
Ivanti Released a Patch in Endpoint Manager Solution (EPM) for a Critical Vulnerability, CVE-2023-39336
Ivanti has addressed a critical vulnerability in its Endpoint Manager (EPM) solution, identified as CVE-2023-39336, with a critical severity score of 9.6/10. This vulnerability, affecting Ivanti EPM versions 2021 and 2022 prior to SU5, could enable Remote Code Execution (RCE) on affected servers.The vulnerability involves an SQL injection that does not require authentication, allowing attackers to execute arbitrary SQL queries and potentially control machines running the EPM agent. The issue is especially severe when the core server uses SQL Express.
Details of the CVE-2023-39336 Vulnerability Affecting Ivanti EPM
Ivanti has provided an advisory here and a restricted access for its customers here, for full details page and further details. Although vulnerability details are not shared, probably to give customers time to fix it, they will be announced in the coming days and this blog will be updated.
Ivanti Updates in December
Ivanti’s last month security update for Avalanche, its Mobile Device Management (MDM) product, addressed 22 vulnerabilities, 13 of which are critically severe. These vulnerabilities, identified in older versions of Avalanche (back to 6.3.1 and likely affecting all 6.X versions), included stack-based, unauthenticated, and heap-based buffer overflows, enabling Remote Code Execution without user interaction. Throughout the year, we shared blog posts on other significant vulnerabilities affecting Ivanti products as well.
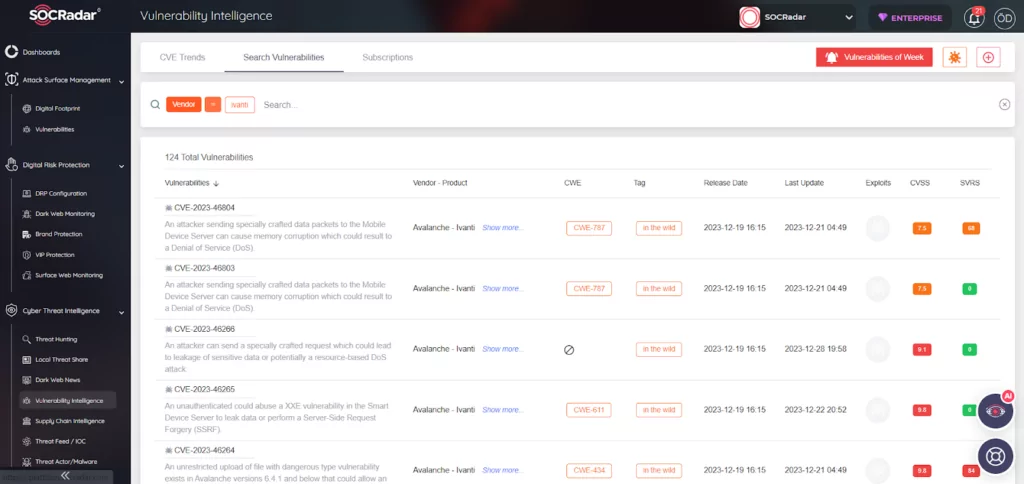
Through SOCRadar’s Vulnerability Intelligence, you may search for vulnerabilities based on vendor or product.
Vulnerability Management with SOCRadar
The Attack Surface Management (ASM) feature of SOCRadar offers efficient tools for the quick detection, assessment, and resolution of security vulnerabilities. Through ASM, organizations gain insights into their asset inventory and timely alerts on relevant security issues, ensuring a swift response and enhanced protection of organizational assets.
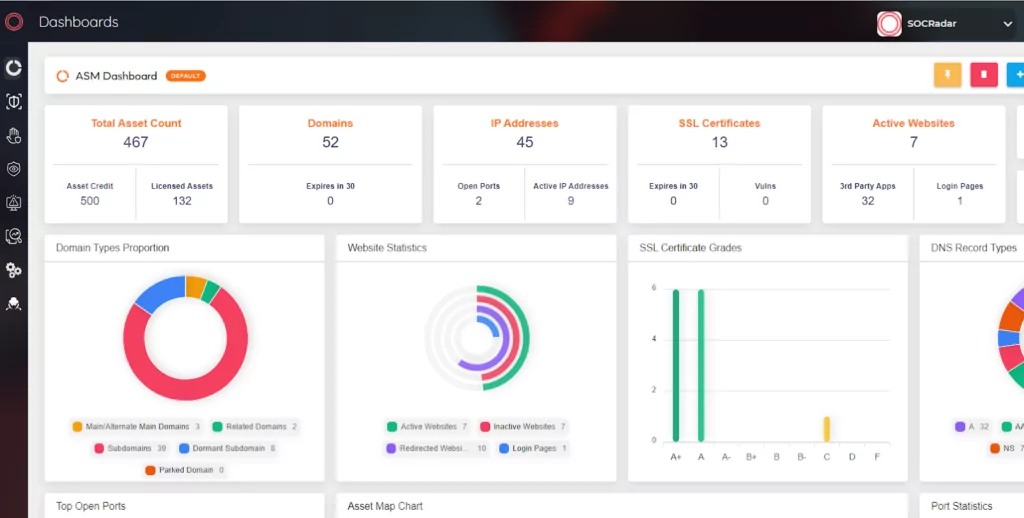
SOCRadar Attack Surface Management



































