
Customer Story: How SOCRadar Stopped a BEC Attack on Track?
“Hello Alice,
ABC company is one of our new business partners. The invoice attached needs to be taken care of today. This is high priority.
Regards,
Bob,
CFO, XYZ”
This email could be perfectly normal and innocent in most cases, but it could also mean Bob’s account is compromised, and Alice was targeted by a Business Email Compromise (BEC) attack.
In the BEC attack, threat actors aim to trick and persuade employees of the victim company to take a specific action, such as making a wire transfer, providing funds to pay for an allegedly new project, or providing confidential information.
To make this type of attack work, hackers compromise corporate email accounts or create new accounts almost identical to the legitimate ones. Then attackers impersonate the owners of the email accounts and send messages to the victims. Common themes in these messages are a sense of urgency and importance since the criminals often impersonate high-level directors or executives, such as CEOs and CFOs.
Almost anyone could fall victim to these attacks. For example, at some point, Facebook, Google, Toyota, Ubiquiti Networks, the Government of Puerto Rico, and the City of Saskatoon were all victims of BEC attacks. According to FBI Internet Crime Report 2022, the Internet Crime Complaint Center received almost 22,000 BEC complaints with adjusted losses of over $2.7 billion.
In the case we will discuss here, we will see how SOCRadar stopped a BEC attack before it even started.
One of the things SOCRadar does perfectly is constantly scanning and monitoring of open internet for your brand and for the keywords our clients provide. We found a URL with our client’s brand name in one of these scans.
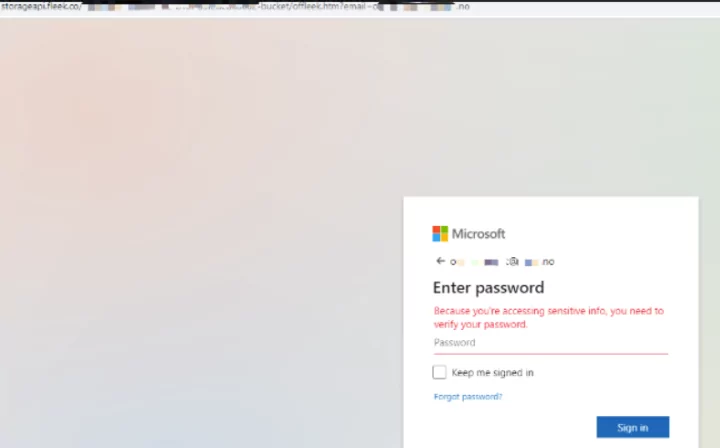
Further investigation made us realize that this is a fake landing page for the Microsoft Outlook email page for a spear phishing attempt. Our analysts realized the targeted person should be a C-level executive. However, our customer’s list of VIP protection was not very extensive and not up-to-date. VIP protection is one SOCRadar’s services to provide extra protection to high-level directors or executives and warn them if their name or any kind of PII is detected on the open or dark web.
If we get back to our case, our analysts found out that the target was the CFO of the client. Our analyst team and Technical Account Manager contacted the client’s security team, reported the findings, and warned the customer against spear phishing and BEC attack attempts. Of course, we also took action to takedown the fake landing page.
BEC Attacks Cost About $150K
Business Email Compromise attacks refer to fraudulent schemes that exploit business email systems to gain unauthorized access to a company’s internal systems. This type of cybercrime can be classified as a form of phishing, in which an attacker attempts to trick an employee into divulging confidential information or initiating financial transactions that result in theft. These scams use various tactics to breach email accounts and can cause significant financial losses, particularly by targeting high-level executives and employees. On average, firms worldwide have suffered financial damages of around $140,000 due to BEC attacks.



































