
Sales of Trello Database, Ivanti Zero-Day Exploits, Phantom Loader, US and Australia Credit Cards
In SOCRadar Dark Web Team’s latest findings, from their week-long monitoring of the dark web, an unauthorized access sale concerning an Italian company has surfaced. Last week’s notable breaches include the database of Trello, a project management platform, with over 15 million entries. The findings also reveal sales of credit cards from the US and Australia, while a new malware loader tool, namely Phantom Loader, is offered for sale on a hacker forum. One of the most alarming discoveries from last week is the sale of exploits for zero-day vulnerabilities affecting Ivanti Secure Connect VPN appliances.
Unauthorized RDP Access Sale is Detected for an Italian Company
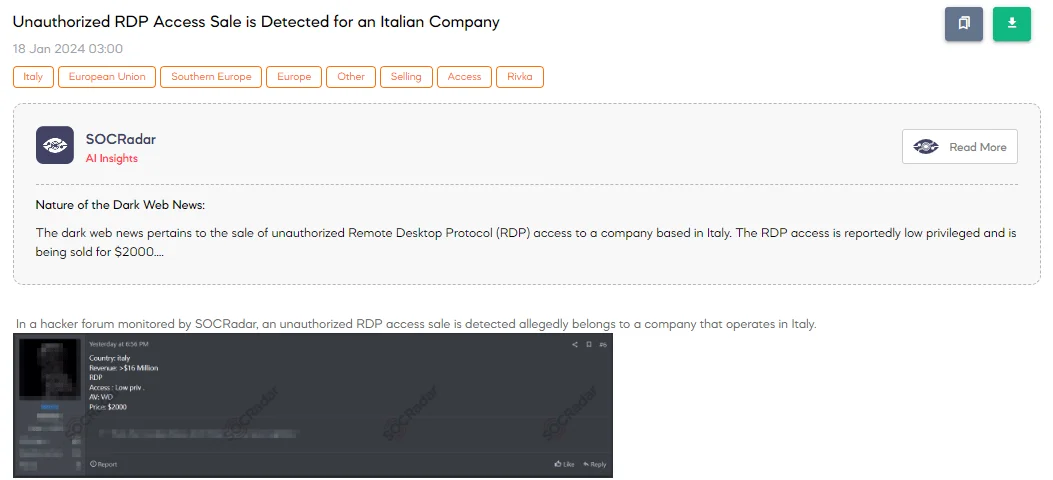
The SOCRadar Dark Web Team has identified a post on a hacker forum advertising the sale of unauthorized Remote Desktop Protocol (RDP) access. This access allegedly pertains to an Italian company with revenues exceeding $16 million. The threat actor offers low-privilege RDP access, noting that the company’s antivirus is Windows Defender (WD). The sale price for this unauthorized access is set at $2,000.
Database of Trello is on Sale

On 16 January, A SOCRadar Dark Web Analyst detected a post on a hacker forum where a threat actor claimed to have unauthorized access to a Trello database. This database allegedly contains 15,115,516 entries, including emails, usernames, full names, and other account information from Trello.com. The threat actor offers to sell this data to a single buyer and is available for contact through the forum or Telegram. To demonstrate the authenticity of the data, a sample containing all entries matching the term ‘cheko’ is mentioned. This incident points to a severe potential data breach involving many Trello users.
Ivanti Vulnerabilities CVE-2023-46805 and CVE-2024-21887 On Sale
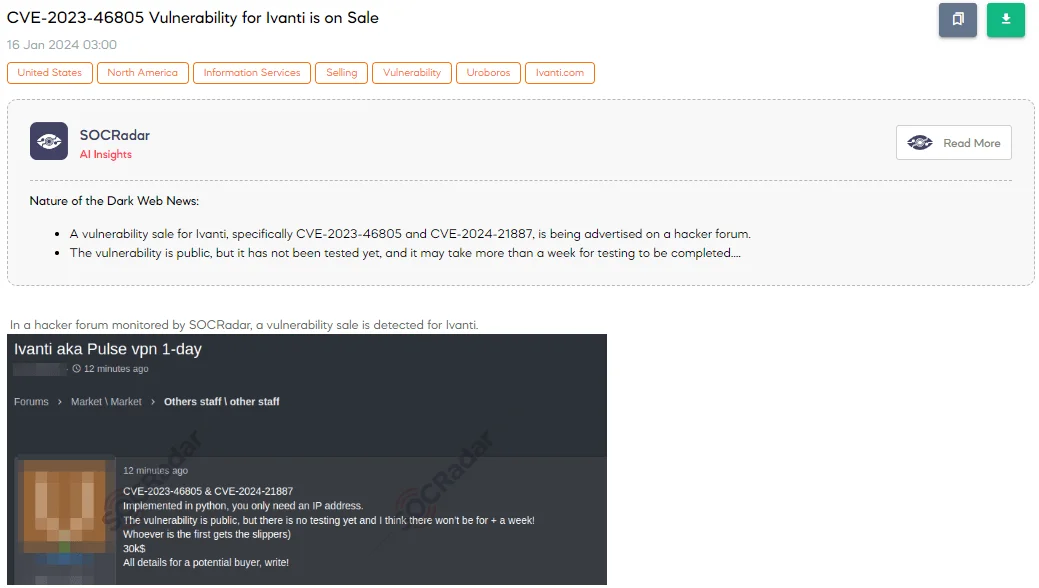
The SOCRadar Dark Web Team has discovered a post on a hacker forum where a threat actor is selling a vulnerability related to Ivanti. They are offering information on two vulnerabilities, CVE-2023-46805 and CVE-2024-21887, for $30,000. The actor highlights that the exploit is implemented in Python and requires only an IP address for execution.
CVE-2023-46805, with a high CVSS score of 8.2, is an authentication bypass flaw found in Ivanti Connect Secure and Ivanti Policy Secure, versions 9.x and 22.x. This vulnerability allows remote attackers to bypass security measures and access restricted resources.
The second vulnerability, CVE-2024-21887, is even more severe, with a critical CVSS score of 9.1. It’s a command injection flaw in the web components of Ivanti Connect Secure and Ivanti Policy Secure. This vulnerability allows an authenticated administrator to execute arbitrary commands through specially crafted requests.
A New Loader Tool Phantom Sale is Detected
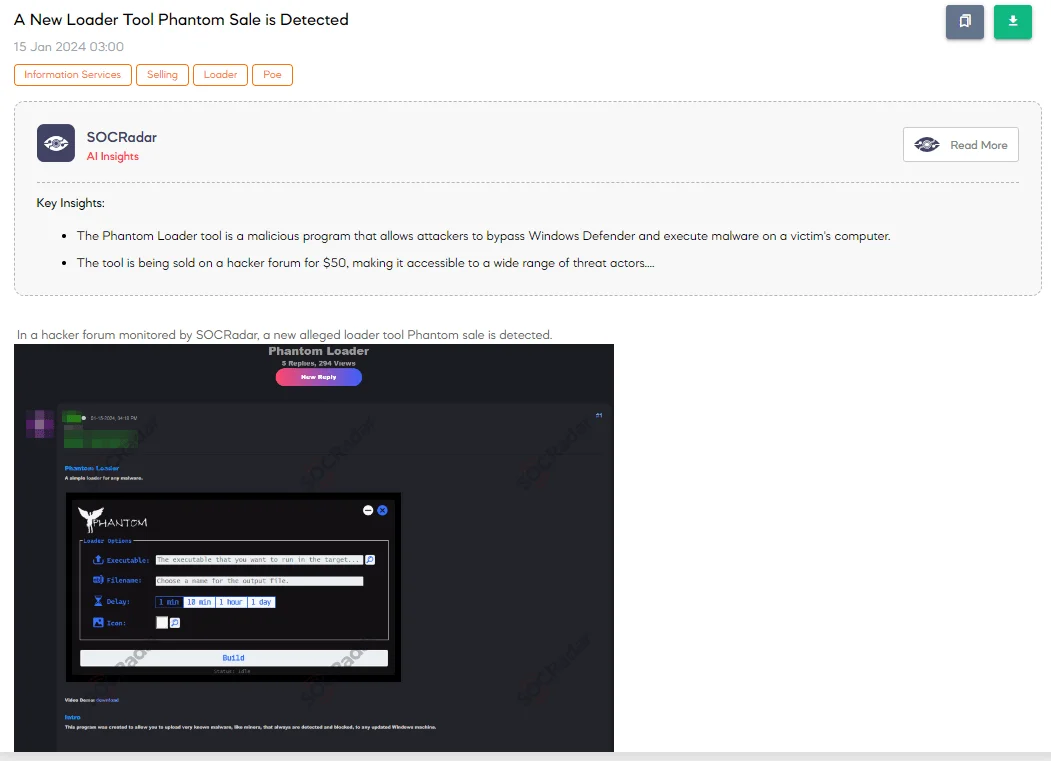
A new cybersecurity threat has emerged with the detection of a sale for a loader tool named Phantom. The threat actor advertises Phantom Loader as a simple yet effective tool for deploying malware on updated Windows machines, including those commonly blocked by security systems. The tool is designed to embed malware within an innocuous-looking executable. Upon execution, it automatically creates a Windows Defender exclusion, extracts the malware to the system, and schedules it to run, ensuring the malware operates undetected.
Key features of the Phantom Loader include the ability to function without an internet connection, automatic bypassing of Windows Defender, customizable executable icons through uploaded images, and the option to set custom execution delays via scheduled tasks. The package offered includes the Phantom Loader, a demonstration video, one year of support and updates, and compatibility with Windows 10 and 11.
10K Credit Cards Belonging to Australia are on Sale
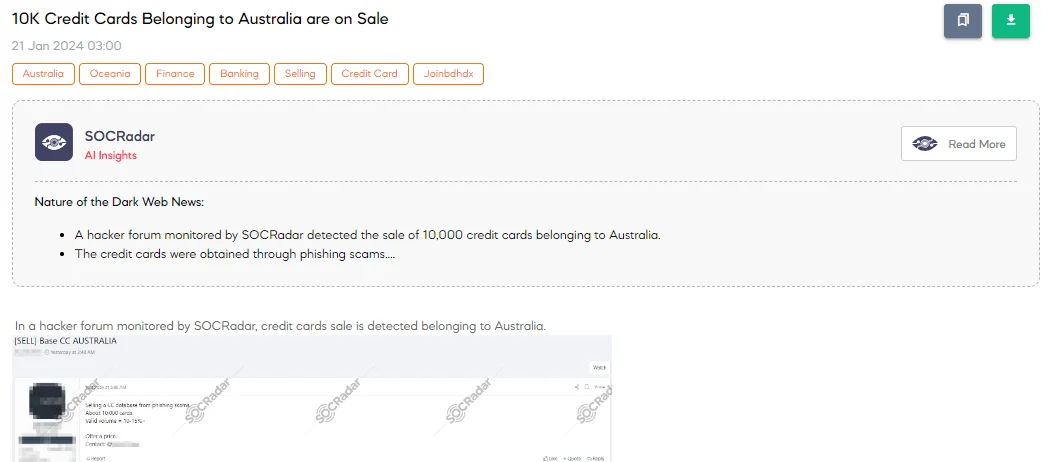
On 21 January, The SOCRadar Dark Web Team has identified a post on a hacker forum advertising the sale of a database containing around 10,000 credit cards from Australia obtained through phishing scams. The threat actor claims that 10-15% of these cards are valid and invites offers to purchase this database.
Credit Cards Belonging to the United States are on Sale
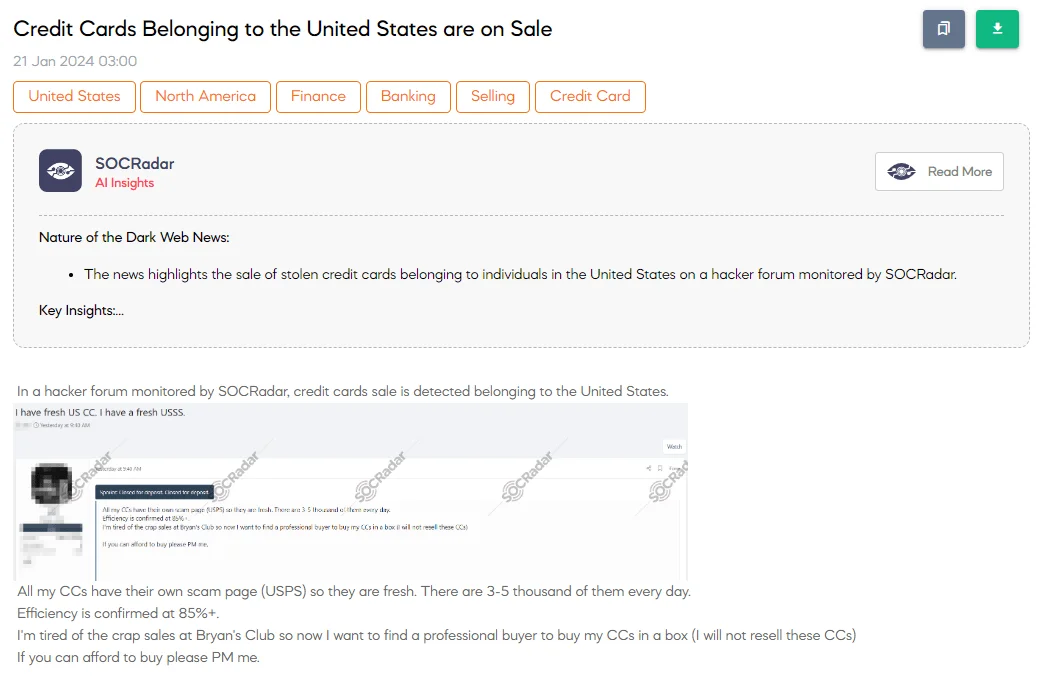
The SOCRadar Dark Web Team has detected a post on a hacker forum regarding the sale of credit cards from the United States. The threat actor advertising these credit cards claims they are sourced daily, numbering between 3,000 to 5,000, using their scam page disguised as the United States Postal Service (USPS). This method ensures the freshness of the credit cards. The actor boasts an efficiency rate of over 85% and desires to find a professional buyer for these cards, emphasizing exclusivity by not reselling the same credit cards.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































