
OpenVPN Access Server Vulnerabilities: Risk of Information Exposure, DoS, and RCE (CVE-2023-46849, CVE-2023-46850)
Last week, OpenVPN Access Server, a widely-used open-source VPN solution, received an update addressing two vulnerabilities, tracked as CVE-2023-46849 and CVE-2023-46850. Although CVSS scores for these vulnerabilities are pending, they can enable attackers to gain unauthorized access to sensitive information and, in some cases, facilitate Remote Code Execution (RCE).

Which Versions of OpenVPN Access Server Are Affected?
Reportedly, the following versions of OpenVPN Access Server include a copy of OpenVPN 2.6 – 2.6.6 that is susceptible to CVE-2023-46849 and CVE-2023-46850, making them vulnerable to exploitation:
- Versions from 2.11.0, to and including 2.11.3
- Versions 2.12.0 and 2.12.1
Vulnerability Details
The first vulnerability, CVE-2023-46849, is described as a “division by zero crash.” It occurs when users have enabled the –fragment option in specific configurations within OpenVPN versions 2.6.0 to 2.6.6. If exploited successfully, the vulnerability could cause a crash in the application, resulting in a Denial-of-Service (DoS) and potentially exposing sensitive data.
According to OpenVPN’s security advisory, CVE-2023-46849 is not easily exploitable on Access Server because the default configuration it comes with does not include the –fragment option. Additionally, the control channel security further complicates exploitation.
The second vulnerability, CVE-2023-46850, is considered a more severe issue. It is described as a Use-After-Free memory vulnerability, leading to undefined behavior.
The security advisory on the OpenVPN community Wiki states, “OpenVPN 2.6 from v2.6.0 up to and including v.2.6.6 incorrectly use a send buffer after it has been free()d in some circumstances, causing some free()d memory to be sent to the peer. All configurations using TLS (e.g. not using –secret) are affected by this issue.”
Attackers could potentially leak sensitive information from the OpenVPN Access Server’s memory, through memory buffer leaks or perform RCE by sending network buffers to a remote peer. This poses significant risks, providing attackers the opportunity to take control of the affected server.
Apply the Patch for OpenVPN Access Server Vulnerabilities
To address the vulnerabilities, OpenVPN has released version 2.12.2 of OpenVPN Access Server, which includes the recently released version 2.6.7 of OpenVPN, effectively resolving CVE-2023-46849 and CVE-2023-46850.
OpenVPN strongly advises users currently running a vulnerable version of OpenVPN Access Server to promptly upgrade to version 2.12.2 to safeguard their systems from potential exploitation.
OpenVPN’s advisory provides the procedure on how to upgrade the Access Server, which you can find here.
How Can SOCRadar Help?
SOCRadar actively monitors organizations’ digital assets inventory, delivering timely alerts on emerging security issues. This proactive approach enables organizations to patch vulnerabilities before threat actors can exploit them.
Utilizing the Attack Surface Management module, you can view the Company Vulnerabilities. Additionally, through the Vulnerability Intelligence module, you can obtain extensive information on all known vulnerabilities, including their timelines encompassing updates and exploitation events.
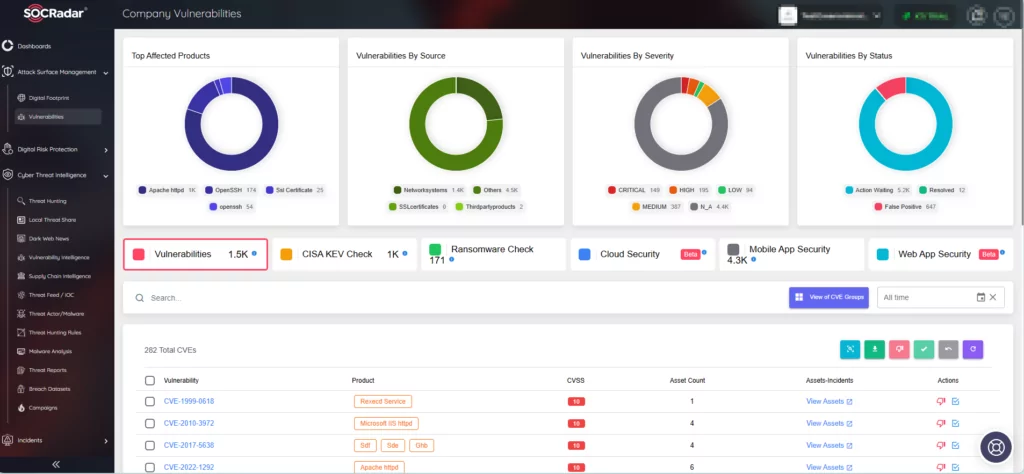
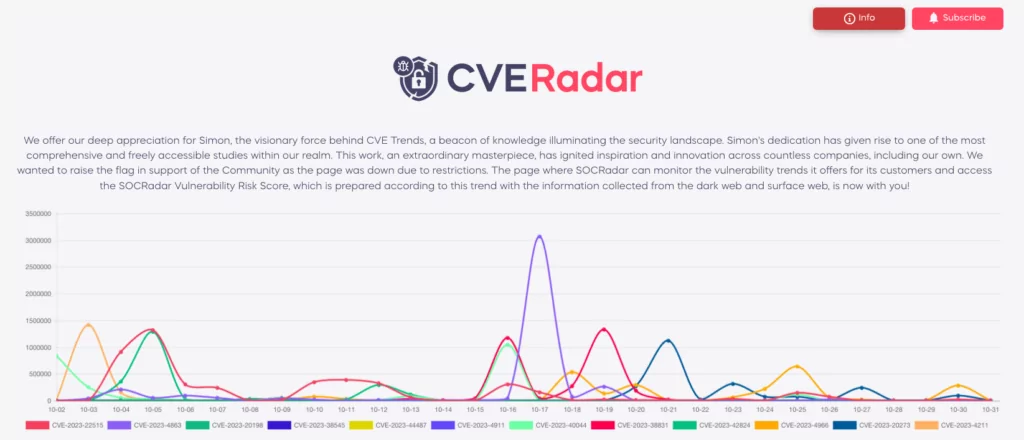
For a preview of the Vulnerability Intelligence capabilities of SOCRadar XTI, you can explore CVE Radar, a complimentary feature provided by the platform. Here, you can stay updated on the latest emerging vulnerabilities, gaining insights into the evolving threat landscape.
Beyond prompt patching, it is advised to enforce strong password policies and implement Multi-Factor Authentication (MFA) measures for your VPN instances. Setting up restrictions to limit VPN access to devices within your organization and whitelisting users can enhance security.
You can assess your VPN security now in SOCRadar Labs through the VPN Security feature.



































