
Internet-Exposed Devices within Federal Networks
As technology evolves and becomes increasingly integral to all aspects of society, the need for robust cybersecurity measures becomes more pressing. One primary aspect of concern in this digital age is the exposure of network management interfaces to the public internet. Recently, Censys, an attack surface management company, has revealed some startling findings regarding the status of devices within federal networks
Understanding The Binding Operational Directive 23-02
Censys recently released a blog post discussing the implications of CISA’s (Cybersecurity and Infrastructure Security Agency) Binding Operational Directive 23-02 (BOD 23-02). The BOD 23-02 acknowledges that network devices such as routers, switches, firewalls, and load balancers, among others, have become a target for threat actors as they can often be exploited due to inadequate security, misconfigurations, and outdated software. The risk is further increased if the management interfaces of these devices are directly connected to and accessible from the public-facing internet. The directive mandates federal agencies to reduce the attack surface created by insecure or misconfigured management interfaces across these devices.
What did Censys Discover?
The team of researchers at Censys carried out an extensive study on the attack surfaces across over 50 organizations and sub-organizations that form the Federal Civilian Executive Branch (FCEB). The exploration led them to identify more than 13,000 unique hosts distributed across over 100 autonomous systems related to these bodies. Delving into the services operating on a portion of the 1,300+ FCEB hosts that can be accessed via an IPv4 address, they uncovered hundreds of devices that are publicly exposed and correspond with the directive’s guidelines. The main culprits being networked devices, which included routers, firewalls, VPNs, access points, and various remote server management technologies. The public exposure of these devices and their remote management interfaces greatly amplifies the potential for cyber threats.
During their research, nearly 250 instances of web interfaces for hosts exposing network appliances were also identified. Many were running remote protocols such as SSH and Telnet. They also found multiple out-of-band remote server management devices, which, according to CISA’s directive, should never be directly accessible via the public internet.
Moreover, there were uncovered multiple instances of exposed managed file transfer tools. Given the sensitive nature of the data these tools handle, they are often prime targets for data theft attacks. Also found were over 10 hosts running HTTP services that exposed directory listings of file systems, a common source of sensitive data leakage.
On top of this, the research highlighted the use of end-of-life software on over 150 instances, which included Microsoft IIS, OpenSSL, and Exim. The use of outdated software, no longer receiving security updates, creates a welcoming environment for new vulnerabilities and exploits.
What needs to be done?
CISA’s BOD 23-02 has set a necessary step towards addressing these vulnerabilities. Upon identification, FCEB agencies are required to secure these devices following Zero Trust Architecture concepts or remove them from the public internet within 14 days. Although this directive is specific to FCEB organizations, the findings and recommendations presented by Censys are applicable to all organizations. Identifying and hardening these interfaces within networks is an essential step in enhancing cybersecurity defenses.
The findings presented by Censys underline the pressing need for robust and comprehensive cybersecurity measures for all organizations. By shedding light on these vulnerabilities, they not only enable the improvement of cybersecurity measures within federal networks but also offer valuable insights applicable to broader cybersecurity landscapes. In a world that is increasingly dependent on digital infrastructure, there has never been a more crucial time for organizations to understand and address their vulnerabilities to ensure a secure digital environment.
How SOCRadar’s EASM Solution Aligns with BOD 23-02
SOCRadar’s EASM solution, AttackMapper, provides a comprehensive and continuous view of an organization’s external attack surface. It automatically identifies and monitors all internet-facing assets, including those classified under BOD 23-02, and alerts security teams about potential vulnerabilities, critical open ports, expired SSL/TLS certificates, and missing security configurations.
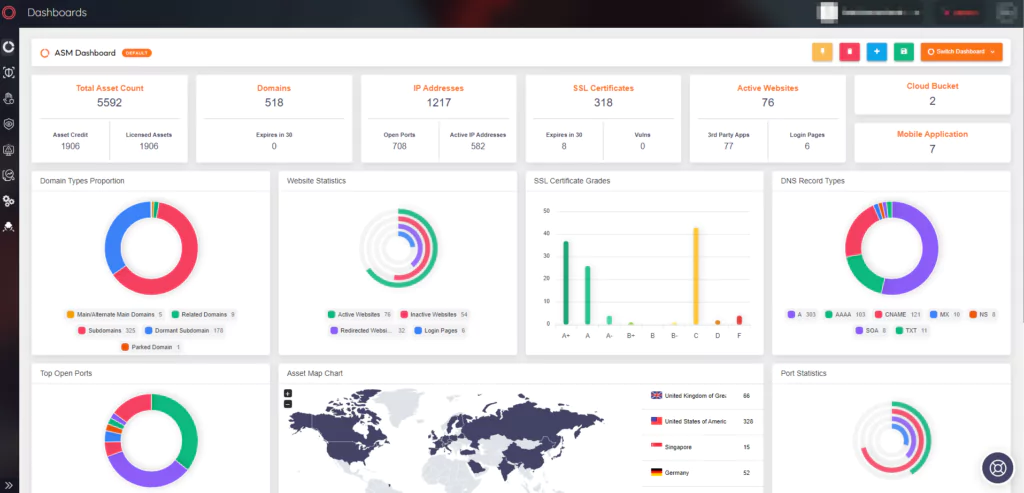
Automated Discovery & Monitoring: SOCRadar’s EASM can identify and classify devices such as routers, firewalls, VPN concentrators, and others outlined in the BOD 23-02. It leverages advanced internet-wide monitoring algorithms to discover these assets and their associated interfaces.
Mitigating Risks: The EASM solution helps to reduce the attack surface by identifying insecure or misconfigured management interfaces. It helps to detect and manage the risks associated with device management interfaces exposed to the public internet, thereby aligning with the key requirements of BOD 23-02.
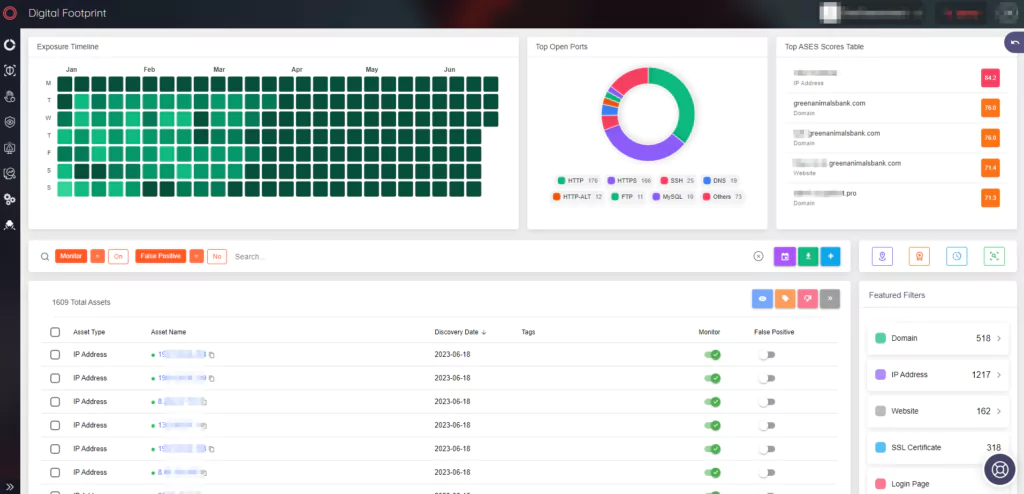
Continuous Vulnerability Detection: SOCRadar’s EASM continuously scans for vulnerabilities in network devices and their management interfaces. By notifying agencies of any exposed critical ports or other potential vulnerabilities, it allows them to prioritize and remediate risks, strengthening their defense against cyber threats.
Zero Trust Architecture Support: The BOD 23-02 encourages agencies to employ a Zero Trust Architecture for improved security. SOCRadar’s EASM solution supports this model by providing capabilities that enforce access control to the management interfaces through continuous monitoring and robust threat intelligence.
In essence, SOCRadar’s EASM solution provides a proactive approach to discovering, monitoring, and mitigating risks related to internet-exposed management interfaces. It aligns well with the BOD 23-02’s mandates, allowing agencies to fortify their cybersecurity posture while adhering to the latest directives.



































