
How to Identify Spear Phishing Attacks
Spear phishing remains one of the most effective tactics cybercriminals use to breach enterprise networks. These highly targeted attacks have only increased in recent years, particularly with the rise of remote work, where employees may lack the robust IT security infrastructure in office settings. As cyber threats evolve, understanding how spear phishing works and how to detect it is critical for protecting sensitive data.
What is Spear Phishing?
Spear phishing is a type of phishing in which attackers personalize malicious emails or messages for a specific person or organization. Unlike general phishing attacks, which are sent to many people, spear phishing is more targeted and convincing, frequently using information about the target to appear legitimate.
The goal is to trick the recipient into disclosing sensitive information, such as login credentials or financial information, or to convince them to install malicious software. This type of attack is commonly used in cyber espionage and fraud.
The Mechanics of Spear Phishing
Spear phishing attacks are meticulously planned, frequently starting with extensive research on the target. Cybercriminals use personal and professional information from social media profiles, company websites, and other online sources to fabricate convincing pretexts. This information enables them to impersonate trusted contacts while making their fraudulent communications appear legitimate.
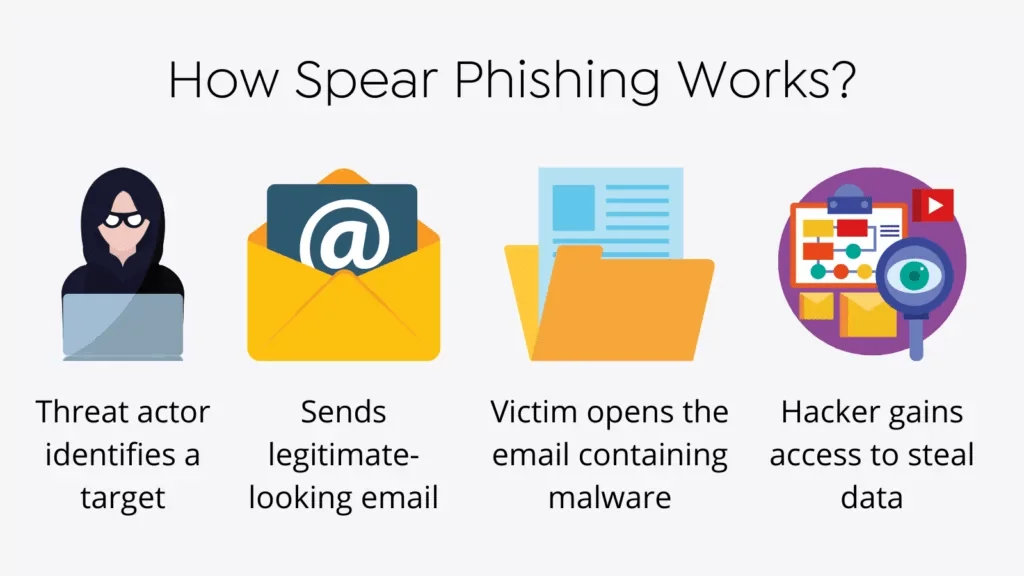
A simple diagram describing a typical spear phishing attack.
Once the attacker has established a credible pretext, they will create an email tailored to the victim. These emails frequently appear from someone the victim knows or regularly interacts with, increasing the likelihood that the victim will trust the message. The email may include a malicious attachment or link that, if opened, can result in significant security breaches, such as unauthorized access to sensitive data or systems.
Recent Example: Blind Eagle Hackers Exploit Spear-Phishing in Latin America
Blind Eagle, also known as APT-C-36, has been active since at least 2018. The group primarily targeted entities and individuals in Colombia, Ecuador, Chile, Panama, and other Latin American countries. Blind Eagle is notorious for its persistent spear-phishing campaigns, which have targeted key industries such as government, finance, energy, and oil and gas.

Attorney General’s Office impersonating email (Source: securelist by Kaspersky)
This threat actor group impersonated government agencies and financial institutions and sent phishing emails containing malicious links or attachments, such as PDFs or Word documents. Once opened, these redirect victims to attacker-controlled websites that use customized Remote Access Trojans (RATs) such as AsyncRAT, which are used for spying, financial theft, and cyber espionage.
Blind Eagle employs techniques such as process hollowing to inject malicious code into legitimate processes, effectively evading detection by security defenses. The group’s adaptability and straightforward yet effective tactics, including open-source RATs, make them a significant and ongoing threat in the region.
How to Spot Spear Phishing Attacks
- Sender Email Address and Name: Always check the sender’s email address and name for discrepancies. Spear phishers often use spoofed email addresses and domains to appear legitimate.
- Urgency and Pressure: Attackers may create a sense of urgency, pushing you to act quickly without verifying the request.
- Check for Suspicious Links and Attachments: Always hover over any links in an email to see the actual URL before clicking. Spear phishing attacks often use links that appear legitimate but lead to malicious websites designed to steal your information. Similarly, be cautious of attachments, particularly if they are from an unknown sender or seem out of context. Common file types used in attacks include PDFs, Word documents, and Excel files.
- Unusual Requests: Be cautious if the email requests sensitive information, unexpected payments, or login credentials.
- Timing and Context: The timing of the email can play a crucial role. If the email arrives at an unusual time or context, it could be an indicator.
Recommendations Against Spear Phishing Attacks
- Be Cautious with Links and Attachments
Before clicking on any link or downloading an attachment, hover over the link to check the URL and scrutinize the file type. Cybercriminals often use familiar file formats like PDFs or Word documents to deliver malware. If something seems off, do not click on it, and report the email to your IT department.
- Employee Security Awareness Training
Regular training sessions can equip employees with the knowledge to identify and respond to spear-phishing attempts. Awareness programs should include real-world examples of spear-phishing tactics and emphasize the importance of vigilance. To learn more about security awareness training tools and capabilities, check out our blog post, Top 10 Phishing Simulation Tools.
- Implement Advanced Email Security Solutions
Deploy advanced email filtering and security solutions to detect and block spear-phishing emails. These tools often use machine learning and AI to identify suspicious patterns and prevent malicious emails from reaching the inbox.
- Enforce Multi-Factor Authentication (MFA)
Implementing MFA across all critical systems adds an extra layer of security. Even if attackers manage to steal credentials through spear phishing, MFA can prevent unauthorized access by requiring a second form of verification.
- Develop an Incident Response Plan
Create and regularly update an incident response plan designed to address spear-phishing attacks. This plan should outline the steps to take when an attack is suspected, including immediate containment and notification procedures.
SOCRadar’s Incident Response can help you better defend against spear phishing. As targeted attacks increase, SOCRadar strengthens your team by providing critical insights into attacker methods, motivations, and techniques. Real-time intelligence tailored to your needs will help you quickly mitigate phishing threats, take down malicious domains, and stay ahead of evolving tactics.
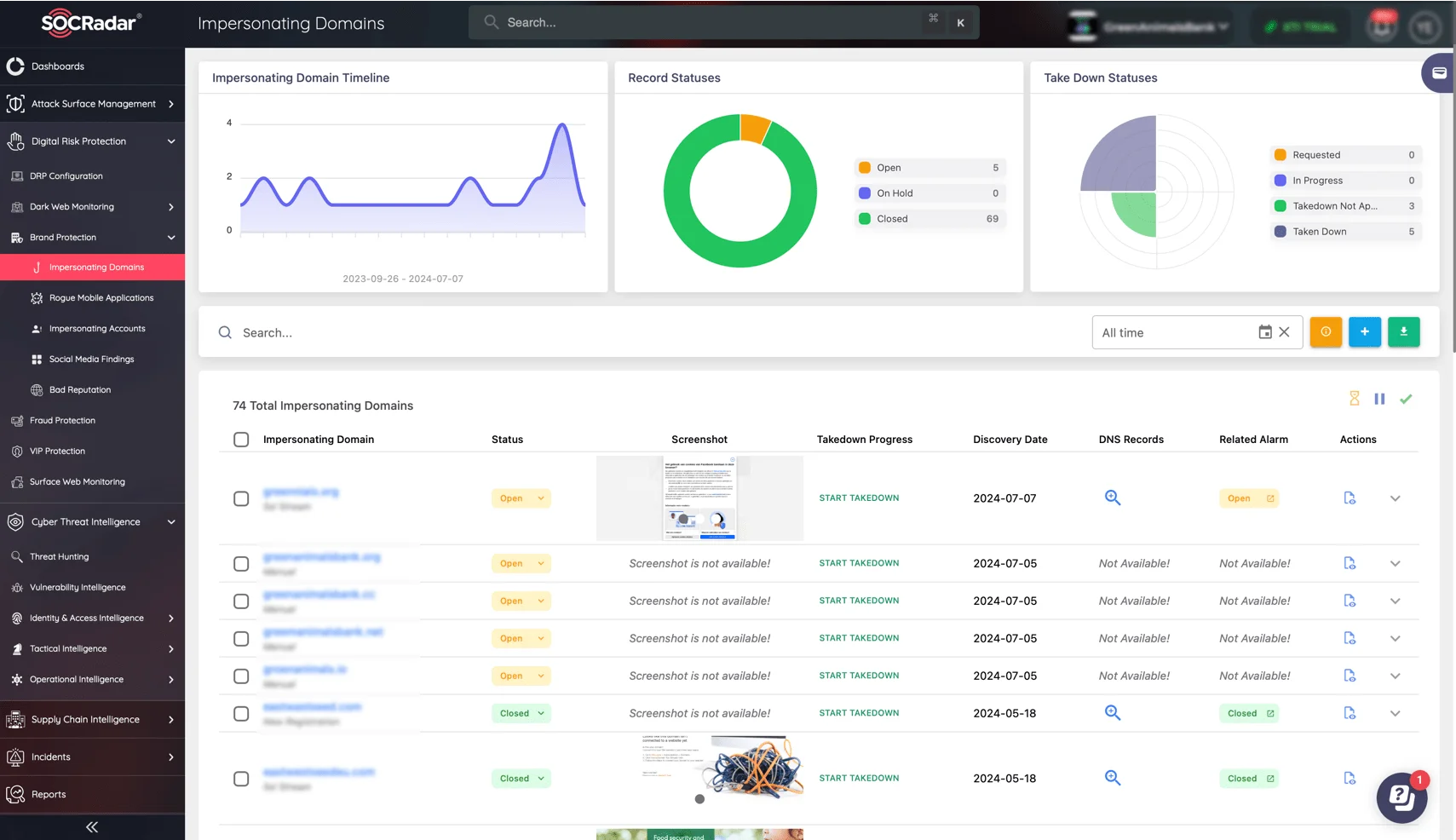
Use SOCRadar’s Brand Protection Impersonating Domains service to monitor incidents as they occur.
SOCRadar enables your team to respond quickly and effectively to spear phishing incidents. Gain a thorough understanding of attack origins and patterns using big data analysis, ensuring that your incident response is both informed and proactive.
Conclusion
Spear phishing continues to pose a significant threat to organizations of all sizes, with attackers constantly refining their tactics to exploit vulnerabilities. Organizations can better protect themselves from targeted attacks by understanding how spear phishing works and implementing proactive defense strategies.
SOCRadar LABS helps you stay ahead of phishing threats. Our free service, Phishing Radar, is intended to detect and mitigate phishing attacks quickly. SOCRadar’s Digital Risk Protection platform scans millions of domain registrations and sends real-time alerts about suspicious activity to keep your organization secure.
SOCRadar LAB’s Phishing Radar
According to research, phishing is the most common infection vector for threat actors, resulting in system breaches and data theft. SOCRadar helps you maintain a proactive security posture by presenting global trends, statistics, and recent attacks relevant to your industry. The free Phishing Radar service from SOCRadar previews your domain’s threat landscape.




































