Critical RCE Vulnerability in ShareFile: PoC Exploit Available
[Update] August 1, 2023: Researchers from Greynoise warn of the first attempts to exploit the vulnerability in Citrix ShareFile. Added the subheading “First Exploits Found in Citrix ShareFile Vulnerability.”
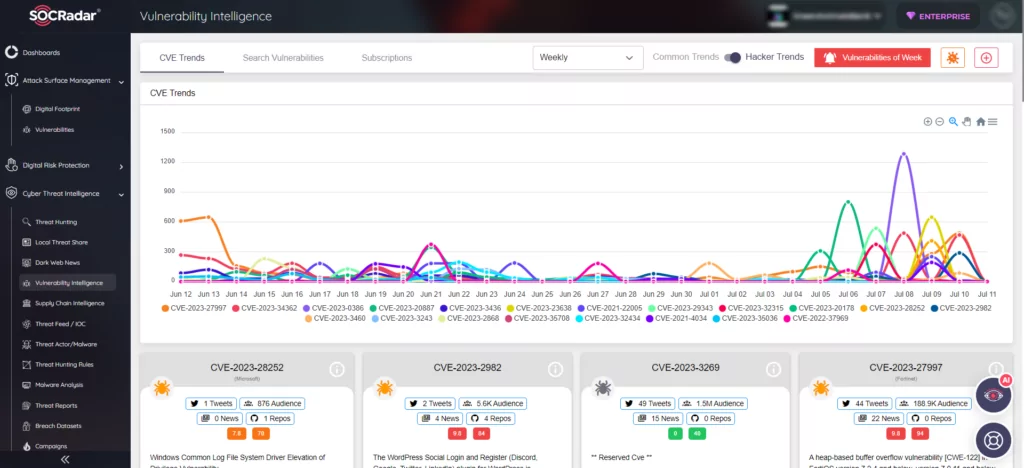
ShareFile, a cloud-based file sharing application, has a critical vulnerability that recently came to light. The vulnerability, CVE-2023-24489, allows unauthenticated arbitrary file upload and remote code execution (RCE).
CVE-2023-24489 (CVSS score: 9.8) is a cryptographic bug in ShareFile’s Storage Zones Controller, a .NET web application running under IIS.
Researchers at Assetnote exploited the bug, which enabled them to achieve unauthorized access and control. By manipulating the upload process and exploiting flaws in the encryption implementation, the researchers could successfully bypass authentication checks and upload a webshell.
Unauthenticated File Uploads in ShareFile
During their investigation of ShareFile, the Assetnote researchers focused on the .NET web technologies used in the application. They honed in on the .aspx files, as they required no additional effort to access.
By examining these files, they identified a specific endpoint, “/documentum/upload.aspx,” designed for file uploads. The researchers discovered that this endpoint lacked proper authentication checks, making it an attractive target for exploitation.
Cryptographic Oversights: Exploiting AES Encryption and Padding in ShareFile
The vulnerability arose from errors in ShareFile’s handling of cryptographic operations. The application used AES encryption with CBC mode and PKCS#7 padding, but it did not properly validate decrypted data. This oversight allowed researchers to generate valid padding and execute their attack.
AES, a block cipher with a fixed block size of 128 bits (16 bytes), can only encrypt and decrypt data in 16-byte blocks. To handle messages that are not multiples of 16 bytes, padding is added to ensure the length becomes a multiple of 16.
In .NET, the default padding mode for AES is PKCS#7, where each added byte represents the total number of bytes added.
Also, block ciphers have a limitation: identical blocks encrypt to the same value, resulting in patterns from the plaintext being preserved in the ciphertext. This vulnerability can be exploited to break the encryption.
To prevent this, modes of operation like Cipher Block Chaining (CBC) introduce randomness by chaining blocks together. In CBC mode, each block is XORed with the previous encrypted block.
Proof-of-Concept Exploit of ShareFile Vulnerability (PoC)
The researchers used two blocks to find a message with valid padding. They modified the final byte of the first block while keeping the rest unchanged.
If the researchers encountered the error message “Invalid request method – GET,” it indicated their successful progress beyond the decryption stage and reaching the subsequent check, which verified the request method as a POST. This outcome was satisfactory as their objective at that stage was to determine the value for “parentid.”
The “parentid” refers to a query parameter used in the ShareFile application. It plays a role in the file upload process and helps determine the parent directory where the uploaded file should be stored.
After several attempts, the researchers identified a “parentid” value that did not trigger a padding exception. They then combined this value with the path traversal to upload an .aspx file to a writable directory in the webroot. Finally, the researchers requested the uploaded file:
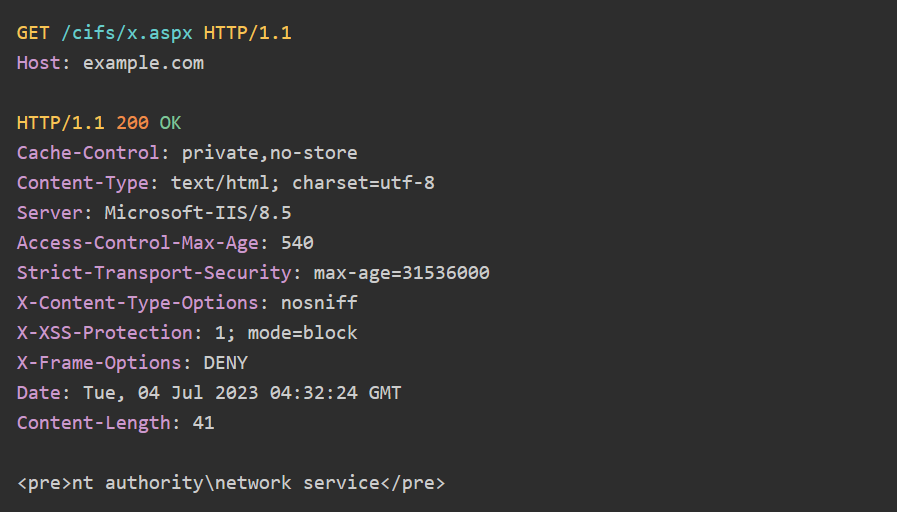
First Exploits Found in Citrix ShareFile Vulnerability
Researchers from Greynoise warn of the first attemptsto exploit the vulnerability in Citrix ShareFile. Attackers can misuse the application’s handling of cryptographic operations to achieve unauthenticated arbitrary file upload and remote code execution. Greynoise has observed suspicious IPs attempting to exploit this flaw, including two never seen before.
Apply the Patch for ShareFile
Citrix has released a security update addressing the ShareFile vulnerability. Users are advised to apply the update.
It is important for developers to exercise caution when implementing cryptography. Default settings and common practices may introduce vulnerabilities. To prevent similar issues, developers should consider encryption modes that provide authentication, such as AES in GCM mode, or adopt the “Encrypt-then-MAC” approach.
Better Patch Management with SOCRadar
Moreover, with the advanced monitoring capabilities offered by SOCRadar, you can promptly detect vulnerabilities across your digital assets and swiftly take necessary actions. SOCRadar’s Attack Surface Management enables real-time tracking of vulnerabilities in automatically identified products within your organization’s digital footprint. This capability empowers you to prioritize assets and vulnerabilities, streamline patch management processes, and effectively fortify your organization against potential risks, ensuring enhanced security measures.
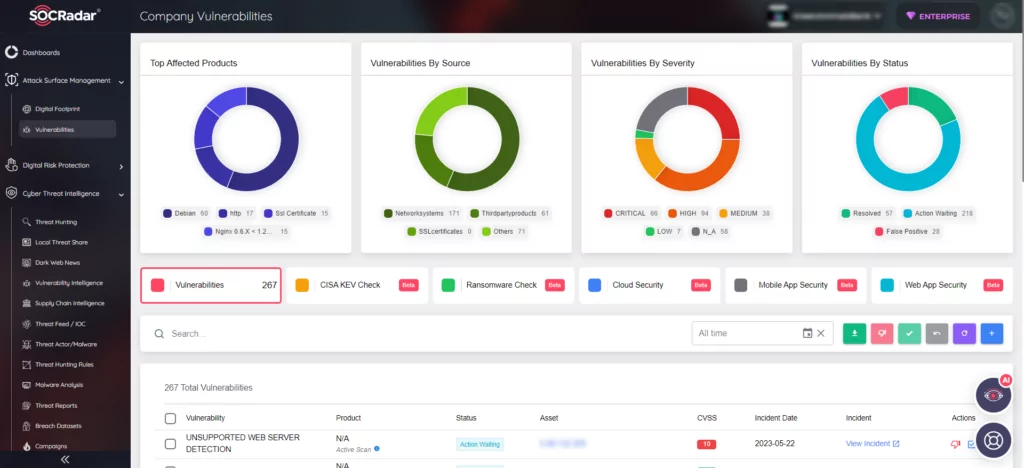
In security research, identifying vulnerabilities is crucial for application safety and data protection. With SOCRadar Vulnerability Intelligence, you get comprehensive details on vulnerabilities, including latest updates, mentions, vulnerability lifecycle, as well as available Indicators of Compromise (IoC) and Proof-of-Concept (PoC) exploits. Using SOCRadar’s intelligence, you can track exploit trends and enhance protection against threats.