Joint CISA and FBI Advisory: APT Activity Targeting Outlook Online
In a recent joint advisory, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) shed light on enhanced monitoring techniques to detect Advanced Persistent Threat (APT) activity targeting Outlook Online. We will explore the key details and recommendations provided in the advisory, along with Microsoft’s efforts to mitigate the Storm-0558 attack, a China-based threat actor targeting customer email accounts.
CISA and FBI Advisory Highlights
The CISA and FBI advisory, released on July 12, 2023, addresses an incident that occurred in June 2023 when a Federal Civilian Executive Branch (FCEB) agency detected suspicious events in Microsoft 365 (M365) audit logs. After reporting the incident to Microsoft, it was confirmed as malicious activity. The advisory aims to enhance organizational cybersecurity postures by implementing logging recommendations and ensuring audit logging is enabled. By following the advisory’s guidance, organizations can detect and respond to similar APT activities more effectively.
Microsoft’s Response to the Storm-0558 Outlook Attack
In a blog post dated July 11, 2023, Microsoft disclosed the successful mitigation of an attack by a China-based threat actor known as Storm-0558. This actor primarily targets government agencies in Western Europe, focusing on espionage, data theft, and credential access.
Microsoft initiated an investigation in response to anomalous mail activity and identified that Storm-0558 gained unauthorized access to customer email accounts starting from May 15, 2023.
The attack exploited forged authentication tokens using an acquired Microsoft account (MSA) consumer signing key. Microsoft promptly blocked the usage of forged tokens, replaced the compromised key, and collaborated with affected organizations to address the issue.
Mitigation Measures and Recommendations
To enhance cybersecurity defenses and detect similar APT activities, organizations are strongly advised to follow the recommendations provided in the CISA and FBI advisory. These measures include enabling audit logging, ensuring logs are searchable, implementing Microsoft 365 Unified Audit Logging (UAL), understanding the organization’s cloud baseline, and applying baseline security configurations for relevant Microsoft products. Separating administrator accounts from user accounts and collecting and storing access and security logs are additional measures recommended to harden cloud environments.
Reporting Suspicious Activity
Organizations are encouraged to report any suspicious activity to CISA’s 24/7 Operations Center or their local FBI field office. Timely reporting enables authorities to investigate and respond effectively, contributing to the collective effort in mitigating cyber threats.
The collaborative efforts of CISA, the FBI, Microsoft, and Extended Threat Intelligence industry leaders like SOCRadar are instrumental in safeguarding organizations against APT activities.
By leveraging the expertise and tools provided by these entities, organizations can enhance their monitoring capabilities, implement effective logging practices, and follow recommended mitigation steps to strengthen their cybersecurity defenses. Additionally, utilizing solutions like SOCRadar’s monitoring capabilities can provide valuable insights and proactive threat intelligence to stay ahead of emerging threats. Taking a proactive and vigilant approach is essential in today’s rapidly evolving cybersecurity landscape to ensure the protection of critical assets and data.
Enhance Security with SOCRadar: Insights into Threat Actors and APT Groups
Gain valuable insights into threat actors and advanced persistent threat (APT) groups with SOCRadar’s comprehensive monitoring. By utilizing automated data collection, classification, and AI-driven analysis across the surface, deep, and dark web, SOCRadar keeps you informed and alerted about their activities.
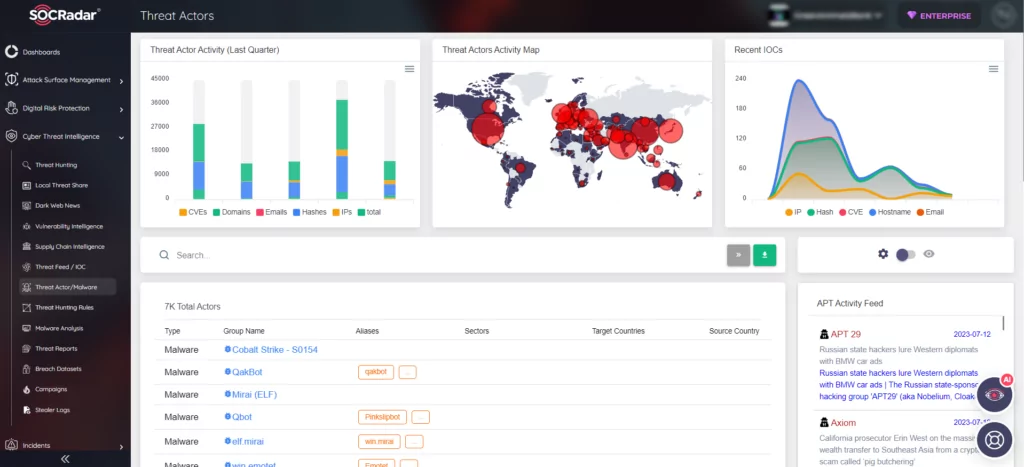
Stay up to date with the latest information on threat actors through the continuously updated Threat Actor panel. This enables you to define use cases that are more effective for detecting and preventing malicious activities, while also allowing for in-depth examination and analysis of threat actors.