
Attackers Exploit Critical Zero-Day Vulnerability in MOVEit Transfer
[Update] July 18, 2023: A notorious cybercrime group’s MOVEit attack has affected 340 organizations and over 18 million individuals. Added the subheading: “MOVEit Attack Impacts 340 Organizations, 18 Million Individuals.”
[Update] July 13, 2023: Pension Benefit Information (PBI) experienced a MOVEit breach that exposed the data of over 370,000 individuals. Added the subheading: “Pension Benefit Information Breached: Over 2.5M Individuals Affected.”
[Update] July 12, 2023: Deutsche Bank has confirmed that a data breach on one of its service providers has exposed customer data. Over 100 companies in more than 40 countries may be affected. Added the subheading: “Third-Party Data Breach: Deutsche Bank Customers’ Data Exposed.”
[Update] July 04, 2023: The financial information of Dublin airport employees has been compromised in a cyber-attack targeting Aon’s MOVEit file-transfer software. Added the subheading: “MOVEit Cyber-Attack Exposes Dublin Airport Staff’s Financial Data.”
[Update] June 22, 2023: Gen Digital, the parent company of Avast, Norton, AVG, and Avira, confirms data breach by Clop ransomware group’s MOVEit Transfer attacks. Added the subheading: “Avast and Norton’s Parent Gen Digital Confirms Data Breach.”
[Update] June 20, 2023: Clop ransomware has named PwC, Ernst & Young, and Medibank as new victims as part of the MOVEit Transfer campaign. Added under the subheading: “PwC, Ernst & Young, Medibank Breached in Clop’s MOVEit Attacks.”
[Update] June 15, 2023: Clop ransomware has started listing the victims who have not contacted them by June 14, 2023. Added under the subheading “Microsoft Links MOVEit Transfer Zero-Day Exploits to Lace Tempest.”
[Update] June 13, 2023: Added the subheading: “Proof-of-Concept Exploit (PoC) for MOVEit Transfer RCE Is Available.”
[Update] June 12, 2023: Minnesota Department of Education (MDE), Illinois Department of Innovation & Technology (DoIT), and University of Manchester have been breached due to the MOVEit vulnerability. See the subheading “MOVEit Vulnerability Affects State Departments and Education.”
[Update] June 9, 2023: New vulnerabilities have been identified. MOVEit Transfer customers are strongly advised to apply the patches. Added the subheading: “New Vulnerabilities Are Discovered in MOVEit (CVE-2023-35036).” Find the instructions under “Recommendations.”
[Update] June 9, 2023: Researchers found that Clop ransomware gang has tried to exploit the MOVEit Transfer vulnerability since 2021. Added the subheading: “Clop Ransomware Attacks on MOVEit Transfer Traced Back to 2021.”
[Update] June 7, 2023: The Clop ransomware gang claims to have stolen data from hundreds of companies that use the vulnerable MOVEit product. Added under the subheading: “Microsoft Links MOVEit Transfer Zero-Day Exploits to Lace Tempest ”.
[Update] June 6, 2023: Microsoft has linked MOVEit’s exploitation to the Cl0p ransomware group, which they refer to as “Lace Tempest.” Added the subheading: “Microsoft Links MOVEit Transfer Zero-Day Exploits to Lace Tempest ”.
[Update] June 5, 2023: CISA has added CVE-2023-34362 to its Known Exploited Vulnerabilities (KEV) list.Added the subheading: “CISA Lists CVE-2023-34362 in Known Exploited Vulnerabilities and Orders Agencies to Patch”.
Cybercriminals are actively exploiting a critical zero-day vulnerability in MOVEit Transfer. Attackers could exploit the vulnerability with SQL injection (SQLi) to execute remote code and steal data from targeted organizations.
MOVEit Transfer is a managed file transfer (MFT) software; its developer is Ipswitch, a subsidiary company of the Progress Software Corporation in the US.
Progress Software issued an advisory on May 31, 2023, alerting customers of the critical vulnerability in the MOVEit Transfer. The vulnerability is tracked as CVE-2023-34362.
How Can the Vulnerability Affect MOVEit Transfer Users?
Researchers previously investigated SQLi-to-RCE exploits in network edge systems. These vulnerabilities can grant threat actors initial access to corporate networks. Attackers can perform remote code execution (RCE), escalate privileges, and potentially gain unauthorized access to systems by exploiting the vulnerability.
In the advisory, Progress Software does not explicitly confirm ongoing exploitation. Still, they strongly urge their customers to remain vigilant for signs of unauthorized access in the span of the last 30 days.
Which Versions Are Affected?
Researchers from Rapid7 have seen the exploitation of the vulnerability across multiple customer environments and report that there has been an increase in related threat activity since the advisory’s release.
Greynoise, a threat intelligence firm, detected scanning activity targeting MOVEit Transfer’s login page at /human.aspx as early as March 3, 2023.
Approximately 2,500 MOVEit Transfer instances, primarily in the United States, are vulnerable to this vulnerability.
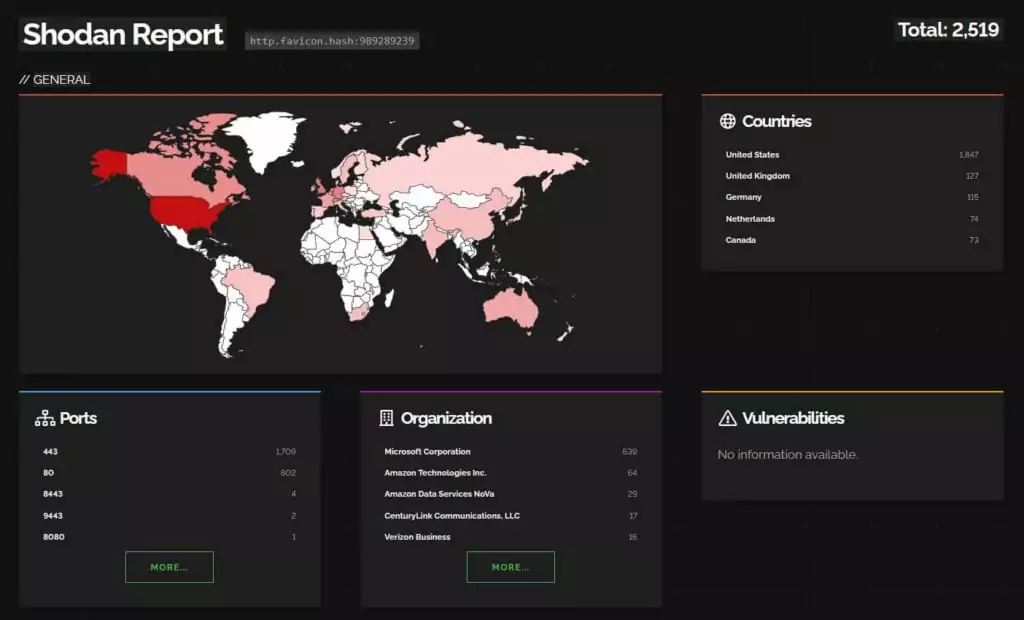
Affected MOVEit Transfer versions and their corresponding fixed versions are listed below:
- MOVEit Transfer 2023.0.0 → MOVEit Transfer 2023.0.1
- MOVEit Transfer 2022.1.x → MOVEit Transfer 2022.1.5
- MOVEit Transfer 2022.0.x → MOVEit Transfer 2022.0.4
- MOVEit Transfer 2021.1.x → MOVEit Transfer 2021.1.4
- MOVEit Transfer 2021.0.x → MOVEit Transfer 2021.0.6
- MOVEit Transfer 2020.1.x → Special Patch Available
You can apply the necessary fixes to address the vulnerability by following this link.
Proof-of-Concept Exploit (PoC) for MOVEit Transfer RCE Is Available
Researchers from Rapid7 have examined the issue by patch diffing, which compares the vulnerable version of the software to the fixed version, and discovered that the exploit is rather complex and requires chaining numerous issues in software implementation.
Researchers have made the PoC exploit available on GitHub and provided technical analysis to demonstrate it.
Microsoft Links MOVEit Transfer Zero-Day Exploits to Lace Tempest
According to Microsoft, the attacks exploiting the CVE-2023-34362 zero-day vulnerability in MOVEit Transfer are attributed to a threat actor known as Lace Tempest. Lace Tempest is notorious for its involvement in ransomware operations and operates the Clop extortion site. This threat actor has a history of exploiting similar vulnerabilities to steal data and extort their victims.
Notable victims of the campaign have recently come to light, including the government of Nova Scotia and UK payroll company Zellis, affecting high-profile clients such as Boots, the BBC, and British Airways.
The Cl0p ransomware gang claims to have stolen data from hundreds of companies that use the vulnerable MOVEit product. The threat actor threatened to publish the names and data of the companies on June 14 unless they contacted them and negotiated a ransom payment.
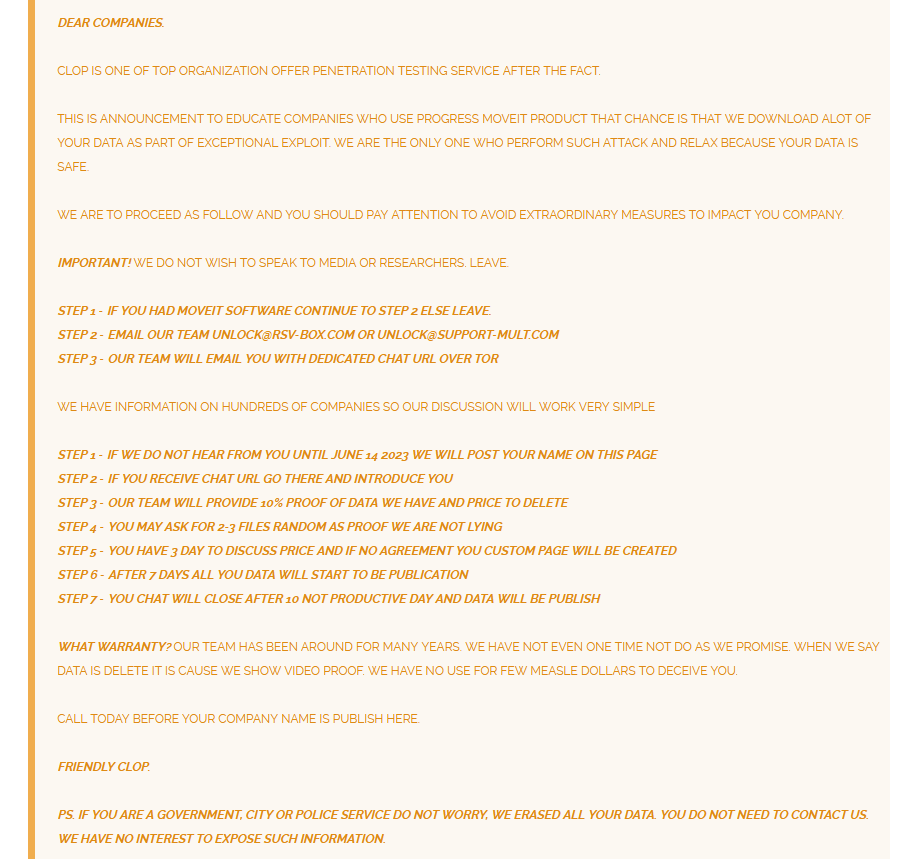
Clop ransomware has started listing its victims after the time period allotted on its announcement. The threat actor had threatened that if victims did not contact them by June 14 and reach an agreement, they would post the company names on the page. As of June 15, the threat actor’s leak site lists the names of 12 companies:
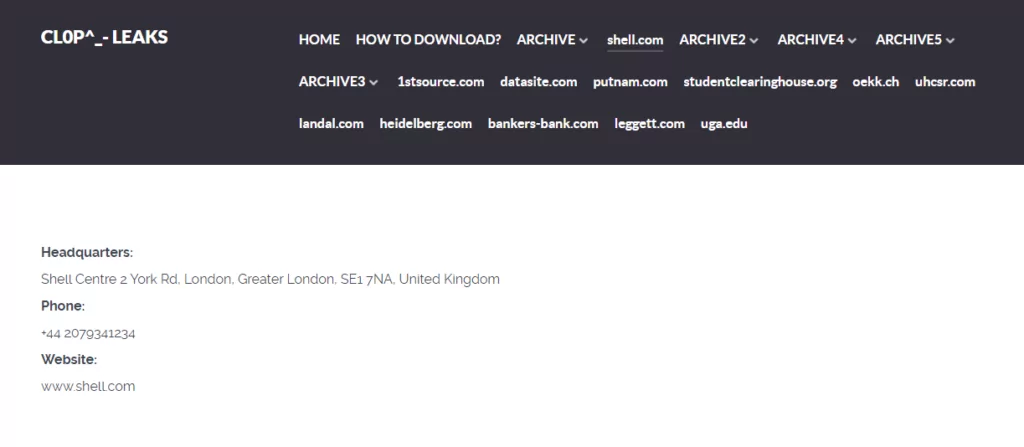
So far, the victim list of Cl0p seems to include the major global energy company Shell, banking industry companies 1st Source Bank and FNBB (bankers-bank[.]com), Software-as-a-Service (SaaS) provider Datasite, investment firm Putnam, the National Student Clearinghouse, insurance firms ÖKK (OEKK) and United Healthcare Student Resources (UHCSR), the holiday villages network Landal Green Parks, technology manufacturer and printing major Heidelberg, multi-sector furnisher Leggett & Platt, and the University of Georgia.
Clop Ransomware Attacks on MOVEit Transfer Traced Back to 2021
Kroll researchers discovered an automated exploitation attack chain that led to the deployment of the human2.aspx web shell in MOVEit Transfer on May 27. They discovered that the threat actor’s method in LemurLoot web shell deployments in recent attacks connected with early malicious activity and found similar activity in various client environments dating back to April 2022, with some instances traced as far back as July 2021.
The threat actors have been testing methods to collect sensitive data from compromised MOVEit Transfer servers since April 2022. Noteworthy exploitation activity occurred on April 27, 2022, May 15-16, 2023, and May 22, 2023.
The intensity of the activity increased on May 15, 2023, preceding the mass exploitation of the MOVEit zero-day bug starting on May 27. This timeline suggests that the Clop ransomware gang strategically planned the attack, waiting for the right tools since July 2021.
MOVEit Vulnerability Affects State Departments and Education
Minnesota Department of Education (MDE), Illinois Department of Innovation & Technology (DoIT), and the University of Manchester disclosed breaches on June 9, 2023, caused by the MOVEit vulnerability.
The MDE announced that a data server was breached, and 24 files were accessed. The files contain information about various students, including 95,000 students in foster care. According to MDE, financial information was not compromised during the breach, and they have not detected any traces of malware within their systems.
DoIT and the University of Manchester have not disclosed any information about their experiences during the breach, and it is unclear whether any data was stolen from these organizations as of yet.
All three organizations are investigating the incidents with the assistance of experts and will notify affected parties of any further information.
PwC, Ernst & Young, Medibank Breached in Clop’s MOVEit Attacks
The Clop ransomware group has targeted PricewaterhouseCoopers (PwC), one of the big four accounting firms, and claims to have obtained client data due to vulnerabilities in the MOVEit software that PwC used for transferring confidential information.
PwC acknowledged that the hack had affected a small number of clients since they used the software in limited engagements. The firm has taken immediate action by discontinuing the use of MOVEit software, reaching out to the affected clients, and initiating an investigation.
In addition to PwC, Medibank and another big four accounting firm, Ernst & Young (EY), have also fallen victim to attacks, as they also used MOVEit in business operations. Currently, Ernst & Young is uncertain about the breach of their data, while Medibank has stated that they have not yet discovered any compromise of customer data.
Avast and Norton’s Parent Gen Digital Confirms Data Breach
Gen Digital, the parent company of renowned antivirus names Avast, Norton, AVG, and Avira, has suffered a data breach as a result of the Cl0p ransomware group’s MOVEit Transfer attacks.
On June 20, 2023, the company confirmed the breach, revealing that personal information, including employee names, addresses, IDs, and email addresses, had been compromised.
Gen Digital has stated that their core IT systems, services, as well as customer and partner data are unaffected. The company has patched the vulnerabilities and is investigating the incident.
MOVEit Cyber-Attack Exposes Dublin Airport Staff’s Financial Data
According to the Dublin Airport Authority (DAA), some employees’ financial information at Dublin airport has been compromised due to a cyber-attack on Aon, a third-party professional service provider. The attack, which targeted Aon’s file-transfer software, MOVEit, affected approximately 2,000 Dublin airport employees, as well as several other organizations in the US and UK.
The Cl0p ransomware gang has claimed responsibility for the hacking of MOVEit. As of now, Aon has not provided any comments on the incident. The DAA has stated that it is providing support and assistance to the affected employees, although no further details were given.
Third-Party Data Breach: Deutsche Bank Customers’ Data Exposed
Deutsche Bank has confirmed that a data breach on one of its service providers has exposed customer data in a likely MOVEit Transfer data-theft attack. Over 100 companies in more than 40 countries may be affected, which is believed to be linked to the Clop ransomware’s MOVEit attacks.
The bank’s own systems were not compromised. The incident impacted German customers who used the account switching service in 2016, 2017, 2018, and 2020, but only a limited amount of personal data was exposed.
The number of affected clients is unknown, but they have been notified and advised on necessary precautions. The bank is investigating the causes of the breach and taking steps to improve data security.
While unauthorized account access is not possible with the exposed data, unauthorized direct debits may be attempted. To mitigate this risk, the bank has extended the period for returning unauthorized direct debits to 13 months.
Other banks, including Commerzbank, Postbank, Comdirect, and ING, were also impacted by the breach.
Pension Benefit Information Breached: Over 2.5M Individuals Affected
Pension Benefit Information (PBI), a population management solutions vendor, experienced a breach that exposed the data of over 370,000 individuals due to the MOVEit vulnerability. The breach resulted in the unauthorized access and exfiltration of names, partial mailing addresses, Social Security numbers (SSN), and dates of birth.
PBI is the United States’ most extensive obituary database, catering to a wide range of organizations. It assists pension funds, insurance companies, and alike in determining qualification for benefits.
The breach also affected other companies utilizing PBI as a third-party vendor. US insurer Wilton Re reported that the details of nearly 1.5 million people were exposed, while CalPERS, the largest public pension fund in the US, stated that 769,000 individuals’ names, birth dates, and SSNs are possibly compromised.
MOVEit Attack Impacts 340 Organizations, 18 Million Individuals
A notorious cybercrime group’s MOVEit attack has affected 340 organizations and over 18 million individuals. Among the victims are 58 US educational institutions, including Colorado State University.
The attackers, known for using Cl0p ransomware, now possess a massive amount of data, raising concerns about potential business email compromise (BEC) and phishing attacks.
Notable victims include Zellis, a UK-based payroll and HR company, as well as Emerson, Siemens Energy, Schneider Electric, Shutterfly, and several German banks.
The cybercriminals are publishing stolen files from organizations refusing to pay ransoms, but they claim to have deleted all data taken from government agencies. Security experts suspect the attackers exploited a zero-day vulnerability in the MOVEit software.
CISA Lists CVE-2023-34362 in Known Exploited Vulnerabilities
The Cybersecurity and Infrastructure Security Agency (CISA) has included the CVE-2023-34362 vulnerability, which has been recently exploited, in its Known Exploited Vulnerabilities (KEV) list and directed U.S. federal agencies and private companies to patch their systems by June 23, 2023.
Details of the MOVEit Transfer SQL Injection Vulnerability
Here are the details about the exploitation of the vulnerability:
- The compromised servers contain a web shell called ‘human2.asp’ in their public HTML folder.
- The web shell code checks for a specific password-like value in the inbound request’s header and returns a “Not Found” error if it is not present.
- Analysis reveals that with the correct password, the web shell executes commands based on specific request headers.
- Threat actors can perform various actions, including retrieving file details, manipulating users, and accessing Azure Blob Storage account information.
- Multiple randomly named App_Web_
.dll files have been found on breached servers. - The attacks began on May 27 and have been associated with several IP addresses.
- The vulnerability also impacts the MOVEit Transfer SaaS and MOVEit Cloud platforms, expanding the potential number of victims.
- Progress Software, promptly responded by taking down MOVEit Cloud, informing customers, and providing mitigation steps and patches.
Recommendations
To ensure the security of MOVEit Transfer servers and prevent exploitation, Progress Software recommends administrators implement the following measures:
- Whitelist traffic on ports 80 and 443 to the MOVEit Transfer server. This action will prevent external access to the web user interface (UI), as well as prevent the functioning of some MOVEit Automation tasks, APIs, and the Outlook MOVEit Transfer plugin. You can still utilize the SFTP and FTP/s protocols for file transfers.
- Inspect the C:MOVEit Transferwwwroot folder for suspicious files, such as backups or large file downloads. The presence of such files could potentially indicate data theft.
There is no further information on the zero-day vulnerability. It is likely a web-facing vulnerability based on the blocked ports and the specific folder highlighted for unusual file detection.
Charles Carmakal, the CTO of Mandiant, advises organizations to patch their systems, conduct forensic investigations, and prepare for possible data extortion or disclosure.
It is crucial to apply the new patch, released on June 9, 2023, to mitigate potential vulnerabilities. You can find comprehensive instructions on the necessary steps in the MOVEit Transfer Knowledge Base Article (June 9, 2023).
Similarly, MOVEit Cloud customers are advised to refer to the MOVEit Cloud Knowledge Base Article (June 9, 2023) for further details and instructions pertaining to their systems.
How Can SOCRadar Help?
SOCRadar provides monitoring capabilities for digital assets to ensure you are promptly informed of any emerging threats. The platform delivers real-time security alerts, allowing you to take immediate action in response to identified issues and prioritize patches.

SOCRadar External Attack Surface Management (EASM) can identify critical ports and conduct continuous monitoring. Using the platform, organizations can significantly mitigate the potential attack vectors that malicious actors may exploit to compromise internal systems.
Furthermore, SOCRadar’s Vulnerability Intelligence offers comprehensive vulnerability details to keep you up-to-date with the latest trends in exploitation.
Indicators of Compromise (IoC)
IPs Address:
- 138.197.152[.]201
- 209.97.137[.]33
- 5.252.191[.]0/24
- 148.113.152[.]144
- 89.39.105[.]108
- 5.252.189[.]0/24
- 5.252.190[.]0/24
- 5.252.191[.]0/24
- 198.27.75[.]110
- 209.222.103[.]170
- 84.234.96[.]104
User Display Name:
- Health Check Service
Folder Path:
- C:WindowsTEMP[random][random].cmdline
Filename:
- human2.aspx
- human2.aspx.lnk
HTTP POST:
- POST /moveitisapi/moveitisapi.dll
- POST /guestaccess.aspx
- POST /api/v1/folders/[random]/files
SHA256 Hash:
- 0b3220b11698b1436d1d866ac07cc90018e59884e91a8cb71ef8924309f1e0e9
- 110e301d3b5019177728010202c8096824829c0b11bb0dc0bff55547ead18286
- 1826268249e1ea58275328102a5a8d158d36b4fd312009e4a2526f0bfbc30de2
- 2ccf7e42afd3f6bf845865c74b2e01e2046e541bb633d037b05bd1cdb296fa59
- 58ccfb603cdc4d305fddd52b84ad3f58ff554f1af4d7ef164007cb8438976166
- 98a30c7251cf622bd4abce92ab527c3f233b817a57519c2dd2bf8e3d3ccb7db8
- a8f6c1ccba662a908ef7b0cb3cc59c2d1c9e2cbbe1866937da81c4c616e68986
- b5ef11d04604c9145e4fe1bedaeb52f2c2345703d52115a5bf11ea56d7fb6b03
- cec425b3383890b63f5022054c396f6d510fae436041add935cd6ce42033f621
- ed0c3e75b7ac2587a5892ca951707b4e0dd9c8b18aaf8590c24720d73aa6b90c
- 0b3220b11698b1436d1d866ac07cc90018e59884e91a8cb71ef8924309f1e0e9
- 110e301d3b5019177728010202c8096824829c0b11bb0dc0bff55547ead18286
- 1826268249e1ea58275328102a5a8d158d36b4fd312009e4a2526f0bfbc30de2
- 2ccf7e42afd3f6bf845865c74b2e01e2046e541bb633d037b05bd1cdb296fa59
- 58ccfb603cdc4d305fddd52b84ad3f58ff554f1af4d7ef164007cb8438976166
- 98a30c7251cf622bd4abce92ab527c3f233b817a57519c2dd2bf8e3d3ccb7db8
- a8f6c1ccba662a908ef7b0cb3cc59c2d1c9e2cbbe1866937da81c4c616e68986
- b5ef11d04604c9145e4fe1bedaeb52f2c2345703d52115a5bf11ea56d7fb6b03
- cec425b3383890b63f5022054c396f6d510fae436041add935cd6ce42033f621
- ed0c3e75b7ac2587a5892ca951707b4e0dd9c8b18aaf8590c24720d73aa6b90c




































