
Campaign Alert: The Year-Long Shadow of AsyncRAT in U.S. Infrastructure

An AI illustration of AsyncRAT
The Rise of AsyncRAT: A Persistent Cyber Threat
AsyncRAT, an open-source remote access tool released in 2019 and available on GitHub, has become a significant threat in the cybersecurity world. Easily accessible and free to use, this tool is frequently exploited as a Remote Access Trojan (RAT). Its features such as keylogging, infiltration techniques, and initial access phase for final payload distribution make it a preferred choice among cybercriminals.
AsyncRAT’s open-source nature has led to numerous modifications and adaptations, making it even more dangerous. As reported by TrendMicro, it has been used in various campaigns, including those organized by APT group Earth Berberoka.
In-Depth Analysis of AsyncRAT’s Impact and Tactics
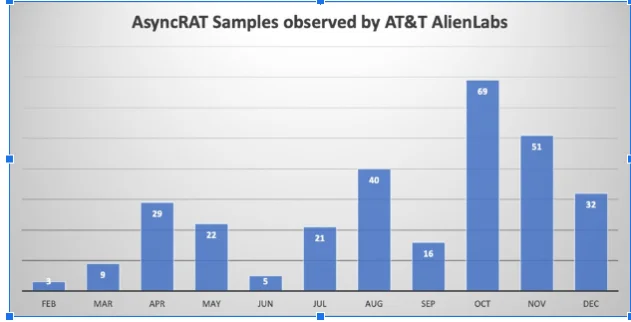
Number of samples observed by Alien Labs in this campaign.
The analysis reveals that AsyncRAT is part of many sophisticated cyber attacks. As observed by AT&T Alien Labs, there was an increase in phishing emails in early September; These emails targeted specific individuals within companies through a multi-stage infection process that included a gif attachment and an svg file, ultimately leading to the execution of the AsyncRAT client. This attack method was also noticed by cybersecurity experts on platforms such as X (formerly Twitter).
The loader used by AsyncRAT consists of multiple stages that are obfuscated and controlled by a Command and Control (C&C) server that evaluates whether the victim has a sandbox environment before deploying the main payload. This complex mechanism demonstrates the high level of evasion tactics used by attackers.
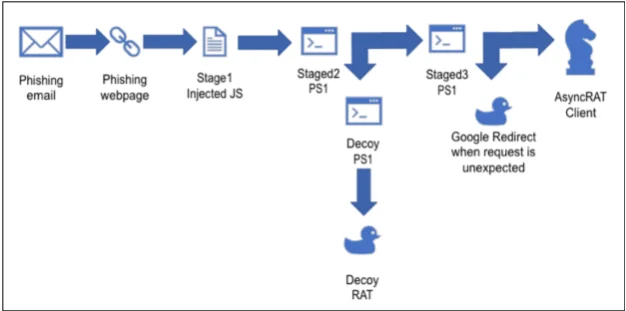
Execution flow. (AT&T Alien Labs research)
SOCRadar’s Role in Addressing the AsyncRAT Threat
In the face of advanced threats, tools such as SOCRadar can play an important role in improving cybersecurity defenses. SOCRadar offers a comprehensive Cyber Threat intelligence Module that can help organizations detect and respond to such threats more effectively. With its suite of resources providing real-time alerts, comprehensive threat analysis, and actionable intelligence, SOCRadar empowers users to proactively anticipate and respond to cyber attacks.
Details of AsyncRAT on the SOCRadar platform (Cyber Threat Intelligence module)
SOCRadar enables users to stay one step ahead of cybercriminals by providing detailed information, real-time alerts, and actionable intelligence on emerging threats. The capabilities of monitoring specific indicators of compromise (IOCs) associated with certain malware and its ability to scan and analyze an organization’s digital footprint make it an invaluable resource in the fight against such sophisticated cyber threats.
For those seeking detailed information and the latest insights on AsyncRAT, SOCRadar offers a wealth of resources. Users can explore the Win.asyncrat IOC Link for specific indicators of compromise, providing a focused view on how to identify and understand the AsyncRAT threat.
Additionally, for a broader perspective that includes in-depth data and analysis, we encourage a visit to the Campaigns page on the SOCRadar platform. This page presents comprehensive information that aids in understanding and mitigating the multifaceted threat posed by AsyncRAT.
Conclusion
The persistent threat posed by AsyncRAT underscores the importance of advanced cybersecurity strategies and constant vigilance. The complex, multi-stage attacks employed by AsyncRAT require a deep understanding of cyber threats and proactive defensive measures. Tools like SOCRadar are invaluable in providing the necessary intelligence and capabilities to detect, analyze, and mitigate sophisticated cyber threats, helping protect infrastructure from the ongoing dangers like posed by AsyncRAT.




































