Oracle Issued 389 New Security Patches in January 2024 Critical Patch Update
Oracle has released its Critical Patch Update advisory for January 2024, aimed at remedying vulnerabilities spanning various products. This update introduces 389 new security patches, including patches for many critical vulnerabilities.
CISA has issued an alert, highlighting the potential exploitation of specific vulnerabilities by threat actors to gain control over affected systems. The agency underscores the critical need for reviewing the January 2024 Critical Patch Update by Oracle and implementing recommended security measures to prevent any attempts at exploitation.
What Are the High-Risk Vulnerabilities in Oracle’s January 2024 Critical Patch Update?
Numerous vulnerabilities within the Oracle January 2024 Critical Patch Update have been classified with a CVSS score exceeding 9.0, denoting critical severity. Many of these vulnerabilities are susceptible to remote exploitation without the need for authentication.
Below is a list of these high-risk vulnerabilities grouped by their type, including the affected Oracle products and their supported versions addressed in the January 2024 Critical Patch Update.
CVE-2021-42575 (CVSS: 9.8): Lack of proper enforcement of policies for SELECT, STYLE, and OPTION elements in OWASP Java HTML Sanitizer.
Affected Product and Version:
- Oracle Hyperion Planning – 11.2.14.0.000
CVE-2021-43527 (CVSS: 9.8): Heap overflow vulnerability in NSS (Network Security Services) during the handling of DER-encoded DSA or RSA-PSS signatures.
Affected Product and Version:
- Fujitsu M10-1, M10-4, M10-4S, M12-1, M12-2, M12-2S Servers – Prior to XCP2430, prior to XCP3130, prior to XCP4040
CVE-2021-46848 (CVSS: 9.8): An off-by-one array size check flaw in GNU Libtasn1.
Affected Product and Version:
- Oracle Communications Cloud Native Core Network Repository Function – 23.3.1
CVE-2022-23221 (CVSS: 9.8): A vulnerability allowing Remote Code Execution (RCE) in H2 Console.
Affected Product and Version:
- Oracle SOA Suite – 12.2.1.4.0
CVE-2022-29155 (CVSS: 9.8): SQL injection vulnerability in OpenLDAP, exploitable during an LDAP search operation due to lack of proper escaping.
Affected Product and Version:
- Fujitsu M10-1, M10-4, M10-4S, M12-1, M12-2, M12-2S Servers – Prior to XCP2420, prior to XCP3120, prior to XCP4030
CVE-2022-31692 (CVSS: 9.8): Authorization rules bypass vulnerability in Spring Security.
Affected Product and Version:
- Oracle Banking Virtual Account Management – 14.5.0-14.7.0
CVE-2022-36944 (CVSS: 9.8): Java deserialization chain in Scala, exploitable only in conjunction with a Java object deserialization within an application.
Affected Product and Version:
- Oracle Communications BRM – Elastic Charging Engine – 12.0.0.4-12.0.0.7
- Oracle Communications Service Catalog and Design – 7.4.2.8.0
- Oracle Banking Corporate Lending Process Management – 14.5.0-14.7.0
CVE-2022-37434 (CVSS: 9.8): Heap-based buffer over-read or overflow in zlib.
Affected Product and Version:
- Oracle Hyperion Financial Management – 11.2.14.0.000
- JD Edwards EnterpriseOne Tools – Prior to 9.2.8.0
CVE-2022-42920 (CVSS: 9.8): Out-of-bounds writing issue in Apache Commons BCEL APIs allows manipulation of class characteristics, producing arbitrary bytecode.
Affected Product and Version:
- Oracle Communications Service Catalog and Design – 7.4.0.7.0, 7.4.1.5.0, 7.4.2.8.0
- Oracle Financial Services Behavior Detection Platform – 8.0.8.1, 8.1.1.1, 8.1.2.5, 8.1.2.6
- Oracle Retail Advanced Inventory Planning – 15.0.3, 16.0.3
CVE-2022-48174 (CVSS: 9.8): Stack overflow vulnerability in ash.c:6030 in busybox, exploitable in the Internet of Vehicles environment, allowing execution of arbitrary code from command.
Affected Product and Version:
- Oracle Communications Cloud Native Core Network Function Cloud Native Environment – 23.3.1
CVE-2023-32002 (CVSS: 9.8): Vulnerability in Node.js allows the bypass of the policy mechanism using Module._load().
Affected Product and Version:
- JD Edwards EnterpriseOne Tools – Prior to 9.2.8.1
CVE-2023-34034 (CVSS: 9.8): A security bypass vulnerability in Spring Security, occurring when using “**” as a pattern in Spring Security configuration for WebFlux.
Affected Product and Version:
- Oracle Communications Service Catalog and Design – 7.4.2.8.0
- Oracle Communications Cloud Native Core Network Slice Selection Function – 23.2.0, 23.3.1
- Oracle Banking Corporate Lending Process Management – 14.5.0-14.7.0
- Oracle Banking Digital Experience – 21.1.0, 22.1.0, 22.2.0
- Oracle Banking Liquidity Management – 14.5.0-14.7.0
- Oracle Financial Services Analytical Applications Infrastructure – 8.0.7, 8.0.8, 8.0.9, 8.1.0, 8.1.1, 8.1.2
CVE-2023-38545 (CVSS: 9.8): Heap-based buffer overflow vulnerability in curl during a slow SOCKS5 proxy handshake.
Affected Product and Version:
- Oracle Essbase – 21.5.3.0.0
- Oracle HTTP Server – 12.2.1.4.0
- MySQL Cluster – 8.0.34 and prior, 8.1.0
CVE-2023-46604 (CVSS: 9.8): Remote Code Execution vulnerability in the Java OpenWire protocol marshaller.
Affected Product and Version:
- Oracle Communications Element Manager – 9.0.0.0.0-9.0.2.0.1
- Oracle Communications Session Report Manager – 9.0.0.0.0-9.0.2.0.1
- Oracle Banking APIs – 22.1.0, 22.2.0
- Oracle Banking Digital Experience – 22.1.0, 22.2.0
- Oracle Financial Services Analytical Applications Infrastructure – 8.0.7, 8.0.8, 8.0.9, 8.1.0, 8.1.1, 8.1.2
- Oracle Enterprise Data Quality – 12.2.1.4.0
CVE-2023-50164 (CVSS: 9.8): Path traversal vulnerability in Apache Struts, allowing attackers to manipulate file upload parameters, leading to the potential upload of a malicious file and enabling Remote Code Execution.
Affected Product and Version:
- Oracle Communications Policy Management – 12.6.1.0.0, 15.0.0.0.0
- Oracle Hyperion Infrastructure Technology – 11.2.14.0.000
- MySQL Enterprise Monitor – 8.0.36 and prior
CVE-2023-44981 (CVSS: 9.1): The vulnerability allows authorization bypass through user-controlled key in Apache ZooKeeper.
Affected Product and Version:
- Oracle Communications Cloud Native Core Network Data Analytics Function – 23.3.0, 23.4.0
- Oracle Communications Service Catalog and Design – 7.4.2.8.0
Secure Your Digital Environment: Apply Oracle’s January 2024 Critical Patch Update
It is strongly advised that you adhere to the Oracle advisory and apply the security patches included in the January 2024 Critical Patch Update as soon as possible, while also ensuring that your systems are running actively supported Oracle products. Oracle states that they periodically receive reports of exploitation attempts against vulnerabilities that have already been fixed. The vendor further warns that incidents have been reported in which attackers succeeded because customers failed to apply available Oracle patches.
For detailed information on each vulnerability, the affected products, and patch availability documents, refer to the Oracle January 2024 Critical Patch Update advisory.
SOCRadar’s Attack Surface Management (ASM) module can help you monitor digital assets, identify potential vulnerabilities affecting your organization, and receive critical security alerts. Sign up for a free edition to experience the full capabilities of SOCRadar XTI and take a proactive step towards a robust security posture.
SOCRadar ASM/Company Vulnerabilities
Explore Comprehensive Vulnerability Details with the Vulnerability Intelligence Feature
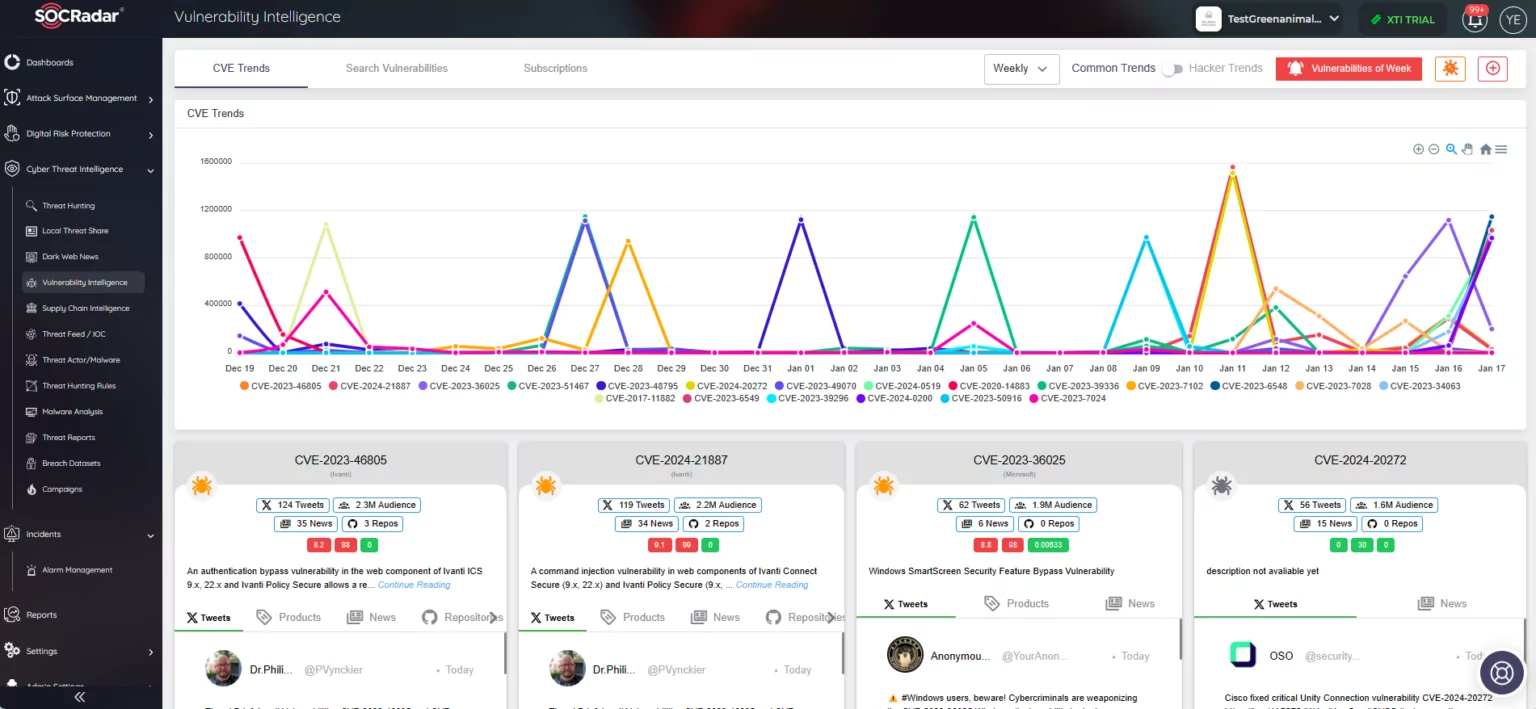
SOCRadar Vulnerability Intelligence
With this module, you gain access to comprehensive details about each identified vulnerability, encompassing information about exploits and mentions.
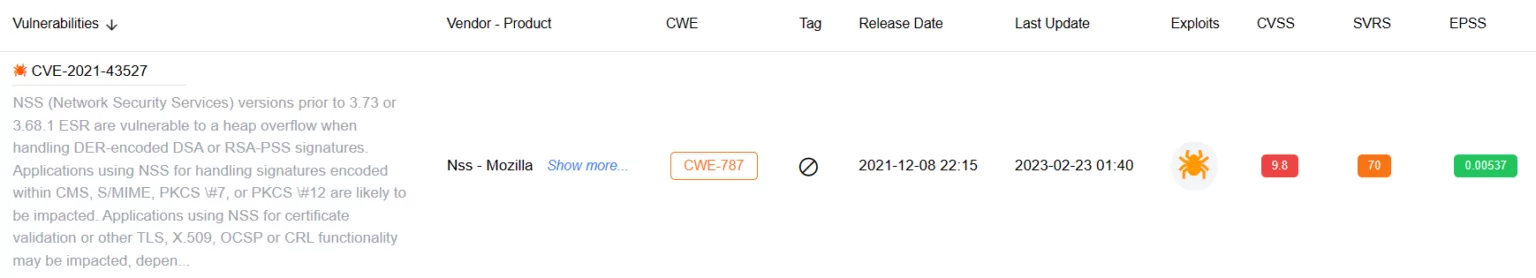
Search for vulnerabilities on SOCRadar’s Vulnerability Intelligence: CVE-2023-43527
Additionally, you can view the SOCRadar Vulnerability Risk Score (SVRS), which helps gain a better understanding of a vulnerability’s prominence and potential for exploitation. This score is derived from various sources, including social media, news, code repositories, the Dark and Deep Web, and exploit attribution to Threat Actor/Malware.
Explore the capabilities of SOCRadar’s Vulnerability Intelligence through CVE Radar, a complimentary feature available on SOCRadar Labs.
CVE Radar from SOCRadar Labs