
Critical RCE Vulnerability in Cisco Unified Communications with Risk of Root Access (CVE-2024-20253)
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert highlighting Cisco security updates, which address a critical vulnerability. The vulnerability affects several Cisco Unified Communications and Contact Center Solutions products, potentially resulting in Remote Code Execution (RCE).
Cisco Unified Communications products enable communication among individuals and teams, whereas Contact Center solutions provide AI-powered agent and customer experiences.
CISA warns that threat actors may exploit the vulnerability to gain control of affected systems, and urges organizations to take necessary security precautions.
Details of the Latest Cisco RCE Vulnerability, CVE-2024-20253
The Cisco Unified Communications RCE vulnerability, identified as CVE-2024-20253, has a severity score of 9.9 in the official advisory.
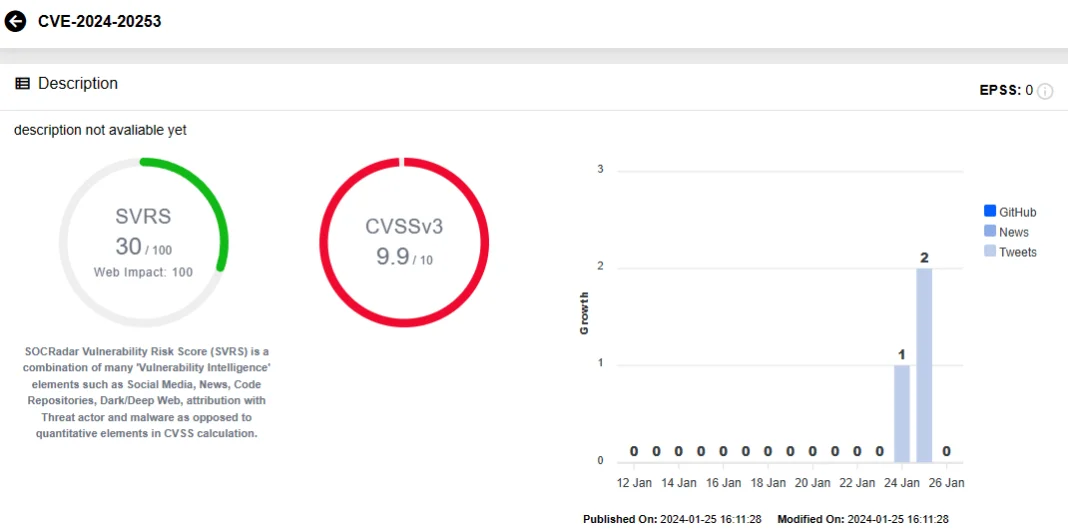
Vulnerability card of CVE-2024-20253 (SOCRadar Vulnerability Intelligence)
CVE-2024-20253 is caused by improper processing of user-supplied data as it is read into memory. To exploit this vulnerability, an unauthenticated, remote attacker could send a crafted message to an affected Cisco device’s listening port, which grants them the ability to execute arbitrary commands on the underlying operating system with the web services user’s privileges.
Cisco notes that with access to the underlying operating system, the attacker could gain root access to the affected device.
Affected Cisco Unified Communications and Contact Center Solutions Products
The following Cisco products are affected by this vulnerability in their default configuration:
- Unified Communications Manager (Unified CM)
- Unified Communications Manager IM & Presence Service (Unified CM IM&P)
- Unified Communications Manager Session Management Edition (Unified CM SME)
- Unified Contact Center Express (UCCX)
- Unity Connection
- Virtualized Voice Browser (VVB)
The Cisco advisory lists the specific versions that are affected, as well as those that include a fix.
SOCRadar’s Attack Surface Management (ASM) module, through real-time visibility into your attack surface and emerging vulnerabilities, allows for proactive threat identification and mitigation.
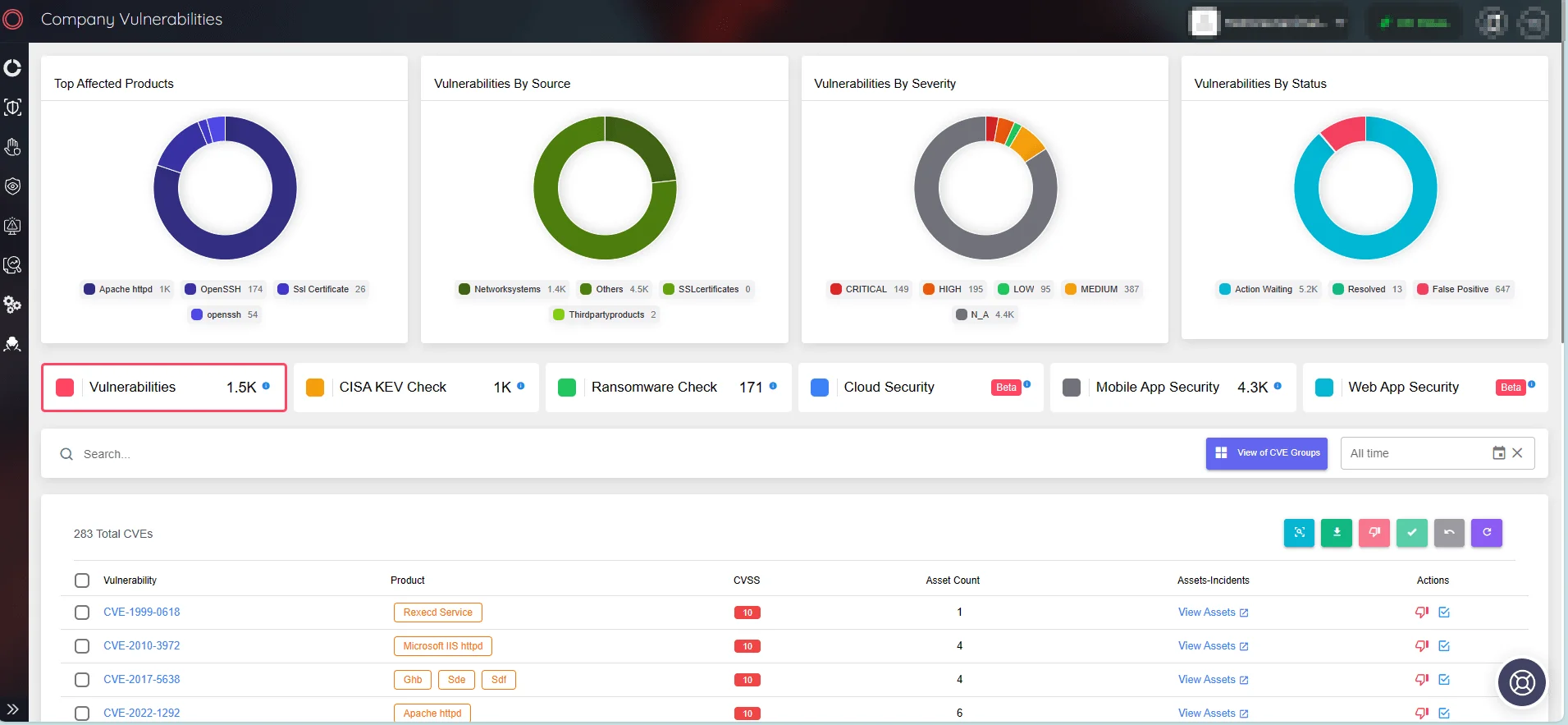
Monitor vulnerabilities affecting your assets via SOCRadar ASM
Is There a Workaround Available to Address CVE-2024-20253?
While no workarounds exist, the Cisco advisory provides a mitigation method:
- Set up Access Control Lists (ACLs) on intermediary devices that separate the Cisco Unified Communications or Cisco Contact Center Solutions cluster from users and the network. These ACLs should only grant access to the ports of deployed services.
Cisco emphasizes that customers should assess the applicability and effectiveness of the mentioned mitigation method in their specific environment. The vendor advises against implementing any workarounds or mitigations without first assessing their impact.
Furthermore, Cisco recommends following the best practices outlined in:
SOCRadar’s solutions provide organizations with critical information to proactively address potential threats and respond quickly to emerging risks. Stay up to date on CVE trends and updates with the Vulnerability Intelligence module.
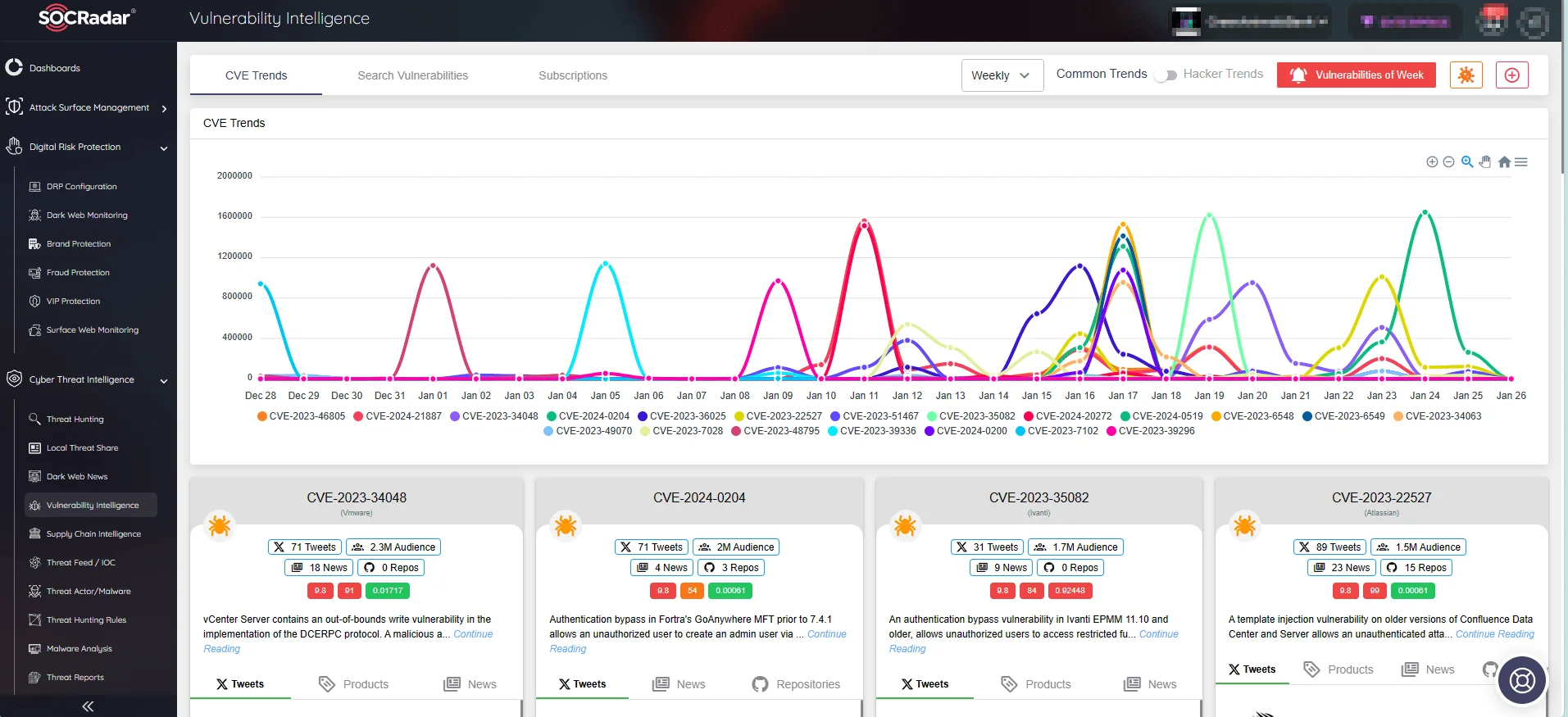
SOCRadar Vulnerability Intelligence
To take advantage of SOCRadar XTI’s capabilities and improve your vulnerability management strategy, sign up for the free edition.



































