
Critical Jenkins CLI File Read Vulnerability Could Lead to RCE Attacks (CVE-2024-23897)
[Update] August 20, 2024: “Critical Jenkins Vulnerability Added to CISA’s Known Exploited Vulnerabilities Catalog”
[Update] January 29, 2024: Read under “PoC Exploits Are Available for the Jenkins Vulnerability, CVE-2024-23897”
Jenkins, a Java-based open-source automation platform with an extensive plugin ecosystem and continuous integration capabilities, has recently disclosed a series of vulnerabilities affecting its deliverables. Among them, a critical vulnerability stands out, with the risk of leading to Remote Code Execution (RCE).
With its widespread adoption by developers and its integral role in DevOps practices, Jenkins has over 300,000 installations globally, solidifying its position as a leader in the CI/CD space. In this blog post, we will provide an outline of the critical issue affecting Jenkins.
Details of the Jenkins RCE Vulnerability, CVE-2024-23897
Tracked under CVE-2024-23897 with a CVSS score of 9.8, the vulnerability in Jenkins stems from an arbitrary file read issue specifically impacting its built-in Command Line Interface (CLI).
The CLI, employed to access Jenkins from script or shell environments, uses the args4j library to parse commands. A specific parser feature, ‘expandAtFiles,’ replaces @ character followed by a file path in an argument with the file’s contents.
The said parser feature is enabled by default in Jenkins versions 2.441 and earlier, LTS 2.426.2 and earlier, and essentially becomes the entry point for attackers to read arbitrary files on the Jenkins controller file system.
What Are the Repercussions of the Vulnerability?
CVE-2023-23897 allows potential attackers with Overall/Read permission to read entire files, whereas those without this permission can still read the first few lines. The available CLI commands determine how many lines can be read.
Binary files containing cryptographic keys can also be read, albeit with certain restrictions.
Aside from the ability to read the contents of all files with a known file path, Jenkins has listed some attacks that threat actors could potentially carry out to achieve RCE through the vulnerability. However, it should be noted that all the attack methods listed below are only possible if an attacker can obtain cryptographic keys from binary files.
- RCE via Resource Root URLs: Exploitable through two variants, this scenario necessitates the Resource Root URL functionality to be enabled.
- In the first variant, attackers employ the CLI WebSocket endpoint and need to know or be able to guess the username of any user with Overall/Read permission. The CLI WebSocket endpoint is accessible if Jenkins is running on a version of Jetty.
- For the second variant, the attacker must possess an API token for a non-anonymous user account. However, Overall/Read permission is not a prerequisite for this exploit variant.
- RCE via “Remember me” cookie: By forging a “Remember me” cookie, attackers can log into Jenkins via a web browser, gaining access to the Script Console when manipulating a cookie for an administrator account. This exploit requires the “Remember me” feature to be enabled and Overall/Read permission to access content beyond the initial lines in files.
- RCE via stored Cross-Site Scripting (XSS) attacks through build logs: By forging serialized console note objects, attackers can execute XSS attacks by injecting arbitrary HTML and JavaScript into build logs. The advisory notes that successful exploitation necessitates attackers’ control over build log output, typically achieved through mechanisms like pull requests.
- RCE via CSRF protection bypass: Using forged CSRF tokens (“crumbs”), attackers can perform CSRF (Cross-Site Request Forgery) attacks through the submission of POST requests with a valid crumb.
In addition to the possible attack cases listed above, attackers can exploit the CVE-2024-23897 vulnerability to decrypt secrets stored in Jenkins, delete any item within the Jenkins environment, and download a Java heap dump of either the Jenkins controller process or any agent process.
SOCRadar’s Attack Surface Management (ASM) module allows you to actively monitor your digital assets, identify potential vulnerabilities affecting your organization, and receive critical security alerts. You can sign up for the Freemium to gain access to SOCRadar XTI’s full range of features.
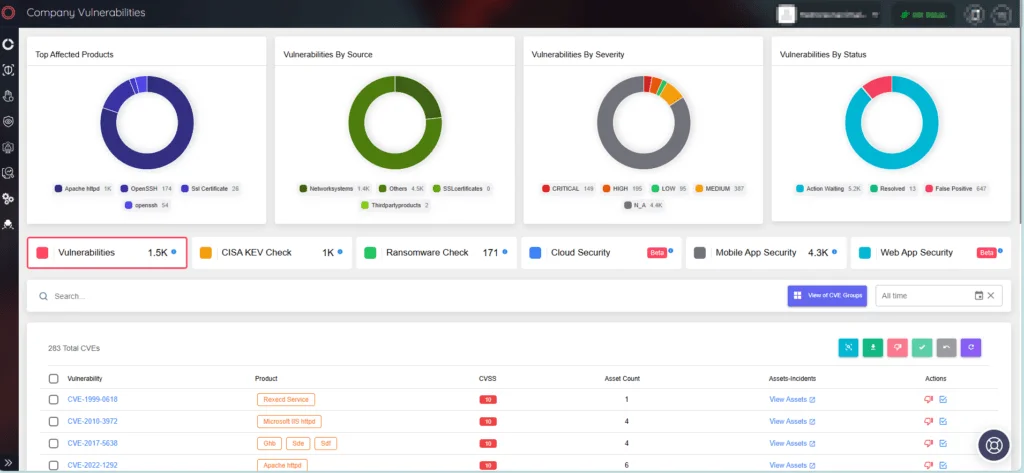
SOCRadar ASM/Company Vulnerabilities
Closer Look at the Core Issue and Other Resolved Vulnerabilities in Jenkins
Files with binary data in Jenkins may encounter issues when read, as the affected feature attempts to interpret them as strings using the controller process’s default character encoding.
Jenkins states that the success of reading depends on this encoding, leading to potential placeholder values for unreadable bytes. For instance, UTF-8 may replace roughly half of random binary data bytes with placeholders, making it challenging for attackers. However, using Windows-1252 encoding, only 5 out of 256 possible values would be replaced, offering fewer bytes to guess and fewer options for each byte.
In the Jenkins advisory, it is noted that telemetry from Jenkins instances indicates that over 90% use UTF-8, predominantly on Linux and Mac OS X, while instances on Windows are more likely to use a set allowing exploits.
It can be identified if you are affected by checking the file.encoding property in Manage Jenkins » System Information. To mitigate potential risks, Jenkins strongly advises administrators to update Jenkins promptly, irrespective of the file.encoding value, as the impact on randomly generated keys can vary.
The security advisory by Jenkins also includes the following high-severity issues:
- CVE-2024-23898 (CVSS: 8.8) – Cross-site WebSocket hijacking vulnerability in the CLI
- CVE-2024-23899 (CVSS: 8.8) – Arbitrary file read vulnerability in Git server Plugin can lead to RCE
- CVE-2023-6148 (CVSS: 8.0) – Stored XSS vulnerability in Qualys Policy Compliance Scanning Connector Plugin
- CVE-2024-23905 (CVSS: 8.0) – Content-Security-Policy protection for user content disabled by Red Hat Dependency Analytics Plugin
- CVE-2024-23904 (CVSS: 7.5) – Arbitrary file read vulnerability in Log Command Plugin
- CVE-2023-6147 (CVSS: 7.1) – XXE vulnerability in Qualys Policy Compliance Scanning Connector Plugin
With the Vulnerability Intelligence feature of SOCRadar, you can monitor CVE trends, access details on vulnerability updates, and stay informed about exploitation activities.
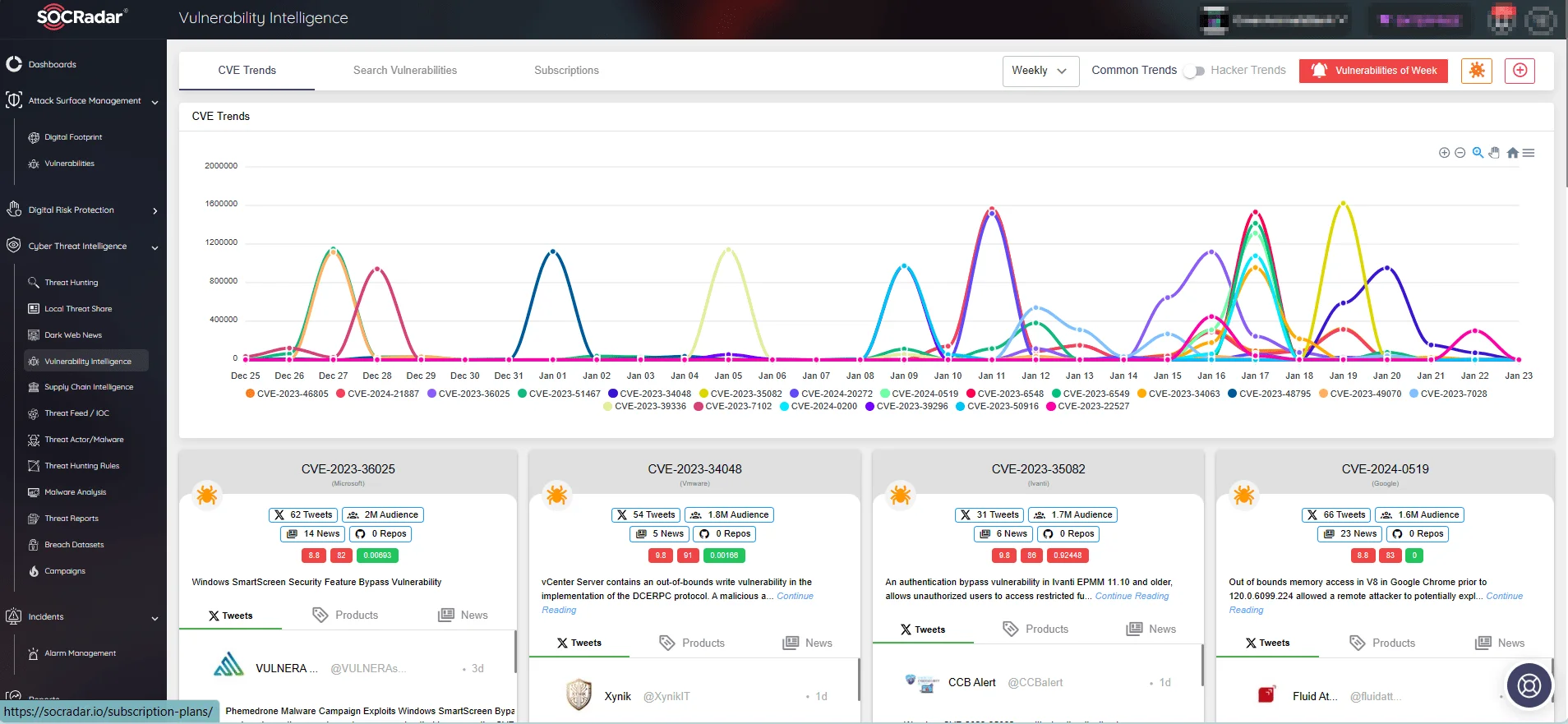
SOCRadar’s Vulnerability Intelligence, CVE trends
Has the CVE-2024-23897 Vulnerability in Jenkins Received a Fix?
In Jenkins versions 2.442 and LTS 2.426.3, a fix has been implemented to disable the command parser feature that leads to CVE-2024-23897.
Jenkins states that administrators facing issues with this fix can revert the change by setting the Java system property hudson.cli.CLICommand.allowAtSyntax to true; however, this action is not recommended, especially for networks exposed no non-admin users.
If updating Jenkins immediately is not feasible, administrators can disable access to CLI as a workaround method.
PoC Exploits Are Available for the Jenkins Vulnerability, CVE-2024-23897
Multiple Proof-of-Concept (PoC) exploits aimed at the Jenkins vulnerability have emerged. Researcher Florian Roth raised an alert on Twitter (X), cautioning about the weaponized PoC exploits and providing links to their GitHub pages (1, 2).
The availability of these PoC exploits is expected to prompt numerous threat actors to exploit the vulnerability in real-world attacks.
You can access detailed information on known vulnerabilities through our Vulnerability Intelligence module. This includes lifecycle information with each update, allowing you to stay informed about new PoC exploits as they emerge.
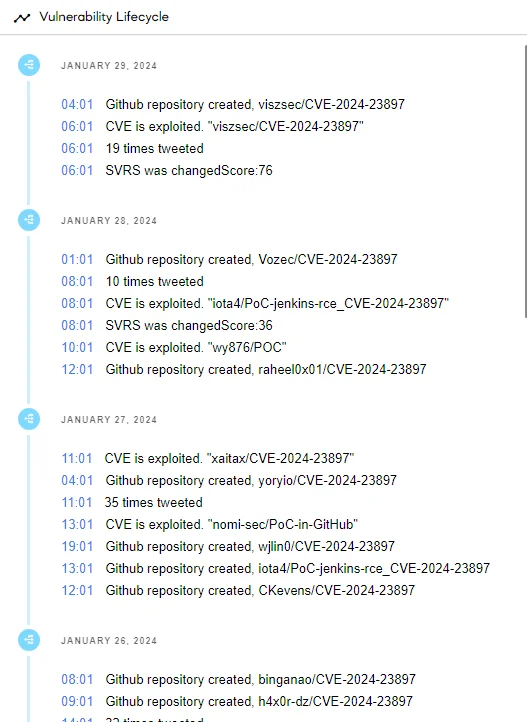
Lifecycle of the Jenkins vulnerability, CVE-2024-23897 (SOCRadar Vulnerability Intelligence)
Researcher Germán Fernández also cautioned that exploits are already in circulation, highlighting a Shodan search revealing over 77,000 assets exposed to the internet.
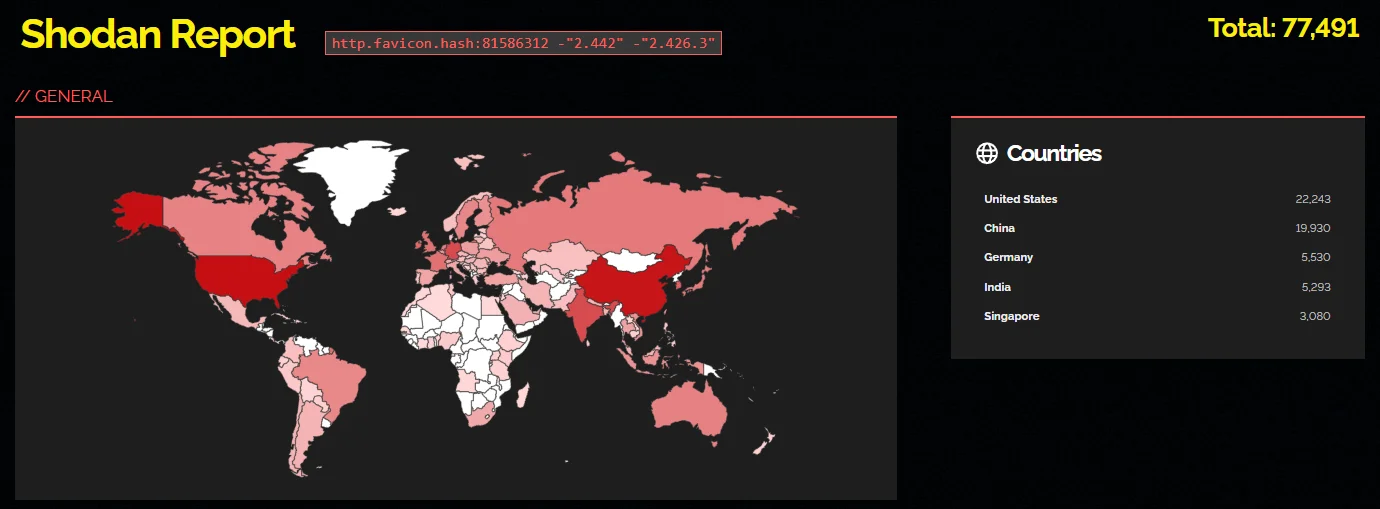
The count of exposed assets underscores the risk posed by the Jenkins RCE vulnerability (Shodan)
Moreover, there have been reports of Jenkins honeypots being targeted due to CVE-2024-23897, with researchers claiming to have observed mass-scanning and exploit activity on Jenkins CLI endpoints. However, it is unclear whether these actions were carried out by threat actors or researchers conducting investigations.
Critical Jenkins Vulnerability Added to CISA’s Known Exploited Vulnerabilities Catalog
CISA has included the critical Jenkins file read vulnerability, CVE-2024-23897, in its Known Exploited Vulnerabilities (KEV) Catalog due to confirmed active exploitation.
Federal agencies are required to address this vulnerability by September 9, 2024, as it poses risks to their operations. A Proof-of-Concept (PoC) exploit for this flaw has been circulating since January, and recently there is evidence of it being exploited in the wild.
Recent Exploitation and Threat Actor Activity
In March, Trend Micro detected several attack attempts leveraging CVE-2024-23897, and noted that Remote Code Execution (RCE) exploits for this vulnerability were being traded across various platforms.
More recently, CloudSEK and Juniper Networks reported that the vulnerability was exploited in attacks against BORN Group and Brontoo Technology Solutions. These attacks have been attributed to the IntelBroker threat actor and the RansomExx ransomware group.




































