How to Combat Fraud with Threat Intelligence: Cutting-Edge Pathway
Organizations have increasingly moved significant portions of their operations online to streamline customer service processes. Instead of physically visiting a location to pay for and pick up products, these transactions have become much simpler through online platforms. However, this convenience comes with a substantial security risk; fraud, which many organizations continue to overlook.
According to Juniper Research, losses from e-commerce online payment fraud reached $41 billion in 2022. Furthermore, the total cost of e-commerce fraud to merchants worldwide was estimated to exceed $48 billion in 2023. Breaking down this staggering figure by region, North America accounts for 42% of the fraud, followed by Europe at 26%. Alarmingly for merchants, projected cumulative losses from online payment fraud worldwide between now and 2027 are estimated to exceed $343 billion.
Fraud presents a serious concern for both businesses and individuals. The landscape is continuously evolving, making it crucial for organizations to stay vigilant about the latest trends to protect themselves and their consumers. Threat actors are launching new campaigns, and their tactics are becoming increasingly sophisticated. Only effective and proactive Threat Intelligence solutions can counter and safeguard against these evolving threats. As 2024 unfolds, let’s examine digital fraud trends and their potential impacts and explore solutions from a threat intelligence standpoint.

Fraud percentage by region
What is Fraud?
Fraud is a type of deception that involves intentionally misleading a person or concealing the truth to gain an unfair or unlawful advantage or to cause harm to another person. Digital fraud, a subset of cybercrime, uses the internet to deceive or misuse web-enabled assets, often for financial gain. Common types of digital fraud include phishing, identity theft, malware, ransomware, and cryptocurrency. This can affect both individuals and businesses, leading to financial losses, reputational damage, and security breaches.
Fraud can have severe consequences for the economy and society, as it can undermine trust, damage reputations, cause financial losses, and harm innocent victims. Detecting and preventing fraud can be challenging, as fraudsters often employ sophisticated techniques and technologies to conceal their actions. It is crucial to recognize the signs of fraud and to use advanced technology to detect and prevent suspicious activity, reporting it to authorities or relevant organizations when necessary.
What are the Common Types of Fraud in Enterprise?
Fraud takes many forms, targeting different victims in various ways for diverse reasons. While financial institutions and insurance providers both deal with it, the types they encounter, the impacts, and how security teams manage them can differ significantly. This section focuses on types of fraud predominantly affecting enterprises:
- Business Email Compromise (BEC): A sophisticated attack targeting businesses conducting wire transfer payments. BEC attack involves compromising legitimate email accounts through social engineering to initiate unauthorized payments.
- Credential Stuffing: Credentials obtained from a data breach in one service are used to access another. This includes data stolen from users and organizations and data resold on the dark web or in hacker forums.
- Credit and Debit Card Fraud: Hackers fraudulently acquire credit or debit card information to steal money or make unauthorized purchases. Cybercriminals may use skimmers at ATMs to read victims’ PIN codes and card numbers. The ease with which cybercriminals can purchase personal information on the dark web amplifies the threat of card fraud.
- Cryptocurrency Fraud: As cryptocurrency platforms have gained popularity in recent years, they face growing concerns about fraud. Despite market volatility, its global market capitalization has exceeded $1.25 trillion, attracting investors and threat actors alike.
- Identity Theft: Personal information is stolen to perform unauthorized transactions, often involving altering Personal Identifying Information (PII), adding unauthorized users, or changing passwords. Synthetic identity theft combines real and fake information to create a new identity.
- Insider Fraud: Increasingly common, this scam is perpetrated by individuals within an organization, using their access to sensitive information for personal gain.
- Impersonation Fraud (Phishing): Involves email, online messaging, fake websites, and social engineering to trick victims into sharing personal data, login credentials, and financial details. According to Astra research, phishing was responsible for an average breach cost of $4.91 million in 2023.
- Malware: Destructive programs designed to gain access to infected devices. According to Kaspersky, 5,704,599 instances of malware and viruses were blocked in 2023.
- Ransomware: Ransomware attackers encrypt data and then demand a ransom amount in exchange for the release of files or a security key. Innovations like Artificial Intelligence and Ransomware-as-a-Service (RaaS) platforms have facilitated these attacks. In 2023, over 72% of businesses worldwide were affected by ransomware attacks (Statista).
SIM Swapping Fraud:SIM swapping targets weaknesses in two-factor authentication systems using calls or text messages to mobile devices. This enables the compromise of one-time passwords and account takeovers for financial gain.

Business Fraud Trends (Source: Techreport)
What measures should be taken to Detect and Prevent Fraud?
Experts estimate that companies lose five to six percent of their annual revenue to fraud. Therefore, implementing a comprehensive fraud prevention program is essential. Such a program typically consists of three core components:
- Education: Enhancing awareness about fraud among employees and stakeholders.
- Investigation: Conducting thorough examinations when fraud is suspected.
- Proactive Prevention: Implementing strategies and measures to deter fraud.
A significant focus of any company’s fraud prevention efforts should be on the development and execution of proactive and preventive techniques. This includes establishing internal controls, policies, and procedures specifically tailored to prevent it. While various solutions exist to combat fraud, most are specialized for specific types of fraudulent activities. Given the unprecedented scale of fraud today, organizations and individuals must strive to become more challenging targets for fraudsters. There is no one-size-fits-all solution for fraud detection. However, the following key capabilities can significantly enhance an organization’s ability to detect various forms of fraud:
- Increased Visibility: Improve insights into decision-making processes, particularly in risk assessment. Understanding the logic behind flagged transactions enables fraud teams to respond more effectively.
- Network Intrusion Prevention: Implement real-time monitoring and alerting systems to prevent threat actors from compromising your network.
- Comprehensive Platform Utilization: Employ a platform capable of detecting, mitigating, and proactively preventing fraudulent activities.
- Up-to-date Intelligence: Ensure comprehensive and proven intelligence coverage, including the dark web, hacker forums, social media, and open-source websites, to protect your organization’s Personally Identifiable Information (PII).
- Stronger Application Architecture Requirements: Develop a deeper understanding of the Tactics, Techniques, and Procedures (TTPs) used by threat actors to enhance application architecture, processes, and controls.
- Leveraging Threat Intelligence: Use threat intelligence to monitor personal, sensitive, and commercial information being sold on hacker forums, safeguarding both organizational and individual interests.
What is the Role of CTI in Fraud Prevention? How Can SOCRadar Help Against Fraudulent Activities?
Detecting and responding to the cyber threats currently facing systems and networks accessible to the internet is crucial in protecting an organization against fraudulent activities. However, organizations must also be vigilant against fraudulent use of their data or brand. Threat Intelligence can help by providing insights into the motivations and methods of criminals, especially in relation to personal and sensitive data.
For instance, an organization can identify instances where cybercriminals are impersonating their brand to launch phishing attacks against unsuspecting customers. This involves providing real-time alerts on the latest phishing trends, enabling organizations to detect potential threats proactively. Techniques like phishing and domain spoofing are commonly employed by threat actors to achieve various objectives against an organization. Another example of fraudulent use of data or brands is when criminals distribute compromised data on the dark web. Threat intelligence allows organizations to monitor the dark web in real-time for any compromised data, enabling swift action to be taken.
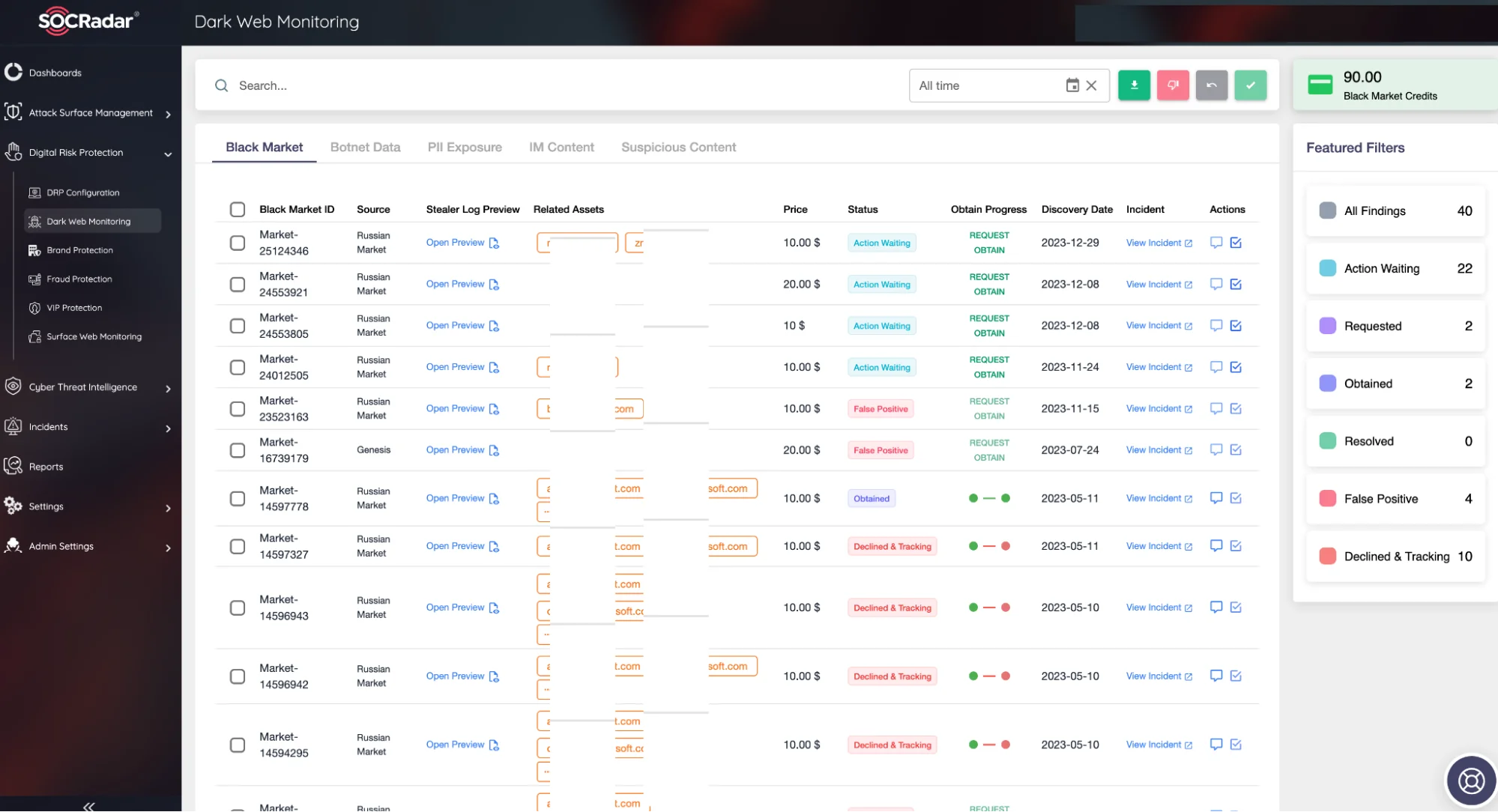
Thanks to the Dark Web Monitoring service within the SOCRadar Digital Risk Protection Module, personal, sensitive, and trade secret information stolen by threat actors in black market environments on the dark web, which are continuously scanned 24/7—especially through info-stealers malware—is identified, and users are informed in a timely manner to prevent their involvement in fraudulent activities. Additionally, devices enslaved in Botnets, many of which are insecure IoT devices, are detected, and instant alarms are generated.
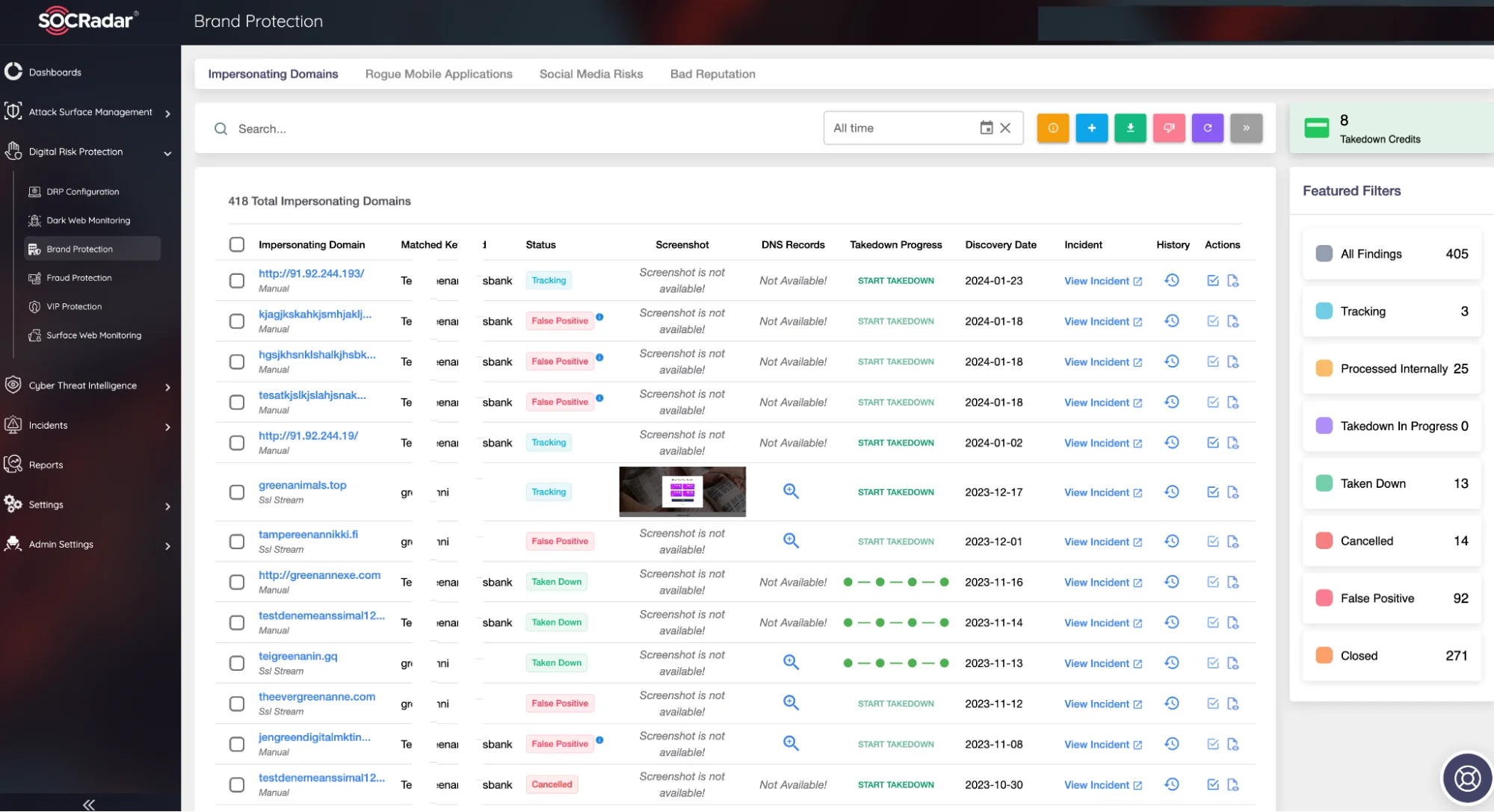
As part of the SOCRadar Digital Risk Protection Module, the Brand Protection collects extensive data points and correlates them with AI models to generate actionable intelligence alerts. This enables instant identification of phishing domains, comprehensive internet scanning, and detection of compromised credentials. It empowers Security Operations and Risk Management teams to quickly and effectively understand how risks, particularly fraud, are evolving through digital transformation and determine the necessary mitigation strategies.
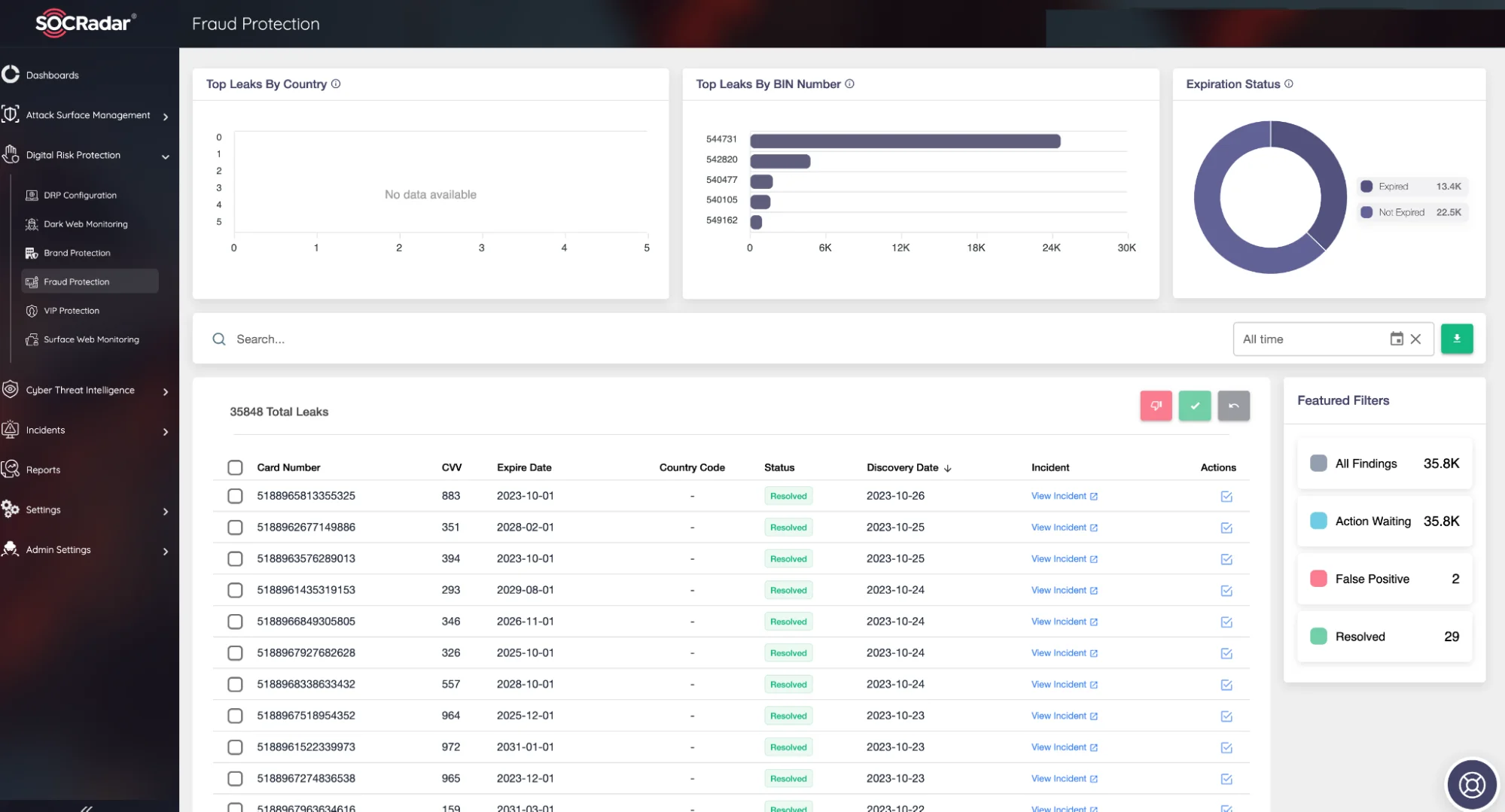
Under the same module, the Fraud Protection assists enterprise organizations in identifying personal and sensitive information compromised by threat actors and in understanding the methods and tools used to commit fraud. This AI-driven fraud protection solution monitors the public attack surface, gathers evidence of fraudulent activities, analyzes content on a large scale, and generates alerts to enable countermeasures.
Conclusion
Organizations continue to digitally transform their operations, moving data from internal networks to the cloud and generating and storing information across an increasing number of services. While this streamlining of operations is changing many industries for the better, it also introduces significant risks.
A comprehensive risk management plan and assessment that keeps pace with evolving security requirements is essential. This should include considering the security of partners, suppliers, and other third parties when assessing an organization’s own risk. Threat intelligence can offer transparency into the environments of these third parties, providing real-time alerts about threats and changes in risk levels.
The SOCRadar External Threat Intelligence platform grants organizations exceptional visibility into their internet-facing attack surface, monitoring critical digital assets to detect and respond to digital fraud. In addition to recognizing fraud-based cyberattacks, the platform’s takedown services expedite actions against critical threats. This includes eliminating fake accounts and rogue infrastructure, thereby helping to prevent future attacks.