
Cisco Releases Patches for Vulnerabilities in Multiple Products
Cisco, this week released updates to fix various security vulnerabilities in its products. These updates also cover serious issues affecting Secure Network Analytics and Identity Services Engine (ISE) products.
The vendor disclosed 25 vulnerabilities, including one critical vulnerability and five high-severity vulnerabilities.
Cisco Will Fix the Critical Vulnerability in Late April
CVE-2022-20812 (CVSS score: 9.0): The vulnerability exists in cluster database API and is caused by the insufficient validation of user-supplied command arguments. CVE-2022-20812 is a critical vulnerability that could allow a remote attacker to authenticate to the system with administrative read and write privileges and overwrite files with root privileges.
Affected products:
- Cisco Expressway Series
- Cisco TelePresence Video Communication Server (VCS)
Release 14.0.7 for the products above includes a partial fix for CVE-2022-20812. Release 14.3, due in late April, will provide a complete fix.
CVE-2023-20102 (CVSS Score: 8.8): The web-based management interface of Cisco Secure Network Analytics is susceptible to a vulnerability that could allow an authenticated, remote attacker to execute arbitrary code. Insufficient sanitization of user-provided data parsed into system memory is responsible for this vulnerability. An attacker could send a specially crafted HTTP request to an affected device to exploit the flaw.
Affected Products:
- Secure Network Analytics Manager
- Secure Network Analytics Virtual Manager
- Stealthwatch Management Console 2200
Cisco has addressed the issue with the release of Secure Network Analytics 7.4.1-Patch SMC Rollup #5.
CVE-2023-20121 and CVE-2023-20122 (CVSS Score: 7.8): Two security vulnerabilities have been discovered in the restricted shell of several Cisco networking products. If exploited by an authenticated, local attacker, these vulnerabilities could allow them to bypass the restricted shell and gain root privileges on the underlying operating system. You can find further information about these vulnerabilities in the details section of the corresponding advisory.
Affected Products:
- Cisco EPNM, Cisco ISE, and Cisco Prime Infrastructure (CVE-2023-20121)
- Cisco ISE (CVE-2023-20122)
CVE-2023-20122 has been resolved with the introduction of ISE version 3.2P1, and CVE-2023-20121 has been addressed with Cisco EPNM version 7.0.1.
Two other highly severe vulnerabilities, CVE-2023-20117 andCVE-2023-20128(CVSS score: 7.2),could allow an authenticated, remote attacker to execute arbitrary commands on affected devices.
Affected Products:
- Cisco Small Business RV320
- Cisco RV325 Dual Gigabit WAN VPN
Small Business RV320 and RV325 routers have reached EoL (end-of-life) and will not receive any patches to resolve the issue.
It is important to note that Cisco will not provide patches for multiple other vulnerabilities with medium severity ratings because the vulnerable products have already reached end-of-life. These products also include Small Business RV016, RV042, RV042G, and RV082 routers. Refer to Cisco’s end-of-life notices for these products.
There are no reports of exploitation regarding the vulnerabilities in this blog; however, it is urgently recommended to refer to Cisco’s vulnerability listing for more details about available patches or workarounds.
Detect, Prioritize, and Patch Vulnerabilities with SOCRadar
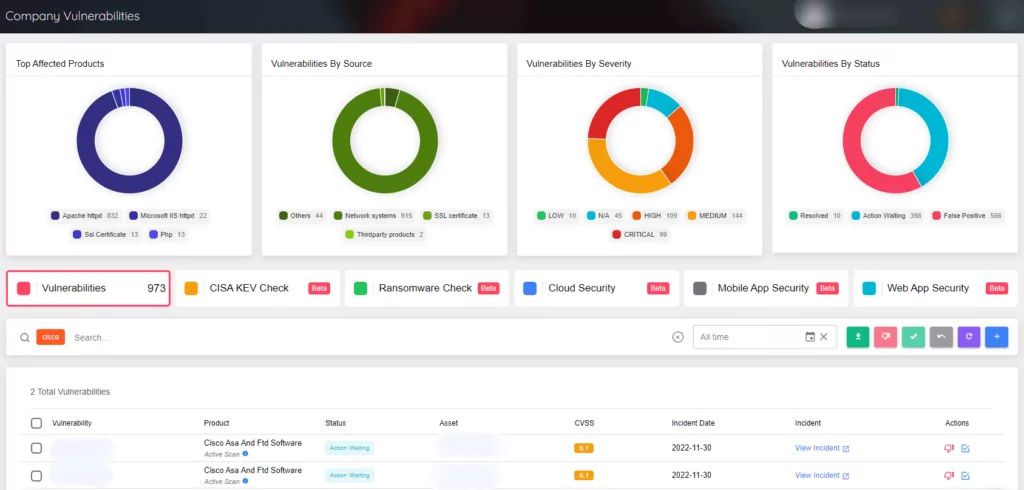
SOCRadar’s Attack Surface Management allows you to track vulnerabilities in automatically detected products in your organization’s digital footprint in real-time. Thus, it enables security teams to be proactive about vulnerabilities that must be prioritized by accessing contextual intelligence. Also, they can easily be aware of vulnerability trends that threat actors actively exploit, thanks to Vulnerability Intelligence in Cyber Threat Intelligence.



































