
Microsoft Products as an Attack Vector
Microsoft is one of the big five American information technology companies and one of the leading companies in the information technology sector. With a wide range of products, Microsoft holds an 85% Market Share in U.S. public sector productivity software. The Microsoft ecosystem, which reaches large customer bases also in worldwide, sees the result of this scope as having a vast attack surface.
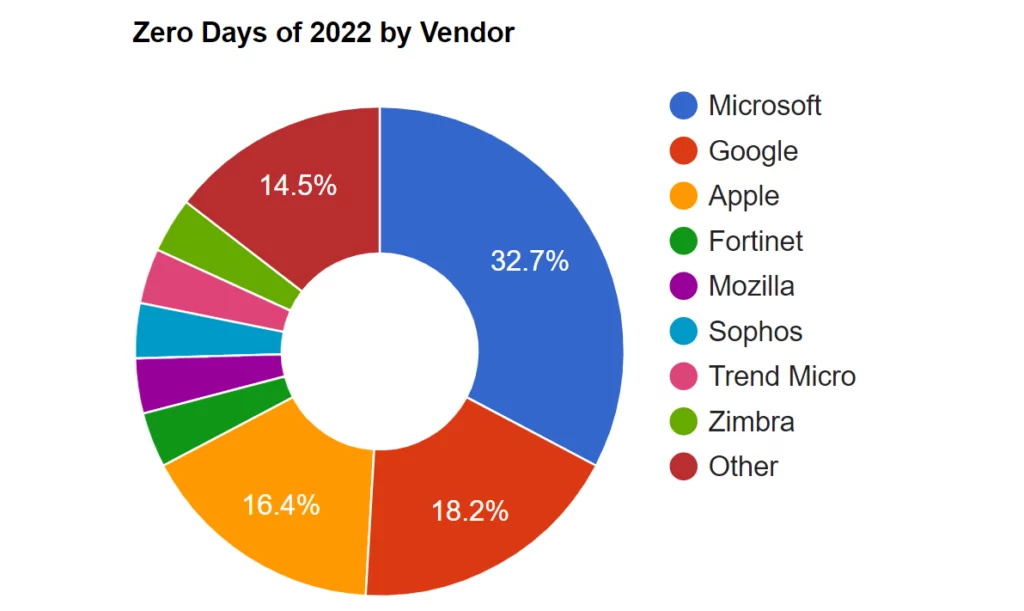
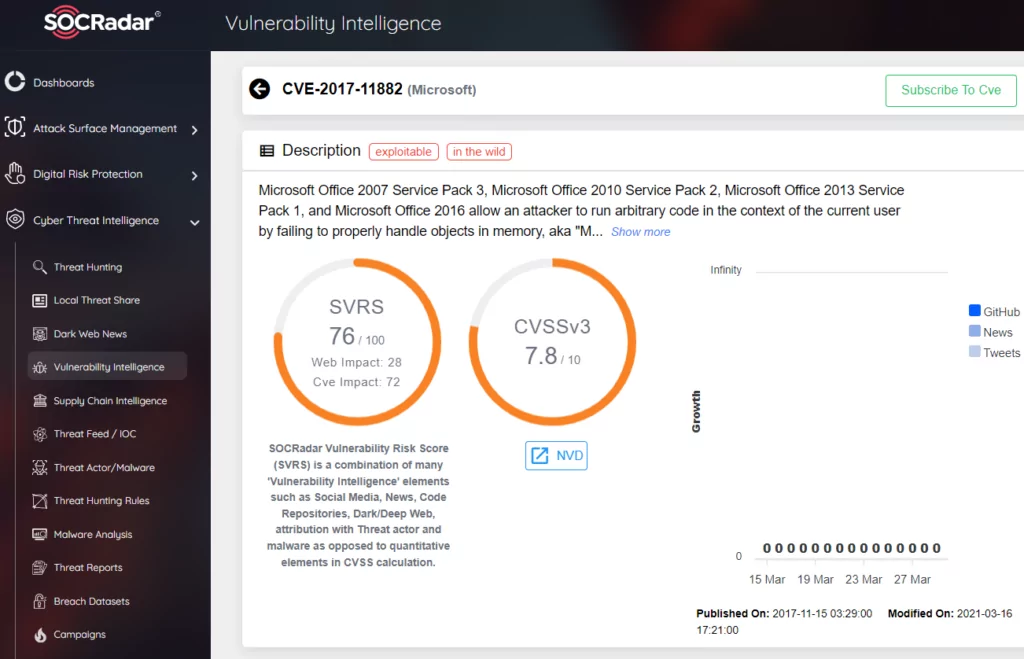
Microsoft has hosted over 300 CVEs in the last three months and over 10.000 registered vulnerabilities in NIST Database. Microsoft product vulnerabilities, among the most exploited for many years, are also on the list with CVE-2017-11882 (Microsoft Office Memory Corruption Vulnerability) in 2022. Moreover, they also cover more than a quarter of CISA’s Known Exploited Vulnerability Catalog with 259 entries.
Analysis of the Attack Surface
The almost ever-expanding Microsoft landscape finds its way into many users and organizations’ daily and operational uses. Microsoft Office Productivity Software, Teams, and cloud-supported service solutions within Microsoft 365 have permeated the daily lives of many Windows users.
Even though Microsoft’s cornerstone Windows has experienced a constant loss in market share for the last ten years, it still ranks 1st among OSes with 74% as of the beginning of 2023. This number corresponds to more than 1.5 billion devices; thus far, any vulnerability on any soft/hardware belonging to this ecosystem may have huge effects.
Microsoft 365
Formerly known as Office 365 is a cloud-based productivity suite that includes Microsoft Office, Exchange, Teams, SharePoint, and OneDrive. It is possible to see that the vast-used software included in this package creates a large attack surface.
Office programs have been the target of attackers for over 20 years as one of the extensive attack vectors. Many malicious attachments from phishing emails have used the macro feature of Office programs that enables repetitive tasks. Attackers could have to exploit the macro-enabled documents and execute malicious code over macros. While macros could be enabled by default, the feature was disabled, and Microsoft started to block Office macros in the mark of the web labeled Office files in 2022.
This late change caused many malicious attachments to be sent as Excel and Word files for years. In 2023, threat actors are predicted to send malicious attachments more as HTML, PDF, or LNK, and Emotet, one of the most dangerous trojans seen since 2014, also started to appear often again in the wild by the end of 2022, and it was seen that it was often distributed with the LNK file type.
Excel Add-ins was also used as an attack vector throughout 2022, and many malware-infected victims’ computers by disguising themselves as typical add-ins. XLL add-ins downloaded over the internet were only set to be automatically blocked as of the end of January 2023.
Another danger in Excel is the Formula Injection attack. If the input is mirrored in CSV files, threat actors may put Excel formulas that will be executed when the victim opens the file or clicks on some link inside the Excel sheet. Threat actors frequently use Microsoft Office programs as an attack vector for simple-to-implement attacks such as Formula or CSV injection.
Exchange Server vulnerabilities in 365 appeared to be exploited in 2022 as an ongoing trend in recent years and used by Ransomware groups such as Cuba and LockBit 3.0. As of 2023, over 60 thousand servers are still vulnerable to ProxyShell, one of Exchange’s vulnerabilities.
Furthermore, a Microsoft Teams vulnerability was found at Pwn2Own held in Vancouver in March 2023, and an Outlook zero-day vulnerability used by Russian hacking group APT28 since April 2022 was also patched with the March 2023 Microsoft update; hence zero-day trend in Microsoft 365 products can be predicted to continue this year as well.
Azure Cloud Services
Azure Cloud Service also appears as an attack vector and another product/service that can be a security vulnerability. In the past years, phishing forms were uploaded and sent to blob storage using Azure Blob for a phishing attack, and a Microsoft SSL certificate could be obtained in this way. There were also cases where it was used to host malware and as a C2 server. In these cases, which can be seen that cloud services may also be used with malicious intentions, can expand the attack vector definition, and reach a meaning beyond a vulnerability.
Misconfiguration in such services can also cause extensive exposure. A misconfiguration, named BlueBleed by SOCRadar and discovered in 2022, showed that over 65,000 entities were exposed to sensitive information.
Windows
With Windows 11, there have been improvements in some critical security policies. An update released in 2022, Windows 11 turns on the operating system’s core isolation memory integrity protection by default. Although the researchers noted a slight loss in performance, overall security was boosted.
Furthermore, Windows is constantly updated, and built-in security solutions such as Defender are improving daily. Still, the most significant stakeholder of the attack surface is Windows OS itself. There are already over 600 vulnerabilities related to the recently released Windows 11.
On the other hand, Windows 10 support will also end in 2025, and many systems still using Windows 10 will become more vulnerable. Microsoft is trying to close these vulnerabilities with Patch Tuesday, which they publish monthly. Even if dozens of vulnerabilities are completed every month, new critical or zero-day vulnerabilities emerge simultaneously.
Mitigation Strategies
- Keep your system up to date.
Every organization that uses products connected to the Microsoft ecosystem should follow their monthly updates and hotfixes and enforce them on their employees. Microsoft’s last security update released in March 2023 patched 80 vulnerabilities, 9 of which were critical and 2 of which were actively exploited zero days.
- Beware of malicious attachments.
Threat actors can infiltrate your system with malicious URLs or attachments in phishing emails. According to Hornet Security’s research, in 2022, about 12% of malicious files were Word, and 10% were Excel files. Although macros are disabled by default, executing such files and enabling editing can still be problematic. These files frequently shared in a workspace are usually more likely to be opened because they do not appear as executables.
- Your configurations should be set correctly.
Systems or servers that are not correctly configured, as well as not following necessary updates, may also allow them to become vulnerable. This situation, which is frequently encountered especially in cloud services, can cause many exposures, and failure to enforce some policies on your employees’ devices may cause a breach. Especially at the point of authorization and access control, security best practices should be followed strictly, and your entire working environment should be arranged accordingly.
- Logging and watching anomalies is essential.
Organizations can quickly identify potential security breaches by monitoring system logs and detecting anomalies. Anomalies can include suspicious logins, abnormal network traffic, or unusual user behavior, which may indicate unauthorized access or malicious activity. Implementing an effective logging and monitoring solution can provide organizations with real-time insights into their system’s security posture and enable them to respond proactively to potential threats. Maintaining an accurate and up-to-date log of all activities on Microsoft products is critical to facilitate incident response and forensic investigation in the event of a security breach.

As the year 2023 has started, the Microsoft system, which has dozens of critical vulnerabilities, continues to grow in the number of devices, even if its market share shrinks. This ever-increasing ecosystem, with many more products and services we have not mentioned in this article, such as GitHub, Visual Studio, Skype, and Xbox, will remain on the agenda as a vast attack surface for years to come.
Especially in sectors such as education, healthcare, and transportation, some updates on IoT devices can take a long time and remain open to exploitation for a long time. In the coming years, millions of devices will remain in an old operating system when Windows 10 comes to the end of its life cycle. Even if the customers of this ecosystem, where new zero days are constantly discovered, get the necessary mitigations, they cannot reach sufficient security levels with only a reactive defense approach.
For this reason, organizations should develop a proactive approach using CTI solutions and know emerging techniques. They should also have eyes on platforms that hackers communicate on, such as the dark web or Telegram. In this way, you can be aware of a credential or initial access sale belonging to your organization and follow threat actors’ current TTPs and IoCs.
Threat actors look for a breach point by mapping vulnerabilities where you have insufficient insight. Thus, with SOCRadar Attack Surface Management, you can control the Operating Systems and versions of your assets and create intelligence beforehand.




































