
Lessons Learned from Education Industry Attacks in 2022
By SOCRadar Research
The education industry covers a diverse range of organizations, including K-12 education, higher education, private and public education, science research institutes, and tutoring ranging from exam preparation to hobby courses. Furthermore, educational technologies are integrally linked to other industries due to numerous related services, such as educational technologies and educational publishing. The users include students, parents, teachers, administrators, and consultants.
The educational system is responsible for many personal and confidential data. Personal data that can be gathered from various sources, such as PII (personally identifiable information), contact information, birth certificates, social security numbers, bank information, intellectual property, and research findings, are combined in the education system.
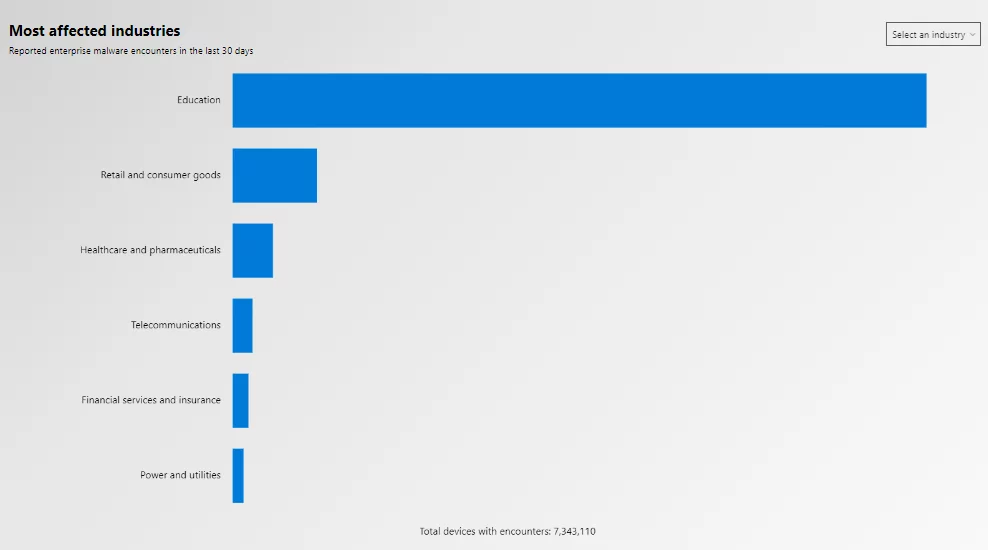
This mix of sensitive data makes the field of education particularly interesting to threat actors. Recently, many universities and school districts have been targeted by cyber-attacks. Ransomware attacks against universities increased by 100% between 2019 and 2020. According to the Microsoft Global Threat tool, the education industry has been the most affected by enterprise malware reported in the last 30 days.
Read our Education Industry Threat Landscape Report to get more insights.
Why Have Cyberattacks Against the Education Industry Increased?
Despite containing sensitive data and hosting a large number of users, the education industry has relatively insufficient cybersecurity measures. Thus, the threat actors’ attention and the cyberattacks on the education industry rise. Cyberattacks on the education industry result in data breaches, operational interruption, reputational damage, and financial losses. Some primary causes of the rise in cyberattacks on the education industry are as follows:
- As participants in educational institutions, students generally prioritize comfort over security, using their own devices, studying in shared spaces, and using public Wi-Fi.
- There is varying cybersecurity awareness among users of all ages.
- Users’ sensitive data and valuable intellectual property obtained from research programs in the higher education system are also valuable for threat actors.
- Higher education institutions operate on more accessible networks due to the inherent information-sharing culture. The structure of networks is wide, allowing users to connect remotely. The open IT infrastructure policy also provides network access for external visiting students, teachers, and researchers, making it difficult to determine who is on the network at any time.
- Since educational institutions must operate on a small budget, outdated technologies with security vulnerabilities are used to provide cybersecurity infrastructure.
- Education shifted to online platforms during the Covid-19 pandemic, and threat actors targeted these platforms as a new entry point into educational systems. Although face-to-face education has returned after the pandemic, online platforms and personal device usage continues.
Cyberattacks Statistics on the Education Industry in 2022
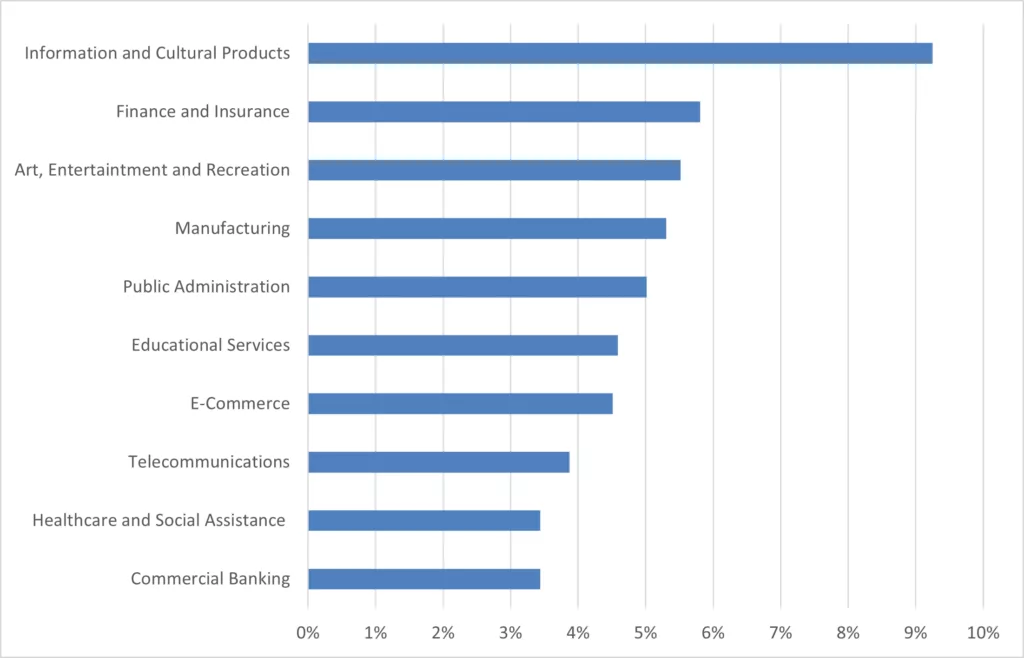
In 2022, the SOCRadar XTI Dark Web News module reported 736 education industry-related posts. The number of education industry-related postings shared on underground forums increased by 61% in 2022 compared to 2021. The most active threat actors were ‘Jitter,’ ‘Kelvinsecurity,‘ and ‘Flowercower.’ According to the distribution of 2022 dark web posts on the SOCRadar XTI platform by industries, the education services rank sixth with a rate of 4.59%.
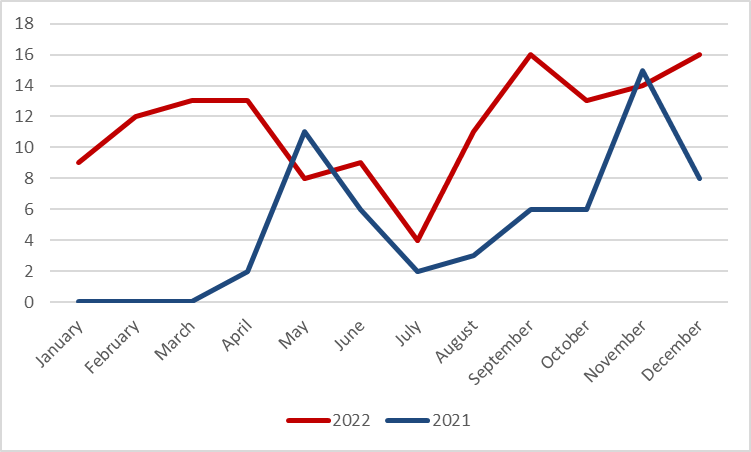
The number of ransomware attacks on the education industry detected by SOCRadar dark web analysts increased by 234%in 2022 compared to 2021. The distribution of ransomware attacks in the education industry in 2021 and 2022 are as follows.
The ransomware groups that targeted education systems are Vice Society, LockBit (LockBit 2.0 version), and Hive. US authorities seized the servers of the Hive ransomware group on January 26, 2023. For more about the Hive ransomware group, click here.

Lessons Learned from Education Industry Attacks in 2022
Lesson 1: Paying ransom is not a solution
Lincoln College, one of the historical colleges of the U.S., was the target of a ransomware attack on December 19, 2021. All registration, academic, finance, admissions, and fundraising systems were impacted and shut down. The school officials agreed to pay the $100,000 ransom after 1.5 months of negotiating with the ransomware group. The first decryption key given by the threat actors did not work after accepting the ransom; they could recover some of the data with the second decryption key sent later.
They could fully recover the systems in March 2022, but the school, which had difficulty maintaining operations after Covid-19, could not overcome the challenges caused by the ransomware attack. On May 13, 2022, the school officially announced the end of its 157-year existence as an educational institute.
Lesson Learned: There is no guarantee that the victim will receive the decryption key or that the decryption key will restore all data once the ransom has been paid. Furthermore, the time required for discussions and subsequent recovery can have an irreversible impact on the organization’s operations. As a result, backups must be optimized to allow faster recovery of the most critical data and services in case of a ransomware attack. It is necessary to reestablish access to systems and data rapidly.
Lesson 2: Rapid digital transformation leads to wider attack surface
Digitalization has recently increased in the education industry, as in many other industries. The Covid-19 pandemic, in particular, forced the education system to shift to remote education rapidly. The digitalization of the system with solutions such as online courses, online meeting tools, smart classrooms with smart whiteboards, and student tracking tools has expanded the attack surfaces of educational institutions. The uncontrolled expanding attack surface exposed new weak points for threat actors.
Lesson learned: Educational institutions’ digitalization without adequate resources and security posture, using various online platforms and supporting tools, should take advantage of advanced threat intelligence tools to monitor their expanding attack surface.
Lesson 3: Supply chain security is critical for the education industry
The New York City Department of Education (NYDOE) reported in March 2022 that threat actors got unauthorized access to the personal information of 820,000 current and past New York City Public School System students. The vulnerability was discovered in the Skedula and PupilPath software, which tracks grades and attendance. A California-based Illuminate Education company owns both platforms. The breach occurred on January 2022, but the third-party software vendor informed the NYDOE in March 2022.
Lesson Learned: In the case of receiving support services from third parties and subcontractors, educational institutions need to ensure that their suppliers have robust cybersecurity protocols for the sensitive data in their systems.
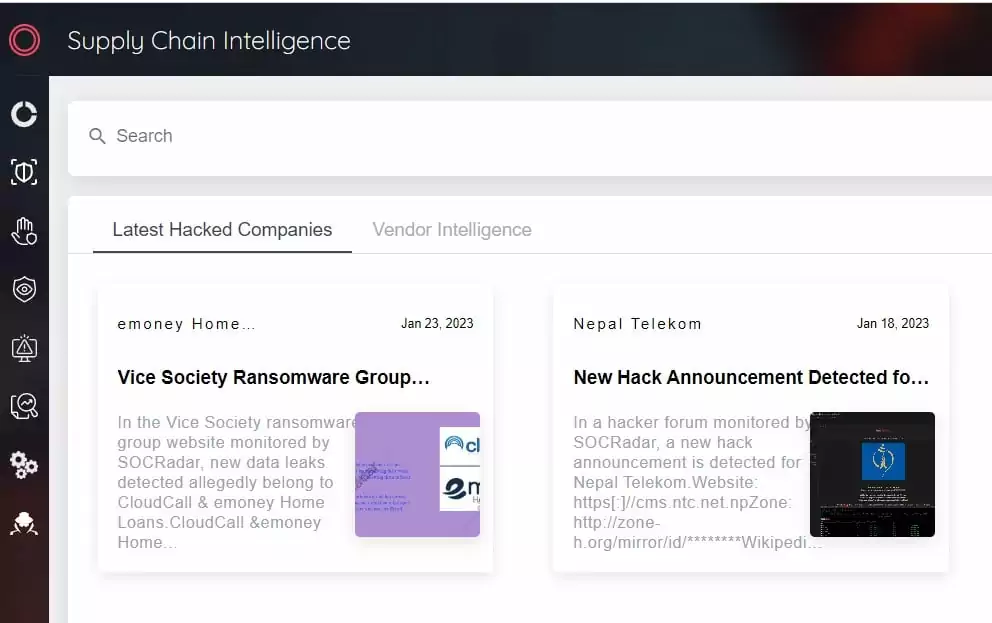
Lesson 4: Extended Threat Intelligence should be implemented
On September 6, 2022, LAUSD, the second-largest school system in the US, announced that it had been the target of a ransomware attack. Research revealed that the attackers, the Vice Society ransomware group, were active on LAUSD’s networks from July 31, 2022, to September 3, 2022.
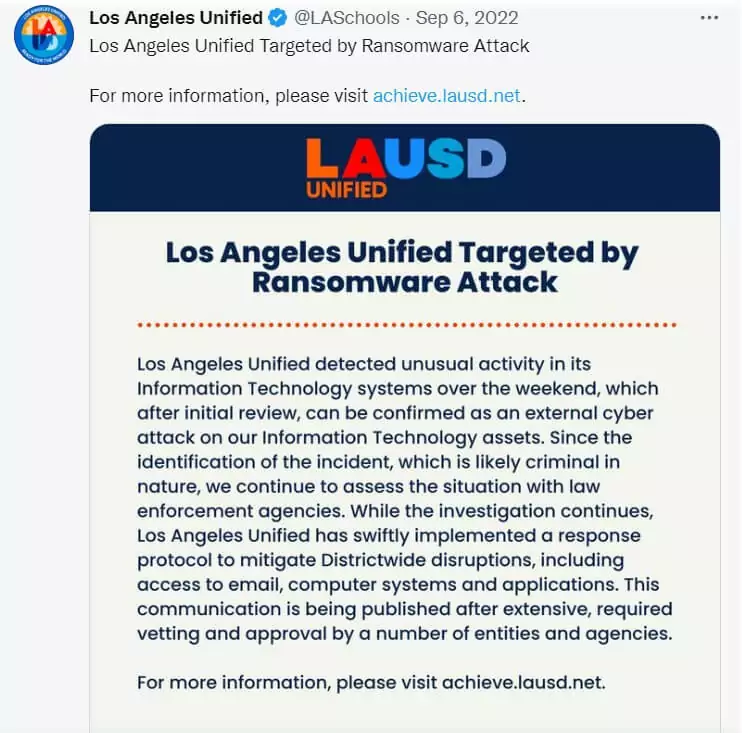
Meanwhile, the authorities took action. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint cybersecurity advisory about the Vice Society Ransomware Group(AA22-249A) on September 6, 2022. The advisory stated that Vice Society actors disproportionately target the education sector with ransomware attacks.
On September 30, the Vice Society announced they would publish LAUSD data on the leak site in a few days.

The group published sensitive data of LAUSD on October 2, 2022, with their response to the CISA.

How Vice Society gained access to the LAUSD networks is unknown. Still, it is believed that the group exploited leaked internal login credentials found on the dark web. It has been observed in the SOCRadar XTI platform, Threat Hunting Module, that many breach data sets of the ‘lausd.net’ domain were published on the dark web before the attack.
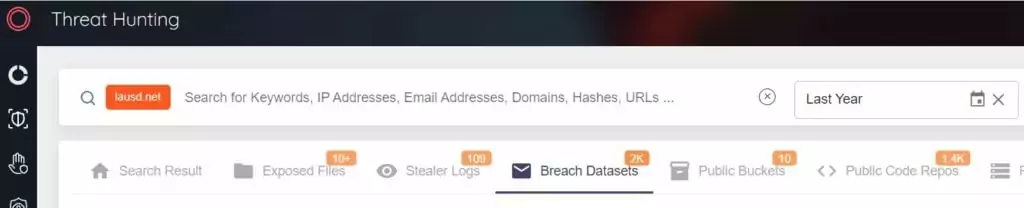
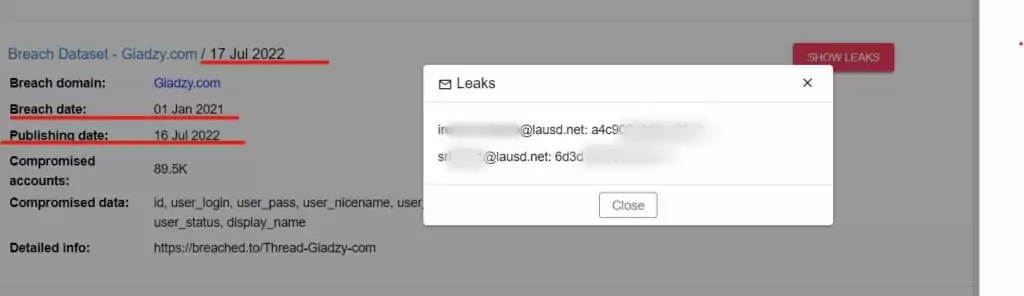
Lesson Learned: An extended threat intelligence solution that monitors the dark web, gathers intelligence, and alerts customers when critical data is released to the dark web is crucial. Thus, the possibility of using compromised accounts in continued attacks is reduced.
Conclusion
The education system has wide networks that provide easy information sharing and remote access for users, including students, instructors, parents, office staff, and administrators. Educational institutions are responsible for protecting a wide range of sensitive data, from birth records to scientific research results. The protection must be maintained despite limited funds and a lack of cybersecurity awareness among its users, many of whom are students.
At this point, educational institutions must identify security vulnerabilities and evaluate the risks and potential threats to develop cybersecurity strategies. Extended cyber threat intelligence systems, where all digital assets are monitored 24/7 and intelligence is gathered from the dark and surface webs, will help reduce the weaknesses of the education sector’s cybersecurity infrastructure.



































