
Exploiting Multiple J-Web Vulnerabilities to Enable Unauthenticated Remote Code Execution in Juniper OS (CVE-2023-36844 through CVE-2023-36847)
Published on August 17, 2023, a significant security bulletin from Juniper Networks sheds light on a collection of vulnerabilities embedded in the J-Web component of Junos OS. While each vulnerability might seem innocuous with an individual medium-severity assessment, when combined, they conjure a critical challenge – the prospect of unauthenticated remote code execution.
Chaining Juniper Vulnerabilities for Remote Code Execution
These vulnerabilities have been cataloged under the CVE identifiers – CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, and CVE-2023-36847. The beauty, or rather the complexity, lies in how they interact synergistically to weave a dangerous narrative. An attacker, who might initially perceive these medium-severity vulnerabilities as inconsequential, could exploit their convergence to craft a chain reaction that leads to a pre-auth remote code execution scenario.
Unearthing the Vulnerability Chain
CVE-2023-36844 and CVE-2023-36845 point to PHP external variable modification weaknesses within J-Web. Exploiting these vulnerabilities empowers remote attackers to manipulate crucial environment variables, ultimately resulting in partial integrity loss. This, in turn, can serve as a stepping stone to exploit other vulnerabilities, underscoring the significance of comprehensive mitigation.
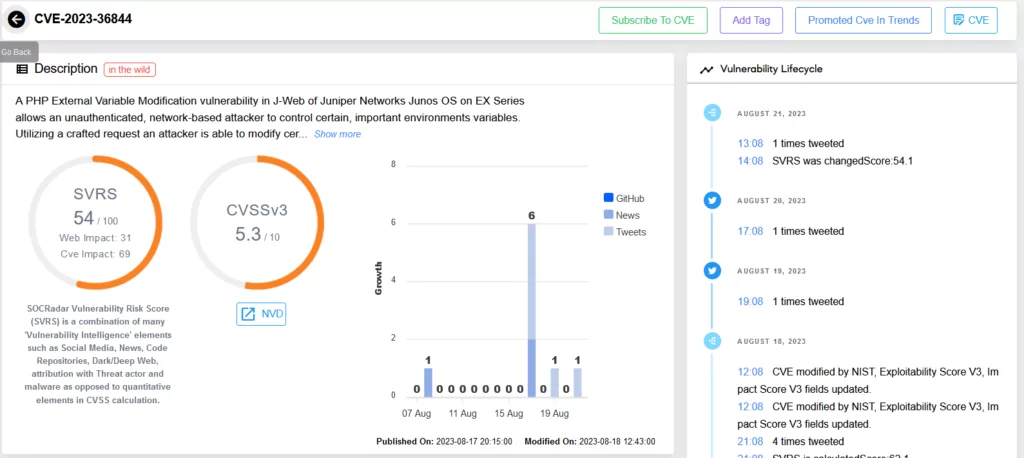
On the other hand, CVE-2023-36846 and CVE-2023-36847 expose missing authentication concerns in Junos OS on SRX Series. These vulnerabilities open avenues for attackers to upload arbitrary files via J-Web, leading to localized loss of file system integrity and the potential for further vulnerability chaining.
Countermeasures and Recommendations
To mitigate this extensive threat, Juniper Networks recommends disabling the J-Web interface or restricting access exclusively to trusted hosts. Swift remediation can be achieved by updating affected SRX and EX Series appliances to the latest Junos OS versions, ensuring that these vulnerabilities are thwarted before they can be exploited.
SOCRadar Vulnerability Intelligence: Enhancing Cyber Resilience
Understanding and staying ahead of such vulnerabilities is crucial. SOC teams can leverage SOCRadar’s Vulnerability Intelligence to receive real-time updates on emerging threats, ensuring proactive protection against potential exploits.
In conclusion, the Junos OS vulnerabilities underscore the evolving threat landscape and the necessity for robust external attack surface management. Timely updates, coupled with vigilant monitoring, can make all the difference in safeguarding critical assets against cyber adversaries.



































