
Access Sales for MediaMarkt, EU/US Companies, and Leaks of Indonesian Database, HelloKitty Ransomware
As the dark web’s intricate landscape unfolds, threat actors persist in their covert operations. In this vast digital domain, the SOCRadar Dark Web Team remains vigilant, revealing series of unsettling incidents each week.
From the sale of unauthorized access affecting several companies to the exposure of sensitive databases and the leak of a ransomware’s source code, this blog post explores the latest discoveries made by our dedicated team.
Find out if your data has been exposed.
Unauthorized VPN Accesses Sale is Detected for Several American Companies
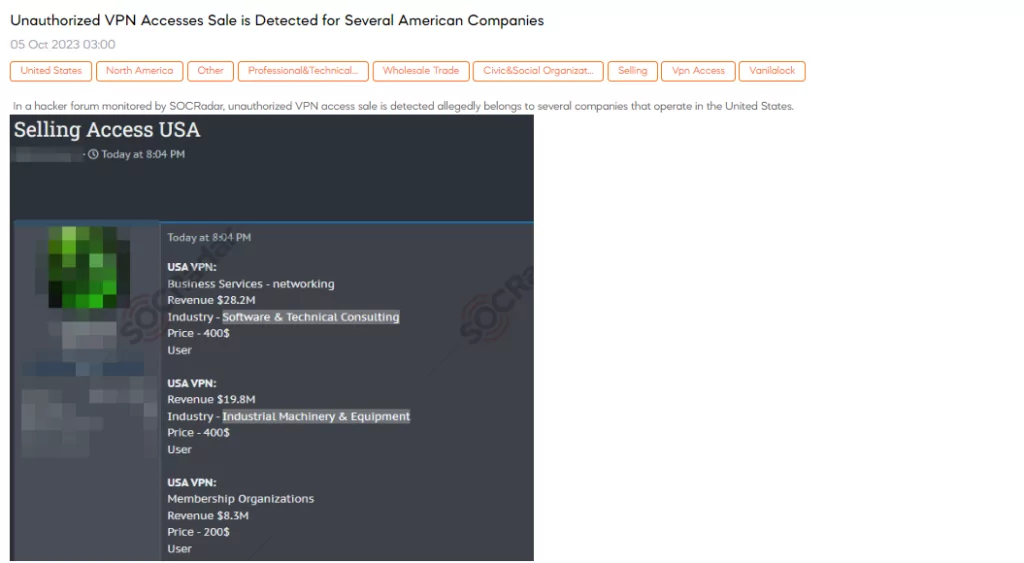
SOCRadar Dark Web Team detected a post where a threat actor claims to be selling unauthorized VPN access, allegedly belonging to several American companies. This post poses a significant security threat to these organizations and their data. The threat actor provides details about the compromised VPNs, including revenue and industry information, and the price for access, typically ranging from $200 to $400 per user.
Among the affected companies, there is one in the business services sector with a substantial revenue of $28.2 million, specializing in networking. Another, in the industrial machinery and equipment sector, reports revenue of $19.8 million. The third company falls under the category of membership organizations and reports revenue of $8.3 million.
Unauthorized Network Access Sale is Detected for a European Shop
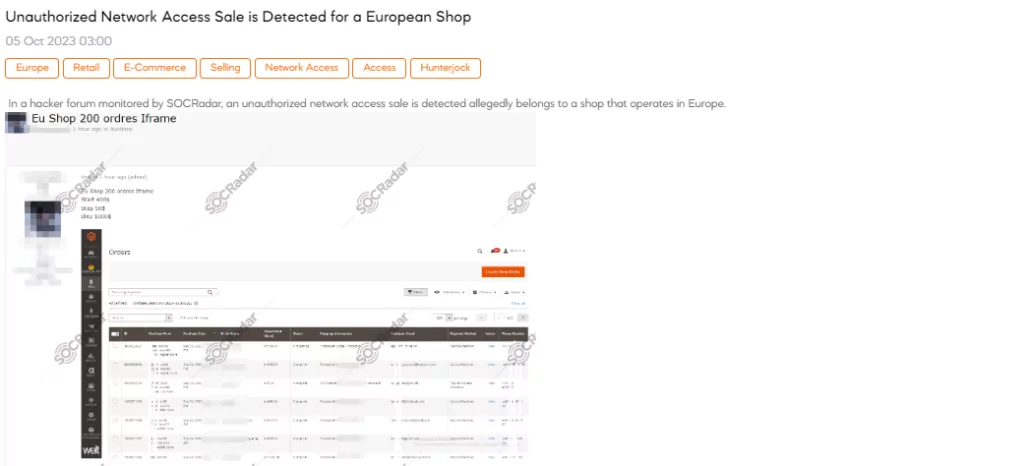
SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to be selling unauthorized network access belonging to a European shop. The threat actor is offering access that includes 200 orders via an iframe. The pricing structure is as follows: a starting price of $400, with increments of $50 for bidding, and an option for an instant purchase (Blitz) at $1,000.
Database of Indonesian National Civil Service Agency is on Sale
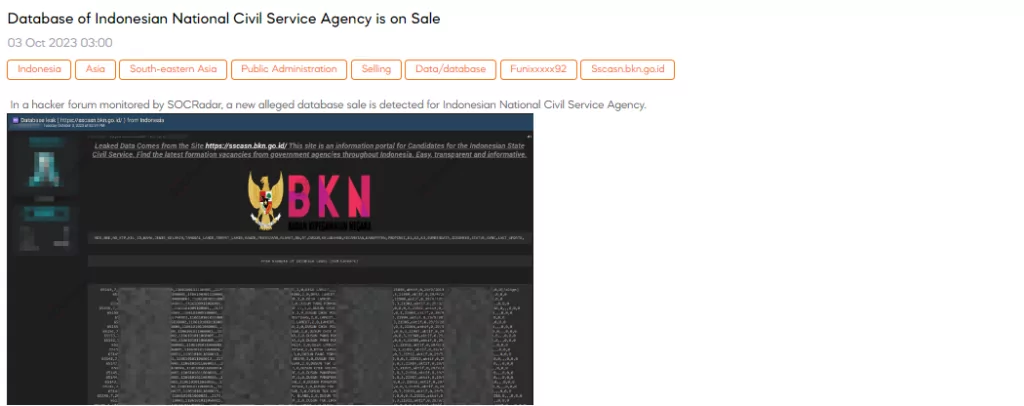
The SOCRadar Dark Web Team detected a post where a threat actor claimed to have access to a database from the Indonesian National Civil Service Agency. The threat actor claims that the leaked data allegedly originated from the website https://sscasn.bkn.go.id/, which serves as an information portal for candidates aspiring to join the Indonesian State Civil Service.
The information allegedly includes fields such as Nomor Induk Kependudukan (National Identity Number), Nomor Kartu Keluarga (Family Card Number), name, gender, date of birth, place of birth, marital status, occupation, address, etc.
Unauthorized Access Sale is Detected for MediaMarkt in Germany
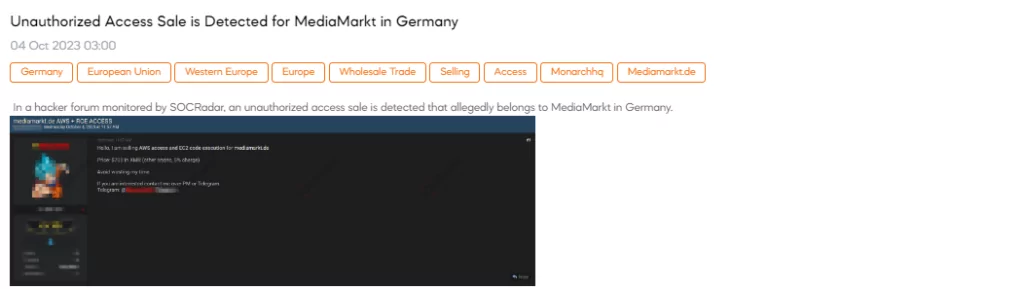
SOCRadar Dark Web Team has identified a post in which a threat actor claims to have unauthorized access for sale, allegedly belonging to MediaMarkt in Germany. The threat actor is offering AWS (Amazon Web Services) access and EC2 (Elastic Compute Cloud) code execution specifically for mediamarkt.de. The threat actor requests a payment of $700 in XMR (Monero cryptocurrency) for this access, with a 5% charge for using other cryptocurrencies.
Source Code of HelloKitty Ransomware is Leaked
SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor shared source code of HelloKitty ransomware. The threat actor claims they are preparing a new product that will attract more interest than LockBit.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































