
MOVEit Exploit Sales, Doge RAT, and Bandit Stealer Malware
As we continue exploring the digital landscape’s obscure corners, the dark web remains an enigmatic yet critical part of the cyberspace ecosystem that continually impacts our increasingly interconnected world. Our weekly dispatch into this realm exposes various intriguing and alarming activities, shedding light on the clandestine operations that often remain hidden within the depths of the internet’s dark alleyways.
Join us as we dissect these alarming dark web findings, endeavoring to understand their implications for our shared cybersecurity.
Find out if your data has been exposed.
New Recruitment Post is Detected
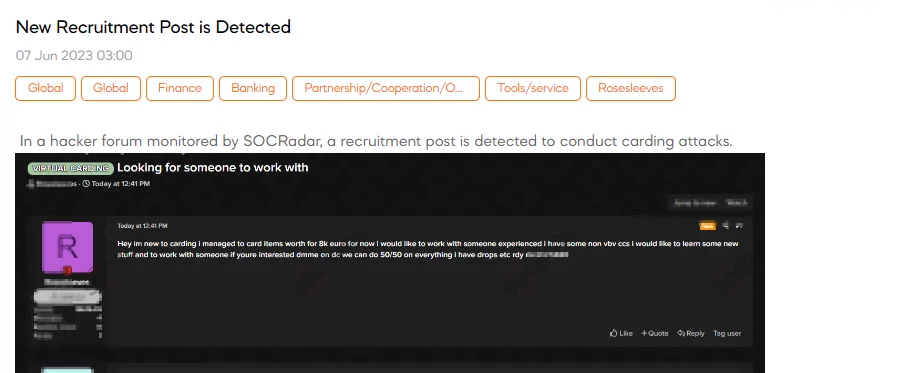
On June 7, SOCRadar dark web team identified a concerning post shared by a threat actor regarding recruitment for carding attacks. The post reveals that the individual admits to being new to carding and has successfully carried out fraudulent transactions amounting to 8,000 euros. They express a desire to collaborate with an experienced individual, possessing non-Verified by Visa (non vbv) credit cards, to learn and engage in further illicit activities. The post suggests a potential split of profits.
New Botnet Service is Detected
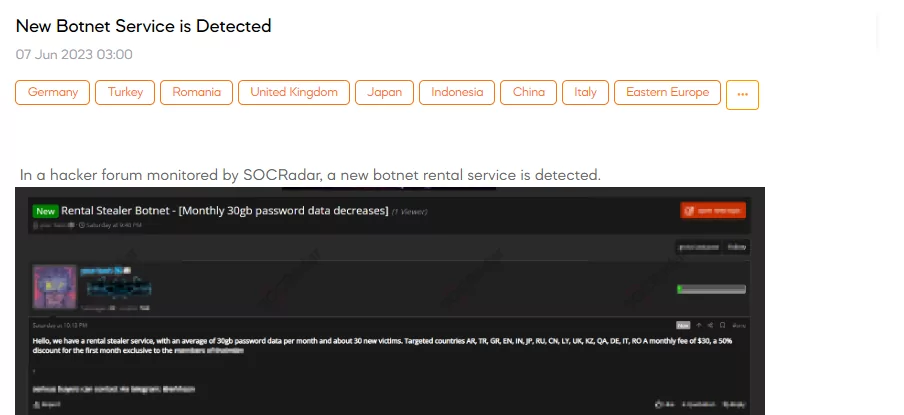
On June 29, a SOCRadar dark web analyst detected a concerning post by a threat actor claiming the existence of a new botnet rental service. According to the post, the service offers a rental stealer service with an average of 30GB of password data per month and around 30 new victims. The targeted countries include Argentina, Turkey, Greece, England, India, Japan, Russia, China, Libya, the United Kingdom, Kazakhstan, Qatar, Germany, Italy, and Romania. The service is offered at a monthly fee of $30, with an exclusive 50% discount for the first month for members of a specific group.
New RAT is Shared
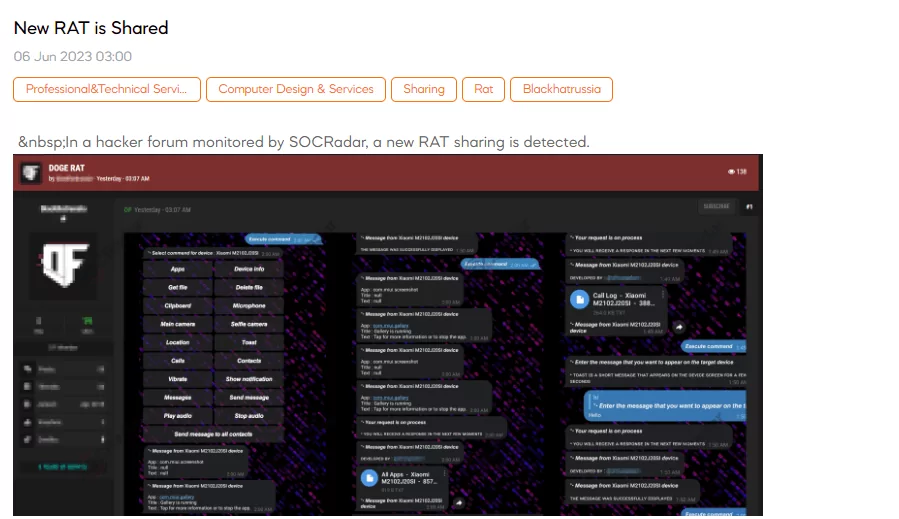
SOCRadar dark web team has detected a post by a threat actor claiming the existence of a new Remote Access Trojan (RAT) called Doge Rat. According to the threat actor, this RAT possesses various features, including real-time functionality, a custom web view, the ability to read and send notifications, displaying toast messages on the target device, obtaining information about the SIM card provider, vibrating the target device, tracking the device’s location, accessing all target messages, sending SMS to any number or all contacts on the target device, retrieving all target contacts, obtaining a list of installed apps, receiving files or folders from the target device, deleting files or folders on the target device, capturing images and videos from both the main and front cameras, recording audio from the microphone with customizable duration, retrieving the last copied text from the clipboard, automatically starting after device boot, and featuring an undetectable presence to antivirus software. Additionally, the threat actor mentions the presence of a keylogger and highlights the presence of a user-friendly Telegram bot interface.
Bandit Stealer is on Sale
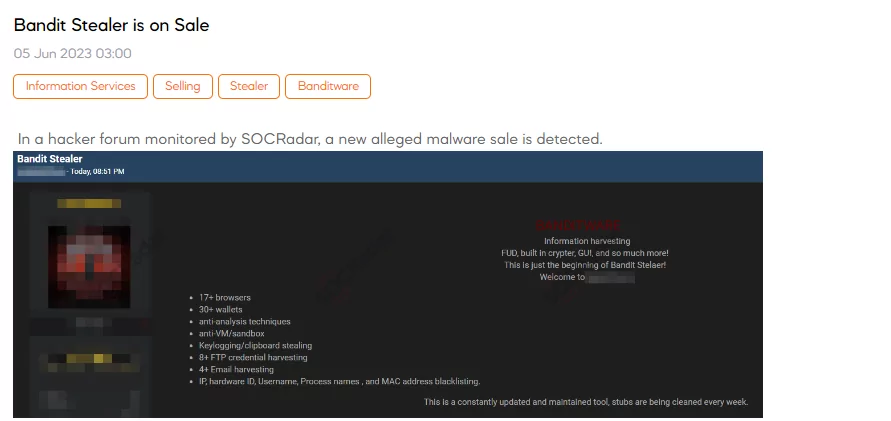
A SOCRadar dark web researcher has detected a concerning post in which a threat actor claims to be selling a new malware named “BANDITWARE.” According to the threat actor, this malware boasts various capabilities, including information harvesting, a fully undetectable (FUD) status, a graphical user interface (GUI), and more. The threat actor declares that Bandit Stealer is just the beginning and highlights its compatibility with over 17 web browsers, 30 cryptocurrency wallets, and its ability to evade analysis techniques, virtual machines (VMs), and sandboxes. Furthermore, the malware is said to possess keylogging, clipboard-stealing functionalities, and the ability to harvest FTP credentials and emails. Additionally, it incorporates features like blacklisting IP addresses, hardware IDs, usernames, process names, and MAC addresses. The threat actor emphasizes that this tool is continuously updated and maintained, with regular cleaning of its stubs
CVE-2023-34362 Exploit is Shared for MoveIT
A SOCRadar dark web researcher has detected a concerning post made by a threat actor who claimed the possibility of achieving Remote Code Execution (RCE) through a vulnerability in MoveIT Transfer software. MoveIT Transfer, developed by Ipswitch, is a managed file transfer (MFT) software widely used for secure data transfer. The specific vulnerability in question is tracked as CVE-2023-34362. Security researchers have previously investigated similar exploits, such as SQLi-to-RCE attacks targeting network edge systems. These vulnerabilities can provide unauthorized access to corporate networks, allowing attackers to execute code remotely, escalate privileges, and potentially compromise sensitive systems. Prompt action and appropriate security measures are crucial to mitigate the risk posed by this vulnerability.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































