
What is Cyber Threat Intelligence? (2023 Edition)
Information that an organization utilizes to understand the risks that have, will, or are presently attacking it is known as cyber threat intelligence. This information is used to predict, prevent, and identify cyber-threats attempting to exploit valuable resources.
To prevent threats, Threat Intelligence enables organizations to make faster, more informed security decisions and shift their behavior from reactive to proactive.
Why is Threat Intelligence Important?
Threat intelligence systems collect data from various sources on emerging or existing threat actors and threats. This information is then evaluated and filtered to provide threat intelligence feeds, and management reports automated security control solutions use. The main goal of this type of security is to keep businesses informed about the dangers of advanced persistent threats, zero-day threats, and exploits and how to protect themselves.
Threat intelligence enables companies to be proactive rather than reactive in the face of potential cyber-attacks by providing predictive skills. It is hard to battle cyber-attacks without first understanding security weaknesses, threat indicators, and how threats are carried out effectively.
Security experts that use cyber intelligence can prevent and contain intrusions faster, thereby saving money in the event of a cyber-attack. Threat intelligence can improve security across the board, including network and cloud security.
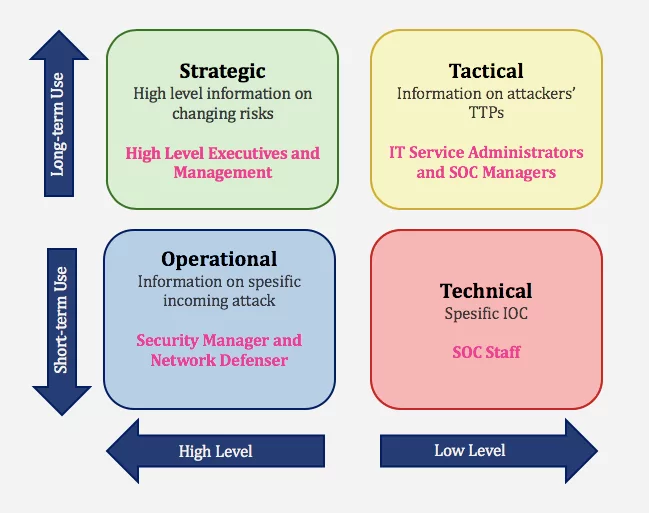
Who Benefits from Threat Intelligence?
The field of elite analysts is commonly assumed to be cyber threat intelligence. In actuality, it offers value to security functions across the board for businesses of all sizes.
Security operations teams are usually unable to process the alerts they get — threat intelligence interacts with your existing security solutions, automatically prioritizing and filtering alerts and other risks. Vulnerability management teams may prioritize the most critical vulnerabilities more precisely with access to threat intelligence’s external insights and context.
Threat intelligence provides critical insights on threat actors, their tactics, techniques, and procedures, as well as other high-level security processes, such as fraud prevention, risk analysis, and other high-level security processes, including critical insights on threat actors, their tactics, techniques, and procedures, and more from data sources across the web.
Threat Intelligence Use Cases
Vulnerability Prioritization
One of the most effective uses of threat intelligence is to collect data and conduct research that will aid your organization in developing a simple metric for assessing risks. Given the time and resources available, this statistic should measure the overlap between the problems you can repair and the solutions that make the most difference.
The traditional method of prioritizing vulnerabilities leads people to believe that “patch everything, all the time, everywhere” is the most excellent security strategy. In theory, achieving this goal would result in an utterly impenetrable system, but it sets an unrealistically high bar. As a result, companies that take this strategy will unavoidably make concessions and prioritize the “greatest” issues.
However, contrary to popular belief, the “greatest” problems (in terms of actual damage) aren’t zero-day threats or clever new exploits, but rather the same old vulnerabilities that continue to be exploited, precisely because so many organizations prioritize new threats over improving their fundamentals.
Open, Deep, and Dark Web Monitoring
Anyone with access to the internet can use open sources. This refers to all the data indexed by search engines, often known as the surface web.
The dark web refers to areas of the internet that are protected by secure logins or paywalls, preventing search engine crawlers from accessing them. Scientific, academic, or government reports, personal information such as financial records or medical histories, and private commercial databases make up most of this data.
The dark web consists of websites that can only be accessed with browsers that provide encryption and anonymity, such as Tor. Although this is not always the case, many dark web websites act as black marketplaces for illegal goods and services.
Vulnerabilities and related exploits are frequently discussed and traded in deep and dark web spaces by both parties interested in keeping them safe and threat actors. As a result, gathering data from these sources is critical to maintaining a more thorough and up-to-date picture of the dangers that exist.
Brand Monitoring
The threat intelligence system will monitor open sources, mainly social media channels. Detecting risks in this environment is a skill in and of itself, as it necessitates a thorough understanding of your company’s brand and the various ways a threat actor can try to exploit it.
These dangers were becoming increasingly visible in public places and scrutinized more closely. They can be more subtle, relying on social engineering tactics rather than software exploits, and require a certain level of knowledge to detect.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































