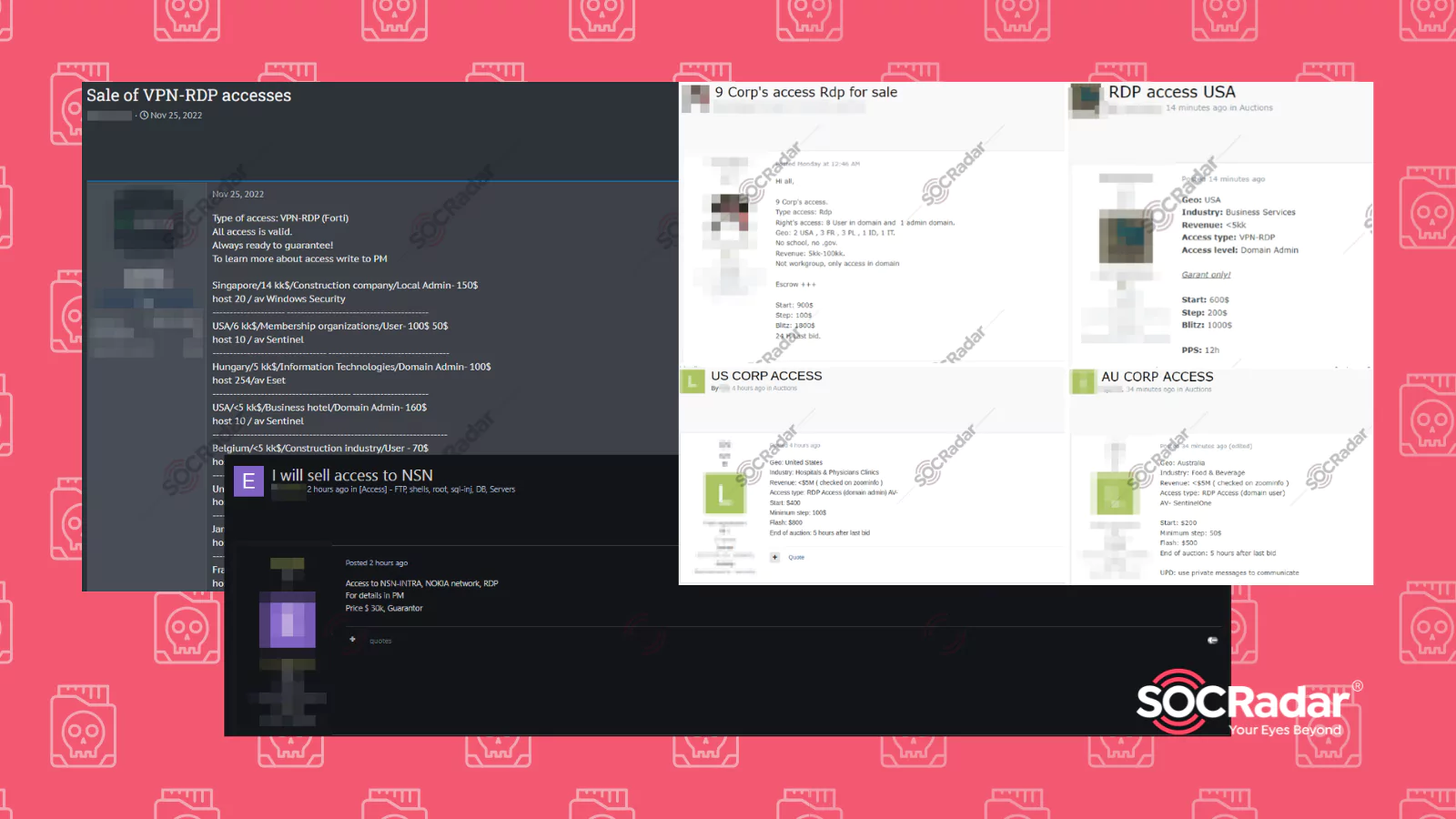
RDP Access Sales on Dark Web Forums Detected by SOCRadar
Remote Desktop Protocol, or RDP, is a protocol developed by Microsoft. It allows the user to control another computer over a network connection. RDP is one of the most common tools for managing remote machines. It has become more significant during and after the pandemic. According to research, the total percentage of participants that worked from home at least one day a week increased to 81%.
Threat actors have noticed this trend as well. They are aware that lots of employees are using RDP daily. With the addition of simple password usage and lack of extra layers of protection, it became an attractive vector for the threat actors to leverage. Threat actors are actively selling RDP access on dark web forums. They’re offering it to other criminals who want to commit fraud, data breaches, or even launch ransomware attacks.
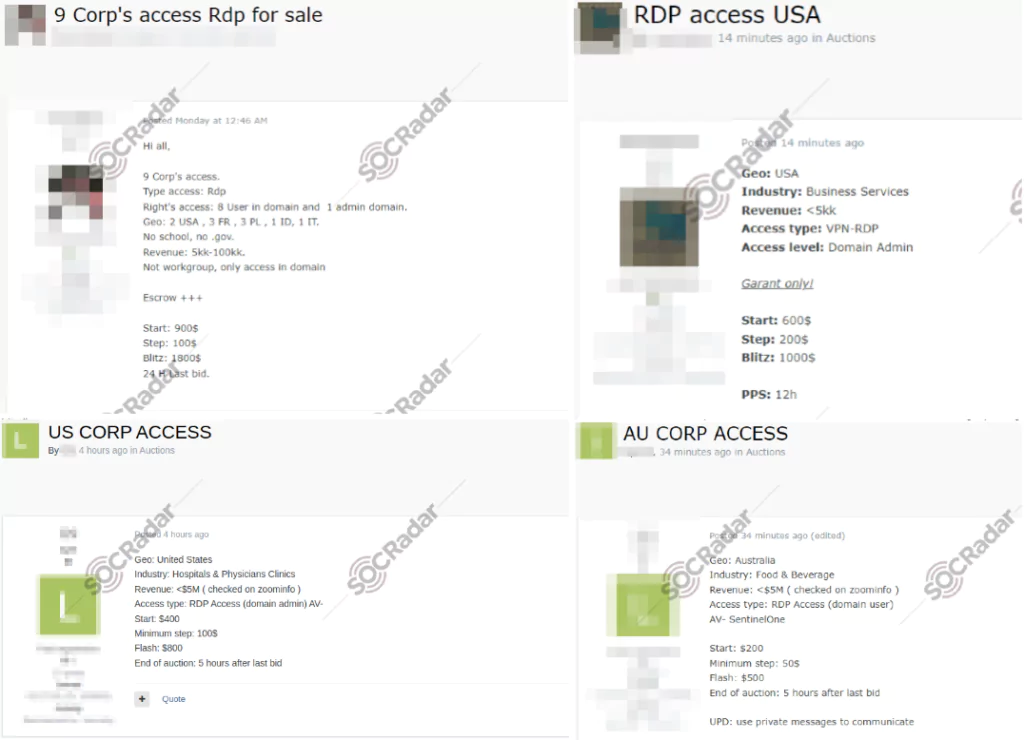
Experienced actors (e.g., ransomware groups) may find it easier to pay for access rather than spend time looking for vulnerabilities. On the other hand, less experienced actors might not be able to complete a full-scale attack. So, they can still make money by selling RDP access.
In this blog post, we’ll discuss these RDP access sales on dark web forums with the help of SOCRadar Threat Intelligence. Understanding the threat they pose to organizations and the risks of using RDP without proper security measures is essential. Let’s dive into the world of RDP access sales and learn how we can protect ourselves!
Overview of the RDP Access Sales Data
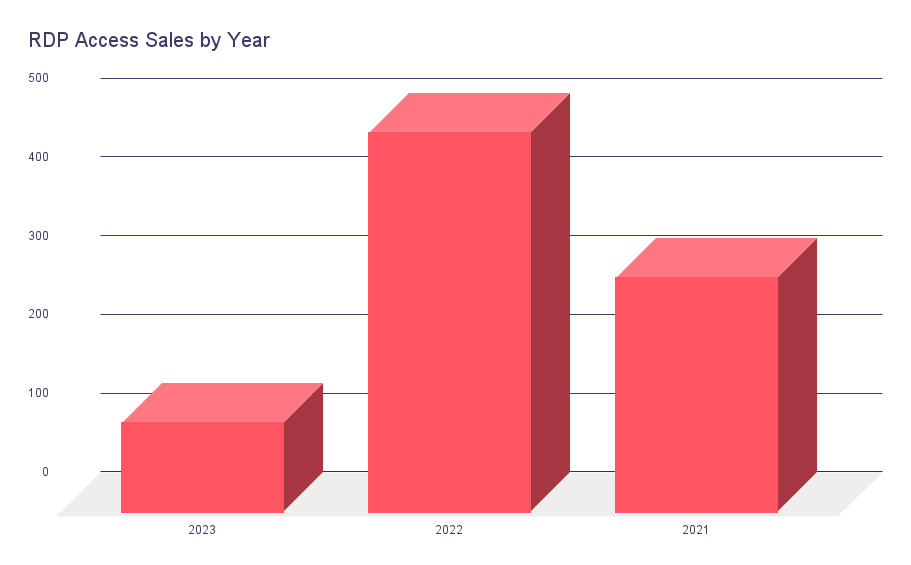
In the following statistics, we examined 891 RDP access sales posted on dark web forums provided by SOCRadar Threat Intelligence. The data dates back to 2021. Let’s dig in!
Researchers have observed the usage of stealers as a widespread method to obtain RDP access. Stealers are malicious software that steals sensitive information, including RDP credentials, from infected systems.
Furthermore, there has been a significant increase in the initial access market, mainly consisting of RDP accesses, as stated in this article, with a growth rate of over 50% from 2021 to 2022. This situation can also be seen in the graphic above. 2022 hits higher than 2021. We cannot predict the future precisely. However, trends indicate that 2023 will not see a pretty high number of RDP access sales.
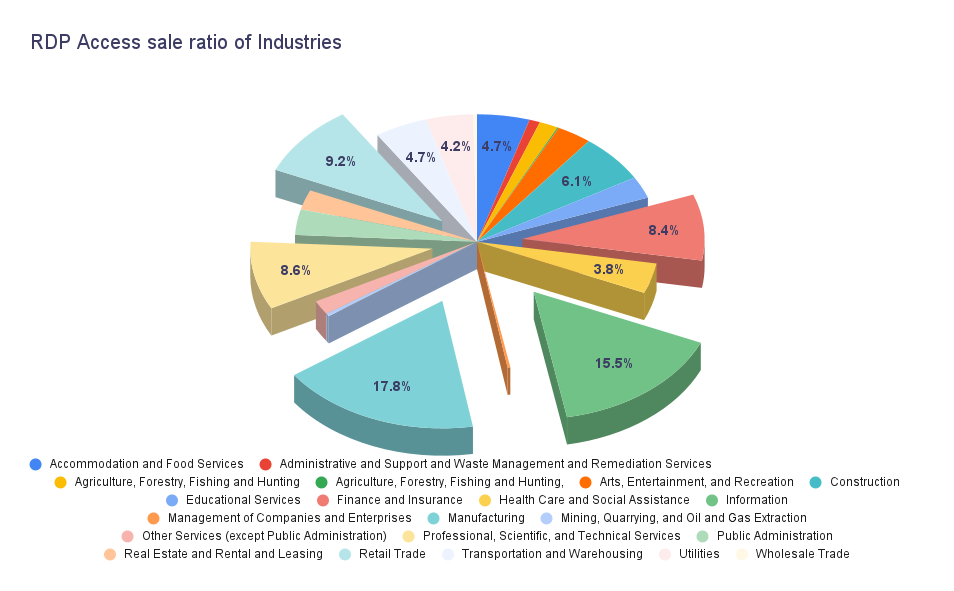
The above data reveals varying rates of RDP access sales across different industries. The manufacturing industry shows a relatively higher sale rate at 17.8%, followed by the information industry at 15.5%. Retail trade accounts for 9.2% of RDP access sales, while professional, scientific, and technical services make up 8.6%. The finance and insurance industry has an RDP access sale rate of 8.4%.
These industry-specific sale ratios can be attributed to several factors. Manufacturing, information, and retail trade industries may be targeted due to lower security measures. They may be more vulnerable to exploitation. The professional, scientific, and technical services industry may be attractive to RDP access sellers because of its potentially valuable intellectual property. On the other hand, the finance and insurance industry becomes a target due to its financial resources, making it easier for RDP access sellers to find buyers and potentially sell the accesses for higher amounts.

The data above highlights North America having the highest sale rate at 31.6%. Nearly 1 in 3 of RDP access sales are from the region. The most significant contributor to this fact is the USA and maybe the correlation with Ransomware groups. The USA is the most attractive target for Ransomware groups. It is a particularly lucrative target for cybercriminals. They may find RDP access sales in North America highly profitable. The presence of valuable assets, financial resources, and critical infrastructure in the region contributes to its appeal.
2022 witnessed a staggering global ransomware volume, reaching 493 million dollars. This alarming figure underscores the financial impact of ransomware attacks, highlighting the substantial sums of money extorted from victims. In addition to the overall volume, the average cost of a successful ransomware attack is equally concerning, with estimates ranging between $570,000 to $812,360.
In a recent example, the BianLian Ransomware group has been observed utilizing RDP as an initial access vector in their cyberattacks. According to the Cybersecurity and Infrastructure Security Agency (CISA), BianLian has exploited RDP vulnerabilities to gain unauthorized access to targeted systems. By leveraging RDP, the group can bypass traditional perimeter defenses and directly infiltrate networks. Once inside, they deploy their ransomware to encrypt critical files and demand ransom payments from the victims.
Chasing the Money
We examined 637 RDP access sale posts in the following graphics out of 891 because not every post contains the information of price range. As a disclaimer, most of the posts are posted as auctions but have a blitz option to buy, as in eBay’s buy it now. We analyzed the posts based on the starting prices to be consistent. However, you should note that some of the sales may have sold for higher prices.
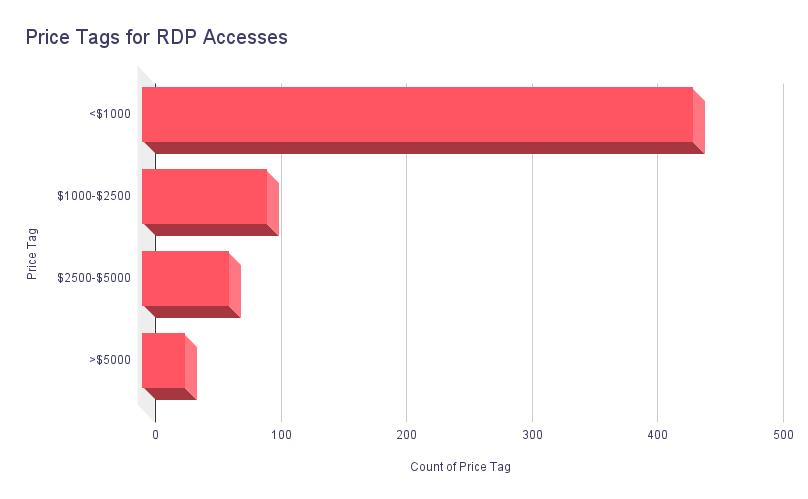
The above graphic sheds light on the price range of RDP access sale posts. Most posts, 438, fall under “less than $1000.” There are 98 posts in the “$1000-$2500 range,” followed by 68 posts in the “$2500-$5000 range.” A smaller number of posts, 33 in total, are priced at “more than $5000.”
The lower price range of “less than $1000” can be attributed to the nature of these initial access sales. Selling RDP access is a relatively quick way to generate income for threat actors. Acquiring RDP access requires less effort compared to conducting a full-scale attack. Additionally, it’s important to note that not all RDP access sellers can gain access to desirable targets, such as multi-billion dollar organizations. Therefore, the price range reflects the compromised access’s varying value and perceived potential.
This variance also affects the median and average values. While the median value for RDP access sales stays at $600, the average value surfaces at $2037.
Below is a batch sale for RDP access as low as $50.
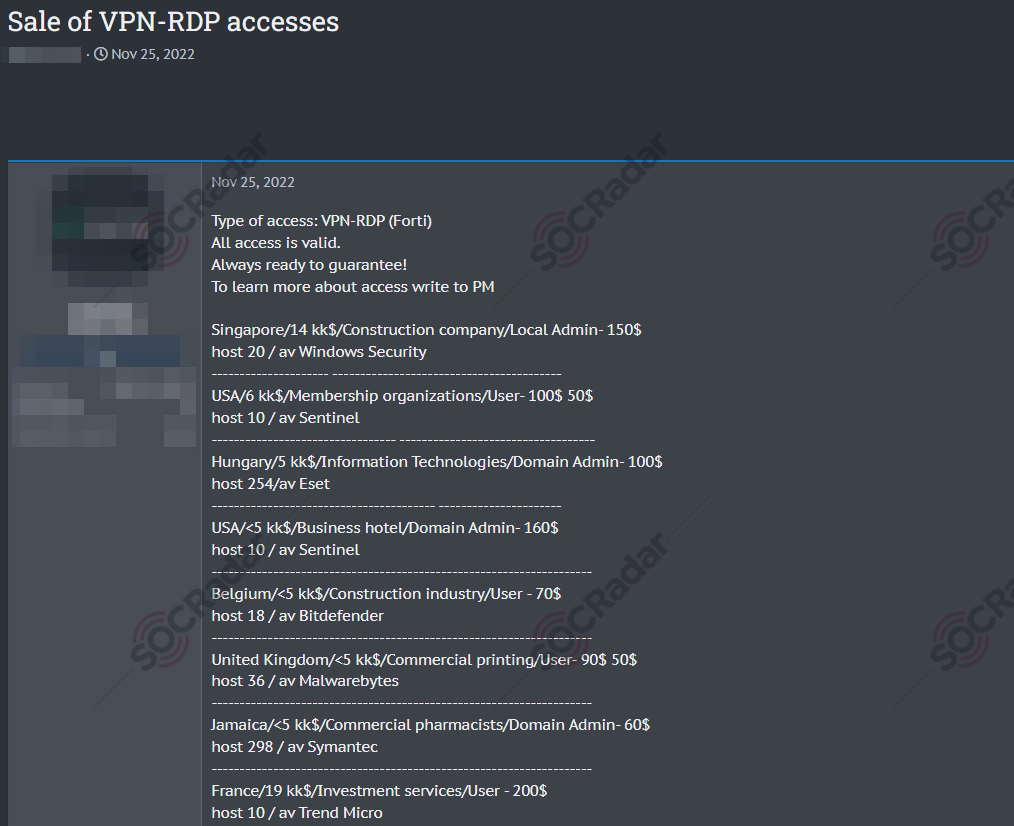
Through analyzing numerous posts on dark web forums, it becomes apparent that cybercriminals employ a specific set of criteria when describing the companies they sell access to. Corporate revenue emerges as the primary factor among these criteria, with nearly all posts mentioning it. The region and business area of the target company follow it. Additionally, some posts refer to the level of complexity as a determining factor for pricing, indicating the time and effort invested by the seller to obtain access.
It is worth noting that the emphasis on revenue as the main criterion aligns with cybercriminals’ motivations. Higher revenue often correlates with a more significant potential for financial gain, making such companies more attractive targets. However, the criteria for complexity can be more subjective, depending on the individual expertise and capabilities of the cybercriminal involved.
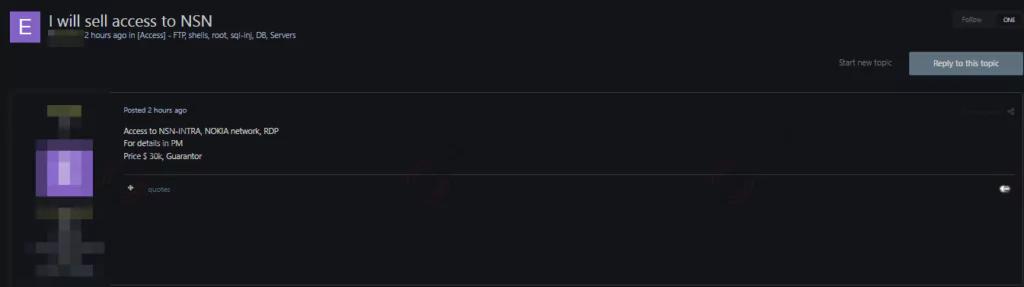
Below is an attractive sale post for a threat actor, selling for $30.000 back in late 2022.
In light of the deductions above, we can examine the graphic below.
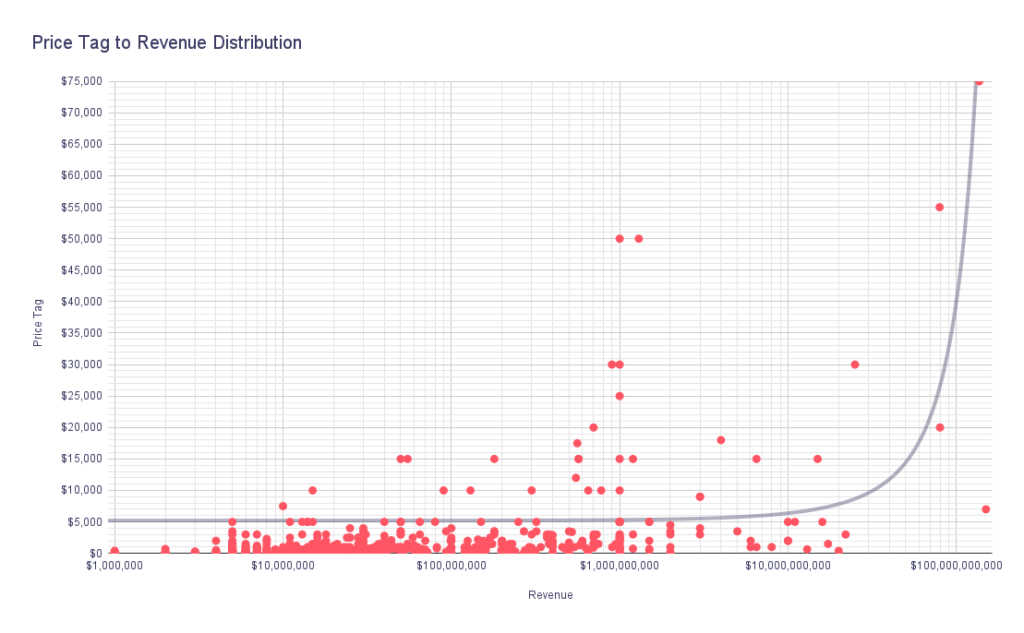
The plot indicates an exponential trend between the revenue and price tag relationship. As we move further to the right on the revenue axis, the corresponding price tags on the price tag axis tend to increase significantly.
The wide range of revenue values, ranging from $1,000,000 to $150,000,000,000, demonstrates the diversity of companies being the subject of RDP access sales. On the other hand, the price tag values ranging from $10 to $75,000 reflect the varying costs associated with the sale of RDP access.
The exponential trend observed in the plot indicates that as a company’s revenue increases, the price tag for its access tends to rise considerably. This also suggests that cybercriminals perceive higher-revenue companies as more lucrative targets, potentially leading to increased demands for access and higher prices.
Notably, this exponential relationship signifies the potential financial gains cybercriminals expect from compromising organizations with higher revenue. However, regardless of their revenue, all companies are potential targets for these threat actors.
The rise of RDP access sales on dark web forums poses a significant threat to organizations of all sizes. Attackers are capitalizing on the demand for corporate data. They are exploiting compromised remote desktops as a gateway to valuable information. To protect against these risks, it is crucial to implement robust security measures. Here are some key recommendations:
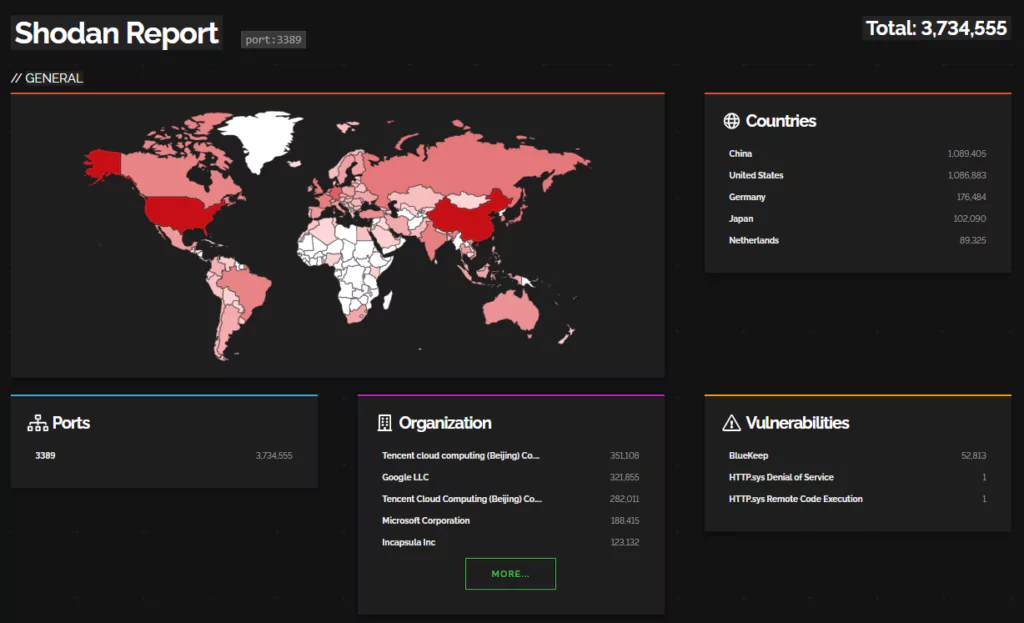
- Strictly limit RDP access and close unused RDP ports. If RDP use is necessary, consider changing RDP ports to non-standard ones to make it more difficult for attackers to breach connected computers. Audit the network for systems using RDP. If RDP is necessary, rigorously apply best practices. With a simple search on Shodan, we can see that over 3.5 million ports are open to the internet. Of those, more than 50 thousand have BlueKeep vulnerability.
-
- BlueKeep (CVE-2019-0708) is a critical vulnerability found in the RDP used by Microsoft Windows operating systems. It has a CVSSv3 score of 9.8 critical. This vulnerability allows attackers to execute remote code on a vulnerable system, providing them with unauthorized access and control. To exploit BlueKeep, an attacker sends specially crafted packets to a system with RDP enabled. These packets are designed to trigger the vulnerability and allow the attacker to execute arbitrary code remotely.
-
-
- Keep RDP clients and servers updated and patched to mitigate vulnerabilities that attackers may exploit. You can see the importance of this step in the Shodan search above. BlueKeep vulnerability was released and patched four years ago. However, vast amounts of machines are still running with vulnerable RDP versions. SOCRadar, with its External Attack Surface Management, can help an organization keep track of vulnerabilities in the environment.
-
-
-
- Ransomware groups leverage the RDP access sales regularly. Keep offline backups to mitigate the impact of potential data breaches or ransomware attacks.
- Threat actors leverage brute forcing to claim RDP access to organizations. Harden RDP against brute force attacks by strengthening credentials. Log RDP login attempts. Implement phishing-resistant multifactor authentication (MFA), enforce account lockout policies, and manage user permissions.
- One of the most critical steps is investing in a dark web monitoring solution, such as SOCRadar Threat Intelligence. It can be crucial for detecting and mitigating the risks associated with RDP access sales on dark web forums.
-
By implementing these recommendations and leveraging the capabilities of SOCRadar Threat Intelligence, organizations can enhance their security posture and protect themselves against the dangers posed by RDP access sales on dark web forums.
SOCRadar has a predictive, preventive, and proactive approach toward security. SOCRadar monitors and analyzes the dark web to provide intelligence on underground activities. With the Dark Web News module, you can track the ecosystem and receive a heads-up if an actor on our radar tries to sell an RDP access.




































