How to Leverage Threat Intelligence in Incident Response
In the ever-evolving landscape of cybersecurity threats, incident response has become a crucial component of any organization’s defense strategy. Rapid and effective incident response can significantly minimize the impact of security breaches and help organizations recover swiftly. One powerful tool in this arsenal is threat intelligence, which provides valuable insights into emerging threats, attacker tactics, and potential vulnerabilities.
Understanding Threat Intelligence
Cyber Threat Intelligence (CTI) refers to the collection, analysis, and dissemination of information about potential and ongoing cyber threats. It involves monitoring a wide range of sources, including public forums, dark web marketplaces, hacker communities, and data breach repositories. The goal is to identify Indicators of Compromise (IoCs), Tactics, Techniques, and Procedures (TTPs) employed by threat actors, and any other relevant information that could aid in understanding the threat landscape. SOCRadar XTI monitors the IoCs of the threat actors up-to-date. It presents them to you on the SOCRadar Threat Feed/IoC Dashboard after passing over 50 million whitelists and validations (IP, Hash, MD5, etc.).
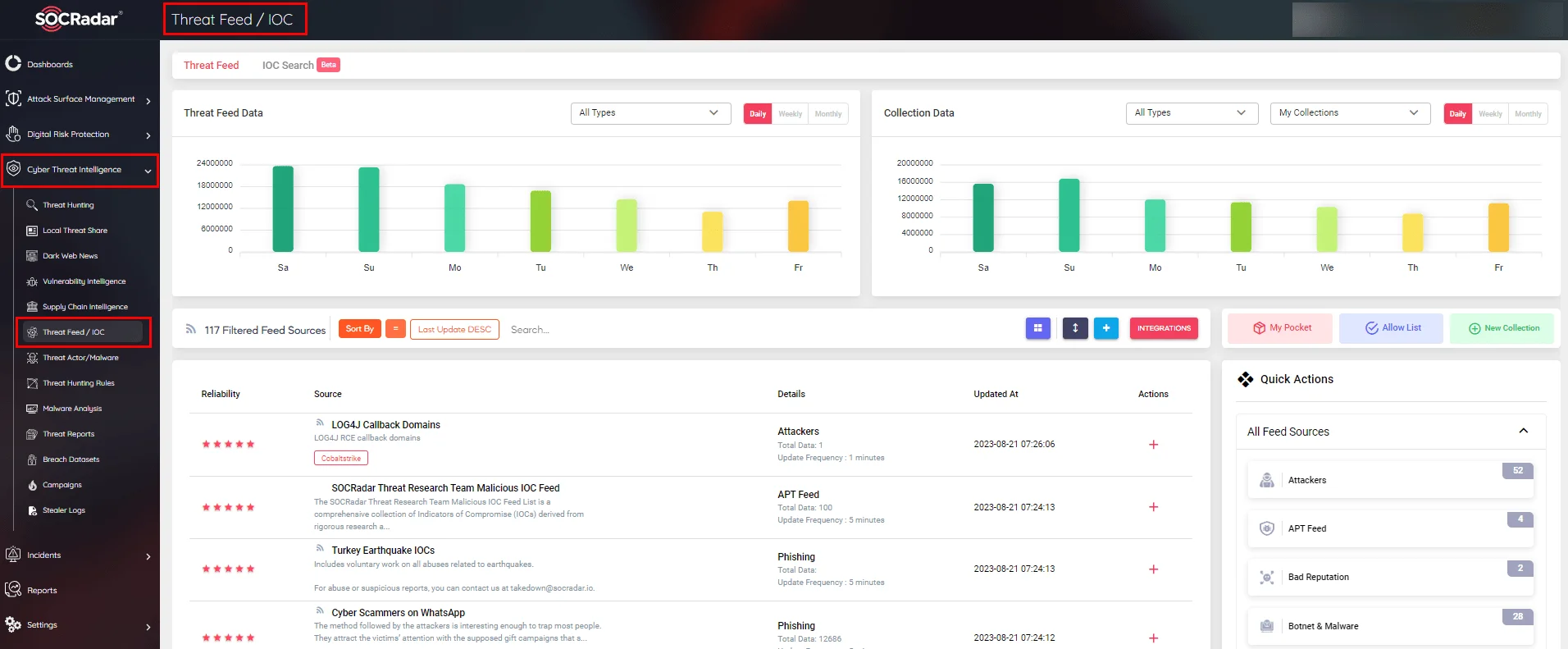
Figure 1: SOCRadar Threat Feed/IoC Page.
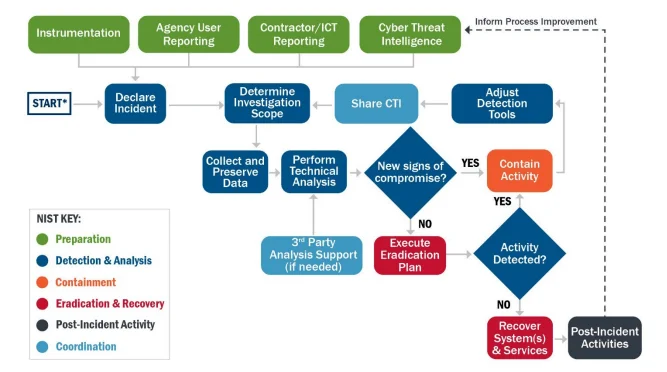
Figure 2. Incident Response Process (CISA)
Benefits of Threat Intelligence in Incident Response
Proactive Threat Detection: Threat intelligence allows organizations to identify potential threats before they manifest into full-blown incidents. By analyzing the latest threat data, security teams can recognize patterns and anomalies that might indicate an ongoing attack.
The SolarWinds incident highlighted the critical need for proactive threat detection. By swiftly identifying unusual activity and leveraging threat intelligence, organizations can respond promptly, mitigating potential damage. During the incident, organizations employing proactive threat detection noticed unusual data traffic patterns emanating from SolarWinds software. Recognizing the anomaly, they swiftly investigated and discovered a compromised software update. By leveraging threat intelligence, they identified the attack’s origin and contained the breach before significant damage occurred. This incident underscores the importance of robust monitoring, continuous evaluation of network behavior, and active participation in threat intelligence communities.
Information-sharing forums and threat intelligence platforms played a crucial role. Early warnings and Indicators of Compromise (IoCs) from other organizations helped in identifying the scale and nature of the attack. SOCRadar XTI monitors information-sharing forums and threat actors. When anything about customers is shared, it detects it and sends it to customers.
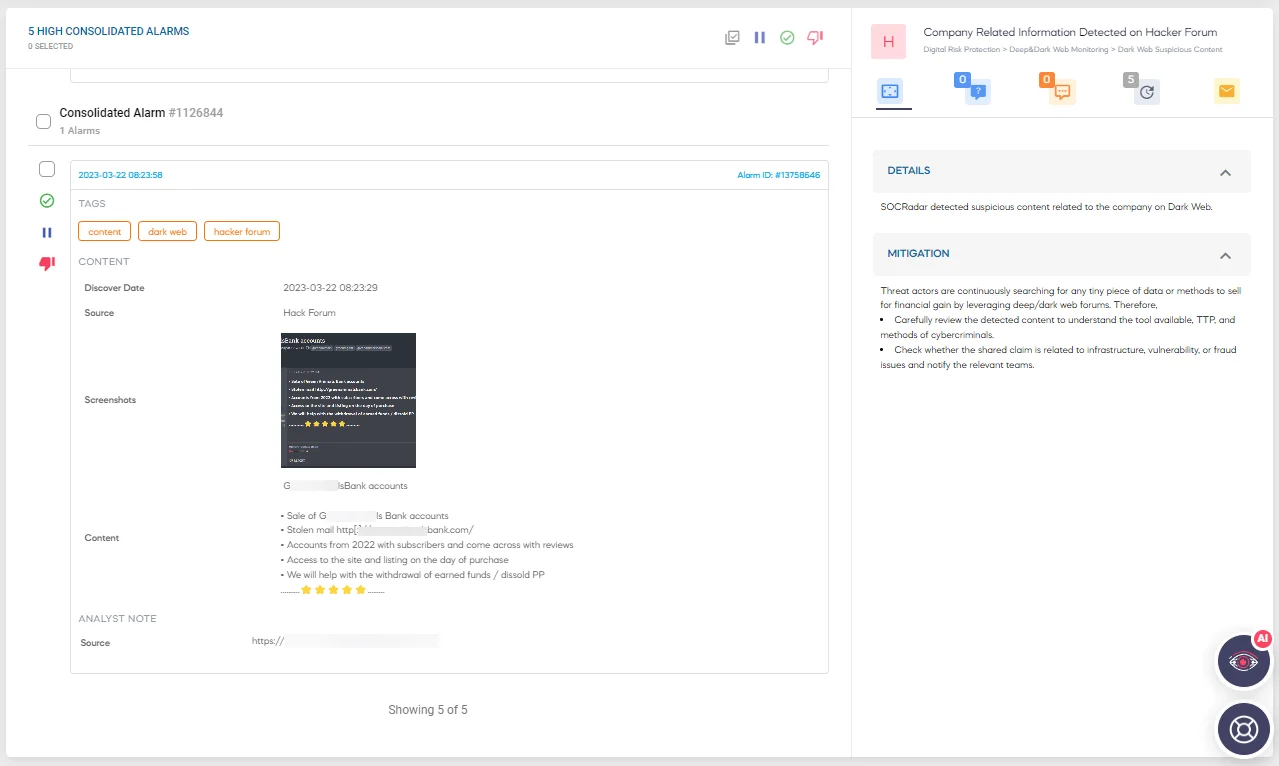
Figure 3: A detected post on dark web forums
Contextual Understanding: Threat intelligence provides context to security incidents. Knowing the motivations, capabilities, and objectives of threat actors allows organizations to tailor their response strategies to effectively counter specific threats.
APT29, also known as Cozy Bear, who is involved in the SolarWinds incident, is a threat actor group with suspected ties to the Russian government. Their motivations are believed to be primarily espionage and gathering intelligence. Understanding APT29‘s affiliation and objectives allows targeted organizations to tailor their defenses to protect against advanced, state-sponsored threats. APT29 uses many attack vectors such as critical vulnerabilities, including the Citrix ADC Network Gateway (CVE-2019-19781) vulnerability, which is one of the top 5 critical vulnerabilities behind ransomware attacks, stolen accounts, phishing, etc. to gain access to victims’ systems. Taking proactive measures such as regularly scanning digital assets, promptly identifying and patching vulnerabilities, monitoring for compromised accounts on the dark web forums and black markets, and implementing advanced threat detection methods can effectively prevent these kinds of potential cyber threats before they materialize.
Contextual understanding plays a pivotal role in incident response, especially concerning threat actors. It helps identify, attribute, and comprehend the motivations and tactics of those responsible for the incident, enabling organizations to mount an effective response and bolster their defenses against future attacks. SOCRadar XTI monitors threat actors and provides their TTPs, IoCs, etc. to its customers.
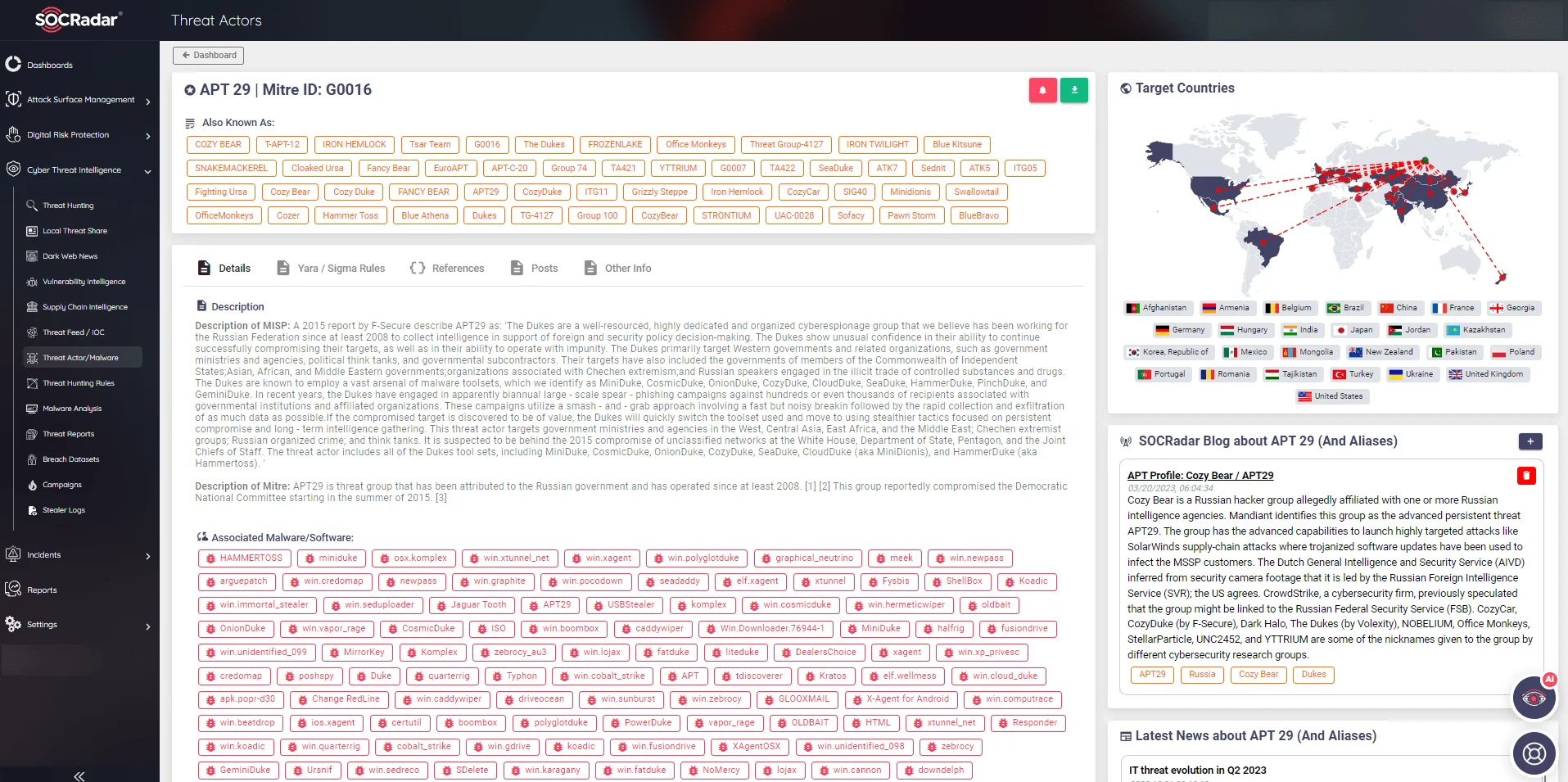
Figure 4: SOCRadar Threat Actor/Malware for APT 29
Improved Decision-Making: With threat intelligence, incident responders can make more informed decisions during the heat of the moment. This could involve deciding on containment strategies, communication plans, or recovery procedures based on up-to-date threat information.
Faster Incident Response: When a security incident occurs, time is of the essence. Threat intelligence expedites the incident response process by offering insights into potential attack vectors and strategies, enabling quicker identification and containment of threats.
In the WannaCry ransomware attack (2017), threat intelligence provided early warnings and contextual insights. Automated alerting allowed organizations to swiftly apply patches and network protections. Understanding the threat actor’s likely motivation expedited the response. Global threat intelligence sharing further accelerated the containment of the attack, minimizing its impact. Threat intelligence was instrumental in mitigating WannaCry swiftly.
Tailored Mitigation Strategies: Threat intelligence enables the development of targeted mitigation strategies. Rather than deploying generic measures, organizations can focus resources on the vulnerabilities and attack vectors most relevant to their specific environment.
Monitoring attack vectors before threat actors can prevent future attacks. SOCRadar XTI scans its customers’ digital assets on the internet and notifies them of security vulnerabilities.
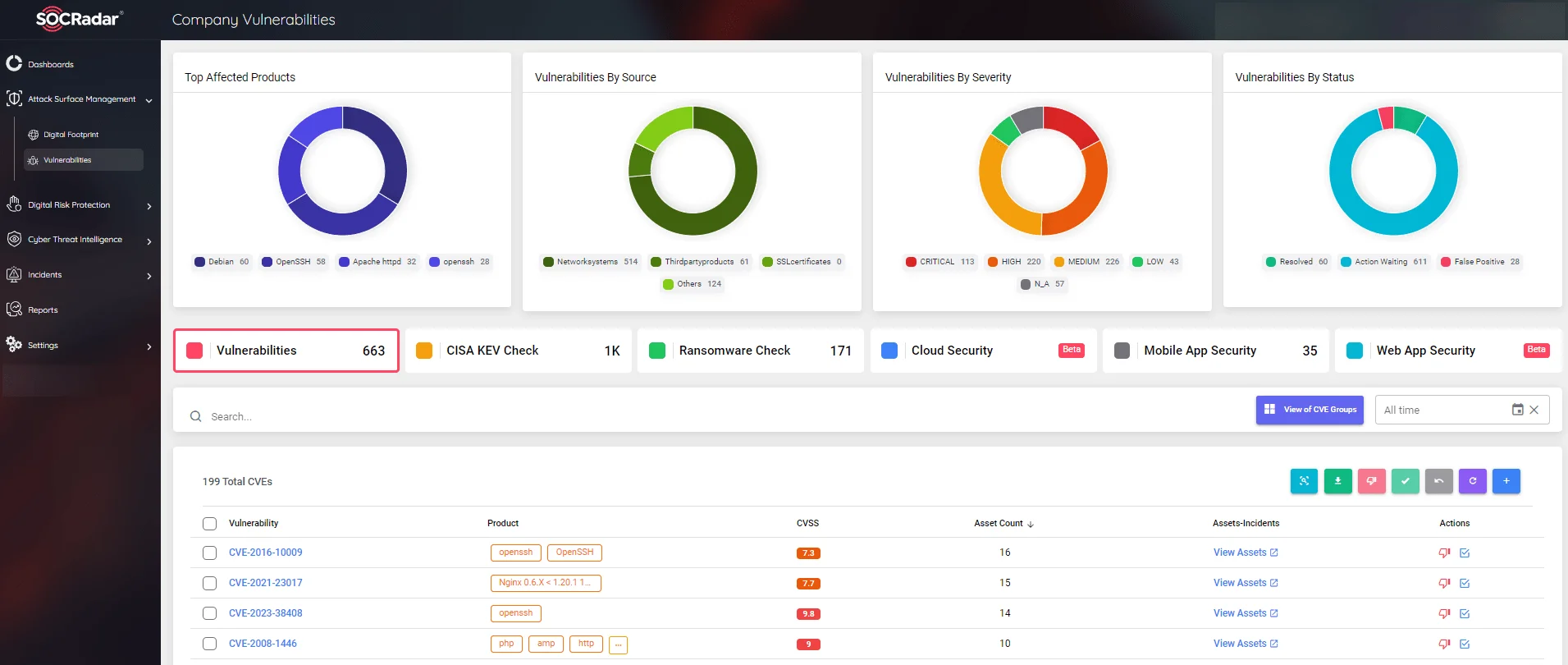
Figure 5: SOCRadar Vulnerability Intelligence module
Incorporating Threat Intelligence into Incident Response
Data Collection and Analysis: Gather threat intelligence data from reliable sources. This includes commercial threat intelligence providers, open-source feeds, and internal security data. Analyze this data to identify trends, patterns, and potential IoCs or TTPs.
Integration with Security Tools: Integrate threat intelligence feeds into your security infrastructure. This could involve connecting threat feeds with your Intrusion Detection Systems (IDS), Intrusion Prevention System (IPS), Next-Generation Firewall (NGFW), Security Information and Event Management (SIEM) platforms, and firewall rules.
Figure 6: SOCRadar Integrations
Automated Alerts: Set up automated alerts based on threat intelligence data. This ensures that your security team is promptly notified when a potential threat emerges, allowing for quicker response times.
In 2020, amidst the COVID-19 pandemic, cybercriminals took advantage of the crisis. They launched extensive phishing campaigns, posing as health organizations, government agencies, and trusted entities. Their aim was to spread COVID-19-related misinformation, distribute malware, and steal sensitive information.
To counter this threat, organizations leveraged threat intelligence feeds with Indicators of Compromise (IoCs) tied to COVID-19 attacks. These IoCs included malicious domains, email addresses, and file hashes linked to these campaigns.
By integrating threat intelligence with automated alerting systems, organizations swiftly detect potential threats. When any COVID-19-related IoCs were spotted in emails or network traffic, automated alerts were triggered instantly.
Incident Playbooks: Develop incident response playbooks that are informed by threat intelligence. These playbooks should outline step-by-step actions to take based on specific threat scenarios, ensuring consistency in response efforts.
Regular Updates and Training: The threat landscape is constantly changing. Ensure that your incident response team receives regular updates on emerging threats and participates in training to understand how to interpret and use threat intelligence effectively.
Conclusion
In a world where cyber threats continue to evolve in sophistication and scale, organizations must adopt proactive strategies to safeguard their digital assets. Threat intelligence provides a powerful means of enhancing incident response capabilities by offering timely and contextual insights into potential threats.SOCRadar XTI provides a rich context added on top of automation-powered information gathering. We use different OSINT tools to generate threat intelligence feeds such as phishing domains, malicious IPs, hacked websites, hashes, and DDoS attackers. By integrating threat intelligence into incident response workflows, organizations can detect, respond to, and recover from security incidents more effectively, ultimately minimizing the impact of cyberattacks.



































