius beyond the typical network perimeter and the client system to evaluate the web browser’s security mechanism.
8- Google Nogotofail
It is a tool for evaluating network traffic security. It analyzes apps for known TLS/SSL vulnerabilities and setup errors. Nogotofail provides a flexible and scalable method for scanning, detecting, and repairing SSL/TLS connections that are vulnerable. It determines whether they are susceptible to man-in-the-middle (MiTM) assaults. It may be installed as a router, VPN server, or proxy server. It is compatible with Android, iOS, Linux, Windows, Chrome, OS, OSX, and any other device used to access the internet.
9- Wapiti
Wapiti is a command-line tool that crawls through websites to discover data-insertable scripts and forms. It does a black box scan and injects payloads into discovered scripts to determine whether they are susceptible. With support for GET and POST HTTP attack techniques, this program generates vulnerability reports in many formats and varying verbosity levels.
It identifies vulnerabilities such as file disclosure, database injection, file inclusion, Cross-Site Scripting (XSS), and insufficient .htaccess setup. It can distinguish between permanent and reflected XSS vulnerabilities and issues an alert anytime an abnormality is identified.
10- ImmuniWeb
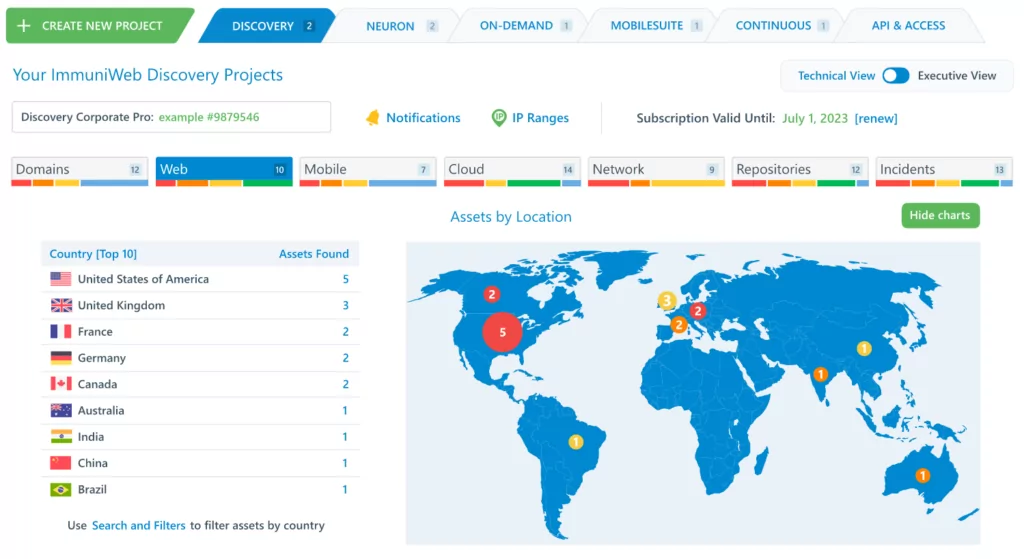
ImmuniWeb is a next-generation security testing tool that employs artificial intelligence. This AI-enabled penetration testing platform provides security teams, developers, CISOs, and CIOs with a comprehensive set of advantages. This platform enables ongoing compliance monitoring with its one-click virtual patching method.
It evaluates a website for compliance, server hardening, and privacy using its unique Multilayer Application Security Testing technique.
How can SOCRadar help you Discover the Vulnerabilities of your Website?
As the breadth and scale of assaults expand, CIRTs (Computer Incident Response Teams) become increasingly crucial for achieving digital resilience. Effective incident response involves immediate access to information on the “who, what, why, when, and how” of an occurrence.
SOCRadar’s unified structure and Extended Threat Intelligence (XTI) concept provide alarms enabling you to convey relevant alerts’ email structure to your SOC team without connecting to the platform.
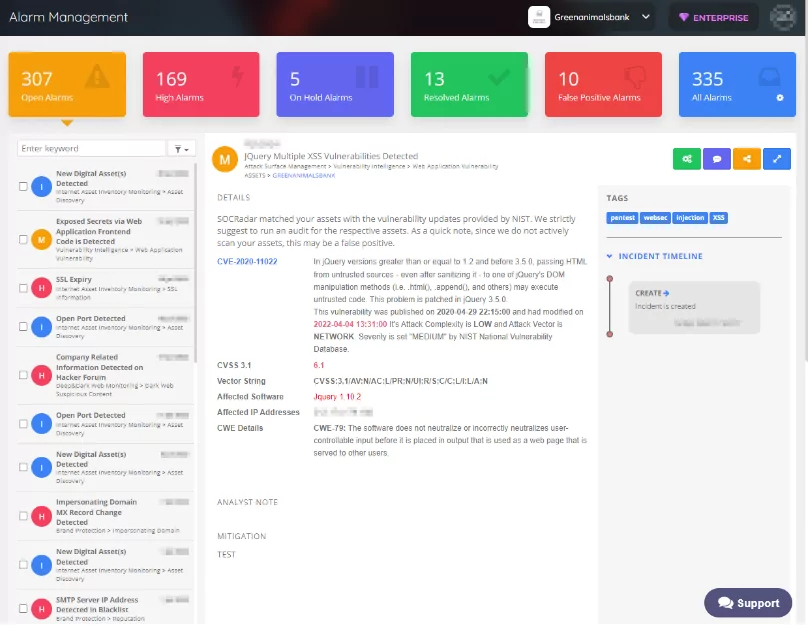
Additionally, you can feed your systems with relevant alerts using the incident API’s filtering structure and process the relevant alarm using the bidirectional API structure (false positive, resolved, etc.).
SOCRadar is an extension of your team that enables you to be more proactive by giving the necessary context for adversary TTPs, motives, and plans.
Key Features of SOCRadar Vulnerability Management:
- Shadow IT
Discover and monitor your neglected external-facing assets, including CMSs, network apps, SSL certificates, and JavaScript libraries, to get fast notifications about the most recent vulnerabilities.
- Vulnerability Trends
Get a threat landscape-centric perspective of global vulnerability trends better to prioritize patching with SOCRadar’s Vulnerability Intelligence dashboard and discover which vulnerabilities are exploited by threat actors.
- Exposed Critical Ports
To avoid disruptive intrusions, continuously monitor your perimeter for essential open ports, such as RDP. Quickly view and download an auto-generated report detailing exposed ports and network services by type, FQDN, and IP address.
- Cryptographic Infrastructure
By monitoring your cryptographic infrastructure for signature signing algorithms, the availability of insecure ciphers, and certificate validity and expiry, you may avoid being susceptible to SSL/TLS attacks such as Heartbleed, POODLE, and Freak.
- JavaScript Threats
Identify out-of-date JS libraries, which often include vulnerabilities such as cross-site scripting (XSS), cross-site request forgery, and buffer overflows.



































