OSINT Framework Tools as Our Friends
What is OSINT?
Open-source intelligence, abbreviated as OSINT, is the gathering of information from publicly available sources that can be analyzed and turned into actionable intelligence. OSINT is commonly used in penetration testing and is a part of the reconnaissance step of real cyber attacks.
OSINT is not only about Cybersecurity
In addition to penetration testing and being a part of actual cyber-attacks, open-source intelligence has other use cases in different areas such as law enforcement or national security. Government officials use OSINT to detect threats against national security. Moreover, OSINT is commonly used to gain the upper hand against rival enterprises in a competitive business environment.
Open-source intelligence also has some trivial use cases every person can utilize. Below, you can see examples of trivial use cases related to geolocation intelligence also called as GEOINT.
- Flight Trackers: With the help of flight tracker websites such as flightradar24.com, a person can track and collect information about ongoing flights and turn the information into actionable intelligence.
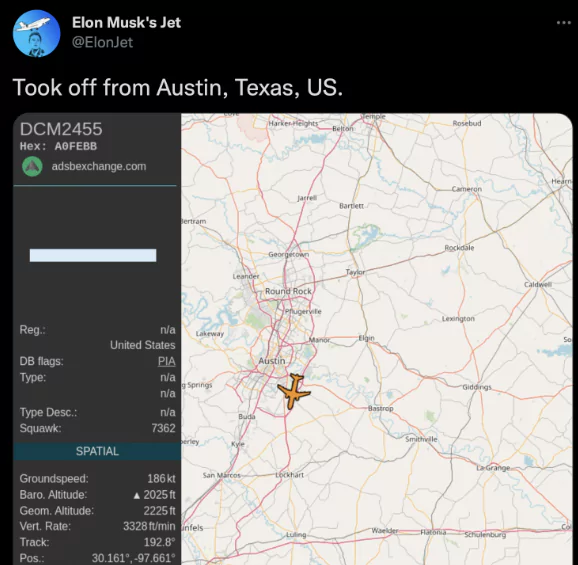
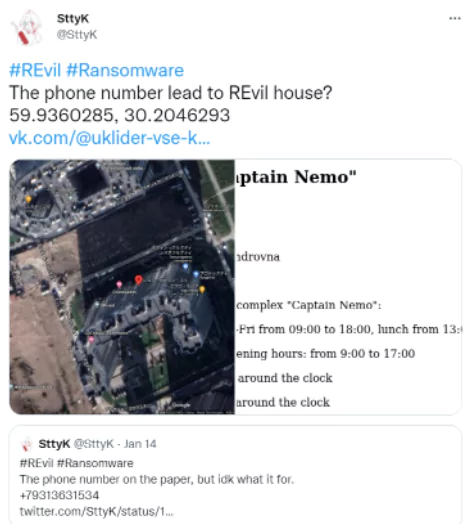
- Satellite Imagery: Satellite Imagery is another OSINT tool enabling users to find satellite images of certain coordinates. A person can utilize satellite imagery tools such as Google Earth to use the intelligence they already have to find the geological location of their target. On 14th of January, 2022, a Twitter user have used OSINT tools along with satellite imagery to find where the members of thenewly-arrested REvil ransom ware gang had lived.
5 useful OSINT tools for security professionals
Having a wide perspective is important for efficient OSINT investigations. Even a tiny piece of information can help you solve the puzzle. For security community, OSINT has a critical role in terms of incident response and threat hunting exercises. There are hundreds of open source intelligence tools security professionals can utilize. Below, we have picked the most common 5 OSINT tools that can be handy at any time.
1. Shodan: A Search Engine for Internet-connected Devices
Shodan is a search engine OSINT tool enabling users to perform targeted searches to collect information about servers connected to the internet, including IoT devices. With Shodan, a user can perform IP Lookups and crawl the internet to produce actionable intelligence.
For example, a threat actor can perform Shodan searches to find unpatched vulnerable servers, which can be exploited by certain vulnerabilities. Below, you can see an example Shodan query finding unpatched servers running version 2.4.49 of Apache, which is vulnerable to CVE-2021-41773, path traversal and remote code execution attacks.

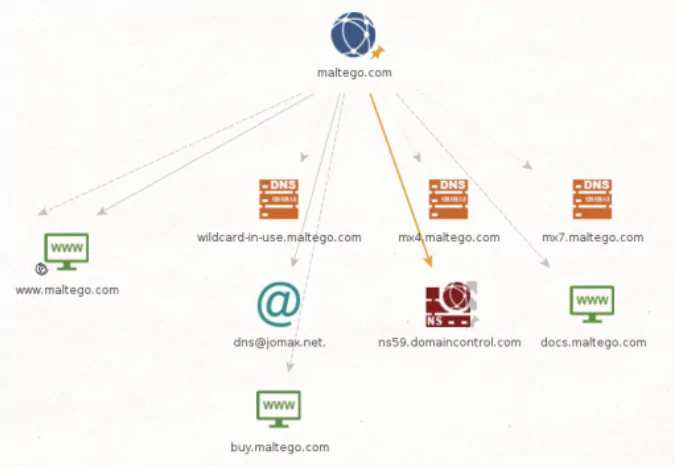
2. Maltego: A Tool for Professional Investigators
Maltego is a graphical link analysis tool commonly used in OSINT and forensics. With Maltego, a user can easily identify links between elements of a structure. By this visual approach, the patterns and relations between elements can be seen clearly. The user can develop a strategy for approaching the target structure through this information, turning data into actionable intelligence.
Below, you can see an example Maltego chart.
3. Google Dorking: Go Dork Yourself before Hackers Do!
Dorking is a technique in which the user performs special search queries to proactively gather actionable intelligence. Through Google’s search engine and customized flags, dorking can uncover sensitive data about servers and systems. For example, one can access public web cameras with the search query “inurl:”ViewerFrame?Mode=””.
4. GitHub Dorking: Find Leaked Secrets in Repositories
Like Google dorking, the GitHub search engine can be utilized with special search queries to find vulnerabilities, compromised private tokens and keys, and additional information in source codes uploaded publicly to GitHub. For example, the search query “extension:pem private” yields repositories including a private key (.pem) file, which sometimes includes compromised private keys.
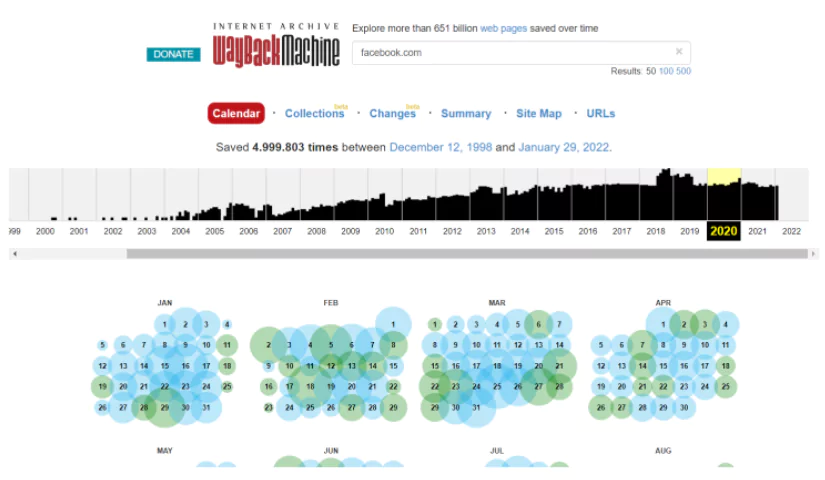
5. Wayback Machine: A Time Machine for the Web
Wayback Machine is a non-profit website enabling its users to access former versions of websites. More than a million websites are added to Wayback Machine daily. One can gather actionable intelligence such as names, phone numbers, addresses from Wayback Machine through accessing old versions of a website. Below, you can see an example Wayback Machine search revealing former versions of facebook.com going as early as 2000.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.