
RCE Vulnerability in OpenSSH’s SSH-Agent Forwarding: CVE-2023-38408
SSH-Agent is a widely used program that holds private keys for public key authentication, providing a secure and convenient way to log in to remote machines using SSH. It is also considered a secure and alternative way to password login, which is considered dangerous for the occasions in which case of history of the command line is exposed or a keystroke listener is installed on the client.
One of its functionalities is agent forwarding, which allows users to access their local SSH-agent from remote servers. However, recent research by Qualys has shed light on a potential security vulnerability related to it that led to remote code execution in the client’s machine.
In this blog post, we will explore the issue, its root cause, and its implications for users and system administrators.
SSH-Agent’s Manual Page: Known Caveats, Surprising Effects
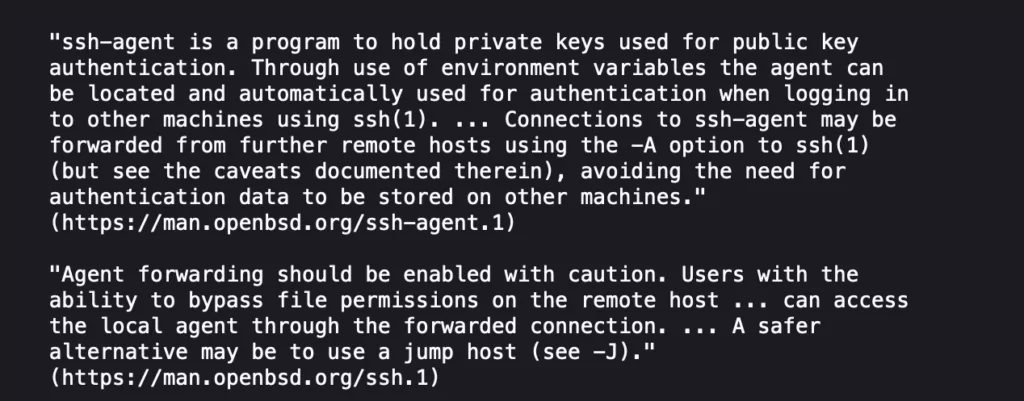
Although manual pages of the SSH-Agent (man SSH-agent) program warn users about the possibility of potential dangers, SSH-agent forwarding is still widely used today.
Researchers from Qualys explain potential attack vectors and consequences by a sample scenario whose main actor is an infamous, fictional character of the infosec world: Alice.
“A system administrator (Alice) runs SSH-agent on her local workstation, connects to a remote server with ssh, and enables SSH-agent forwarding with the -A or ForwardAgent option, thus making her SSH-agent (which is running on her local workstation) reachable from the remote server.”
According to researchers from Qualys, a remote attacker who has control of the host, which Alice has connected to, can load (dlopen()) and immediately unload (dlclose()) any shared library in /usr/lib* on Alice’s workstation (via her forwarded SSH-agent if it is compiled with ENABLE_PKCS11, which is the default).
The vulnerability lies in how SSH-agent handles forwarded shared libraries. When SSH-agent is compiled with ENABLE_PKCS11 (the default configuration), it forwards shared libraries from the user’s local workstation to the remote server. These libraries are loaded (dlopen()) and immediately unloaded (dlclose()) on the user’s workstation. The problem arises because certain shared libraries have side effects when loaded and unloaded, which can be exploited by an attacker who gains access to the remote server where SSH-agent is forwarded to.
The Root Cause of the SSH-Agent Vulnerability
The root cause of this vulnerability is the combination of the SSH-agent’s forwarding mechanism and the side effects of shared libraries. Shared libraries in /usr/lib* are assumed to come from official distribution packages and are not expected to perform operations other than dlopen() and dlclose(). Unfortunately, chaining certain side effects from these libraries allows an attacker to achieve remote code execution in SSH-agent.
Implications
The implications of this vulnerability are significant. An attacker who gains access to the remote server where SSH-agent is forwarded could potentially execute malicious code on the user’s local workstation. This could lead to unauthorized access, data theft, or even a complete compromise of the user’s system.
Mitigations for the SSH-Agent Forwarding RCE Vulnerability
Given the potential risks associated with forwarding, users and system administrators should exercise caution when enabling this feature. While it offers convenience, it also increases the attack surface.Here are some steps to mitigate the risk:
- Minimize Agent Forwarding: Limit the use of forwarding to only when necessary. Avoid enabling forwarding for every SSH session and only use it on trusted remote servers.
- Use Jump Hosts: Consider using the -J option in SSH to specify a jump host. This approach allows you to access remote servers through an intermediary host, reducing the exposure of your SSH-agent.
- Disable PKCS#11 Support: If possible, compile the SSH-agent without ENABLE_PKCS11 to prevent forwarding shared libraries and reduce the potential attack surface.
- Keep Software Updated: Regularly update your operating system and SSH software to ensure you have the latest security patches: OpenSSH 9.3p2 or later
Stay One Step Ahead of Attackers with SOCRadar Vulnerability Intelligence
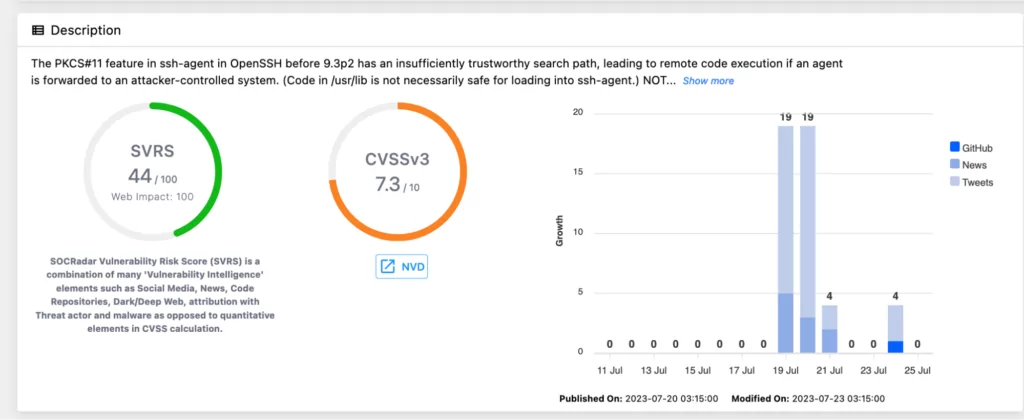
SSH-Agent forwarding is a powerful feature that enhances the usability of SSH, but it comes with certain risks. The recent research highlighting potential vulnerabilities in SSH-agent forwarding reminds us of the importance of security best practices. Users and system administrators can maintain a secure SSH environment and protect their systems from potential threats by understanding the risks and taking necessary precautions.
SOCRadar’s Vulnerability Intelligence module provides valuable support to organizations in handling issues like the recently discovered SSH-agent vulnerability. As threat actors continuously monitor vulnerability trends and exploit potential weaknesses, it becomes crucial for businesses to stay vigilant and well-informed.
Sign up for a free edition of the SOCRadar to learn more and stay up to date on the latest vulnerabilities.

































