
Comparing Benefits from Different Security Monitoring Services
By 2021, it is estimated that the total cost of cybercrime was 6 trillion USD making threat actors the third-largest economy after the U.S. and China. McAfee states cybercrimes accounted for 14% of the entire internet economy in 2016. This data shows that makes cyber security monitoring is a critical issue.
The increasing effects of digitalization and new technologies such as IoT have increased internet usage in our daily lives. Digitalization processes accelerated significantly after the “new normal” entered our lives with Covid-19.
Digitalization Increases the Importance of Security Monitoring
From SMEs to Forbes 500 giants, many companies also digitize their operations. On the other hand, this process has enlarged the cybercrime market. Considering monetization is their primary motivation, threat actors have increasingly been taking advantage of these new “opportunities” every day.
According to ENISA (European Union Agency for Cybersecurity) Threat Landscape Report (2021), numerous methods from social engineering to complex malicious software applications have been increased, and targets from small to mid-sized businesses.
How can one protect from threat actors regarding all those threat methodologies and the constant climb in cybercrime? The answer is establishing “proactive security systems,” which allows security teams to obtain the necessary information via cyber threat intelligence and act before the attack. The initial application of proactive measurements is called security monitoring.
What is Security Monitoring?
In basic, security monitorings are a regular intelligence gathering and analysis method for detecting malicious software or suspicious activities in the system. To succeed, this monitoring has to be done both internally and externally.
Internal monitoring can be described as monitoring the “inside” of the system, where the system refers to the whole network of computers in the one’s corporation. The bridges and doors to the outer world must be monitored to ensure security on the inside first. Monitoring intrusions on the network and firewall prevents possible threats and responds before the “threat” sets up and damages the system. Also, monitoring and storing the user logs will help to ensure security and helps to establish a “zero trust” system where security teams can monitor possible threats due to human error.
SOCRadar’s AttackMapper provides SOC teams complete visibility into their organization’s internet-facing digital assets by monitoring its digital footprint. With SOCRadar’s AttackMappper, you will be able to monitor your attack surface and identify hacker-exposed vulnerability risks constantly.
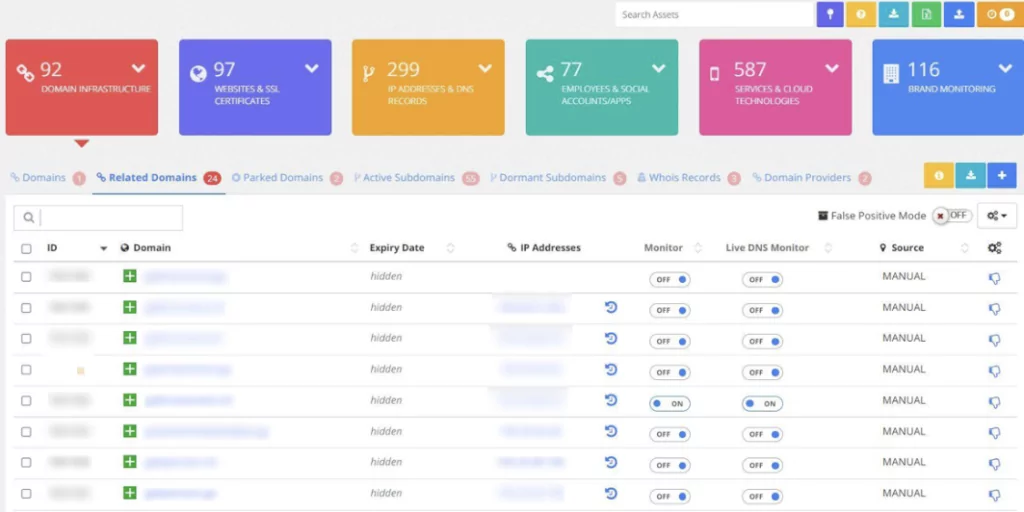
On the other hand, external monitoring aims to yield actionable intelligence to facilitate SOC teams’ and security professionals’ future actions to stop cyber attacks. Also, through external monitoring, you will be able to identify sensitive data leaks rapidly.
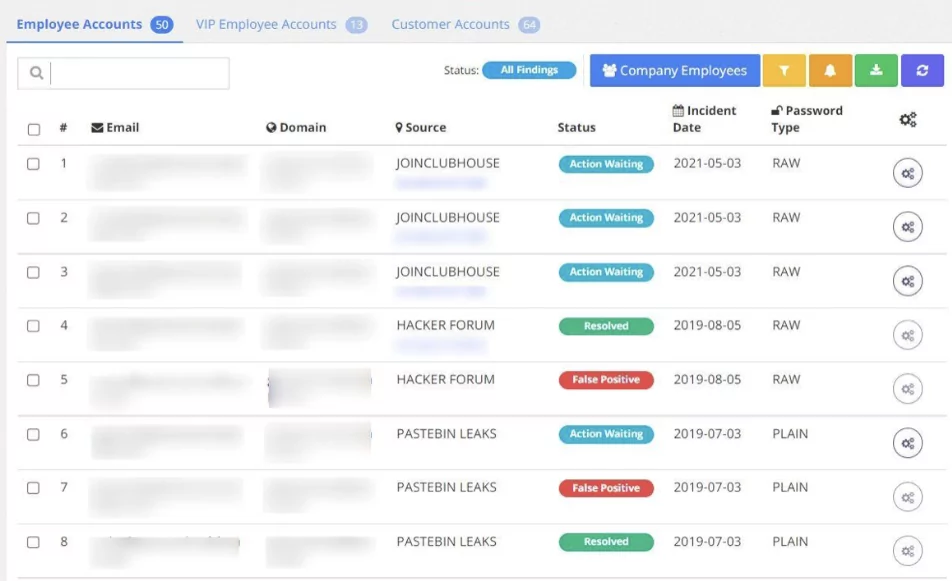
SOCRadar’s RiskPrime constantly monitors the external web, identifies external cyber risks, and notifies your organization. In case of sensitive data leaks (such as compromised credentials, credit card leaks, source code leaks.)
Advantages of Security Monitoring
By holding all the tricks above up in their sleeves, SOC teams can,
- Detect suspicious activities inside the corporation’s network and respond rapidly.
- Conveniently observe the network and firewall infiltrations.
- Discover possible data leaks earlier.
- Detect future cyberattacks before the attack occurs.
- Enable corporations to understand the landscape and arrange cybersecurity budgets accordingly.
Security monitoring comes in handy regarding all these tools, especially when building and maintaining an effective cybersecurity solution to stop threat actors from damaging your organization. To effectively use security monitoring to its full potential, we can divide it into three parts.
The Three Parts of Security Monitoring
1. Attack Surface Management
This step can be grouped under internal security monitoring. To start with, the “attack surface” has to be defined. Attack surface is the all external-facing digital assets a corporation has. The whole IT presence on the web can be categorized under the attack surface. Major elements can be active and inactive websites, servers, IPs and domains, and any possible ports or wifi networks (also the IoT devices) that are physically around the corporation.
Especially forgotten IT infrastructures such as old development or marketing websites can potentially be exploited and counted as vulnerable attack surfaces.
Reducing these surfaces as much as possible might be a solution for some of the examples above. Yet, “Attack Surface Management” is much more complex than that. ASM aims to constantly discover, record, classify and monitor all external-facing assets of a corporation. By improving visibility into the attack surface and bringing additional context to the external-facing digital assets,
Attack Surface Management can improve the decision-making capabilities of SOC teams and can highlight the weak links in the system which can be fortified. Thanks to these capabilities, SOC teams can respond to incidents faster.
2. Dark Web Monitoring
The dark web refers to websites not indexed in search engines and only accessible with some specialized web browsers. There are forums where underground groups could publish or sell leaked data on the dark web. Since the dark web cannot be reached through ordinary ways, it is puzzling to detect if one is a threat or not. SOCRadar provides you with a dark web monitoring service to deal with this problem.
Dark web monitoring tracks hacker forums, underground black markets, and ransomware leak sites to detect sensitive information about your organization and notify you to prevent cyber attacks and potential breaches. SOCRadar utilizes AI-based monitoring tools to monitor the dark web. Dark web monitoring can be considered similar to a search engine on the dark web. These tools assist in finding leaked or stolen data, such as passwords and credentials, that are to be sold on the dark web.
Dark web monitoring continuously searches the dark web to find leaked sensitive data by only providing the company name and the domain name. This typical search is efficient in cost and time since only specific information is searched on the dark web. When a leakage or a threat is discovered, a predefined alert notifies the company members related to the threat. Apart from the fact that possible threats are notified to the customer, this service also gives us insight into understanding attackers’ methods.
Some types of risks that an organization might be involved in are third-party breaches, P2P leaks, and general potential threats on the dark web.
Organizations are generally interested in this security monitoring service of dark web monitoring in order not only to learn if there is a threat but also to have a precaution since this service gives an immediate response to the organization.
3. Surface Web Monitoring
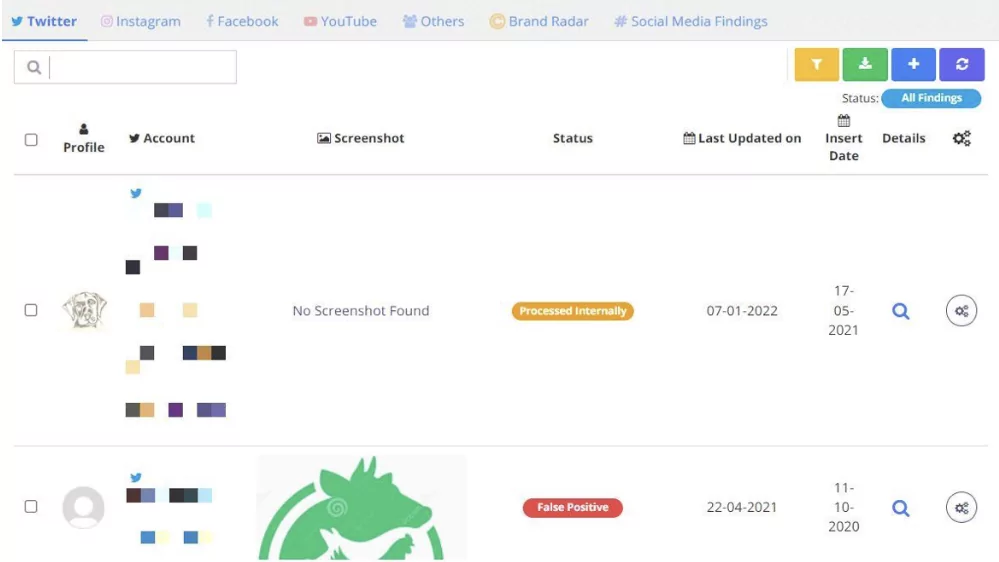
The surface web is the area of the internet that we surf in daily life. Social media and communication platforms, such as Telegram, Discord, and Twitter, could be an example of the surface web.
As mentioned in the above subsection, dark web monitoring, probable threats, and data leakages are generally published or sold through the dark web; however, dark web forums are not the only place. Ransomware gangs sometimes also communicate through the surface web and could leak the data in surface-web forums. Some well-known ransomware groups have Telegram and Discord channels to communicate with their customers. That is where surface web monitoring comes into play.
With surface web monitoring, leaked information through Telegram and Discord groups is detected and notified to customers, which allows the customer to be informed about any leakage occurring on the surface web so that the organization takes precautions. More than that, it is possible to detect any imitating websites or apps with this service. The customer organization gets informed about whether somebody is inappropriately using their name or not. SOCRadar can provide all these features with surface web monitoring.
References
- https://www.hpe.com/emea_europe/en/what-is/security-monitoring.html
- https://www.hpe.com/emea_europe/en/what-is/security-monitoring.html
- https://cipher.com/blog/5-reasons-why-you-need-24×7-cyber-security-monitoring/
- https://www.mcafee.com/enterprise/en-us/assets/executive-summaries/es-economic-impact-cybercrime.pdf
- https://www.enisa.europa.eu/publications/enisa-threat-landscape-2021/@@download/fullReport
- https://www.pwc.com/us/en/services/consulting/cybersecurity-risk-regulatory/library/2021-digital-trust-insights/cyber-threat-landscape.html
- https://theprint.in/tech/digital-economy-firms-faced-270-cyberattacks-on-average-in-2021-each-success-cost-3-6-mn-wef/806555/
- https://www.techtarget.com/searchsecurity/tip/What-is-attack-surface-management-and-why-is-it-necessary
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































