
Telegram: A New Place for Hackers
One of the most commonly used messaging apps, Telegram, has become more and more popular ever since the privacy policy scandal of WhatsApp in January 2021. WhatsApp announced that they have been sharing their customers’ sensitive data with Facebook for a couple of years, which created turmoil in WhatsApp users. People have been searching for an alternative for WhatsApp, and they have decided to switch to other messaging apps such as Telegram.
Telegram’s Increasing Popularity
Even though Telegram only encrypts messages in communication between your device and its servers by default (you can manually enable end-to-end encryption), Telegram is known for its safety and encryption policies. App has around 500 million active users, and more than 100 million people have downloaded the app in 2021.
Telegram’s popularity also attracted hackers’ attention, and it became the main hub for threat actors. The fact that Telegram is a legit messaging app used by millions gave hackers the chance to conceal themselves and achieve their evil deeds.
Utilizing Telegram to Perform Malicious Activities
Hackers have been using Telegram to carry out various malicious tasks. Below, you can see the most common ways threat actors utilize the app.
Sharing Stolen Databases
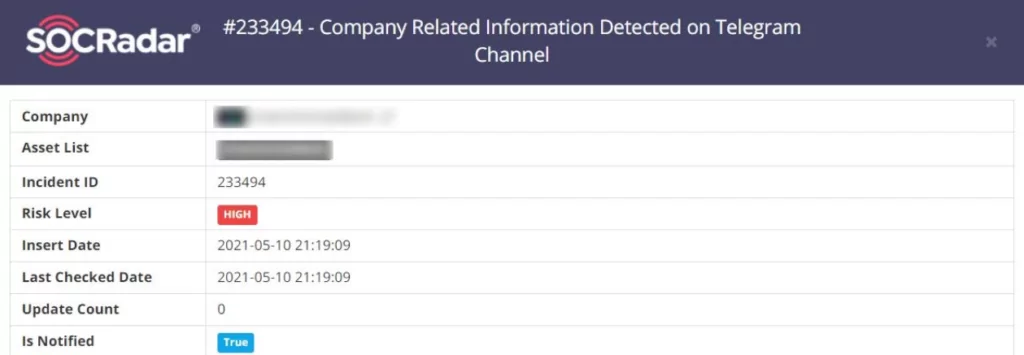
Typically, threat actors tend to sell data dumps in hacker forums inside the Dark Web. They put up the databases to auction and try to make as much money as possible by selling the dump to the highest bidder. After selling the data dump or failing to do so, they sometimes opt to share the information openly and post the leaks on hacker forums, Pastebin, and Telegram. SOCRadar tracks and monitors Telegram groups hackers mainly use and detects data leaks your organization suffers. Below, you can see a screenshot of a Telegram data leak incident detected by SOCRadar.
Communicating with Other Hackers
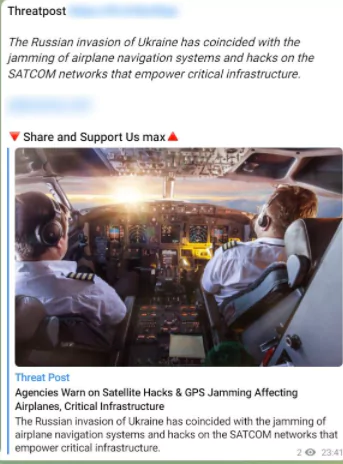
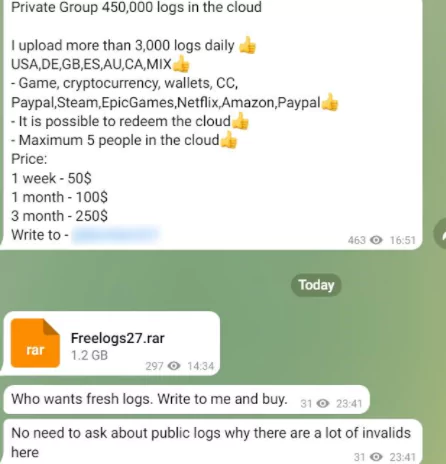
Threat actors have also been using the app to chat with other people. However, we see that hacker channels go beyond the intended usages by performing malicious activities. Hackers discuss tactics, techniques, and procedures (TTPs) to perform cyber attacks, new emerging vulnerabilities and zero-days, important cybersecurity events and news, and many other subjects to be up-to-date in the cybercrime sector. They also utilize Telegram to communicate with potential buyers of database sales posted on hacker forums on the dark web. We see that the app has been a primary communication platform for threat actors. Below, you can see two example posts in hacker Telegram channels, one a cybersecurity news post and the other one advertising a private data leak channel.
Telegram Bots: Automating Malicious Activities
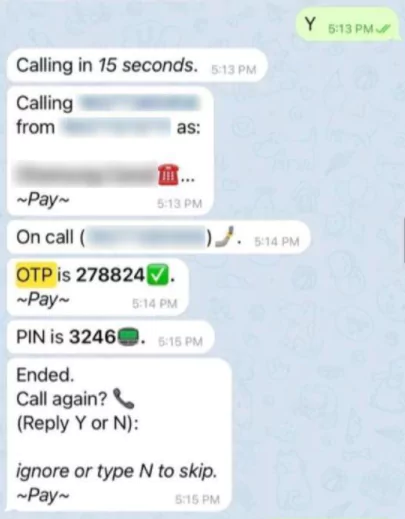
Telegram bots offer hackers a broad range of possibilities in automating malicious tasks. For example, we have seen that with the help of Artificial Intelligence, some bots perform sophisticated social engineering attacks by impersonating banks and companies to steal and capture OTP and SMS codes from their victims. In particular, OTP-Bot, a well-known malicious Telegram bot, claims %98 success rate on their OTP capturing attacks, a near-perfect success rate. Below, you can see a sample screenshot showing successful OTP-Bot attacks.
We also see that Telegram is being used as an infection vector through automatized bots to deploy malware. Some of these malware grants threat actors access to the victim system through the Command and Control (C2) server.
Faulty Feature: “People Nearby”
Another feature hackers exploit in Telegram is called “People Nearby.” This feature lets users see the precise locations of nearby people who have turned this feature on (the feature is off by default). However, this feature has a security flaw since threat actors can abuse it by spoofing their geolocation and accessing the precise locations of innocent people. Every bit of information is significant in the cybercrime sector, so this security flaw can give threat actors the upper hand in achieving their malicious intentions.
When addressed with this security flaw, Telegram developers chose to turn a blind eye to this matter, but the solution is simple. SOCRadar CTIA team suggests users turn this feature off to protect their privacy against hackers.
Find Out What’s Happening In Telegram Hacker Channels
With the ThreatShare module in the Cyber Threat Intelligence suite offered by SOCRadar as part of its Extended Threat Intelligence approach, you can regularly monitor the Telegram channels of threat actors.
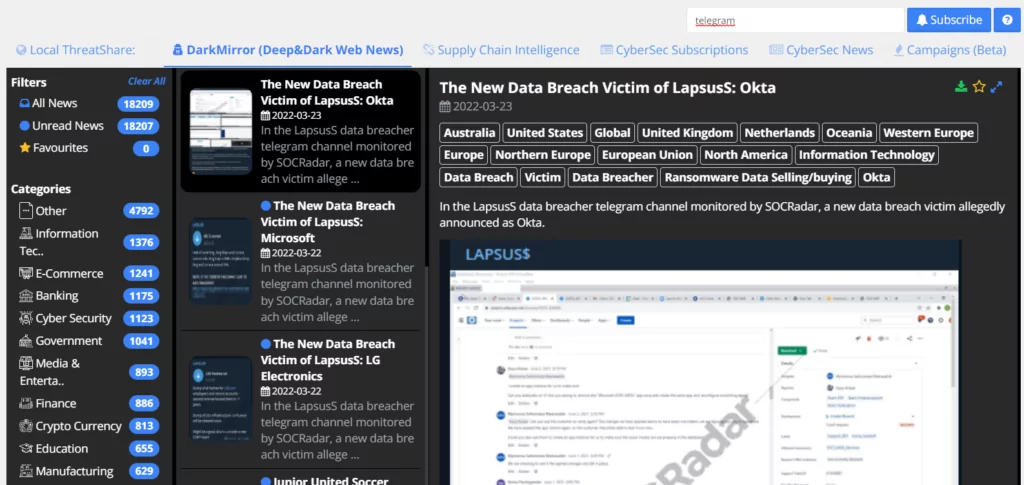
Threat Share’s CyberSec News module delivers the most relevant news about products and technologies automatically discovered in your digital assets. On the other hand, DarkMirror shares important agendas in deep and dark web forums, social media, and communication channels such as Telegram and ICQ with screenshots and texts.
Find whether your data is exposed to threat actors and minimize the risks in your digital assets. SOCRadar regularly scans the internet for new Telegram groups to find leaked data about your company. Furthermore, it alerts you if there is any information concerning your organization.




































