
What is Vulnerability Management?
The increasing number of vulnerabilities that security teams have to deal with makes it impossible to try to remediate all critical vulnerabilities. In fact, a small number of vulnerabilities pose a disproportionately large risk, however, few organizations can identify the most critical vulnerabilities that are exploited through malware kits, ransomware attacks, and other threat actors. At this point, Vulnerability Management comes into play.
Vulnerability management is a cyclical process of identifying IT assets and correlating them with a continuously updated vulnerability database to identify threats, misconfigurations, and vulnerabilities across endpoints, workloads, and systems. It is essential to cyber security and is one of the most proactive strategies to distinguish security weaknesses before leading to a breach.
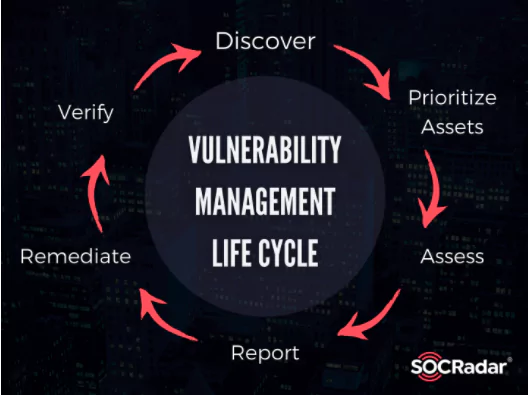
Essential Steps of Vulnerability Management Cycle
Vulnerability Management is a continuous process of identifying, assessing, reporting, managing, and remediating security vulnerabilities. There are numerous stages in this process, and they are described below.
- Discover:
Inventorying all network assets and identifying host details, including the operating system and open services, to recognize security vulnerabilities on an ongoing automated schedule. Closing the blind spots through maintaining up-to-date visibility on infrastructure and assets to reduce the threats against the organization. Configuration Management Databases (CMDBs) can be useful for this purpose.
- Prioritize Assets:
Categorizing assets into groups or business units and assigning a business value to asset groups based on their criticality to business operation. This should be a cross-functional effort that requires continuous collaboration and communication.
- Assess:
Determining a baseline risk profile to reduce risks according to the asset criticality, vulnerability threat, and asset classification. Adopting a risk-based approach as the Vulnerability Management (VM) Team to treat vulnerabilities that are exploitable and critical to business.
- Report:
Measuring the level of business risk connected with an enterprise’s assets according to security procedures. Documenting a security plan, monitoring suspicious activity, and reporting discovered vulnerabilities based on the audience to help the decision-making process.
- Remediate:
Prioritizing and fixing vulnerabilities in order according to business risk. Establishing controls and demonstrating progress.
- Verify:
Verifying the threats that have been eliminated through follow-up audits.
Why Do Enterprises Need Threat Intelligence for Vulnerability Management?
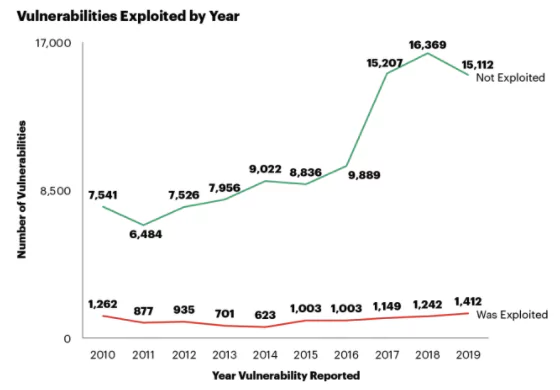
A total of 18,103 vulnerabilities were recorded last year, at an average rate of 50 CVEs per day, by security specialists, researchers, and vendors. Almost 60 percent of the total were classified as critical or high severity vulnerabilities. Among all the CVEs reported in 2020, 68% of those do not require user interaction of any kind to exploit. In addition, over 16K vulnerabilities were recorded this year while there are still two months to the end of the year.
There are a sheer number of vulnerabilities to track manually in most organizations, and these vulnerabilities do not pose equal risk. CVSS frameworks based on “low, medium, high and critical” ratings do not work well since threat actors pay no attention to these scores most of the time.
The period between disclosure of vulnerabilities and their exploit by malicious actors is reducing with each passing day, so enterprises need to be fast in the remediation. With limited time and resources and without the risk background needed to prioritize vulnerabilities, successfully tracking multiple issues across thousands of various assets in a distributed network is almost impossible. Because of this, organizations employ threat intelligence platforms like SOCRadar to analyze the true risk of the identified vulnerabilities which is also called Vulnerability Intelligence.
SOCRadar can help vulnerability teams keep an up-to-date inventory of external-facing assets. To complete the overall life cycle of a vulnerability threat, the platform has extra capabilities to continuously scan these assets and detect new critical vulnerabilities. For the prioritization, SOCRadar performs a global surface, deep and dark web monitoring to identify the vulnerabilities exploited by adversaries or in the wild.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































