
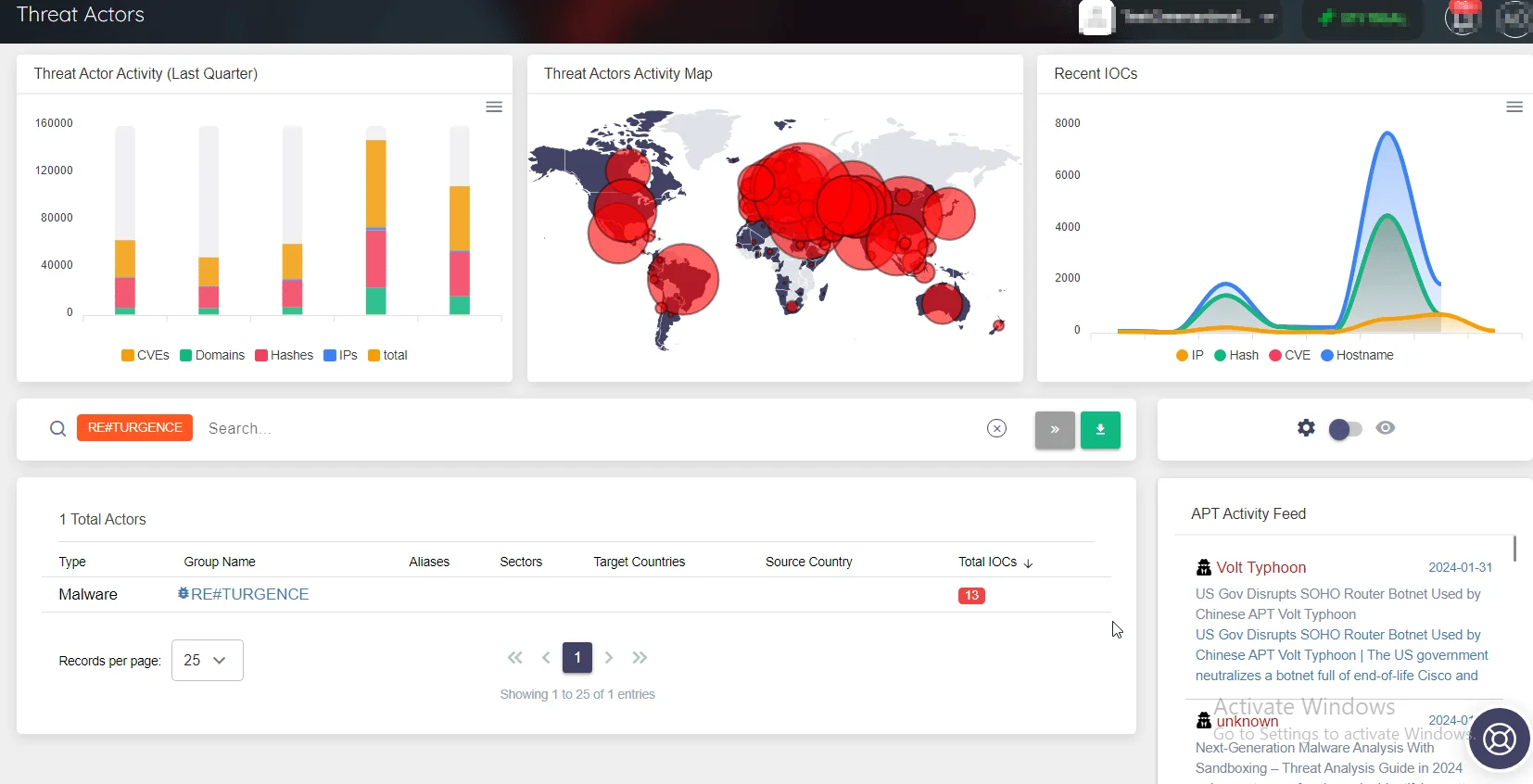
RE#TURGENCE: A Deep Dive into Turkish Hackers’ Campaign Targeting MSSQL Servers
Financially motivated Turkish threat actors have emerged with a significant development in cyber threats, introducing a new campaign named “RE#TURGENCE”. This campaign exploits MSSQL servers to deliver the MIMIC ransomware across the US, EU, and LATAM regions.

An AI illustration of the RE#TURGENCE campaign
RE#TURGENCE primarily aims to gain initial access through MSSQL database servers. The attack strategy involves two potential outcomes: selling access to compromised hosts or deploying ransomware payloads. This pattern was revealed following a significant operational security failure by the attackers.
Similar to the previously identified DB#JAMMER campaign, RE#TURGENCE attackers gain entry by brute-forcing administrative passwords on exposed MSSQL servers. The critical xp_cmdshell procedure, usually disabled by default, is exploited to execute commands on the host system, marking the start of the intrusion.
Upon successful entry, attackers initiate code execution through the xp_cmdshell procedure. The key phase involves downloading and executing a file via a PowerShell command, which then downloads and runs a heavily obfuscated Cobalt Strike payload. This payload, loaded into the current process using in-memory reflection techniques, plays a vital role in the campaign’s progression.
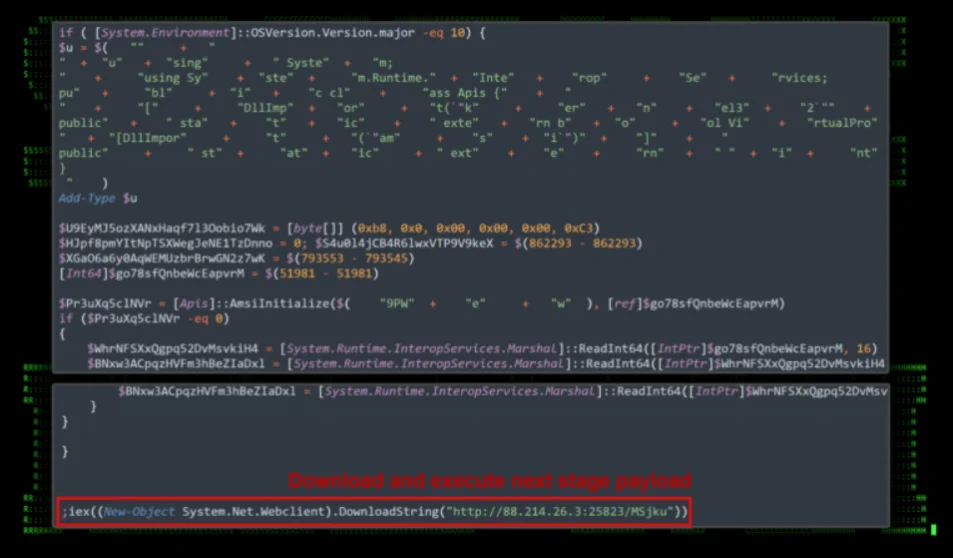
PowerShell initial code execution, phase 1 (Securonix)
Threat actors achieve persistence by creating local users and abusing legitimate software by installing the AnyDesk service. Then, they use Mimikatz to access credentials and the Advanced Port Scanner utility to understand the network better, enabling lateral movements across the network.
The endgame of RE#TURGENCE involves the deployment of the MIMIC ransomware. This strain uses the legitimate Everything application to locate target files for encryption. The ransomware, manually executed by the attackers, significantly disrupts operations on the compromised servers.
Interestingly, the campaign’s unfolding allowed insights into the attackers’ operations, revealing communications and usernames that tie back to geographical profiles consistent with known hacking platforms.
C2 and Infrastructure of RE#TURGENCE
The RE#TURGENCE campaign consisted of several Command and Control (C2) IP addresses and a specific domain for its Cobalt Strike beacon, highlighting the sophisticated infrastructure supporting this operation.
The C2 addresses used seemingly random, non-standard port numbers. The only domain used, seruvadessigen.3utilities[.]com, was pulled from the Cobalt Strike beacon configuration.
Cobalt Strike beacon configuration (Securonix)
Mitigations and Recommendations Against RE#TURGENCE
Robust security practices are essential to combat threats like RE#TURGENCE. These include implementing strong password policies, ensuring regular updates, using multi-factor authentication, and maintaining effective intrusion detection systems. Additionally, organizations should focus on regular backups, employee training, and a comprehensive incident response plan.
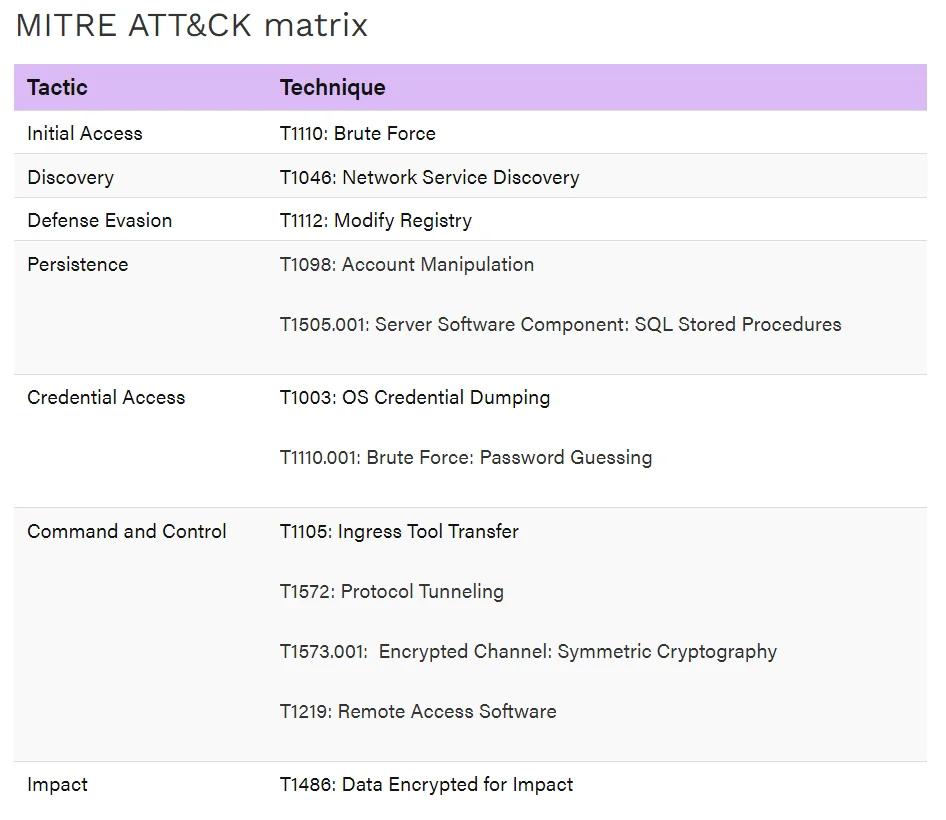
MITRE ATT&CK matrix
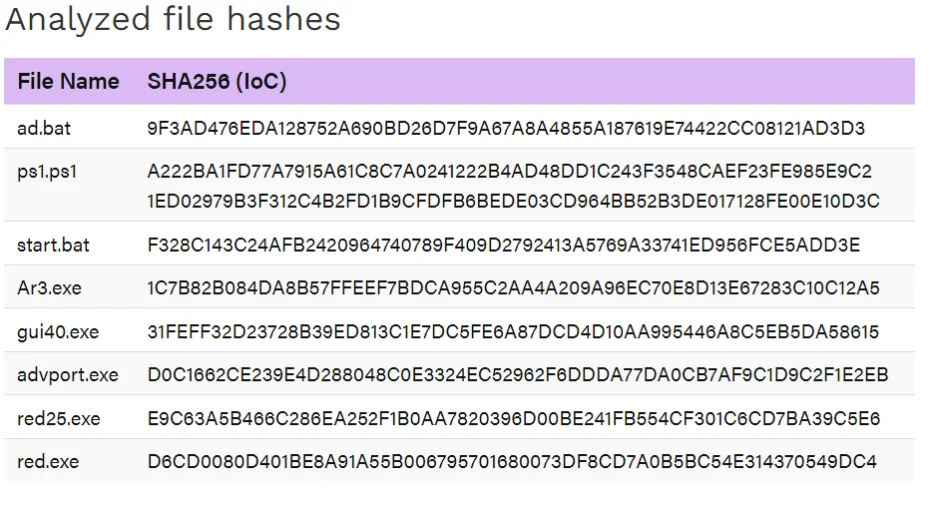
Analyzed file hashes
RE#TURGENCE underscores the ever-present need for proactive cybersecurity measures. As threat actors evolve their tactics, our defenses must evolve as well. The campaign serves as a stark reminder of the complexity and persistence of modern cyber threats, underscoring the need for advanced solutions such as those provided by SOCRadar.
For more information about threat campaigns, you can explore the Campaigns page on the SOCRadar platform; a complementary version of this feature is also available on SOCRadar Labs.
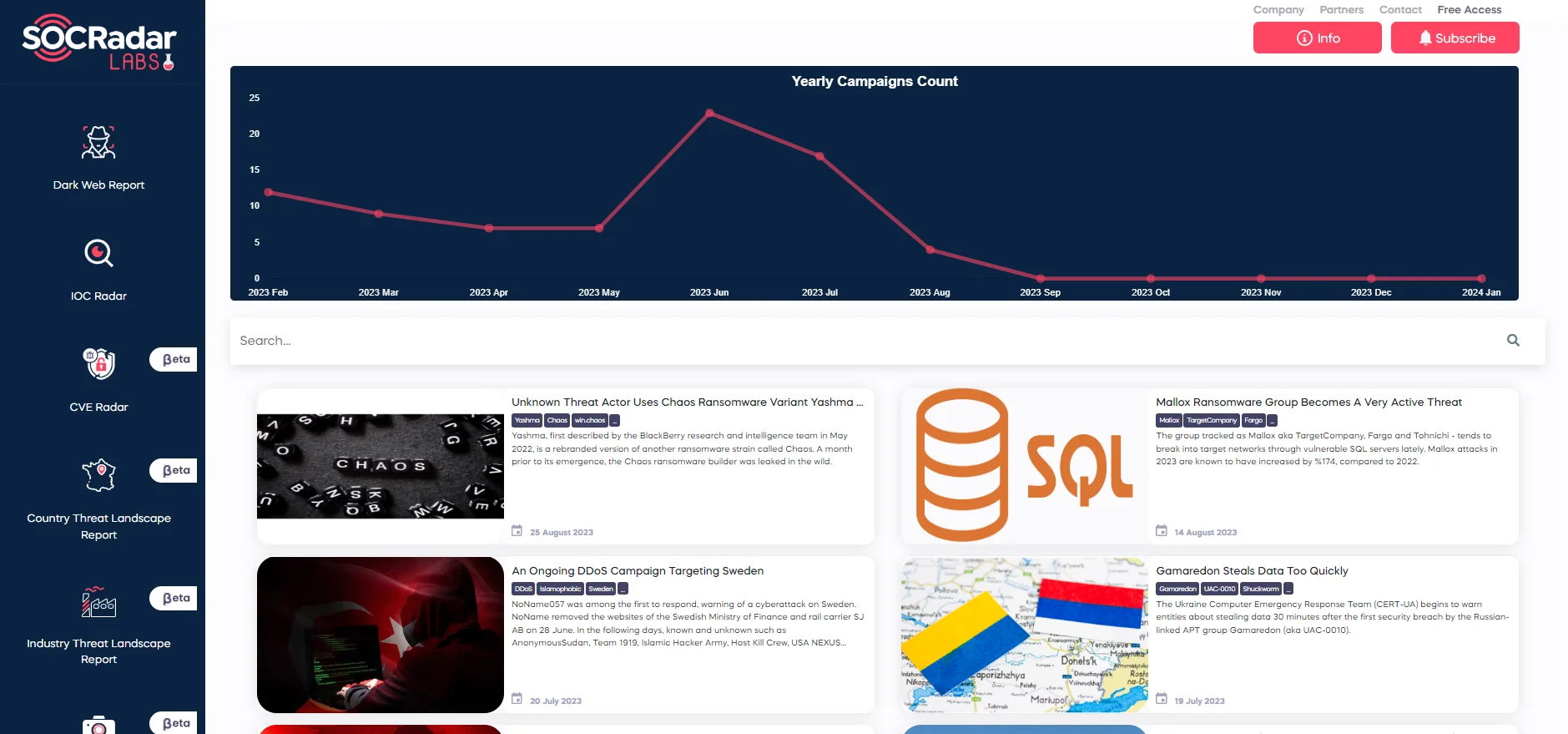
Campaigns page on SOCRadar Labs
Access Insights on Threat Actors and Malware with SOCRadar XTI
At SOCRadar, we offer a suite of tools to tackle such threats. Our services span from Cyber Threat Intelligence to Digital Risk Protection and Dark Web Monitoring. We emphasize the importance of a multi-layered defense strategy and continuous vigilance in the ever-evolving landscape of cyber threats.
For more details on identified Threat Actors/Malware, including the latest related news, associated vulnerabilities and threat actors, as well as available YARA rules, you can access the SOCRadar platform. This information is automatically updated on the platform whenever available, providing you with timely threat intelligence to combat cyber threats effectively.
Campaigns page on SOCRadar Labs



































