Cloud Security Module: Minimize Risk of Misconfigured Buckets
Not long ago, there were discussions about whether organizations should migrate to the cloud. The future has come, and almost all digital assets -services, databases, IT resources, and apps- are now stored in the cloud. Of course, this migration had an inevitable result, such as widening the attack surface. Added to this was that organizations did not meet all the requirements in the process of moving to the cloud, and the misconfigured buckets issue became a significant threat.
Misconfigured or left public cloud buckets to remain a critical information security issue. So, is there anything organizations can do about it? Let’s take a closer look at the problem and the solution.
Types of Cloud Misconfigurations
It is quite challenging to detect and fix errors in the cloud environment. As such, cloud misconfigurations stand out as an essential issue. According to Gartner’s 2019 survey results, misconfigured clouds are the source of 80% of data breaches. Estimates are that this rate will exceed 90% by 2025.
Human errors are the leading cause of misconfigured clouds. Therefore, it is helpful to take a look at the common mistakes.
1. Lack of Identity Access Management
Identity Access Management (IAM) failure is one of the most common cloud misconfigurations. Access management policies that grant broad permissions can overlook issues that could lead to breaches. To avoid this, identities must be centralized, and multi-factor authentication must be implemented with strict rules. It is also vital that identity roles are correctly determined and checked regularly.
2. Using Default Credentials
One of the most common ways development teams take quick action and simplify processes with their colleagues is to create default credentials. They use these credentials to log in to databases and some services. These are generally known to many people inside and outside the team. Although these credentials are only used during development, they can sometimes be left as they are. Developers should not use this type of credentials and eliminate the potential for risk in the first place.
3. Not Monitoring Bucket Status
The status of data stored in the cloud should be regularly monitored and logged. Even if organizations only have employees in charge of controlling cloud environments, it is difficult to maintain security without automated alerts.
No Cloud Storage Provider is Secure

Critical organization assets, such as confidential and sensitive data, databases, and source codes, can be found in cloud buckets. Threat actors can seize this data, which they can use in future attacks or sell them on hacker forums to make a profit.
In July, there was an incident of data leakage on the website of Proud Makatizen, administered by the City of Makati in the Philippines. Over 600 thousand files of the platform opened for Covid-19 assistance services were exposed due to a misconfigured Amazon Web Services S3 bucket.
Another popular cloud storage provider, Google Cloud buckets, a research conducted in 2020 also revealed striking data. 6% of all Google Cloud buckets were misconfigured and vulnerable to attacks. Considering how widely it is used around the world, the volume of the threat becomes clearer.
BlueBleed Leaks
Another recent example is the BlueBleed, which SOCRadar discovered and regarded as the most significant B2B leak in recent times. The Incident caused the leakage of sensitive data of over 65,000 entities from 111 countries. It made publicly exposed Proof-of-Execution (PoE) and Statement of Work (SoW) documents, user information, product orders/offers, project details PII (Personally Identifiable Information) data due to a single misconfigured Azure Blob Storage.
How SOCRadar Cloud Security Module Protect Organizations?
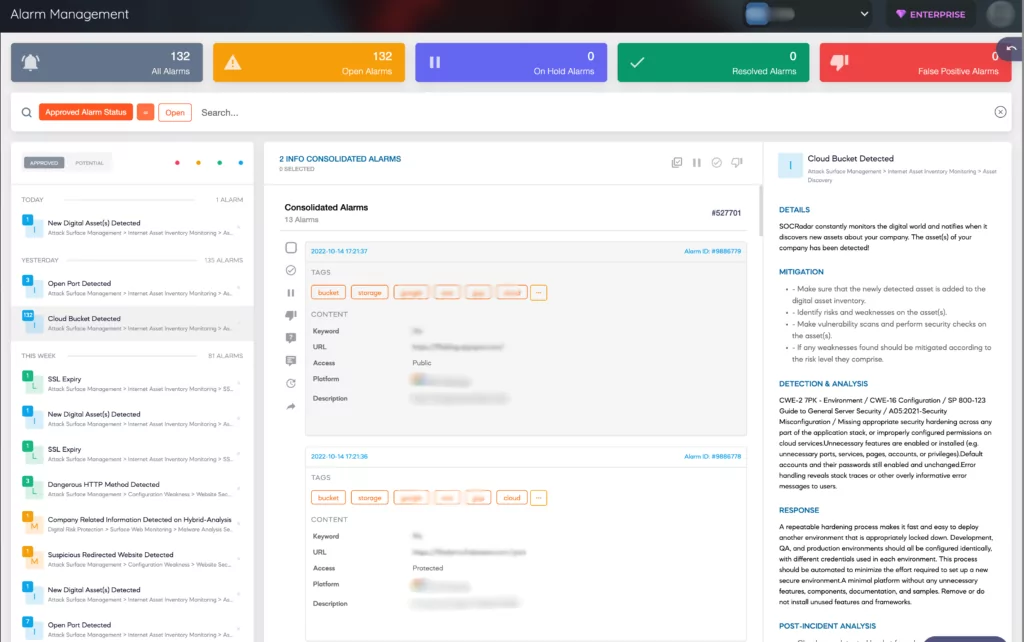
SOCRadar has expanded its External Attack Surface Management (EASM) services with the new Cloud Security Module (CSM) developed to ensure the security of its customers’ cloud storages. In addition to discovering new cloud buckets with EASM, cloud buckets can be defined as an asset thanks to the new module that can detect whether buckets are “public,” “private,” or “protected.” SOCRadar sends a “Cloud Bucket Detected” alert when it discovers new cloud storage owned by users, adding it to digital assets.
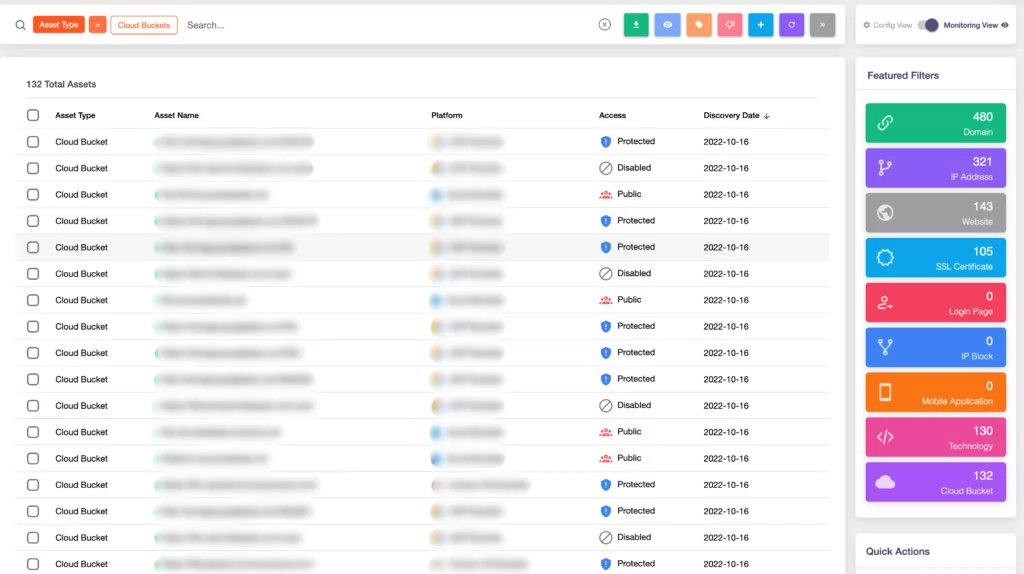
With SOCRadar CSM, your buckets’ status is constantly monitored. It also sends a “Cloud Bucket Status Change” alert when there is any change, for example, when the bucket’s status is changed from “private” to “public.”

Gartner is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


































