Patch Released for CVE-2023-25194 RCE Vulnerability in Apache Kafka
The most recent patch for Apache Kafka fixes an unsafe Java deserialization vulnerability. The vulnerability, tracked as CVE-2023-25194, could be used to execute code remotely with authentication.
Apache Kafka is a widely used open-source platform for event streaming, employed by numerous companies for various purposes such as high-speed data transportation, analytical streaming, data consolidation, and important business operations.
How Critical Is the CVE-2023-25194 RCE Vulnerability?
The vulnerability has the potential to enable a remote attacker with authentication to run any code on the system. This is due to unsafe deserialization that occurs during the configuration of the connector through the Kafka Connect REST API.
An attacker could take advantage of this vulnerability by sending a specially crafted request, leading to arbitrary code execution or a denial of service on the system.
Although it has not yet received a CVSS score, the CVE-2023-25194 vulnerability in Apache Kafka has been considered important and affects versions 2.3.0 through 3.3.2 of the platform.
How Does It Affect?
To exploit the CVE-2023-25194 vulnerability, an attacker must have access to a Kafka Connect worker and be able to create and modify connectors that use an arbitrary Kafka client SASL JAAS configuration and a SASL security protocol. This has been possible on Kafka Connect clusters since Apache Kafka version 2.3.0.
An authenticated attacker can configure the sasl.jaas.config property for any of the connector’s Kafka clients to “com.sun.security.auth.module.JndiLoginModule“. It is possible via the following properties:
- producer.override.sasl.jaas.config
- consumer.override.sasl.jaas.config
- admin.override.sasl.jaas.config
The server establishes a connection to the LDAP server of the attacker and deserializes the LDAP response. The attacker can then use it to launch java deserialization gadget chains on the Kafka connect server.
The attacker can induce unrestricted deserialization of untrusted data if gadgets are in the classpath. The exploit can lead to remote code execution and enable the attacker to access other resources on the network.
Users can specify these properties in connector configurations for Kafka Connect clusters running with default configurations since Apache Kafka 3.0.0. Users could not specify these properties prior to Apache Kafka 3.0.0 unless the Kafka Connect cluster was configured with a connector client overridden by the policy that enabled it.
Check out the proof-of-concept (PoC) example on GitHub.
Recommendations
Starting from Apache Kafka version 3.4.0, a new system property named “-Dorg.apache.kafka.disallowed.login.modules” has been added to prevent the use of problematic login modules in SASL JAAS configurations.
Additionally, “com.sun.security.auth.module.JndiLoginModule” has been disabled by default in Apache Kafka 3.4.0.
Security researchers recommended that users of Kafka Connect validate their connector configurations and only permit trusted JNDI configurations.
They should also check the dependencies of their connectors for any vulnerable versions and take appropriate actions such as upgrading the connectors, upgrading the specific dependency, or removing the connectors.
Furthermore, besides utilizing the “org.apache.kafka.disallowed.login.modules” system property, users of Kafka Connect can also establish their own connector client configuration override policy to manage which Kafka client properties can be overridden directly in a connector configuration and which cannot.
Stay Safe with SOCRadar Vulnerability Intelligence
SOCRadar is a powerful platform for staying informed about the latest security threats and vulnerabilities.
The Vulnerability Intelligence module provides detailed information on all known vulnerabilities, presented in an actionable format, making it easier for you to take the necessary steps to protect your organization.
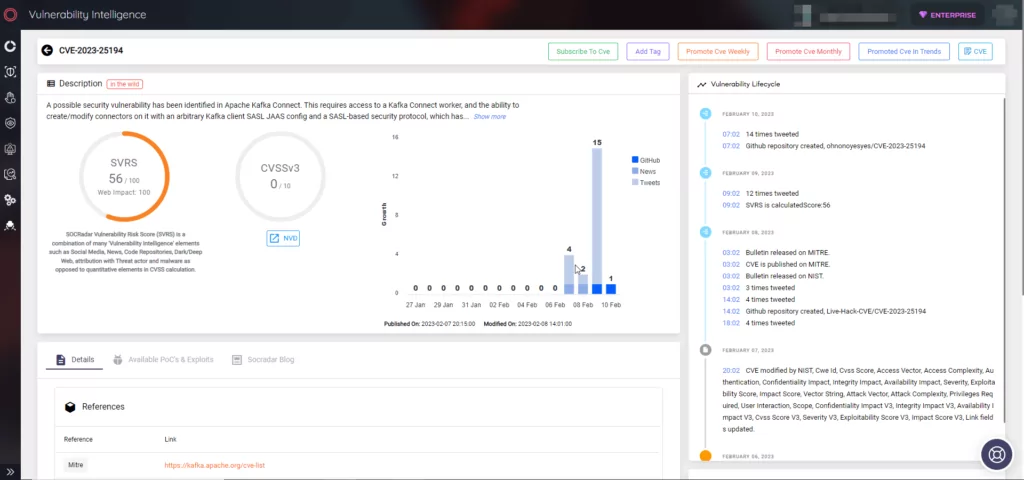
SOCRadar also includes External Attack Surface Management (EASM), which constantly scans your perimeter from the attackers’ point of view to discover digital assets and alert you to any emerging issues.
With SOCRadar, you can have the information you need to stay informed about potential risks and prioritize your security measures.