Fix Available for Double Free Vulnerability in OpenSSH 9.1 (CVE-2023-25136)
CVE-2023-25136, a pre-authentication double-free vulnerability, has been fixed in OpenSSH version 9.2p1. The vulnerability is highly severe, with a CVSS score of 9.8, and could be used to cause a denial-of-service (DoS) or remote code execution (RCE).
OpenSSH is a free and open-source tool for secure remote communication and access. Administrators and developers widely use it, and it is compatible with various operating systems.
CVE-2023-25136 affects the default configuration of OpenSSH version 9.1p1 (sshd).
How Does the CVE-2023-25136 Work?
The double-free vulnerability was discovered by Mantas Mikulenas and reported to OpenSSH Bugzilla in January 2023. The vulnerability was introduced in July 2022 and is caused by freeing the same memory location twice, which in this case is “options.kex_algorithms.” The first instance of freeing occurs through the do_ssh2_kex() function, which subsequently calls compat_kex_proposal().
When the compatibility bit “SSH_BUG_CURVE25519PAD” is not set and the compatibility bit “SSH_OLD_DHGEX” is set, “options.kex_algorithms” becomes a dangling pointer after being freed. This leads to the memory being freed again through kex_assemble_names() with “listp” being equal to “&options.kex_algorithms.”
Is it Easy to Exploit?
OpenSSH employs security mechanisms such as sandboxing and privilege separation, so creating a successful exploit can be difficult. Aside from its difficulty, the pre-auth double-free vulnerability, CVE-2023-25136, could be exploited for remote code execution (RCE) or denial-of-service (DoS) attacks.
In the event of a DoS attack, only the forked daemons crash due to a sandbox violation when attempting to execute writev(), while the main server daemon remains unaffected and can handle new clients.
Proof-of-Concept is Available
JFrog has provided a detailed analysis and proof-of-concept for the CVE-2023-25136 vulnerability, which is available on GitHub.
The DoS proof-of-concept triggers the double-free vulnerability using the paramiko package, resulting in an abort crash. The connecting client version banner is changed to reflect an outdated client such as PuTTY v0.64.
The RCE exploit works by allocating another struct named EVP_AES_KEY instead of the freed options.kex_algorithms. It is later freed again when the double-free occurs and then overwritten with another chunk using the authctxt->user or authctxt->style.
When EVP_Cipher() attempts to use the EVP_AES_KEY, it will use this overwritten chunk with attacker-controlled data.
Qualys Security has been able to use this double-free vulnerability to achieve limited remote code execution exploits when no memory protections such as ASLR or NX are applied.
Apply the Fix
The best way to protect yourself from this vulnerability is to update the latest version. Users are advised to update as soon as possible to ensure that their systems are not vulnerable to attack.
OpenSSH issued a security advisory on February 2, 2023, announcing the release of version 9.2p1. They noted that this version was significant due to the pre-auth double-free vulnerability (CVE-2023-25136). You can find the fix for this vulnerability by examining the commit made in OpenSSH’s GitHub repository.
How Can SOCRadar Help?
SOCRadar is an Extended Threat Intelligence platform that updates you on the latest security threats and vulnerabilities. It gathers data on all known vulnerabilities and presents it in an easy-to-use format, using alerts to help you prioritize your actions and inform you of potential risks to your organization. You can use SOCRadar’s Vulnerability Intelligence module to get detailed information on vulnerabilities, which can aid you in managing related issues and prioritizing patches when required.
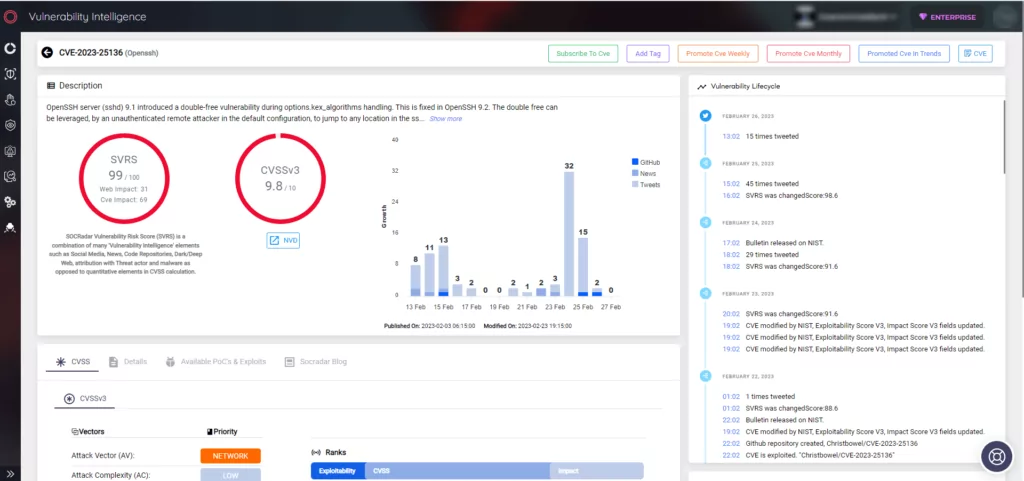
Moreover, its External Attack Surface Management (EASM) functionality can identify your digital assets and notify you of any potential threats.