On-Device Fraud Trend in Mobile Malware Campaigns
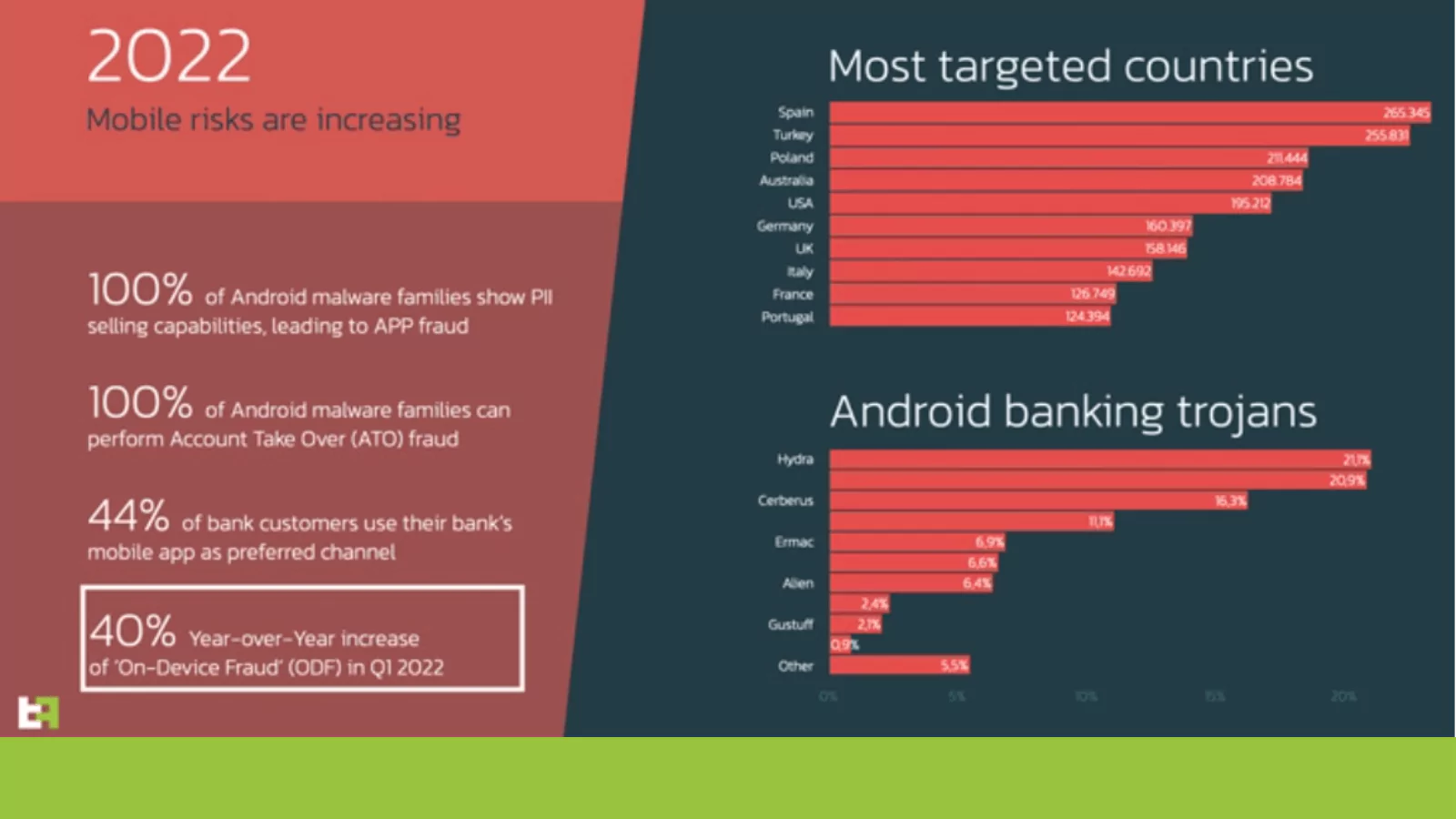
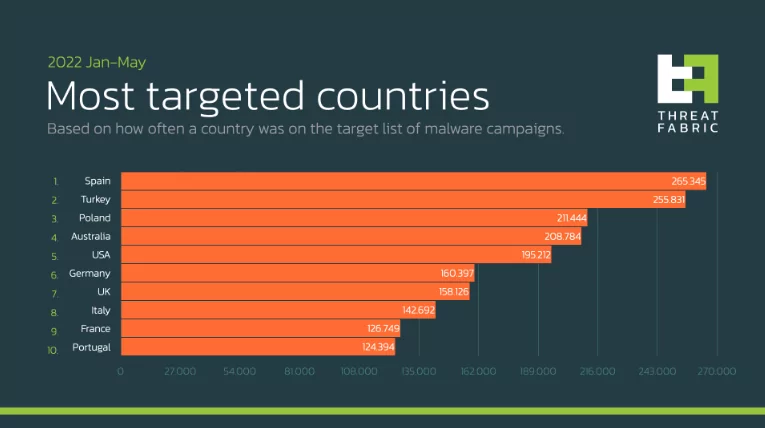
According to the 2022 mobile threat landscape analysis published byThreatFabric, ODF (on-device fraud) banking trojans targeting Android devices are widespread, while Spain and Turkey are at the center of malware campaigns. The other most targeted countries are Poland, Australia, the USA, Germany, the UK, Italy, and France.
ODF (On-Device fraud) Becoming Widespread
The point that ThreatFabric draws the most attention to is the trend of the ODF (on-device fraud) method. Since the beginning of 2022, there has been a close to 50% increase in cases of fraudulent exploitation of Android devices.
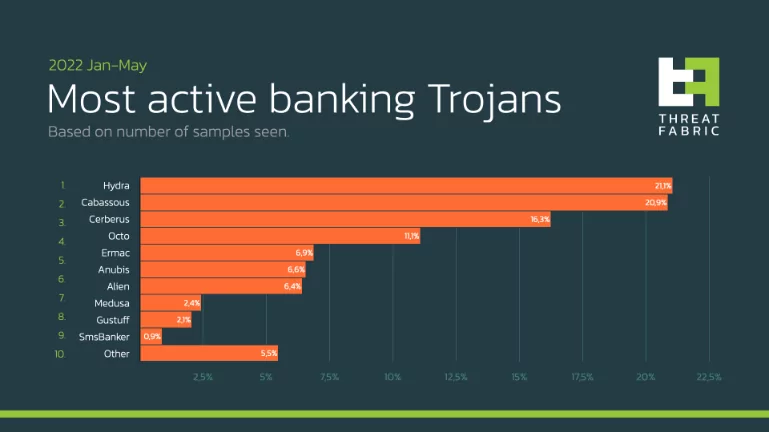
The most active banking trojans between January – May 2022 are Hydra, FluBot, Cerberus, Octo, and ERMAC.
Another notable phenomenon is that an increasing number of malware droppers have been observed in the Google Play Store. Here are some popular apps that are seemingly harmless but impersonate trusted apps, causing a security breach on devices:
- Nanu Cleaner
- QuickScan
- Chrome
- Play Store
- Pocket Screencaster
- BAWAG PSK Security
With the ODF method, the capabilities of banking trojans are also developing. For example, Octo, which has been on the agenda recently, can retrieve credentials from the compromised device even if the user does not click the “Login” button on the fake login screen.
Google Accessibility Service Sounds Alert
ERMAC, which emerged in September 2021, gained new capabilities that threaten crypto wallet applications by leveraging the Android Accessibility Service. Cybersecurity experts have almost agreed that the Accessibility Service is Android’s weakest point. By using this service, threat actors use reliable APIs and present fake login screens to users.
With Android 13, Google tries to make it harder to infect malware by restricting API access of apps installed from outside the Play Store.
Precautions May Be Inadequate
According to ThreatFabric, Google’s restrictions can be easily bypassed with a few simple configurations, and stricter measures are needed against this type of malware threat.
Users are responsible for avoiding malware campaigns. These include not downloading applications from outside the Google Play Store, making the right decision about which permissions to give to applications, and being more careful about sharing personal information.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































