
E-Commerce Threat Landscape Report: 17.4M Credit Card Information Sold
Attacks in the e-commerce industry are usually known to threaten financial information. When a user makes a payment, credit card data is stored in e-commerce sites, adding to billions of credit card data that can be harvested by potential attackers if not properly protected.
With the holiday season, there may be an upsurge in credit card theft. Databases containing customer credit card information are frequently sold on the black market and hacker forums before being recycled for use elsewhere.
Download the SOCRadar E-Commerce Threat Landscape Report for an in-depth analysis of the growing credit card fraud ecosystem.
Even Inactive Card Information Has Value
In the first eight months of 2022, 17.4 million credit card data was sold on the black market, according to the SOCRadar Financial Industry Threat Landscape Report.
Checkers are used to remove invalid and pointless numbers to determine whether a credit card number is currently in use. E-commerce websites are generally used for testing. Threat actors abuse victims’ credit cards to pay the testing fee, which is typically between $0.5 and $1.
According to experts, credit card information has some value on the dark web, even if it is not active. Because the subsequent attacker will take the same actions after purchasing the previously used credit card information, the new attacker will use a checker to determine the percentage of active cards. This most recent attempt using the same cards will cover up the evidence of the initial attacker.
Techniques of Credit Card Theft
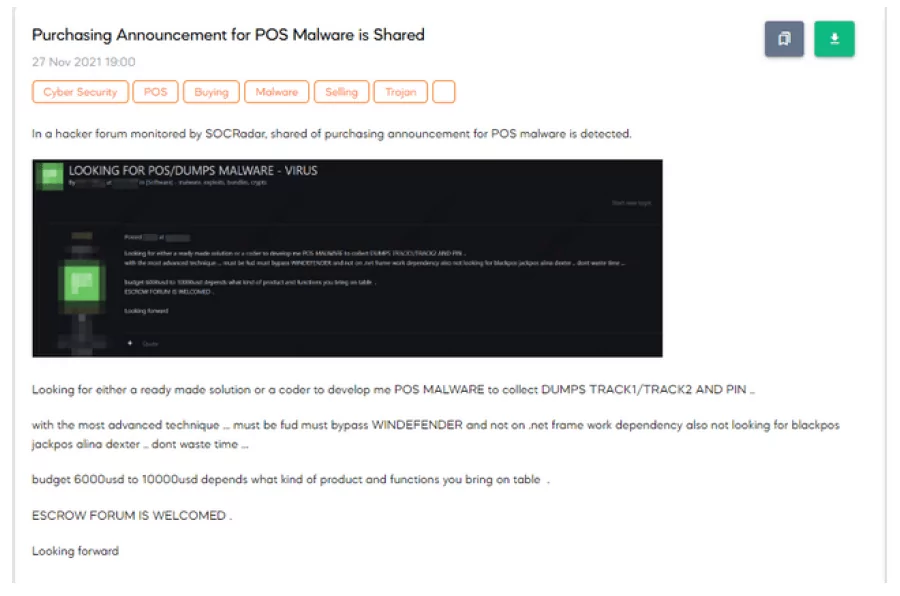
Credit Card Skimming: POS (point-of-sale) devices could be infected with malware (BlackPOS) and used to steal credit card information when a transaction is made. The data can then be directed to the attackers.
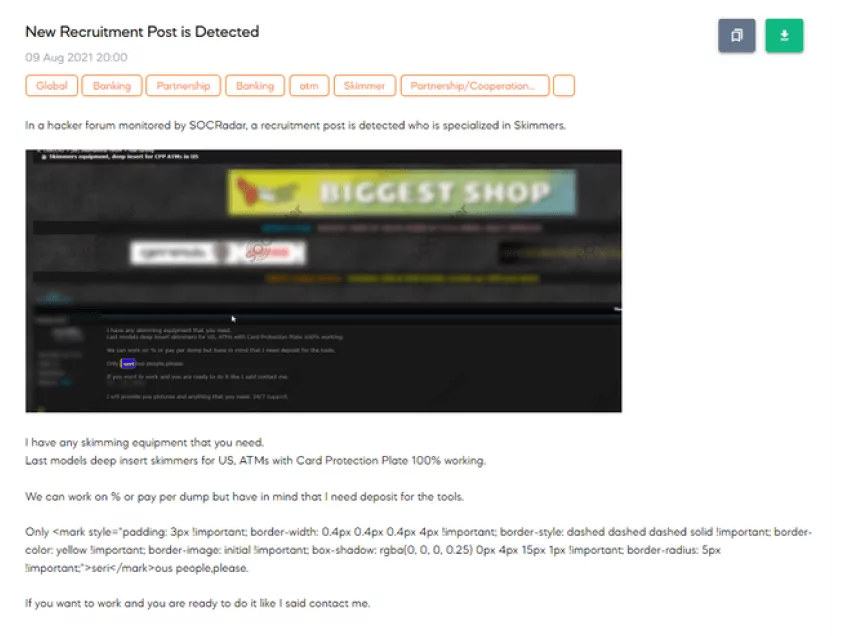
ATM Skimming: Threat actors can insert devices into card slots of ATMs. The device will steal card information when a person uses the ATM. The attackers additionally record the PIN with a small camera.
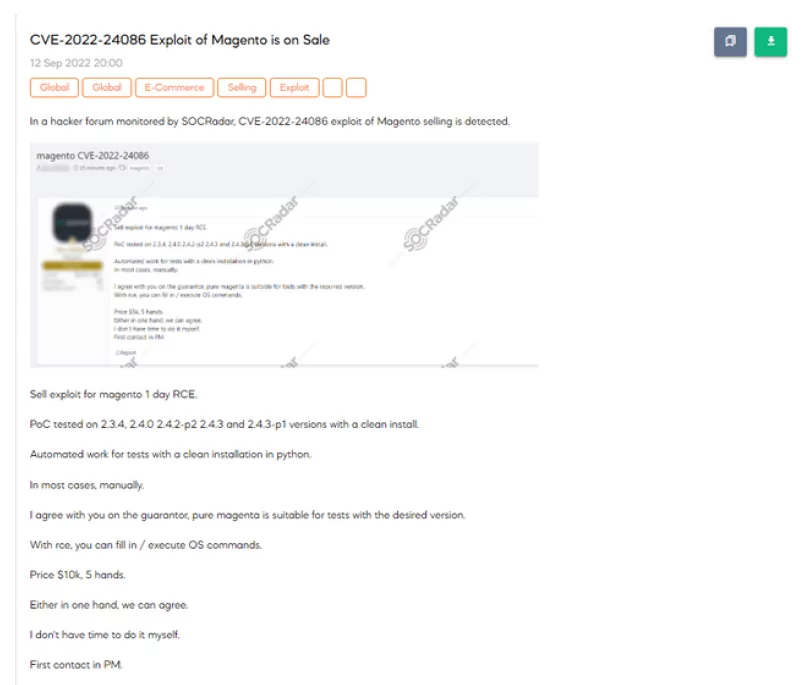
Online Skimming: Online skimming attacks are also possible. Online skimming threats are commonly named “Magecart attacks.” Attackers can access credit card data by infecting e-commerce websites’ checkout pages. The credit card information is copied and sent to the cybercriminals by this difficult-to-detect malware, which skims every interaction without either party being aware of the transaction.
There are also elements to credit card fraud; cybercriminals might come around in an organizational structure to carry out these attacks. Read the full report here to find out.
Origin of Magecart
Web skimming attacks are the primary method used by the well-known hacker group Magecart. They are becoming more prevalent in e-commerce and other sectors where customer bank card information is collected.
Below are a few of the well-known Magecart cases through the years:
- Over 380,000 credit cards were affected by payment card skimming software built on the British Airways website in 2018. Over three weeks, attackers stole payments made via the airline’s website and mobile app.
- On the NewEgg’s payments page, one of the largest retailers in the United States, hackers injected 15 lines of card skimming code, which remained for more than a month. The code steals credit card information sent to a server controlled by hackers with a similar domain name, presumably to avoid detection. To blend in, the server even used an HTTPS certificate.
- Segway, the company that makes two-wheeled self-balancing personal transporters, was another well-known hack in 2022. A malicious Magecart script was added to Segway’s online store because of the hack, which could have given threat actors access to customers’ credit card numbers and personal information.



































