
Growing Cybercrime Outsourcing Model: Initial Access Brokers
By SOCRadar Research
The initial access market has shown a dramatic increase in 2022 compared to the previous year. While SOCRadar observed 2309 sales advertisements in 2021, the number of ads in 2022 was 3168, an increase of 37%. On the other hand, the average price of initial access sales followed an inverse rate, falling from around $5000 to the $2000s. The increase in the number of advertisements and the ease of stealing access led to decreased prices and increased further cyberattacks using these accesses.
Most initial access sales involve VPN or RDP credentials and are made through dark web forums and marketplaces. Researchers observed the usage of stealers to obtain these accesses as a widespread method in 2022. Another popular method was the exploitation of vulnerabilities in devices such as firewalls in the outer layers of networks. In 2022, many remote authentication vulnerabilities came to the fore and were exploited by threat actors. Initial access brokers are hard to track, and it is estimated that most trading is done in private groups, but if they are shared publicly, it’s usually on the dark web. Many dark web markets have added credentials for initial access or direct access to their catalogs, and even credential markets have emerged.
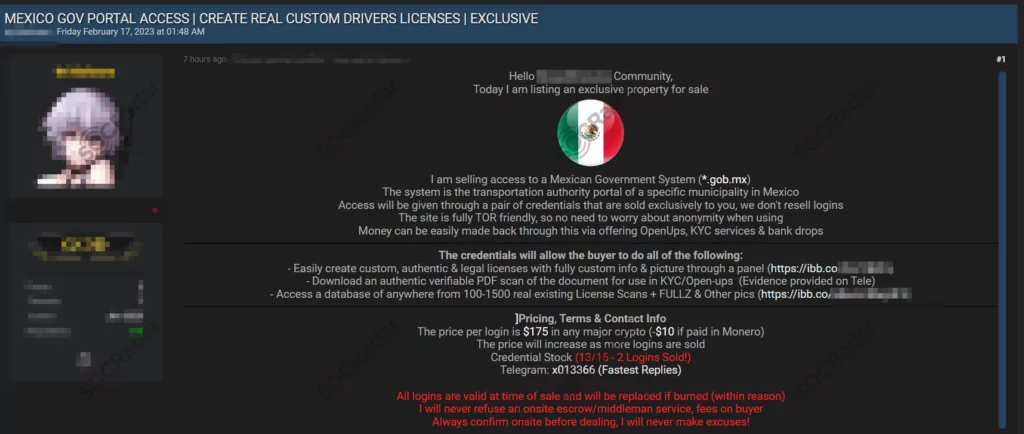
What are the Credential Markets?
Credential markets should actually be treated as different things from to initial access market, but they have a close relationship as initial access brokers use stolen credentials. Although there are particular markets to sell credentials on the dark web, threat actors can sell most of them on hacker forums or general dark web marketplaces. Still, even though initial access brokers acquire resources from these, we should also consider that they have affiliates for whom they have especially received credentials.
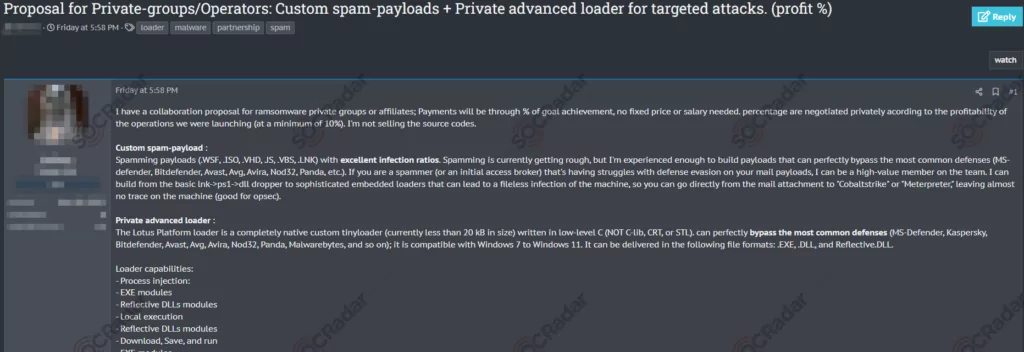
Researchers have observed tens of millions of credentials sold on the dark web. Many may also be repackaged old credentials. If these credentials are at the VIP level, they can be sold individually or in much larger datasets.
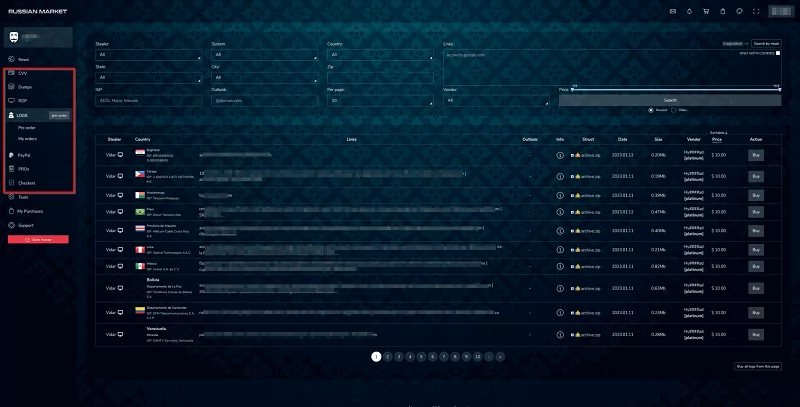
As of the beginning of 2023, the main markets that pose a cyber threat are as follows:
- Russian Market
- Genesis Market
- 2easy
How Initial Access Brokers Work?
Ransomware groups are one of the primary affiliates of initial access brokers. Google researchers define them as Locksmiths of the Cybersecurity World, which can be seen as the precursor forces of many ransomware attacks. In fact, although Initial Access Brokers have been in the cybercrime world for a long time, they were not in an uptrend until the RaaS concept emerged.
In a blog published in 2022, Google revealed that an initial access broker group was linked to Conti. It has also been seen that large ransomware groups work with outside partners, even if their capabilities are comprehensive. The broker group in question, Exotic Lily, was active enough to send more than 5000 phishing emails a day and target as many as 650 organizations. The way the threat group worked, on the other hand, followed a specific pattern.
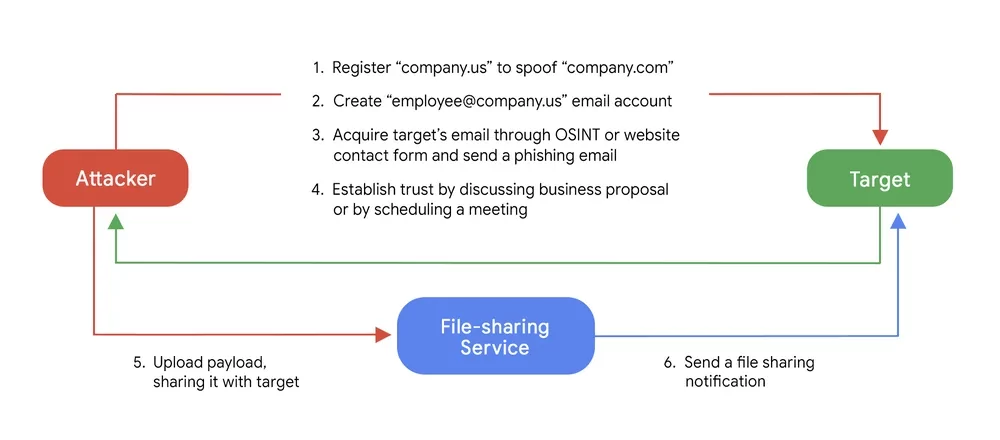
Not only ransomware but every breach also starts with the first steps of the attack life cycle: reconnaissance and initial access steps. Social engineering attacks are carried out by using the personal information of employees. Suppose the credentials of the employees who are victims of social engineering are stolen. In that case, threat actors can sell them to brokers for initial access, and the attack process could continue.
How to Mitigate the Threat?
Even though traditional security products are obliged to protect us against such dangers, as we saw in 2022, the vulnerabilities of such products may, unfortunately, serve the opposite of their purpose by providing access to threat actors. In this case, organizations should raise their cybersecurity posture by increasing awareness and adopting a proactive security approach rather than relying only on traditional security products.
Organizations could train their employees and prepare them for social engineering attacks, but human-induced errors will always occur. When threat actors exploit a human-related vulnerability, some information can be captured by the attackers and used in a cyber attack operation against the organization. Security personnel should detect the attackers’ movements or the credentials on sale using the dark web modules of CTI products such as SOCRadar Digital Risk Protection to prevent such attacks.

Initial Access Market Expected to Grow
One of the most significant incidents in 2022, the Medibank breach, took place using access sold on Telegram channels. We should consider that the locksmiths of this world will increase both their activities and profitability in these times when many activities in the cybercrime world are trending upward. Especially since ransomware groups started working on the RaaS operating model, many threat actors using this service have been able to purchase various accesses and execute an almost automated attack scheme.
In addition to the dark web, much access is sold in Telegram channels, and many institutions can become open targets despite multi-layered defense systems. The usage of such services by even a relatively less capable threat actor triggers many cyberattacks. Even if organizations think that security products will provide an adequate defense, we observed that many access advertisements were obtained through vulnerabilities on these products in the last year, and 2023 seems to follow a similar trend. For this reason, it will be necessary for organizations to increase their CTI capabilities and be aware of the activities on the dark web throughout 2023.



































